Why I’m helping Cloudflare grow in Asia

I’m excited to announce that I’ve joined Cloudflare as Head of Asia. This is an important time for the company as we continue to grow our presence in the region and build on the successes we’ve already had in our Singapore office. In this new role, I’m eager to grow our brand recognition in Asia and optimize our reach to clients by building up teams and channel partners.
A little about me
I’m a Californian with more than 20 years of experience growing businesses across Asia. I initially came to Asia with the Boston Consulting Group and since then I’ve helped Google and Twitter start and grow their businesses in Singapore and Asia. In many cases throughout my career, I’ve been one of the very first employees (sometimes the first) on the ground in this part of the world. To me, the Asian market presents an often untapped opportunity for companies looking to expand, and it’s a challenge that has appealed to me throughout my career.
 This year's Chinese New Year celebration
This year's Chinese New Year celebration
Why Cloudflare?
I’m driven by opportunities to work with global businesses that drive change and are full of ambitious and passionate people. Cloudflare’s mission is to help build Continue reading
HTTPS or bust: Chrome’s plan to label sites as “Not Secure”

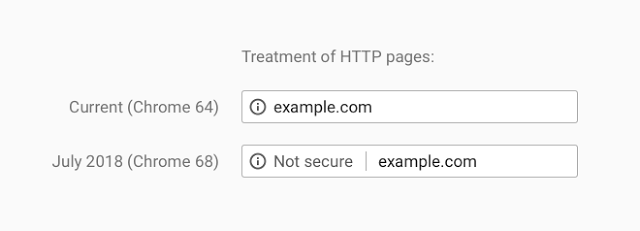
Google just announced that beginning in July 2018, with the release of Chrome 68, web pages loaded without HTTPS will be marked as “not secure”.
More than half of web visitors will soon see this warning when browsing unencrypted HTTP sites, according to data from Cloudflare’s edge that shows 56.62% of desktop requests originate from Chrome. Users presented with this warning will be less likely to interact with these sites or trust their content, so it’s imperative that site operators not yet using HTTPS have a plan to do so by July.
How did we get here (and why)?
To those who have followed the Chrome team’s public statements, this announcement comes as no surprise. Google has been gearing up for this change since 2014, as Chrome boss Parisa Tabriz tweeted and Chris Palmer memorialized in a widely distributed email. While this step is an important and potentially jarring one for users, it’s by no means the last step that Google will take to influence website administrator behavior for the better.
But why are they making this change (now)? Google’s primary motivation for driving HTTPS adoption is simple: a safe browsing experience is good for business. Users that feel Continue reading
AT&T Macro-Sizes its Microservices Supplier Program
 The carrier deployed more than 300 microservices last year.
The carrier deployed more than 300 microservices last year.
We’ve added a new GIT Fundamentals course to our library!
Log into your members account, or check out ine.com to view our latest addition to the INE video course library, GIT Fundamentals.
Why Study GIT Fundamentals:
GIT Version Control Systems are popular among many organizations, you should learn the basics now so that when faced with a GIT based project you’re able to contribute to your team quickly and efficiently.
About the Course:
This course is 3 hours and 27 minutes long and taught by Eric Parker. This is an introductory course, meant to familiarize students with the core GIT system concepts.
What You’ll Learn:
At the end of the course, students will be able to modify and commit data to both local and remote GIT repositories. Upon the completion of the course, you will be ready to start contributing to GIT based projects of your choice.
About the Instructor:
Eric Parker is a native Texan and a graduate of Texas A&M University and is more than happy to tell you all about it! He has spent the last 12+ years building software solutions in the Raleigh, NC area and has architected JAVA, .NET and JavaScript based software projects in both mid-size and enterprise level companies. He Continue reading
Indigenous Connectivity Summit Participants Share Their Stories
Madeleine Redfern, the mayor of Iqaluit – the largest and only city in Nunavut, Canada – has a colorful way of describing how sparsely populated the territory is. “The seals outnumber the people.” With a population of just over 35,000 people spread out over an arctic 1,750,000 square kilometers, Internet access is a challenge. In fact, according to Redfern, her most favorited tweet was that she couldn’t tweet… because the connection was too slow.
