AT&T Makes its SD-WAN ‘Dynamic’
 The operator architected its SD-WAN through the AT&T Integrated Cloud (AIC).
The operator architected its SD-WAN through the AT&T Integrated Cloud (AIC).
Is There a Future for Blockchain-Enabled SD-WAN?
 The combination could mitigate the audit and regulatory risk involved in each transaction.
The combination could mitigate the audit and regulatory risk involved in each transaction.
Dell EMC’s Jeffrey Baher on the Past, Present and Future for Open Networking
 Dell EMC recently expanded its Open Networking initiative, which focuses on abstracting and decoupling hardware and software networking elements, beyond the data center core. The goal is to enable an end-to-end, software-defined architecture, where mix-and-match software from innovative third-parties can run on agnostic hardware to help service provider and enterprise customers accelerate their digital transformation initiatives,... Read more →
Dell EMC recently expanded its Open Networking initiative, which focuses on abstracting and decoupling hardware and software networking elements, beyond the data center core. The goal is to enable an end-to-end, software-defined architecture, where mix-and-match software from innovative third-parties can run on agnostic hardware to help service provider and enterprise customers accelerate their digital transformation initiatives,... Read more →
The 2017 APM/NPM Report Survey is Here!
 Take survey and enter to win one of two $300 Gift Cards redeemable at various retailers including Amazon, Target, Visa Virtual Card, etc.
Take survey and enter to win one of two $300 Gift Cards redeemable at various retailers including Amazon, Target, Visa Virtual Card, etc.
Versa Optimizes SD-WAN Voice and Video from User’s Perspective
 Versa wants to bring SD-WAN value up the stack.
Versa wants to bring SD-WAN value up the stack.
How To Access Devices with Unsupported SSL Ciphers
With the HeartBleed bug effectively killing off SSLv3 and vulnerabilities in cipher block chaining ruling out another whole swathe of SSL ciphers, network engineers may have found themselves trying to connect to a device and either getting no response (Safari), or getting a response like this (Chrome):
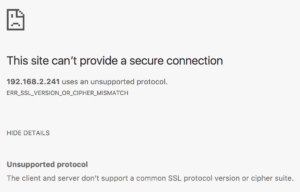
Or this (Firefox):
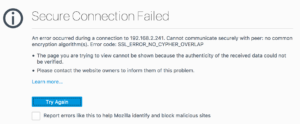
Once upon a time, it was possible to go into settings and enable the old, insecure ciphers again, but in more recent updates, those ciphers no longer exist within the code and are thus inaccessible. So what to do? My answer was to try a proxy.
Charles Proxy
The first proxy I looked at seemed promising. Although not free, Charles Proxy offers a 30 day free trial, and that seemed like a good thing to try. It’s limited additionally by only running for 30 minutes at a time before it has to be reloaded, but for my testing purposes that was not a problem.
During installation I declined to give Charles Proxy permission to configure the system proxy settings. Instead, I manually updated just my Firefox browser to use the proxy which was now listening on port 127.0.0.1:8888. Since I was making an SSL connection, I also Continue reading
The Super Secret Cloudflare Master Plan, or why we acquired Neumob

We announced today that Cloudflare has acquired Neumob. Neumob’s team built exceptional technology to speed up mobile apps, reduce errors on challenging mobile networks, and increase conversions. Cloudflare will integrate the Neumob technology with our global network to give Neumob truly global reach.
It’s tempting to think of the Neumob acquisition as a point product added to the Cloudflare portfolio. But it actually represents a key part of a long term “Super Secret Cloudflare Master Plan”.
 CC BY 2.0 image by Neil Rickards
CC BY 2.0 image by Neil Rickards
Over the last few years Cloudflare has been building a large network of data centers across the world to help fulfill our mission of helping to build a better Internet. These data centers all run an identical software stack that implements Cloudflare’s cache, DNS, DDoS, WAF, load balancing, rate limiting, etc.
We’re now at 118 data centers in 58 countries and are continuing to expand with a goal of being as close to end users as possible worldwide.
The data centers are tied together by secure connections which are optimized using our Argo smart routing capability. Our Quicksilver technology enables us to update and modify the settings and software running across this vast network in seconds.
Deploy360 at IETF 100, Day 3: SIDR, TLS & Crypto
This week is IETF 100 in Singapore, and we’re bringing you daily blog posts highlighting some of the topics that Deploy360 is interested in. After the focus on IPv6 & IoT during the first couple of days, we’re switching tack today with a focus on routing and crypto matters.
We’re having to wait until after lunch, but then there’s a choice of UTA, SIDROPS or ROLL at 13.30 SGT/UTC+8.
UTA will be focusing on resolving the final IESG comments on the use of TLS for email submission and access which outlines current recommendations for using TLS to provide confidentiality of email traffic between a mail user agent and a mail access server. Next up for discussion are the open issues on a draft related to Strict Transport Security (STS) for mail (SMTP) transfer agents and mail user agents, before consideration of a draft on an option to require TLS for SMTP.
NOTE: If you are unable to attend IETF 100 in person, there are multiple ways to participate remotely.
Over in SIDROPS, there will be a review of the status of BGP Origin Validation deployment in RENATA: the Columbia National Research and Education Network. This represents the first wide-scale deployment Continue reading
Nifty and Nerdy: 10 Holiday Gifts for IT Pros
Stuck on what to get your favorite tech-loving geek? Here are some ideas.