Linux Shell Tips and Tricks
A collection of useful tips and tricks for the linux shell that I have stumbled across over the years. I'll keep updating this post as I come across something of value. I use bash, so these apply to bash unless noted otherwise but my work in other shells. cat The cat command can be...Simple DDNS solution supporting IPv6 and your own domains using Cloudflare and some Python
I think it is safe to say that most of IT professionals have some kind of lab environment and many of us have some kind of lab at home. Sometimes it is necessary to use resources from that lab outside of the house, which means they need to be exposed to the Internet and you […]Video: Why Knowing About Industry / Market Makes You Smarter
You can be useful to your salary owner by understanding whats happening in the wider market. I use the example of understanding TLS 1.2/1.3 to explain why L4/L5/App firewalls are losing their value. If your job requires communication with non-technical roles (Mgrs, PMs, Execs) knowing about these trends and how they force vendors to behave […]Data Center Management as a Service Promises to Be Disruptive
 Just three vendors offer this service now, but major colocation providers such as Equinix would be wise to jump on the DMaaS train early.
Just three vendors offer this service now, but major colocation providers such as Equinix would be wise to jump on the DMaaS train early.
iNOG-10 & RIPE-Hackathon
In June 2018, I was lucky enough to attend the iNOG 10 session in Dublin, co-present a talk and also take part in the RIPE hackathon.
This post is a share on the experience. This isn’t because I’m running out of non-technical material, but this is to uncover both events for those that may want to attend, take part and experience what these kinds of sessions offer.
iNOG
The iNOG Irish Network Operators community surfaced briefly with events in 2005 (originally as the IENOG) but fell silent and was reborn in 2015 as the organisation
as it is today. Started by five returnees to Ireland and some economic migrants, the group has been seeing a high number of attendees to the events and over 700 members on Meetup! Not bad for something that came in on a started on a boat!!! (See below).
The group aims to deliver valuable content to the audience free of charge. Whilst ‘valuable’ has a variety of meanings depending on the audience, the general idea is to share experience of network based activities. As you can imagine, this is very wide ranging and just in the iNOG 10 session, talks were given on automation, data Continue reading
Check Out Our Newest Network Automation Course, Now Available On Our Streaming Site
We’ve just added a new Network Automation course, Network Automation with Ansible (v2), to our video library!
Instructor: Eric Chou
Course Duration: 4hrs 33min
Course Description
Ansible is quickly becoming the automation tool of choice for networking. This course aims to demystify Ansible and get you up and running with today’s technologies. After covering the basics, we’ll move on to the more advanced topics as they are applicable to network automation. This course will be cover the latest Ansible GA release 2.4 with some augments for upcoming development release 2.5.
Headcount: The Latest in Hirings, Firings, and Retirings — July 5, 2018
 Diane Bryant leaves Google Cloud after 7 months; Equifax hires former IBM executive to serve as its CTO; Riverbed creates a new position - chief customer officer.
Diane Bryant leaves Google Cloud after 7 months; Equifax hires former IBM executive to serve as its CTO; Riverbed creates a new position - chief customer officer.
Research: P Fat Trees
Link speeds in data center fabrics continue to climb, with 10g, 25g, 40g, and 100g widely available, and 400g promised in just a few short years. What isn’t so obvious is how these higher speeds are being reached. A 100g link, for instance, is really four 25g links bundled as a single link at the physical layer. If the optics are increasing in speed, and the processors are increasing in their ability to switch traffic, why are these higher speed links being built in this way? According to the paper under investigation today, the reason is the speed of the chips that serialize traffic from and deserialize traffic off the optical medium. The development of the Complementary metal–oxide–semiconductor, of CMOS, chips required to build ever faster optical interfaces seems to have stalled out at around 25g, which means faster speeds must be achieved by bundling multiple lower speed links.
Mellette, William M., Alex C. Snoeren, and George Porter. “P-FatTree: A Multi-Channel Datacenter Network Topology.” In Proceedings of the 15th ACM Workshop on Hot Topics in Networks, 78–84. HotNets ’16. New York, NY, USA: ACM, 2016. https://doi.org/10.1145/3005745.3005746.

The authors then point out that many data operators Continue reading
Nokia Strikes 5G Test Deal With China Social Media Giant Tencent
 The vendor has seen around 20 percent growth per quarter over the past two quarters across its enterprise, webscale, and cable TV markets.
