Reflections on reflection (attacks)
Recently Akamai published an article about CLDAP reflection attacks. This got us thinking. We saw attacks from Conectionless LDAP servers back in November 2016 but totally ignored them because our systems were automatically dropping the attack traffic without any impact.
We decided to take a second look through our logs and share some statistics about reflection attacks we see regularly. In this blog post, I'll describe popular reflection attacks, explain how to defend against them and why Cloudflare and our customers are immune to most of them.
A recipe for reflection
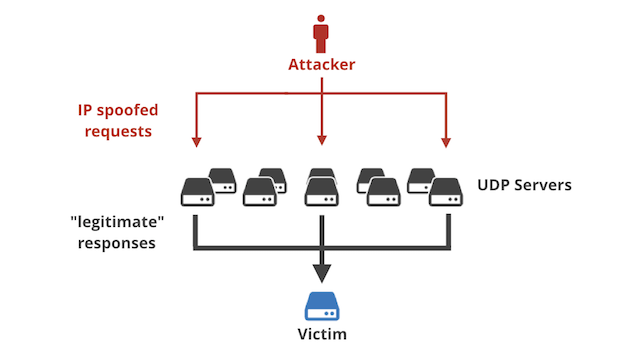
Let's start with a brief reminder on how reflection attacks (often called "amplification attacks") work.
To bake a reflection attack, the villain needs four ingredients:
- A server capable of performing IP address spoofing.
- A protocol vulnerable to reflection/amplification. Any badly designed UDP-based request-response protocol will do.
- A list of "reflectors": servers that support the vulnerable protocol.
- A victim IP address.
The general idea:
- The villain sends fake UDP requests.
- The source IP address in these packets is spoofed: the attacker sticks the victim's IP address in the source IP address field, not their own IP address as they normally would.
- Each packet Continue reading
Speed, Power, Performance: NSX & Memorial Day Motorsports
With Memorial Day weekend coming up, for me, it’s all about hot dogs, hamburgers, and fast car racing. I am huge Formula 1 fanatic, but Memorial Day is a bonanza of racing from the F1 Monaco Grand Prix, to NASCAR’s Coke 600, and of course the Indianapolis 500 all on the same day! The raw speed and performance of these races remind me of a 2016 VMworld presentation (NET8030) on NSX performance.
The argument still comes up now and again that “hardware is faster than software.” Network guys like me just assume that’s true. So, it came as a surprise to me when I watched the session which turned that assumption on its head. In this session, the presenter demonstrated that software is faster than hardware, way faster. Of course, I was dubious at first but quickly learned that physical networking and virtual networking is like the difference between the pace car and the race car. I always assumed the physical switch was the race car, but in the throughput presentation, Samuel showed two VM’s running on the same host with NSX routing, switching, and firewalling between them could get up to 106G! This information surprised me. Sort of like the same experience I had Continue reading
Linux Foundation Grows So Much it Hires a Chief of Staff
 Sheryl Chamberlain hails from the consulting company Capgemini.
Sheryl Chamberlain hails from the consulting company Capgemini.
Reading List: WannaCry and Ransomware
A good bit has been written about the recent WannaCry outbreak over the last few weeks; rather than stringing the best out through Worth Reading posts, I have collected the three best posts on the topic here.
Over the weekend a cyber attack known as “WannaCry” infected hundreds of computers all over the world with ransomware (malware which encrypts your data until you pay a ransom, usually in Bitcoin). The attack takes advantage of an exploit for Windows known as “EternalBlue” which was in the possession of NSA and, in mid April, was made public by a group known as “The Shadow Brokers.” Microsoft issued a patch for the vulnerability on March 14 for all supported versions of Windows (Vista and Continue reading
New Relic Taps Further Into AWS For Performance Insight
 The goal is to provide a single place to see the health of all applications.
The goal is to provide a single place to see the health of all applications.
Cisco Jumps On IoT Security Train with IoT Threat Defense
 It's a bunch of existing security services and software bundled together to target IoT security.
It's a bunch of existing security services and software bundled together to target IoT security.
Help Shape the Future of the Internet
This year, the Internet Society celebrates its 25th anniversary. Our own history is inextricably tied to the history of the Internet. We were founded in 1992 by Internet pioneers who believed that “a society would emerge from the idea that is the Internet” – and they were right.
As part of the celebration, this September we will launch a comprehensive report that details the key forces that could impact the future of the Internet. The report will also offer recommendations for the Future and we need your input.
Masergy Brews Its Own Complementary SD-WAN Technology In-House
 SD-WAN Go will complement Silver Peak's SD-WAN offering sold by Masergy.
SD-WAN Go will complement Silver Peak's SD-WAN offering sold by Masergy.
Datanauts 085: Understanding In-Memory Databases
Todays Datanauts podcast explores the architecture and design challenges of running distributed in-memory databases. Our guests are Swapnil Bawaskar and Jim Bedenbaugh from Pivotal. The post Datanauts 085: Understanding In-Memory Databases appeared first on Packet Pushers.Worth Reading: The Embiggening Bite of GPUs
The post Worth Reading: The Embiggening Bite of GPUs appeared first on rule 11 reader.
SecurityTarget Data Breach Lawsuits Are Settled | Fortune.com
Target gets out of its security breach quite cheaply I think.
The post SecurityTarget Data Breach Lawsuits Are Settled | Fortune.com appeared first on EtherealMind.
Calix Uses SDN Platform in Channel Bonding Trial for Verizon
 In-house trial delivered 80 Gb/s aggregate bandwidth over a single fiber strand.
In-house trial delivered 80 Gb/s aggregate bandwidth over a single fiber strand.
