Network Automation Tools: Featured Webinar in December 2016
The featured webinar in December 2016 is the Network Automation Tools webinar, and in the featured videos you'll find in-depth description of automation frameworks (focusing on Ansible) and open-source IPAM tools (including NSoT recently released by Dropbox).
To view the videos, log into my.ipspace.net, select the webinar from the first page, and watch the videos marked with star.
Read more ...Python Functions – Basic
Python Function is a block of statements that can be used multiple times in a program. Its tedious task to use same block of statements multiple times, instead we can have function which contains same block of statement and can be called wherever there is need for the same. A function in Python is defined […][minipost] Capturing bidirectional traffic of virtual machine (VMs) on vmWare ESX 6.x
Here I was getting a trouble with communication between an ESX virtual machine and the nearby switch (Nuage/DCN controller VM talking with a VTEP switch if someone is interested) and because that switch was direct destination of the control plane packets (OVSDB over TCP) I was not having much success creating a mirroring interface on the switch. So I learned how to capture a specific virtual machine traffic directly on the ESXi host’s SSH console and to not forget that, I will document this here.
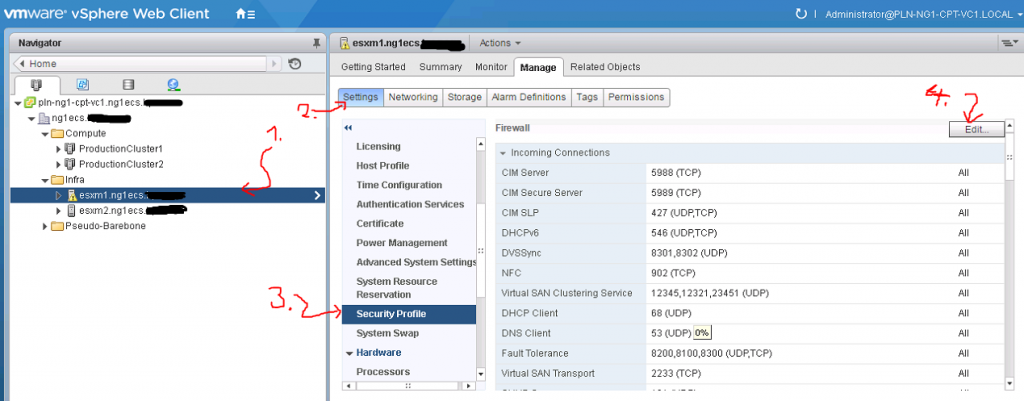
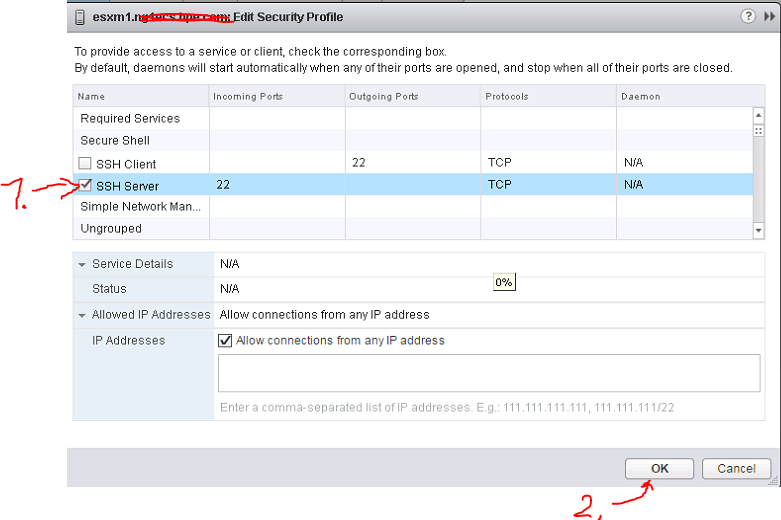
Step 1 – enable SSH to the ESX host
In most cases this is not running by default, so go to the ESXi server direct terminal or iLo and via “F2″enter system customization and enter troubleshooting section:
Right behind this menu should be “SSH Enable” option, and you simply hit that with enter 
ALTERNATIVE: If you have vCenter deployed, you can use its GUI to enable SSH on a specific host like this:
Step 2 – locating switchport ID
My virtual machine was called “DCN4.0R5_VSC1” and was simply connected to logical vswitch0 in Continue reading
Video: Arista Algomatch
Lots of interesting technology has been implemented in the latest Arista switches based on the Cavium Xpliant ASICs.
The post Video: Arista Algomatch appeared first on EtherealMind.