The vendor has seen around 20 percent growth per quarter over the past two quarters across its enterprise, webscale, and cable TV markets.
ThetaRay Scores $30 Million Series B for AI-Powered Security
 The startup’s customers include banks and industrial firms. Its latest funding round brings its total to $60.5 million.
The startup’s customers include banks and industrial firms. Its latest funding round brings its total to $60.5 million.
Telecom Services 23% of US IT Market
The drive for SD-WAN and mobile phones degrades this position.
Debugging Serverless Apps
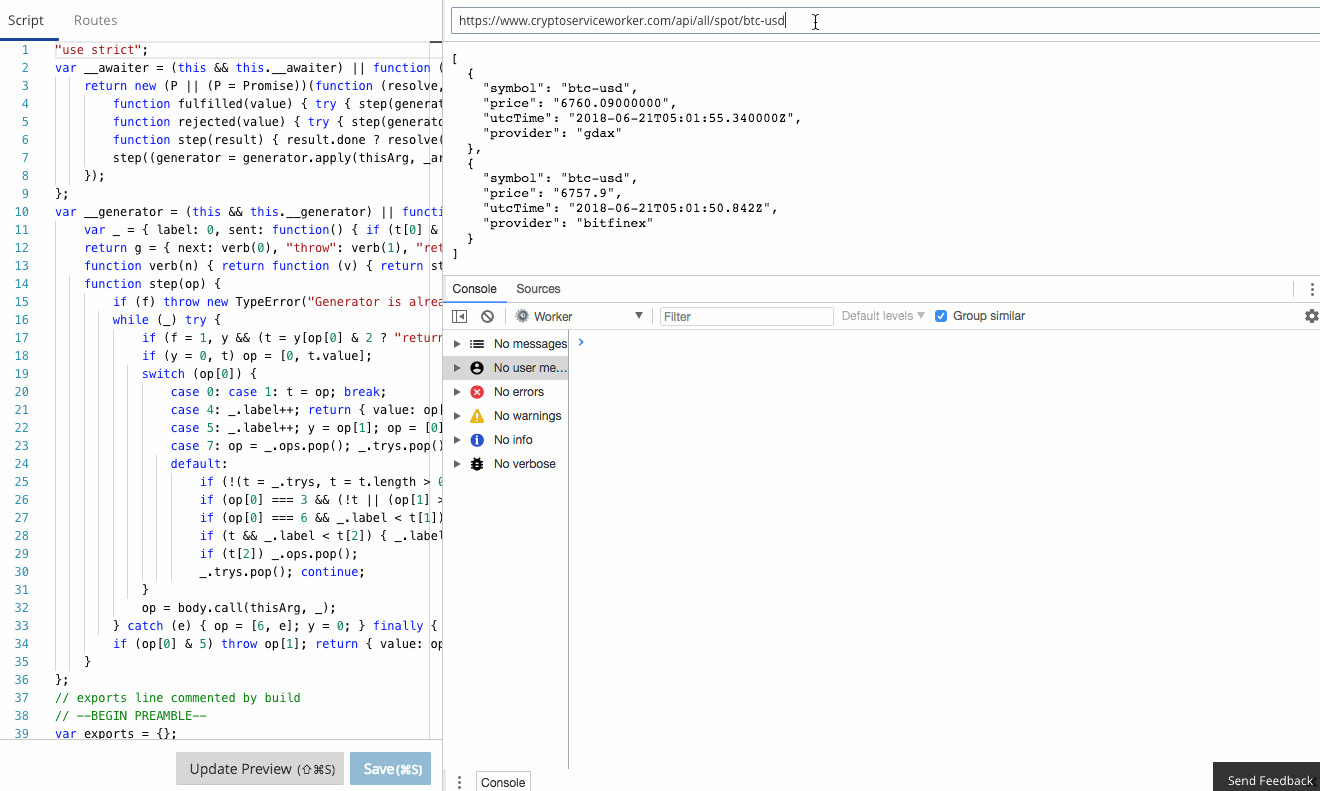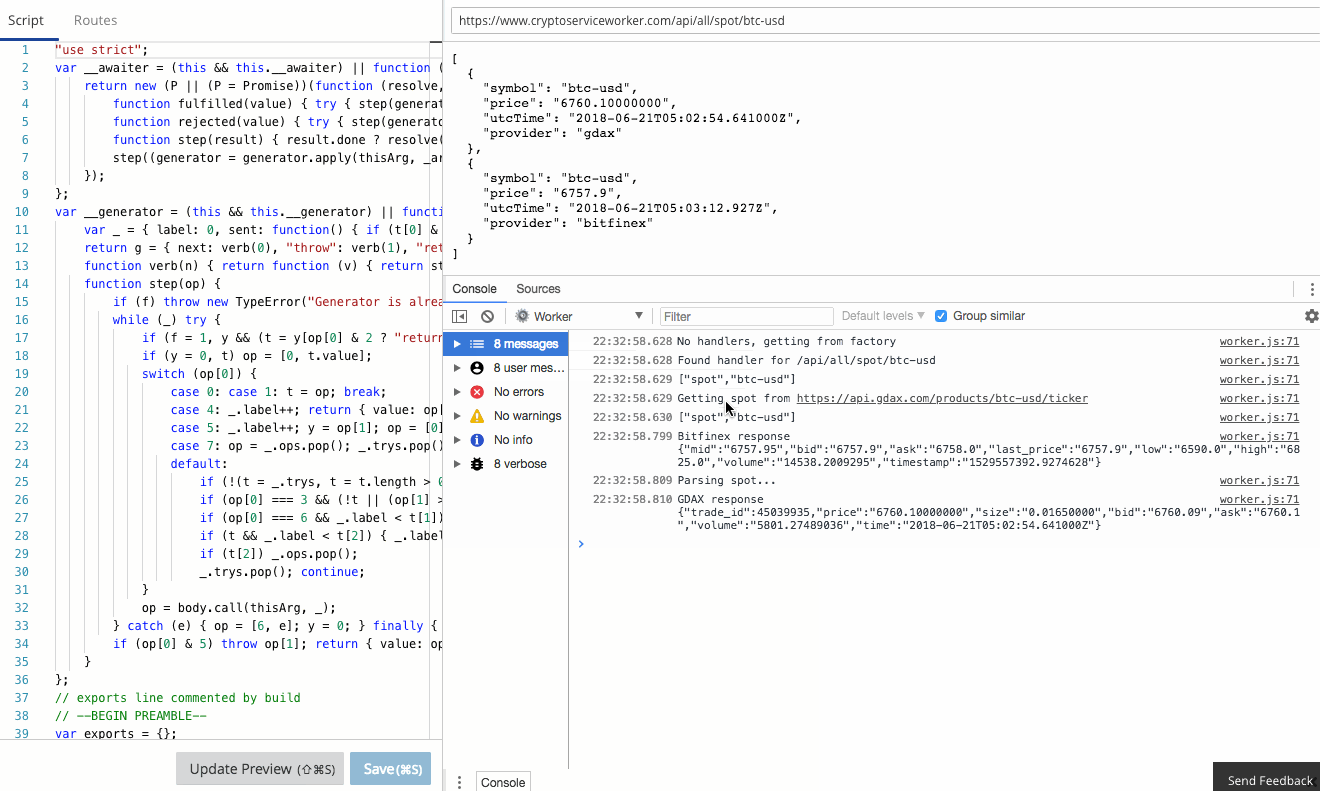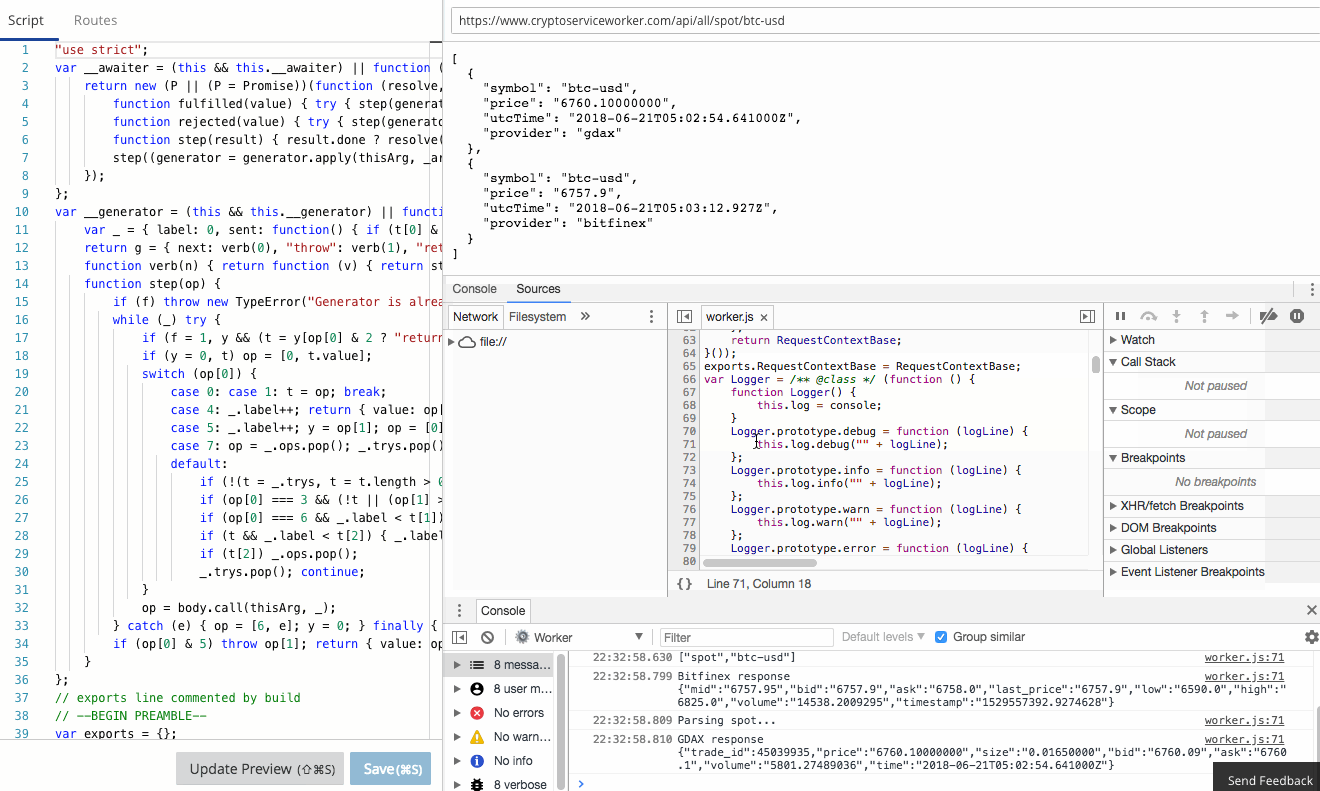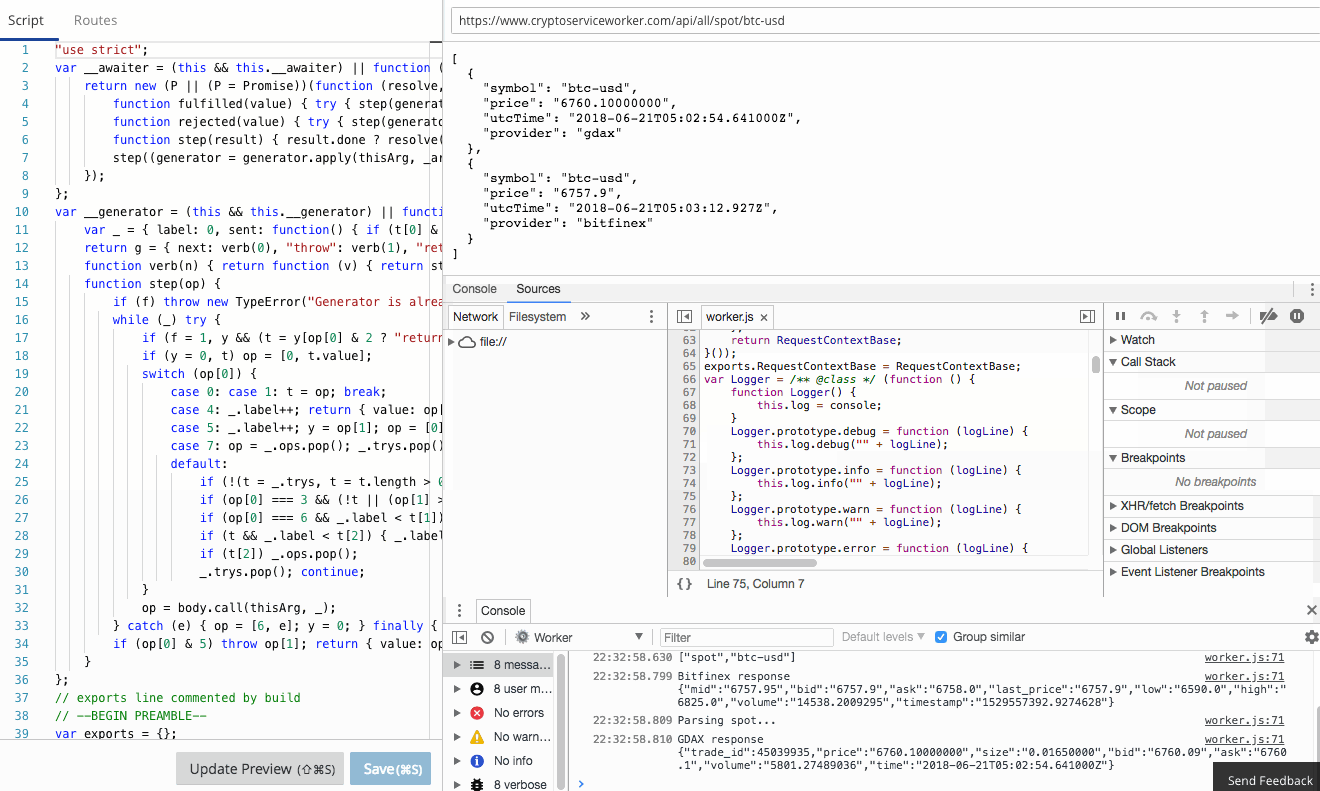
