Unhappiness with MPLS Spurs SD-WAN Adoption
 These are enterprises with more than 1,000 employees.
These are enterprises with more than 1,000 employees.
Worth Reading: Leaving fixed function switches behind
The post Worth Reading: Leaving fixed function switches behind appeared first on 'net work.
The Next Level: An IT Army Of One
Today on the Next Level we talk to three tech pros from smaller organizations about what it means to be an IT army of one.
The post The Next Level: An IT Army Of One appeared first on Packet Pushers.
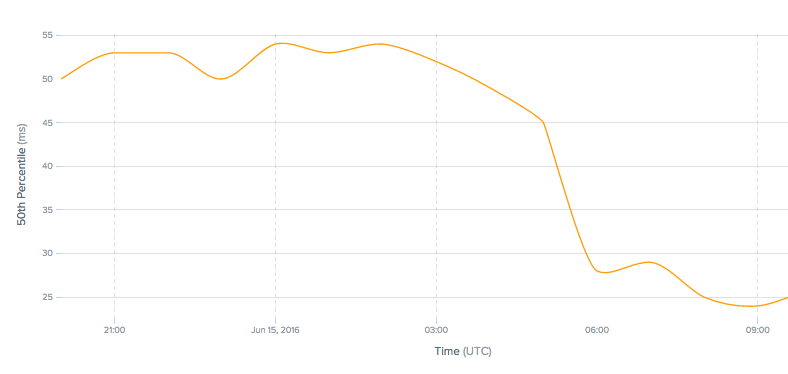
Hello, Colorado! CloudFlare’s 82nd Data Center is Live in Denver

Hello from the Mile High City! Denver is our twelfth data center in the United States, and our 82nd data center globally, improving regional web performance.
Denver Tech Scene
Near the iconic Rocky Mountains, Denver brews more beer than any other American city, and is home to a thriving technology and entrepreneurship community. The Colorado community brought us companies such as Chipotle, HomeAdvisor, and LogRhythm - and is helping build the next great Colorado company.
Mile High, Twice as Fast
Despite having a unique place on the map of the United States, and it's significant distance from other cities (900 miles to Dallas; 1,000 miles to Chicago, 1,000 miles to Los Angeles), Denver has not always been a major point of regional interconnection. Through the efforts of the community, and greater localized peering of traffic, this is changing for the better.
Visitors to millions of websites using ISPs, big or small, such as Aerux, Blackfoot, Comcast and CenturyLink, should see a 2x increase in performance, as they are now served from our Denver data center.
CloudFlare participates at two major internet exchanges: Any2 Denver and IX-Denver.