Dell EMC Ethernet Switching Update
I’m at the Dell EMC World 2017 conference in Las Vegas this week, and I’ve been enjoying catching up on what the network group has been up to. In my previous experience, the legacy Dell Networking products have unfortunately been seen as those things that get thrown in when you buy a rack of servers
. In other words, they lacked credibility or worse, the rack would come with another vendor’s switches in them, reinforcing the idea that Dell’s own products weren’t up to the job.

It’s my belief though, that two things in recent years have dramatically changed that perspective. The first is Dell EMC’s OS10, a modular network operating system which by all accounts is actually pretty capable. Previous OS incarnations were of varying quality, as has been the case with many vendor-branded switches, and with the release of OS10, Dell Networks (as it was at the time) put a stake in the ground and showed that they wanted things to be different.
The second element is disaggregation. Dell identified the opportunity to use what was becoming ubiquitous merchant silicon like the Broadcom Trident II chipset to be able to play at the exact same level as everybody Continue reading
Worth Reading: Cherry picker
The post Worth Reading: Cherry picker appeared first on rule 11 reader.
3 Ways Organizations Use NSX for Application Continuity
Five example customers using NSX to enable application continuity for their business
No one looks forward to data center outages. Not the business leaders who fear revenue loss from applications being down, nor the heroic IT admin whose pager is going off at 3:00 AM. Therefore many critical data centers have a sister location and some form of a disaster recovery plan, should something go awry. At the same time, infrastructure teams are under pressure to be more agile and more responsive to the business, across the board, while still lowering costs and making the most out of what they already have. So what exactly happens in the case of a disaster?
The Ponemon Institute reports the average cost of a data center outage to be $740,357, but with massive variance – some known examples going up to $150 million. As businesses move to accelerate to keep up with changes in their industry, each minute lost to downtime can have an impact not only on company resources but also on brand reputation. This is why enabling business continuity or application continuity in a manner that doesn’t require new infrastructure is vital. VMware NSX can offer companies a competitive edge through networking and security Continue reading
Verizon Sees SDN as a Pillar of Network Streamlining, Cost Reduction
 Management cites ability to lower bit delivery costs.
Management cites ability to lower bit delivery costs.
Ericsson’s Dynamic Orchestration Helps Operators With VNF Support
 Verizon is already using the orchestrator.
Verizon is already using the orchestrator.
Dell EMC Software-Defined Storage Aims to Modernize Enterprise Data Centers
 This includes a new SDS solution for storing and analyzing streaming IoT data.
This includes a new SDS solution for storing and analyzing streaming IoT data.
eBay’s OpenStack Cloud Manages 167,000 Virtual Machines
 EBay is deploying Docker containers on OpenStack.
EBay is deploying Docker containers on OpenStack.
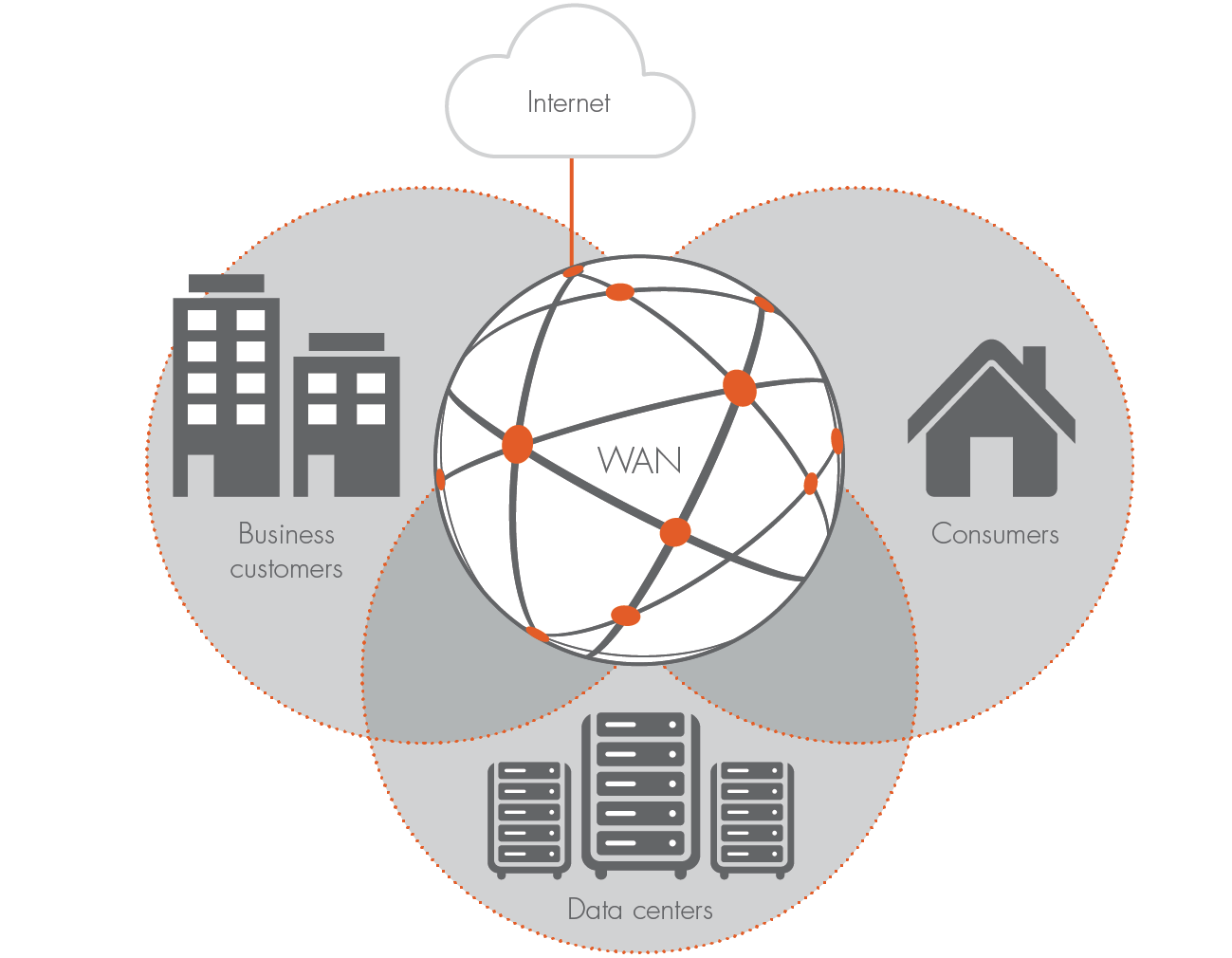
Time to Overhaul Your Campus Network
