Network Break 442: HashiCorp Swaps Open Source For BSL; Open Enterprise Linux Goes After RHEL
Today on Network Break we discuss big moves in open source, including HashiCorp switching from an open source license to "business source" and Red Hat competitors banding together to offer an alternative to Red Hat Enterprise Linux (RHEL). We also discuss Google's odd attempt to get employees back to the office by charging them to stay at an on-campus hotel.Wasm core dumps and debugging Rust in Cloudflare Workers
A clear sign of maturing for any new programming language or environment is how easy and efficient debugging them is. Programming, like any other complex task, involves various challenges and potential pitfalls. Logic errors, off-by-ones, null pointer dereferences, and memory leaks are some examples of things that can make software developers desperate if they can't pinpoint and fix these issues quickly as part of their workflows and tools.
WebAssembly (Wasm) is a binary instruction format designed to be a portable and efficient target for the compilation of high-level languages like Rust, C, C++, and others. In recent years, it has gained significant traction for building high-performance applications in web and serverless environments.
Cloudflare Workers has had first-party support for Rust and Wasm for quite some time. We've been using this powerful combination to bootstrap and build some of our most recent services, like D1, Constellation, and Signed Exchanges, to name a few.
Using tools like Wrangler, our command-line tool for building with Cloudflare developer products, makes streaming real-time logs from our applications running remotely easy. Still, to be honest, debugging Rust and Wasm with Cloudflare Workers involves a lot of the good old time-consuming and Continue reading
Worth Reading: Networking for AI Workloads
Sharada Yeluri (Senior Director of Engineering at Juniper Networks) wrote a long article describing the connectivity requirements of AI workloads and new approaches to Ethernet fabrics. Definitely worth reading if you’re interested in these topics.
Worth Reading: Networking for AI Workloads
Sharada Yeluri (Senior Director of Engineering at Juniper Networks) wrote a long article describing the connectivity requirements of AI workloads and new approaches to Ethernet fabrics. Definitely worth reading if you’re interested in these topics.
Kubernetes 005. Overview of MicroK8s from Canonical (Ubuntu-folks).
Dear friend,
This year I had a pleasure and privilege to attend KubeCon Europe 2023 and this was the first time I’ve heard about MicroK8s. That sounded interesting and I decided I shall experiment with it and write a blogpost; but it didn’t catch my attention to a degree that I put it on top of my list; instead, I’ve put it to back burner. The last week I was talking to a colleagues of mine, who told me that he needs to test something in his production Kubernetes at home. I was quite interested, what does the one mean by “production Kubernetes cluster at home” and it appeared to be MikroK8s. At this stage I though, I don’t have any more excuses, so I just should sit and write it.
Is Kubernetes Used in Network Automation?
It is, indeed. The last week when we posted a blog about starting programming in C we got an interesting discussion in LinkedIn about Go vs Python with one right-honorable gentleman, who rightfully suggested that one of the main weaknesses of Python is that it requires to install dependencies on the host before you can use application. However, to be brutally honest, many Continue reading
Measuring the Use of DNSSEC
It's challenging to measure the uptake of DNSSEC in the DNS. There are just so many aspects of the DNS that are occluded from view! How many DNS names are there in the DNS? How many of these are signed? How many queries are processed by DNS infrastructure? How many queries add DNSSEC validcation. We present a new measurement here which is a query-weighted view of the DNS, looking the amount of queries for DNS names that are DNSSEC-signed as a proportion of the total query load.Argument Farming

The old standard.
I’m no stranger to disagreement with people on the Internet. Most of my popular posts grew from my disagreement with others around things like being called an engineer, being a 10x engineer, and something about IPv6 and NAT. I’ve always tried to explain my reasoning for my positions and discuss the relevant points with people that want to have a debate. I tend to avoid commenting on people that just accuse me of being wrong and tell me I need to grow up or work in the real world.
Buying the Farm
However, I’ve noticed recently that there have been some people in the realm of social media and influencing that have taken to posting so-called hot takes on things solely for the purpose of engagement. It’s less of a discussion and more of a post that outlines all the reasons why a particular thing that people might like is wrong.
For example, it would be like me posting something about how an apple is the dumbest fruit because it’s not perfectly round or orange or how the peel is ridiculous because you can eat it. While there are some opinions and points to be Continue reading
Integrating Calico statistics with Prometheus
Metrics are important for a microservices application running on Kubernetes because they provide visibility into the health and performance of the application. This visibility can be used to troubleshoot problems, optimize the application, and ensure that it is meeting its SLAs.
Some of the challenges that metrics solve for microservices applications running on Kubernetes include:
- Visibility: Microservices applications are typically composed of many small, independent services. This can make it difficult to get a clear picture of the overall health and performance of the application. Metrics provide a way to aggregate data from all of the services, giving you a single view of the application.
- Troubleshooting: When something goes wrong with a microservices application, it can be difficult to identify the root cause of the problem. Metrics can help you to track down the problem by providing information about the state of the application at the time of the failure.
- Optimization: Metrics can be used to optimize the performance of a microservices application. By tracking metrics such as CPU usage, memory usage, and network traffic, you can identify areas where the application can be improved.
