Progressive Dutch Municipality Protects Citizen Data and Meets Compliance with VMware NSX
 Summary: Municipality of Zoetermeer implements Zero-Trust model with VMware NSX-enabled micro-segmentation for advanced security inside data centers. Zoetermeer follows the Dutch BIG (Baseline Information Security Dutch Municipalities) regulations Zoetermeer is a modern, fast-growing municipality in the province of South Holland. It provides local services such as water supply, sewage and garbage disposal to around 125,000... Read more →
Summary: Municipality of Zoetermeer implements Zero-Trust model with VMware NSX-enabled micro-segmentation for advanced security inside data centers. Zoetermeer follows the Dutch BIG (Baseline Information Security Dutch Municipalities) regulations Zoetermeer is a modern, fast-growing municipality in the province of South Holland. It provides local services such as water supply, sewage and garbage disposal to around 125,000... Read more →
Technology Short Take #83
Welcome to Technology Short Take #83! This is a slightly shorter TST than usual, which might be a nice break from the typical information overload. In any case, enjoy!
Networking
- I enjoyed Dave McCrory’s series on the future of the network (see part 1, part 2, part 3, and part 4—part 5 hadn’t gone live yet when I published this). In my humble opinion, he’s spot on in his viewpoint that network equipment is increasingly becoming more like servers, so why not embed services and functions in the network equipment? However, this isn’t enough; you also need a strong control plane to help manage and coordinate these services. Perhaps Istio will help provide that control plane, though I suspect something more will be needed.
- Michael Kashin has a handy little tool that functions like
ssh-copy-idon servers, but for network devices (leveraging Netmiko). Check out the GitHub repository. - Anthony Shaw has a good comparison of Ansible, StackStorm, and Salt (with a particular view at applicability in a networking context). This one is definitely worth a read, in my opinion.
- Miguel Gómez of Telefónica Engineering discusses maximizing performance in VXLAN overlay networks.
- Nicolas Michel has a good Continue reading
Technology Short Take #83
Welcome to Technology Short Take #83! This is a slightly shorter TST than usual, which might be a nice break from the typical information overload. In any case, enjoy!
Networking
- I enjoyed Dave McCrory’s series on the future of the network (see part 1, part 2, part 3, and part 4—part 5 hadn’t gone live yet when I published this). In my humble opinion, he’s spot on in his viewpoint that network equipment is increasingly becoming more like servers, so why not embed services and functions in the network equipment? However, this isn’t enough; you also need a strong control plane to help manage and coordinate these services. Perhaps Istio will help provide that control plane, though I suspect something more will be needed.
- Michael Kashin has a handy little tool that functions like
ssh-copy-idon servers, but for network devices (leveraging Netmiko). Check out the GitHub repository. - Anthony Shaw has a good comparison of Ansible, StackStorm, and Salt (with a particular view at applicability in a networking context). This one is definitely worth a read, in my opinion.
- Miguel Gómez of Telefónica Engineering discusses maximizing performance in VXLAN overlay networks.
- Nicolas Michel has a good Continue reading
Sprint Builds its 5G Clout Through Open Source, NYU Affiliation
 “We need network architects to think like software architects.”
“We need network architects to think like software architects.”
Cloudera’s PaaS Targets Big Data Workloads Running in the Cloud
 The service is available on AWS and will soon expand to other public clouds.
The service is available on AWS and will soon expand to other public clouds.
CCNA Wireless – CCNA Wireless Notes Chapter 2
ITU-R
A telecommunications regulatory body that regulates or decides how different parts of the RF spectrum may be used. Countries can also have own regulatory bodies that regulate the spectrum within the country. Maintains spectrum in three different regions:
Region 1: Europe, Africa, Northern Asia
Region 2: North and South America
Region 3: Southern Asia and Australiasa
Most bands in the RF spectrum are tightly regulated and require a license. Using a frequency in a licensed range requires an organization to submit an application to the regulatory body.
ITU-R allocated two two ranges for Industrial, Scientific and Medical (ISM) use:
2.400 to 2500 GHz
5.725 to 5.825 GHz
ISM bands are unlicensed and anyone can use them.
Unlicensed bands are more vulnerable to interference and noise due to them being more accessible.
FCC
Federal Communications Commission (FCC) regulates RF frequencies, channels and transmission power within the US but other countries may also follow the rules of the FCC. FCC has allocated Unlicensed National Information Infrastructure (U-NII) in addition to the ISM band. Consists of four bands in the 5 GHz band.
U-NII-1 5.15 to 5.25 GHz
U-NII-2 5.25 to 5.35 GHz
U-NII-2 Extended Continue reading
Worth Reading: Who controls the Internet?
The post Worth Reading: Who controls the Internet? appeared first on rule 11 reader.
Rackspace Acquires TriCore Solutions, Names Eazor as CEO
 Its new CEO comes from EarthLink, where he led the company's acquisition by Windstream.
Its new CEO comes from EarthLink, where he led the company's acquisition by Windstream.
DDN Hires Intel Storage Guru for New CTO Position
 The move reflects the growing demand for software-defined storage.
The move reflects the growing demand for software-defined storage.
Less Is More – Why The IPv6 Switch Is Missing
At Cloudflare we believe in being good to the Internet and good to our customers. By moving on from the legacy world of IPv4-only to the modern-day world where IPv4 and IPv6 are treated equally, we believe we are doing exactly that.
"No matter what happens in life, be good to people. Being good to people is a wonderful legacy to leave behind." - Taylor Swift (whose website has been IPv6 enabled for many many years)
Starting today with free domains, IPv6 is no longer something you can toggle on and off, it’s always just on.
How we got here
Cloudflare has always been a gateway for visitors on IPv6 connections to access sites and applications hosted on legacy IPv4-only infrastructure. Connections to Cloudflare are terminated on either IP version and then proxied to the backend over whichever IP version the backend infrastructure can accept.
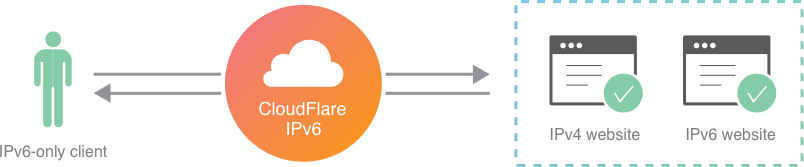
That means that a v6-only mobile phone (looking at you, T-Mobile users) can establish a clean path to any site or mobile app behind Cloudflare instead of doing an expensive 464XLAT protocol translation as part of the connection (shaving milliseconds and conserving very precious battery life).
That IPv6 gateway is set by a simple Continue reading