Preview: Networking Field Day Exclusive with Aruba (HPE) – The 8400 core switch
Back to Silicon Valley!
As a network type, it’s hard not to be excited when heading to a Networking Field Day event. I joined then NFD club by attending NFD14 and have been hooked ever since.
Not only is it an honor and a privilege to be invited to an NFD event, the personal relationships that are forged in the larger TFD community are some of the most valuable I’ve ever had in my career.
This go around we’ll be visiting Aruba (A Hewlett Packard Enterprise Company) in Santa Clara to deep dive on the newest addition to the Aruba product line – the 8400 core switch.
A new face in campus town – the Aruba 8400
It’s been a while since anything exciting happened in the world of campus networking. It’s a steady segment for most vendors but nothing disruptive has really happened in the last few years.
And that’s not incredibly surprising. For better or worse, as long as campus networks aren’t broken in most enterprises, they are often neglected in favor of the data center and cloudy pursuits.
Aruba is touting the 8400 to increase automation and visibility in the campus core – both are areas Continue reading
Preview: Networking Field Day Exclusive with Aruba (HPE) – The 8400 core switch
Back to Silicon Valley!
As a network type, it’s hard not to be excited when heading to a Networking Field Day event. I joined then NFD club by attending NFD14 and have been hooked ever since.
Not only is it an honor and a privilege to be invited to an NFD event, the personal relationships that are forged in the larger TFD community are some of the most valuable I’ve ever had in my career.
This go around we’ll be visiting Aruba (A Hewlett Packard Enterprise Company) in Santa Clara to deep dive on the newest addition to the Aruba product line – the 8400 core switch.
A new face in campus town – the Aruba 8400
It’s been a while since anything exciting happened in the world of campus networking. It’s a steady segment for most vendors but nothing disruptive has really happened in the last few years.
And that’s not incredibly surprising. For better or worse, as long as campus networks aren’t broken in most enterprises, they are often neglected in favor of the data center and cloudy pursuits.
Aruba is touting the 8400 to increase automation and visibility in the campus core – both are areas Continue reading
Elevators Vs. Networks: Applying Predictive Analytics
Could predictive analytics help foresee network failures?
Container Networking Challenges the Focus of Tigera Calico Update
 Enterprises looking to deploy containers are struggling with connectivity challenges.
Enterprises looking to deploy containers are struggling with connectivity challenges.
Worth Reading: Ageism in technology
The post Worth Reading: Ageism in technology appeared first on rule 11 reader.
Home Automation Setup with Apple #HomeKit
As many of you know, I’ve been diving into the home automation pond for awhile now. I’ve been asked to blog out my current home setup and this is an attempt to do that. There’s MUCH too much to be put into a single post, which is why I started a new blog for this subject over at www.homekitgeek.com as well as doing some video reviews of different HomeKit accessories. Work in process, but I’ll do the short version here.
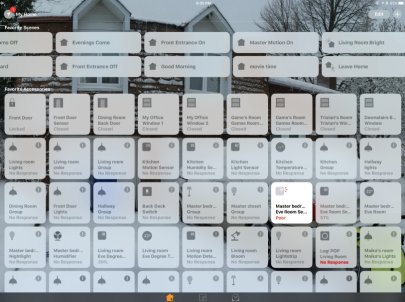
Apple HomeKit
![]()
I chose to use the Apple homeKit framework as the base for my home automation journey for a few reason. The biggest one is that I already owned a couple of Apple TV (gen4) devices which fit the home automation hub role. These devices are a homeKit hub and are the always-on/always-present devices that are used to perform orchestration/automation actions when I’m home or away. These also tie directly into Apple’s iCloud which allows me remote access to my homeKit gear without having to VPN into my home network.
Home Setup Room-By-Room
There’s a lot to talk about here, but I thought I would just do a quick description of what’s going on room-by-room Continue reading
Equinix Adds Direct Connection to SAP Cloud
 Equinix already offers direct connectivity to AWS, Microsoft Azure, Oracle Cloud, Google Cloud Platform, and IBM Bluemix.
Equinix already offers direct connectivity to AWS, Microsoft Azure, Oracle Cloud, Google Cloud Platform, and IBM Bluemix.
The Knowledge Mortgage
One of the common questions I get is this: I need to study to get a job, and I do not see how learning all this theory stuff is helpful. It’s time to take this line of thinking on with a look at the concept of a learning (or knowledge) mortgage.
The post The Knowledge Mortgage appeared first on rule 11 reader.
Codefresh ‘Democratizes’ Kubernetes Management for GKE
 Platform can support Kubernetes-based container deployment in 10 minutes.
Platform can support Kubernetes-based container deployment in 10 minutes.
Worth Reading: A code camps getting the boot?
The post Worth Reading: A code camps getting the boot? appeared first on rule 11 reader.
RFC 8212: Bringing Sane Defaults to EBGP
It’s amazing how long it can take to get some sanity into networking technologies. RFC 8212 specifies that a BGP router should not announce prefixes over EBGP until its routing policy has been explicitly configured. It took us only 22 years to get there…
For more technical details, read this email by Job Snijders.
Virtualization Fueling Rise of the Modern Mobile Network Operator
 What the modern MNO will need is a virtualized mobile core.
What the modern MNO will need is a virtualized mobile core.

