Cisco Port Security Basics and configurations
Lets talk about the port security and the modes of port security. So the question is why port security required, may be want to safe from the attacks as well.
Why Port Security is important ?
Well port security is generally used so that you can easily prevent the unwanted MAC address traffic from the external or the internal network.
Port security can be enabled in three different ways are defined as below:
- Protect : In the protected state, switch port will drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value.
- Restrict : In the restrict state, switch port will drops packets with unknown source addresses until you remove a sufficient number of secure MAC addresses to drop below the maximum value and causes the SecurityViolation counter to increment
- Shutdown : In the shutdown state, switch port will Continue reading
Bosh or Kubo? Tools for Deploying Containers Are Proliferating
 The IT industry has a selection of tools for deploying containers. They can use a PaaS or a CaaS based on Kubernetes, Marathon, or Docker.
The IT industry has a selection of tools for deploying containers. They can use a PaaS or a CaaS based on Kubernetes, Marathon, or Docker.
Broadcom Trident 3 Telemetry
Seems like everyone is building telemetry applications that look pretty much the same.
The post Broadcom Trident 3 Telemetry appeared first on EtherealMind.
Network Break 140: Broadcom Announces Trident 3; Nokia Launches New Network Processors
From new Broadcom ASICs to Nokia network processors to a Mellanox & HPE deal, Network Break analyzes the latest tech news to keep you up to speed. The post Network Break 140: Broadcom Announces Trident 3; Nokia Launches New Network Processors appeared first on Packet Pushers.My Cisco Live 2017 Schedule
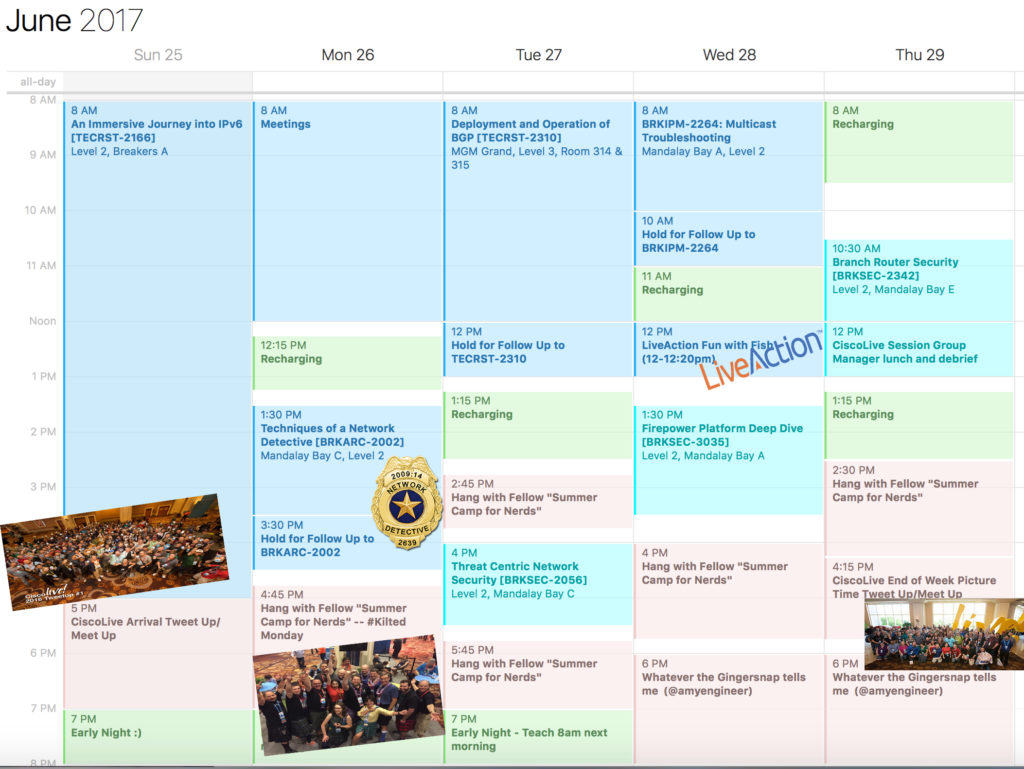
It is that time once again. CiscoLive 2017 – Summer Camp for Geeks! This will be my 15th CiscoLive/Networkers. What is my absolute #1 suggestion to anyone going to a CiscoLive event? Easy – “Begin with the End in Mind“. Know what your priorities are and then schedule your week accordingly.
So… here you go. My CiscoLive (CLUS) priorities and schedule for the week.
- Teach
- Recharge
- Learn
- Play and Have Fun
VMware NSX Achieves Common Criteria EAL 2+ Certification
VMware NSX 6.3 for vSphere has achieved Common Criteria certification at the Evaluation Assurance Level (EAL) 2+ (view the certification report)(view the press release). This marks yet another milestone of our commitment to providing industry leading certified solutions for customers from federal departments and agencies, international governments and agencies, and other highly regulated industries and sectors. Along with FIPS, DISA-STIG, ICSA Labs firewall certification, and several other independent evaluations, the Common Criteria compliance accreditation validates NSX as a reliable network virtualization platform that satisfies stringent government security standards.
Common Criteria is an international set of guidelines (ISO-15408) that provides a methodology framework for evaluating security features and capabilities of Information Technology (IT) security products. It is mutually recognized by 26 member nations.
Regulatory compliance is one of the challenges faced by government IT departments in their efforts to modernize legacy systems, and Common Criteria is often required for procurement sales. The Common Criteria accreditation affirms that NSX for vSphere complies with the security requirements specified within the designated level and simplifies the introduction of NSX into government and highly regulated environments. NSX enables customers in the public sector to implement network Continue reading
High-Performing IT Teams: 7 Winning Traits
A new study finds that successful IT teams are more likely to use certain management practices and technologies.
Brian Gracely on Containers in the Enterprise
Hear how containers are moving into the enterprise, the challenges of putting them into production, and the best ways to learn about container technologies. Brian Gracely is director of product strategy for Red Hat OpenShift and co-host of The Cloudcast and The ServerlessCast.