Does NFV Create Vendor Lock-In?
 The challenge becomes scalability.
The challenge becomes scalability.
98.01% of sites on Cloudflare now use IPv6
It's 2016 and almost every site using Cloudflare (more than 4 million of them) is using IPv6. Because of this, Cloudflare sees significant IPv6 traffic globally where networks have enabled IPv6 to the consumer.
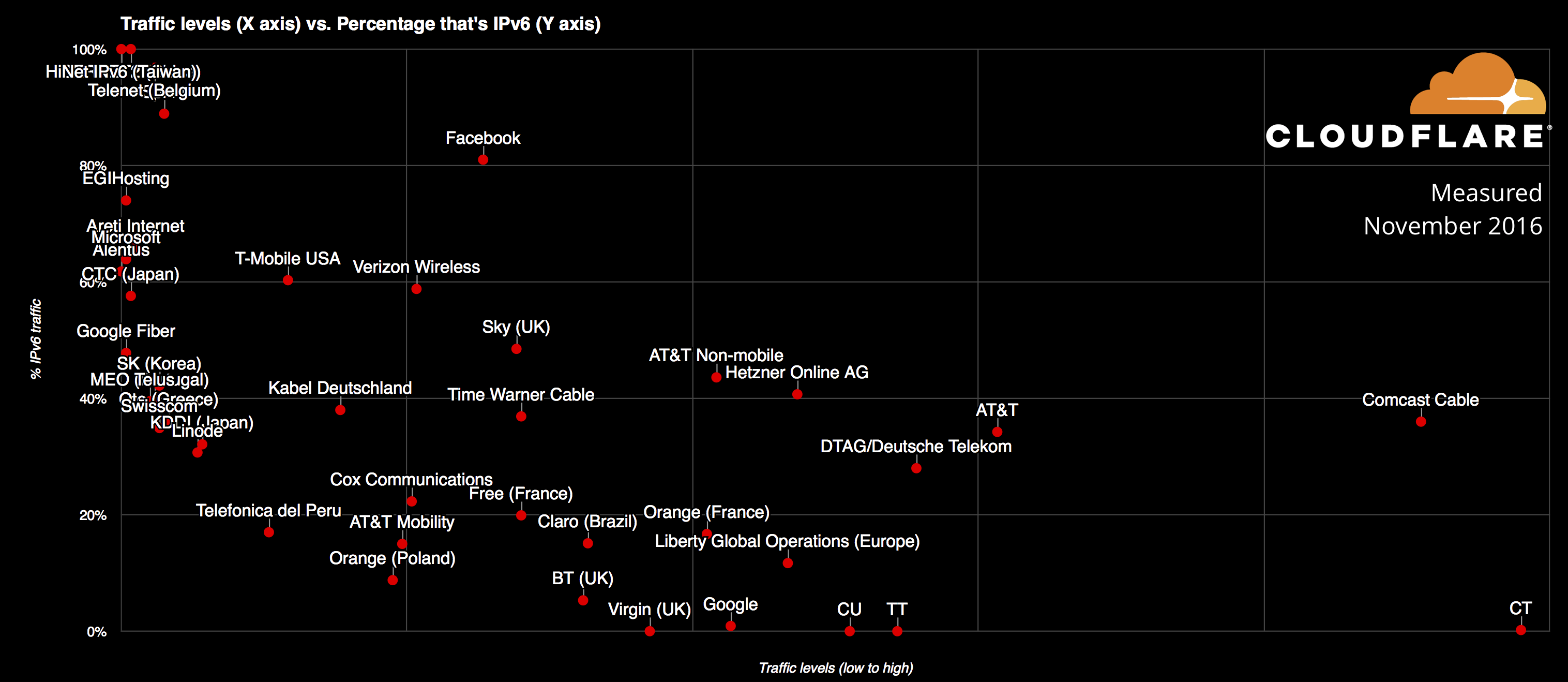
The top IPv6 networks are shown here.
The chart shows the percentage of IPv6 within a specific network vs. the relative bandwidth of that network. We will talk about specific networks below.
Why IPv6? Because fast internet.
IPv6 is faster for two reasons. The first is that many major operating systems and browsers like iOS, MacOS, Chrome and Firefox impose anywhere from a 25ms to 300ms artificial delay on connections made over IPv4. The second is that some mobile networks won’t need to perform extra v4 -> v6 and v6 -> v4 translations to connect visitors to IPv6 enabled sites if the phone is only assigned an IPv6 address. (IPv6-only phones are becoming very common. If you have a phone on T-Mobile, Telstra, SK Telecom, Orange, or EE UK, to name a few, it’s likely you’re v6-only.)
How much faster is IPv6? Our data shows that visitors connecting over IPv6 were able to connect and load pages in 27% less time than visitors connecting Continue reading
RapidAPI Raises $3.5M In Funding to Expand API Platform
 Martin Casado played a key role in Andreessen's funding of the company.
Martin Casado played a key role in Andreessen's funding of the company.
China Still Leads The Supercomputing Pack
Country retains its lead in latest TOP500 list of supercomputers.
10 Ways IT Can Prepare For Reduced Holiday Staff
Find out steps IT organizations can take to ensure everyone enjoys a happy holiday.