- SLAs: Many microservices applications have SLAs that they must meet. Metrics can be used to Continue reading
Heavy Networking 694: A Network Engineering Roundtable
This week on Heavy Networking we've assembled a roundtable of network engineers to talk about...stuff. Each guest has brought a topic to discuss with the table, so we've got lots of subjects and lots of experiences and opinions. In particular we explore SPB, career advice, getting network automation off the ground, and the joys and perils of self-hosting.
The post Heavy Networking 694: A Network Engineering Roundtable appeared first on Packet Pushers.
Heavy Networking 694: A Network Engineering Roundtable
This week on Heavy Networking we've assembled a roundtable of network engineers to talk about...stuff. Each guest has brought a topic to discuss with the table, so we've got lots of subjects and lots of experiences and opinions. In particular we explore SPB, career advice, getting network automation off the ground, and the joys and perils of self-hosting.Kubernetes Unpacked 032: AI Use Cases For Kubernetes
On today's Kubernetes Unpacked we speak with Evis Drenova about whether AI has a role to play in the Kubernetes ecosystem. We discuss everything from using chat-based generative AI tools to interact with Kubernetes to data models and data sets on Kubernetes to Machine Learning with Kubernetes.
The post Kubernetes Unpacked 032: AI Use Cases For Kubernetes appeared first on Packet Pushers.
Kubernetes Unpacked 032: AI Use Cases For Kubernetes
On today's Kubernetes Unpacked we speak with Evis Drenova about whether AI has a role to play in the Kubernetes ecosystem. We discuss everything from using chat-based generative AI tools to interact with Kubernetes to data models and data sets on Kubernetes to Machine Learning with Kubernetes.One Tool to Rule Them All: How the Next Generation Does Cybersecurity
As cybersecurity becomes a vital part of business operations, the next generation of professionals will seek better advancements in protective technologies.Debug Queues from the dash: send, list, and ack messages
Today, August 11, 2023, we are excited to announce a new debugging workflow for Cloudflare Queues. Customers using Cloudflare Queues can now send, list, and acknowledge messages directly from the Cloudflare dashboard, enabling a more user-friendly way to interact with Queues. Though it can be difficult to debug asynchronous systems, it’s now easy to examine a queue’s state and test the full flow of information through a queue.
With guaranteed delivery, message batching, consumer concurrency, and more, Cloudflare Queues is a powerful tool to connect services reliably and efficiently. Queues integrate deeply with the existing Cloudflare Workers ecosystem, so developers can also leverage our many other products and services. Queues can be bound to producer Workers, which allow Workers to send messages to a queue, and to consumer Workers, which pull messages from the queue.
We’ve received feedback that while Queues are effective and performant, customers find it hard to debug them. After a message is sent to a queue from a producer worker, there’s no way to inspect the queue’s contents without a consumer worker. The limited transparency was frustrating, and the need to write a skeleton worker just to debug a queue was high-friction.
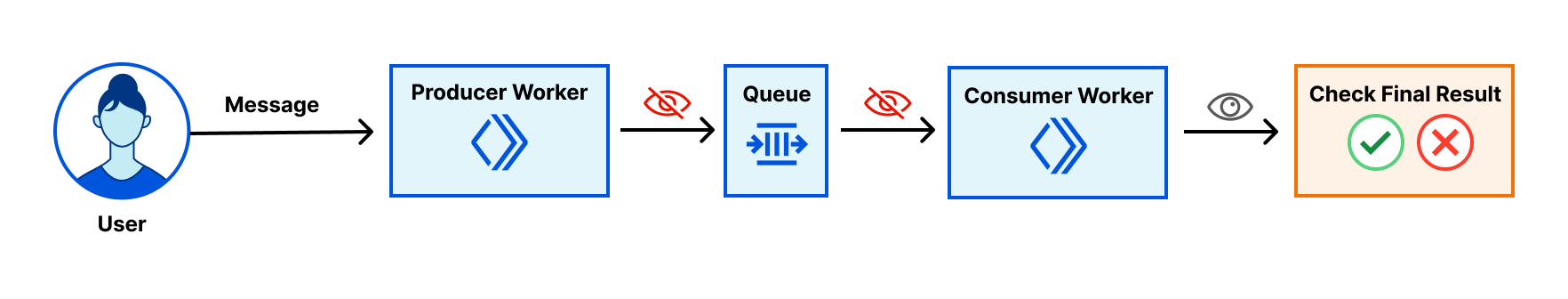
Now, Continue reading
Introducing scheduled deletion for Cloudflare Stream


Designed with developers in mind, Cloudflare Stream provides a seamless, integrated workflow that simplifies video streaming for creators and platforms alike. With features like Stream Live and creator management, customers have been looking for ways to streamline storage management.
Today, August 11, 2023, Cloudflare Stream is introducing scheduled deletion to easily manage video lifecycles from the Stream dashboard or our API, saving time and reducing storage-related costs. Whether you need to retain recordings from a live stream for only a limited time, or preserve direct creator videos for a set duration, scheduled deletion will simplify storage management and reduce costs.
Stream scheduled deletion
Scheduled deletion allows developers to automatically remove on-demand videos and live recordings from their library at a specified time. Live inputs can be set up with a deletion rule, ensuring that all recordings from the input will have a scheduled deletion date upon completion of the stream.
Let’s see how it works in those two configurations.
Getting started with scheduled deletion for on-demand videos
Whether you run a learning platform where students can upload videos for review, a platform that allows gamers to share clips of their gameplay, or anything in between, scheduled deletion can help Continue reading