Madeleine Redfern participated in the first ever Indigenous Connectivity Summit last November. She and other participants shared their experience and expertise to help close the connectivity gap in Indigenous communities. Many also sat down for brief interviews with the 1st-Mile Institute, a New Mexico nonprofit that has initiated a local “Broadband for All” program. The videos are now available to watch on the 1st-Mile Institute’s website.
You can also find the videos on the Internet Society’s Indigenet page, which includes resources from the Summit including the presentations, the policy brief Spectrum Approaches for Community Networks, and other ways to get involved!
The post Indigenous Connectivity Summit Participants Share Their Stories appeared first on Internet Society.
HPE Leads Data Center Server Market, IHS Says
 Enterprises continue to be the biggest server buyers — for now.
Enterprises continue to be the biggest server buyers — for now.
The DNS Negative Cache
Considering the DNS query chain—
- A host queries a local recursive server to find out about
banana.example - The server queries the root server, then recursively the authoritative server, looking for this domain name
banana.exampledoes not exist
There are two possible responses in this chain of queries, actually. .example might not exist at all. In this case, the root server will return a server not found error. On the other hand, .example might exist, but banana.example might not exist; in this case, the authoritative server is going to return an NXDOMAIN record indicating the subdomain does not exist.
Assume another hosts, a few moments later, also queries for banana.example. Should the recursive server request the same information all over again for this second query? It will unless it caches the failure of the first query—this is the negative cache. This negative cache reduces load on the overall system, but it can also be considered a bug.
Take, for instance, the case where you set up a new server, assign it banana.example, jump to a host and try to connect to the new server before the new DNS information has been propagated through the system. On Continue reading
Verizon to Use KSI Blockchain Technology Developed for Estonia
 Verizon is planning to offer blockchain services for enterprises.
Verizon is planning to offer blockchain services for enterprises.
AI and Rules Drive Deepfence App-Focused Container Security
 The company's approach is to diffuse an attack before it explodes.
The company's approach is to diffuse an attack before it explodes.
Cradlepoint Brings SD-WAN to LTE Networks for First Responders, Fleets
 The modem supports two concurrent LTE connections from two different operators.
The modem supports two concurrent LTE connections from two different operators.
Dell EMC Lets Enterprises Mix and Match Storage with Cisco Compute
 The converged infrastructure offers pooled resources and greater scalability.
The converged infrastructure offers pooled resources and greater scalability.
Full Stack Journey 018: Istio, Envoy & Service Meshes
Today's Full Stack Journey dives into Istio, Envoy & service meshes with guest Shannon McFarland.Full Stack Journey 018: Istio, Envoy & Service Meshes
Today's Full Stack Journey dives into Istio, Envoy & service meshes with guest Shannon McFarland.
The post Full Stack Journey 018: Istio, Envoy & Service Meshes appeared first on Packet Pushers.
Address 5G Traffic Growth with Dell EMC and VMware
 A new solution brief from Dell EMC and VMware discusses an innovative turnkey solution—Dell EMC NFV Ready Bundle for VMware—that is optimized to simplify and accelerate production deployments.
A new solution brief from Dell EMC and VMware discusses an innovative turnkey solution—Dell EMC NFV Ready Bundle for VMware—that is optimized to simplify and accelerate production deployments.
Cloud Security Alliance Puts ERP Applications in its Crosshairs
 Future CSA papers will address SAP and Oracle ERP security.
Future CSA papers will address SAP and Oracle ERP security.
CommScope Virtualizes the Baseband Radio for In-Building Wireless
 This means it can add capacity without having to physically move hardware.
This means it can add capacity without having to physically move hardware.