Research: The Security Impact of HTTPS Interception
The use of TLS interception by outbound proxy servers is causing serious problems in updating the TLS standard to Version 1.3.
At the same time, middlebox and antivirus products increasingly intercept (i.e., terminate and re-initiate) HTTPS connections in an attempt to detect and block malicious content that uses the protocol to avoid inspection . Previous work has found that some specific HTTPS interception products dramatically reduce connection security ; however, the broader security impact of such interception remains unclear. In this paper, we conduct the first comprehensive study of HTTPS interception in the wild, quantifying both its prevalence in traffic to major services and its effects on real-world security.
This is the same problem that middleboxes cause anywhere on the Internet – Firewalls, NAT gateways, Inspection, QOS, DPI. Because these complex devices are rarely updated and hard to maintain, they create failures in new protocols. IPv6 rollout has been slowed by difficult upgrades. The same problem is happening with TLS. Its undesirable to fall back to insecure TLS standards that “work” but are insecure.
The EtherealMind View
The business need for proxy servers or protocol interception is for a small range of activities
- Scan Internet content for malware Continue reading
What is happy eyeballs ?
What is happy eyeballs ? This term is very important to understand if you are deploying dual stack IPv6 network. Before defining happy eyeballs, do you know what is an eyeball network ? Where is it used ? Where does ‘ happy eyeballs ‘ term come from ? Eyeball is an end […]
The post What is happy eyeballs ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
NFV/SDN: Reality, Challenges and Guidance
 There are questions that could derail the benefits of NFV/SDN that haven't been addressed.
There are questions that could derail the benefits of NFV/SDN that haven't been addressed.
Worth Reading: Botnets in the Cloud
The post Worth Reading: Botnets in the Cloud appeared first on 'net work.
Gap Weaves a Global SD-WAN Strategy
 Gap is using Viptela's platform for its SD-WAN.
Gap is using Viptela's platform for its SD-WAN.
Deadline 3 May: Recognize an outstanding technologist
Do you know someone who has made an outstanding contribution to the development of the Internet?
We are pleased to announce that candidate nominations for the 2017 Jonathan B. Postel Service Award are open.
This annual award is presented to an individual or organization that has made outstanding contributions in service to data communications and places particular emphasis on those who have supported and enabled others.
Nominations are encouraged for individuals or teams of individuals from across the data communications industry around the world who are dedicated to the efforts of advancing the Internet for the benefit of everybody.
Ixia Updates CloudLens for Public Cloud Visibility
 CloudLens is available on AWS, and Azure is coming soon.
CloudLens is available on AWS, and Azure is coming soon.
MicroSegmentation of Applications using Application Rule Manager
“Micro-Segmentation provides a way to build a zero-trust network – where all networks, perimeters and application are inherently untrusted.” – declared Forrester Consulting in 2015 with their white paper Leveraging Micro-Segmentation to build zero-trust model. The last mile in creating a truly zero-trust network implies not trusting each application and also tiers within an application (Figure 1). To complete the last mile, network, security and risk professionals are increasingly looking for tools to understand application communication patterns and providing access controls to them. With version 6.3.0, NSX has unveiled 2 new tools, namely, Application Rule Manager (ARM) and Endpoint Monitoring (EM), to help professionals understand application patterns.
 Figure 1: Zero-Trust Model using NSX
Figure 1: Zero-Trust Model using NSX
From Theory to Practice
Micro-Segmenting each application requires understanding of application communication patterns. Users should allow the flows required by the application. To accomplish zero-trust, users should be closing all unwanted flows & ports. Figure 2., is a sample practical firewall policy model to achieve that. In this model, ARM/EM provides application patterns and a one-click conversion of those patterns into distributed firewall rules to achieve inter/intra application rules.
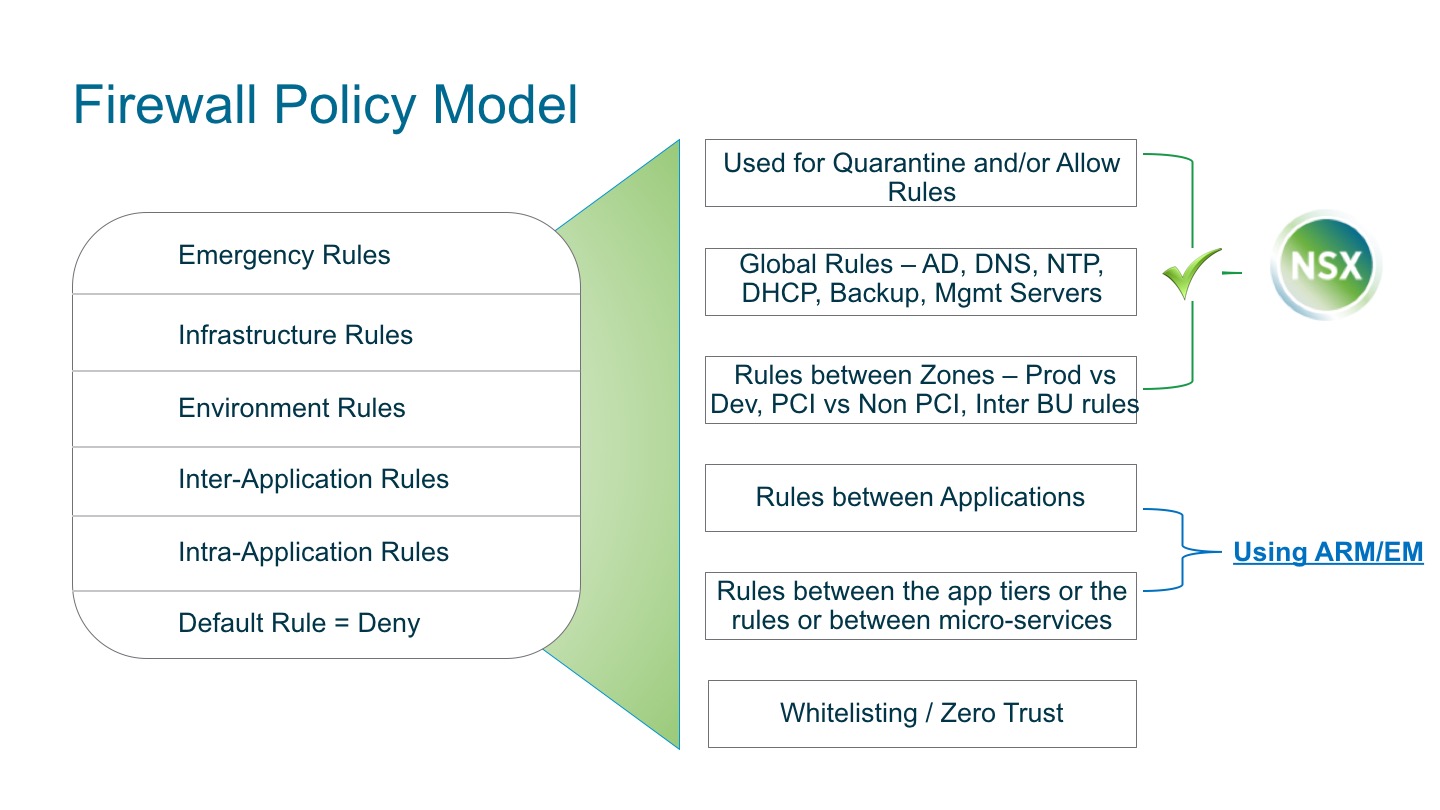 Figure 2: Firewall Policy Model
Figure 2: Firewall Policy Model
Generating Distributed Firewall Rules Rapidly
Any application in the datacenter can be Continue reading