Over the last few years cloud service providers have steadily adopted white-box Ethernet switches and modern, flexible Network Operating Systems into their ecosystems. Mega data center operators, such as Google, Amazon, and Microsoft, have replaced their proprietary gear with white boxes in their production environments. The major benefit of this paradigm shift is significantly reduced CapEx and OpEx, a more reliable environment, and customized traffic flows for efficiency. According to IDC, the worldwide ODM direct Ethernet switch (white box) market was $677 million in 2016 and is expected to exceed $900 million in 2017. That’s a growth rate of 33%, and the trend is accelerating.
The shift in white-box adoption started as early as 2012, but has been limited to data centers for many reasons. Even though Enterprise IT executives are motivated to adopt white-boxes, the migration has been slow and challenging. Essentially, the Enterprise network is distinctly different from data center network in many ways.
- The data center network is usually homogeneous, while the Enterprise network is heterogeneous. Typically, Enterprises require a variety of speeds ranging from 100Mbps to 100Gbps, and run over different cables, including various types of copper and fiber. The increasingly deployed Power over Ethernet (PoE) Continue reading
Silver Peak CEO: SD-WAN Pure-Plays are Hot Acquisition Targets
 Legacy players will want to complement their own tech through pure-play SD-WAN acquisitions.
Legacy players will want to complement their own tech through pure-play SD-WAN acquisitions.
JNCIE-DC : The Awesome story of Joao
Hello, I'm very proud to post the story of Joao. He passed recently JNCIE-DC and became one of the firsts JNCIE x4. Joao is a "Juniper Fan" like me. I'm currently preparing JNCIE-DC as well, so I was so happy to read his experience. Enjoy Reading. David...JNCIE-DC : The Awesome story of Joao
Hello, I'm very proud to post the story of Joao. He passed recently JNCIE-DC and became one of the firsts JNCIE x4. Joao is a "Juniper Fan" like me. I'm currently preparing JNCIE-DC as well, so I was so happy to read his experience. Enjoy Reading. David...JNCIE-DC : The Awesome story of Joao
Hello, I'm very proud to post the story of Joao. He passed recently JNCIE-DC and became one of the firsts JNCIE x4. Joao is a "Juniper Fan" like me. I'm currently preparing JNCIE-DC as well, so I was so happy to read his experience. Enjoy Reading. David...Troubleshooting: Models
How well can you know each of these four systems? Can you actually know them in fine detail, down to the last packet transmitted and the last bit in each packet? Can you know the flow of every packet through the network, and every piece of information any particular application pushes into a packet, or the complete set of ever changing business requirements?
Obviously the answer to these questions is no. As these four components of the network combine, they create a system that suffers from combinatorial explosion. There are far too many combinations, and far too many possible states, for any one person to actually know all of them.
How can you reduce the amount of information to some amount a reasonable human can keep in their minds? The answer—as it is with most problems related to having too much information—is abstraction. In turn, what does abstraction really mean? It really means you build a model of the system, interacting with the system through the model, rather than trying to keep all the information about every subsystem, and how the subsystems interact, in your head. So for each subsystem of the entire system, you have a model you are Continue reading