PowerNSX: PowerShell cmdlets to automate NSX
Looking to automate NSX for vSphere? Unsure where to start? Look no further than PowerNSX.

PowerNSX is a PowerShell module that abstracts the VMware NSX for vSphere API to a set of easily used PowerShell functions. It aims to focus on exposing New, Update, Remove and Get operations for all key NSX functions as well as adding additional functionality to extend the capabilities of NSX for vSphere management beyond the native UI or API.
PowerNSX works closely with VMware PowerCLI, and PowerCLI users will feel quickly at home using PowerNSX. Together these tools provide a comprehensive command line environment to manage your VMware NSX for vSphere environments.
PowerNSX continues to be updated and feature requests are welcome via the issues tracker on the projects GitHub page. Remember that VMware does not support this module, and PowerNSX comes with no warranties express or implied. Please test and validate PowerNSXs functionality before using in a production environment.
What’s in the box?
So what does your free download of PowerNSX give you?
At a glance:
- Over 210 cmdlets providing CRUD operations for a majority of NSX for vSphere’s capability. This command-line environment (programmatic language) allows for projects and applications of all sizes!
- Quickly deploy entire application stacks Continue reading
Worth Reading: High Speed Optical Networking
The post Worth Reading: High Speed Optical Networking appeared first on 'net work.
Network Break 113: Nutanix Targets Networking; More IoT Threats
Todays Network Break episode examines new networking features from Nutanix, the latest in IoT security research, a Google/Intel partnership & more The post Network Break 113: Nutanix Targets Networking; More IoT Threats appeared first on Packet Pushers.OpenStack Becomes a Standard Building Block for NFV
 OpenStack is becoming the de facto standard for infrastructure orchestration for NFV deployment by leading Communications Service Providers (CSPs).
OpenStack is becoming the de facto standard for infrastructure orchestration for NFV deployment by leading Communications Service Providers (CSPs).
FlokiBot: A Flock of Bots?
In early October, Flashpoint released an analysis of an underground forum advertisement for a new malware family known as FlokiBot. It took some time before a sample was found in the wild, but a researcher known as hasherezade flagged one on VirusTotal in early November. […]FlokiBot: A Flock of Bots?
In early October, Flashpoint released an analysis of an underground forum advertisement for a new malware family known as FlokiBot. It took some time before a sample was found in the wild, but a researcher known as hasherezade flagged one on VirusTotal in early November. She also wrote an analysis of its dropper here. This […]Does NFV Create Vendor Lock-In?
 The challenge becomes scalability.
The challenge becomes scalability.
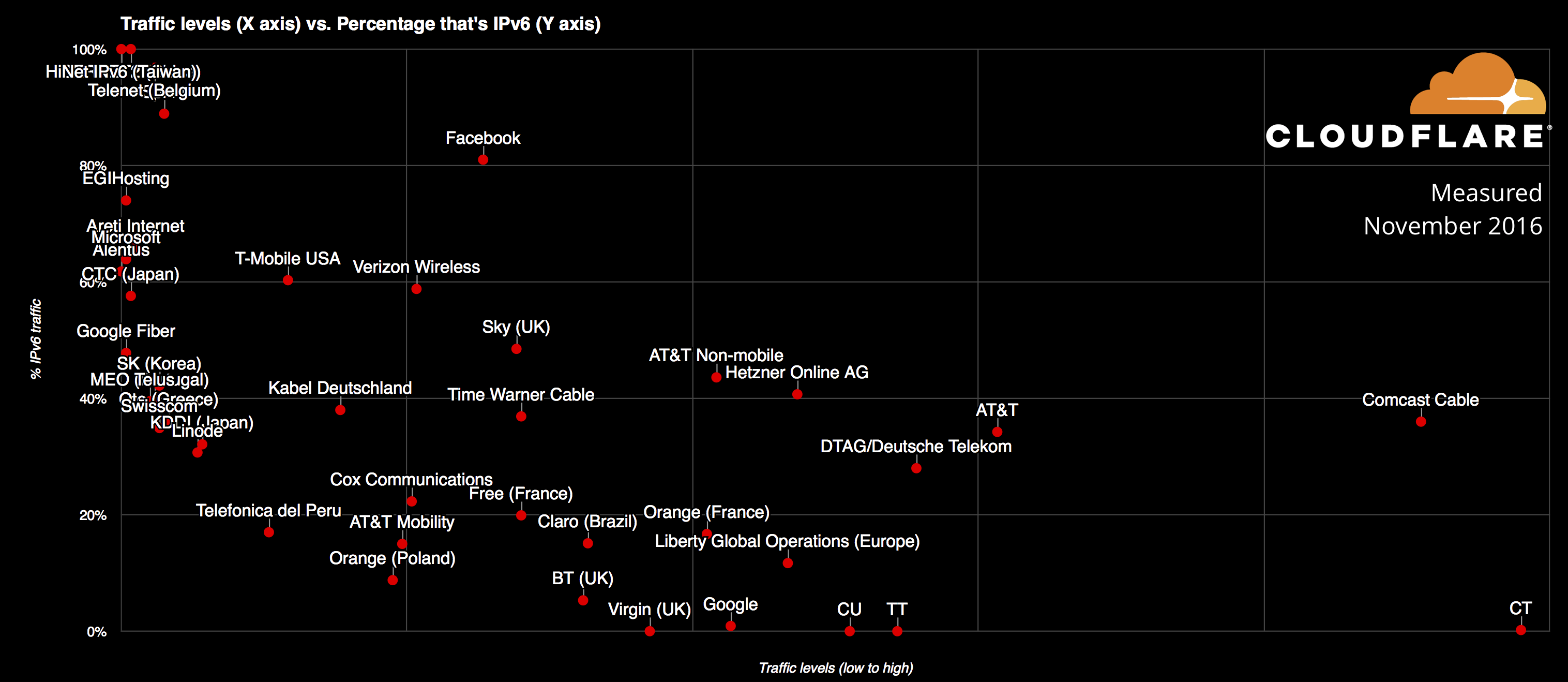
98.01% of sites on Cloudflare now use IPv6
It's 2016 and almost every site using Cloudflare (more than 4 million of them) is using IPv6. Because of this, Cloudflare sees significant IPv6 traffic globally where networks have enabled IPv6 to the consumer.
The top IPv6 networks are shown here.
The chart shows the percentage of IPv6 within a specific network vs. the relative bandwidth of that network. We will talk about specific networks below.
Why IPv6? Because fast internet.
IPv6 is faster for two reasons. The first is that many major operating systems and browsers like iOS, MacOS, Chrome and Firefox impose anywhere from a 25ms to 300ms artificial delay on connections made over IPv4. The second is that some mobile networks won’t need to perform extra v4 -> v6 and v6 -> v4 translations to connect visitors to IPv6 enabled sites if the phone is only assigned an IPv6 address. (IPv6-only phones are becoming very common. If you have a phone on T-Mobile, Telstra, SK Telecom, Orange, or EE UK, to name a few, it’s likely you’re v6-only.)
How much faster is IPv6? Our data shows that visitors connecting over IPv6 were able to connect and load pages in 27% less time than visitors connecting Continue reading
RapidAPI Raises $3.5M In Funding to Expand API Platform
 Martin Casado played a key role in Andreessen's funding of the company.
Martin Casado played a key role in Andreessen's funding of the company.