The Workers team have already done an amazing job of creating a functional, familiar edit and debug tooling experience in the Workers IDE. It's Chrome Developer Tools fully integrated to Workers.
console.log in your Worker goes straight to the console, just as if you were debugging locally! Furthermore, errors and even log lines come complete with call-site info, so you click and navigate straight to the relevant line.
In this blog post I’m going to show a small and powerful technique I use to make debugging serverless apps simple and quick.
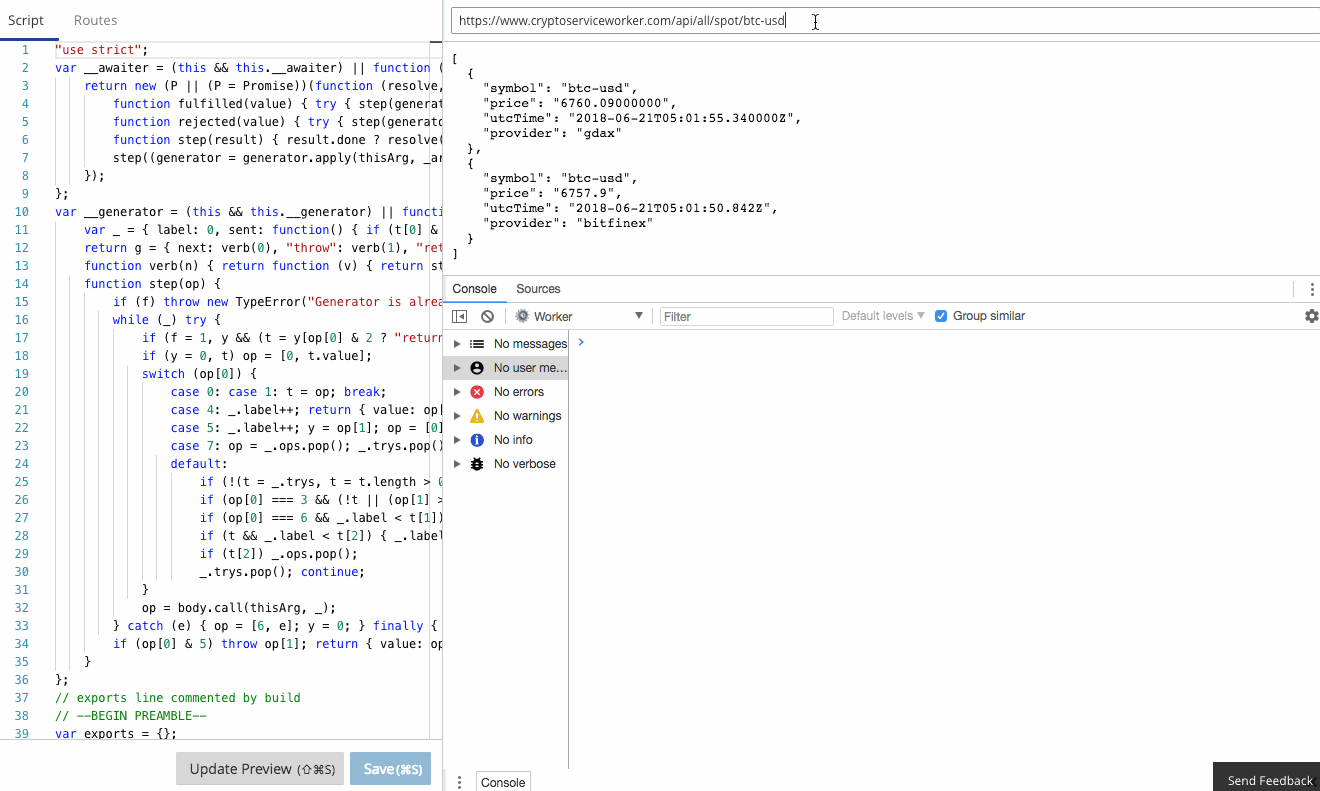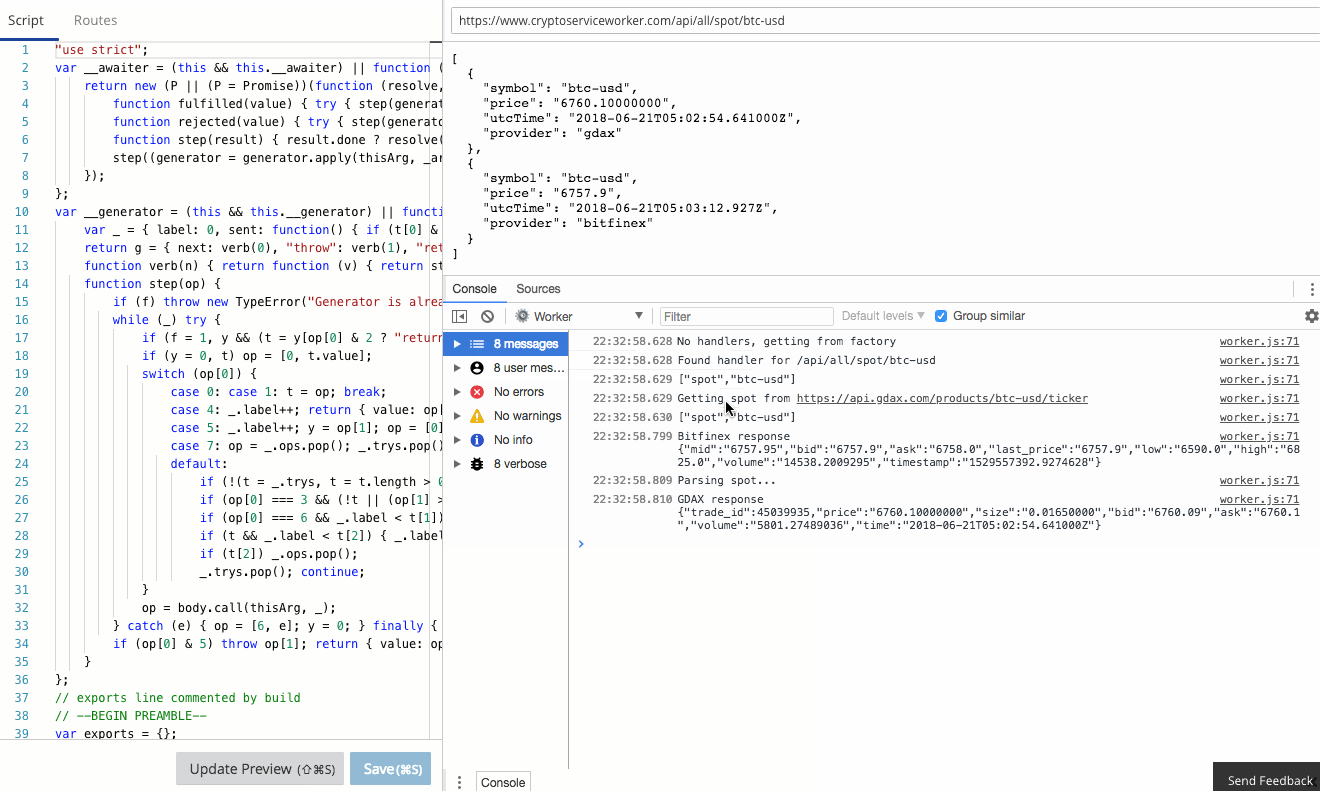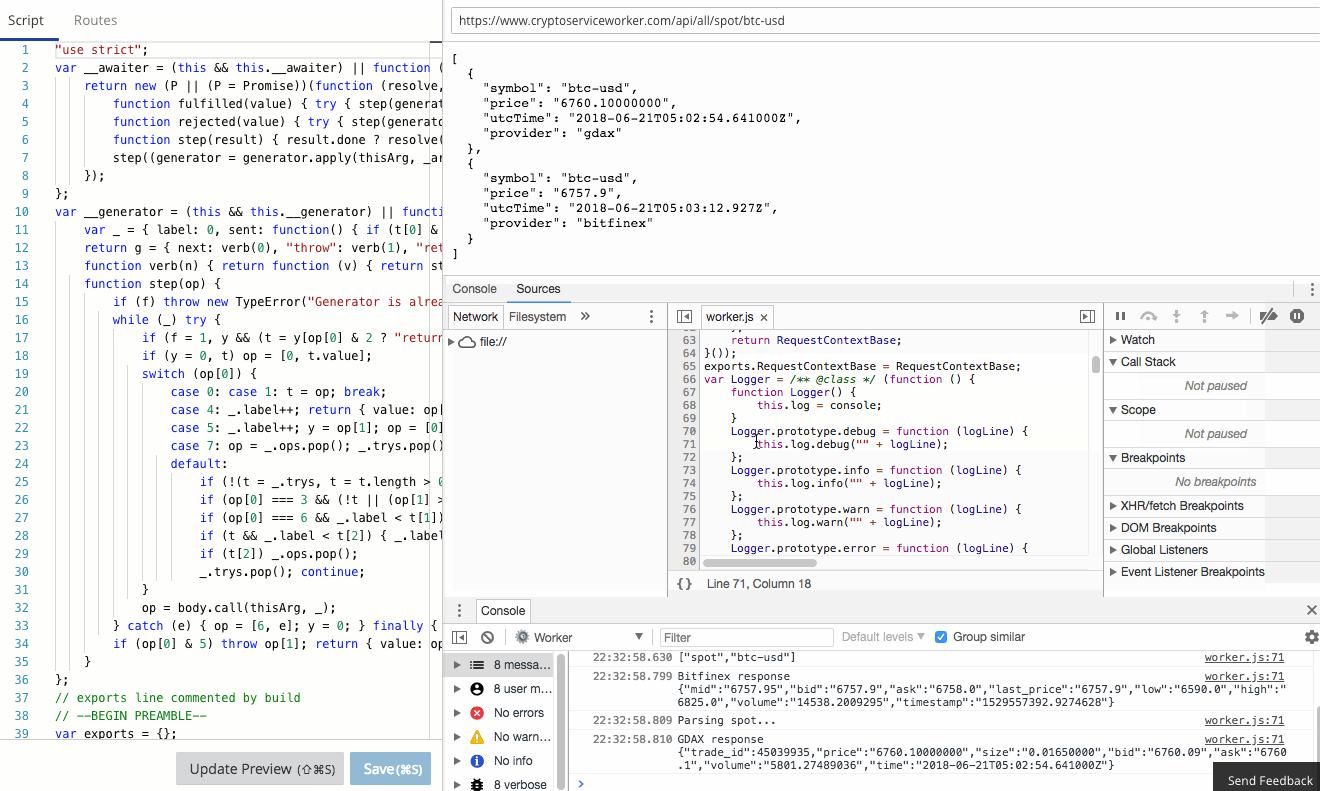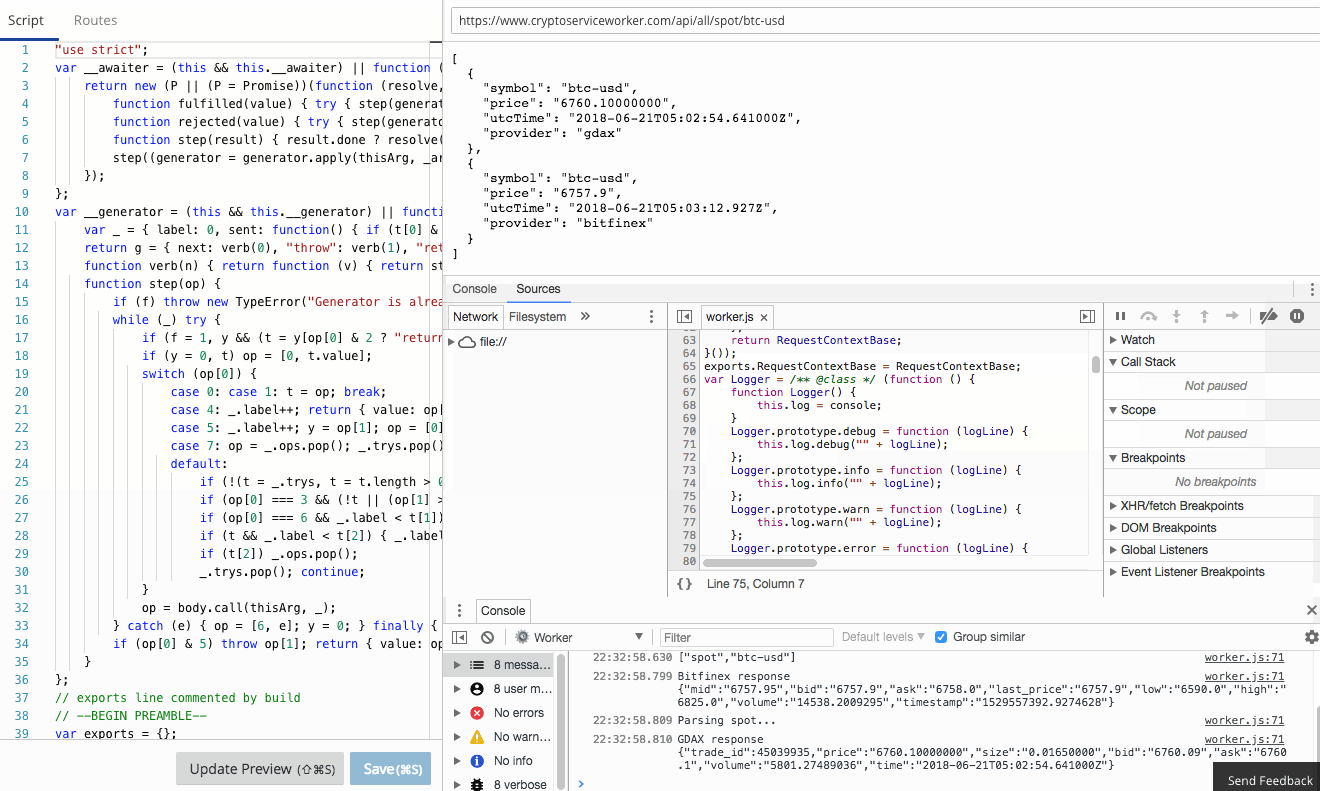
There is a comprehensive guide to common debugging approaches and I'm going to focus on returning debug information in a header. This is a great tip and one that I use to capture debug information when I'm using curl or Postman, or integration tests. It was a little finicky to get right the first time, so let me save you some trouble.
If you've followed part 1 or part 2 of my Workers series, you'll know I'm using Typescript, but the approach would equally apply to Javascript. In the rest of this example, I’ll be using the routing framework I created in part 2.
Requesting Debug Info
Feedback: Data Center Infrastructure for Networking Engineers
When I created the Data Center Infrastructure for Networking Engineers webinar, I wanted to reach these goals:
- Understand the data center acronym soup;
- Build a conceptual framework of the data center technologies and solutions.
Every now and then I get feedback from a happy attendee telling me how the webinar helped them. Here’s what I got earlier this month:
Read more ...
