Who Needs an IPO? Blue Coat Gets a $4.65B Bid from Symantec
 So much for going public.
So much for going public.
Virtual Firewalls: Featured Webinar in June 2016
Virtual Firewalls is the featured webinar in June 2016, and the featured videos (marked with a star) explain the difference between virtual contexts and virtual appliances, and the virtual firewalls taxonomy.
To view the videos, log into my.ipspace.net (or enroll into the trial subscription if you don’t have an account yet), select the webinar from the first page, and watch the videos marked with star.
If you're a trial subscriber and would like to get access to the whole webinar, use this month's featured webinar discount (and keep in mind that every purchase brings you closer to the full subscription).
Brussels, Belgium: CloudFlare’s 81st Data Center is Live!

Our week begins in Brussels, where we announce our newest data center. This is our 23rd data center in Europe alone, and our 81st data center globally - providing additional redundancy to nearby facilities in Amsterdam and Paris.
Millions of websites using CloudFlare are now faster in Brussels, and we are excited to exchange traffic at the Belgium National Internet Exchange (BNIX).
Strategic City
 Brussels - which hosts several strategic European institutions such as the European Commission and the Council of the European Union - is home to over 40,000 EU employees. With the turn up of our Brussels data center, they join the rest of the country in experiencing a faster Internet. Impressively, close to 90% of Belgium's citizens are online.
Brussels - which hosts several strategic European institutions such as the European Commission and the Council of the European Union - is home to over 40,000 EU employees. With the turn up of our Brussels data center, they join the rest of the country in experiencing a faster Internet. Impressively, close to 90% of Belgium's citizens are online.
Two more cities
We will be announcing two more data centers this week - each in one of the world’s most populous countries. Could you guess which ones?
BGP As-path prepending – Use cases, Alternatives and Challenges
BGP As-path is a mandatory BGP attribute which has to be sent in every BGP message. BGP as-path prepending is one of the BGP traffic engineering methods which will be explained in detail throughout this post. Outline: What is BGP As-path attribute ? Why BGP as-path attribute is used ? What is BGP as-path prepending […]
The post BGP As-path prepending – Use cases, Alternatives and Challenges appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
The Case of the Failed IPv6 Ping – Part 1: The Facts and Clues
Put your detective hat on your head and your Network Detective badge on your lapel. It is time for the Case of the Failed IPv6 Ping.
Part #1 – We hit the crime scene together and we work methodically together to
- Gather the Facts
- Collect the Clues
- Follow the Evidence
- Interview the Witnesses
- Question the Suspects
Part #2 – I give you what the problem ended up being.
Ready?  Let’s PLAY!
Let’s PLAY!
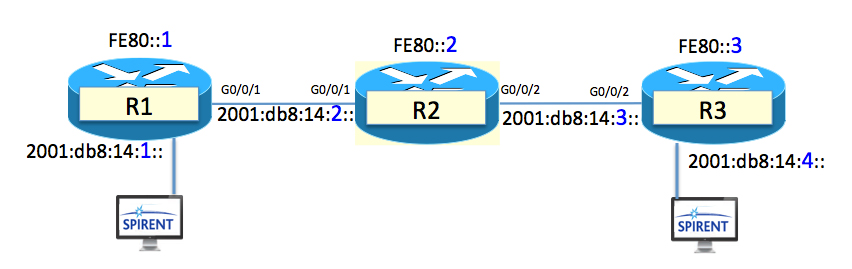
It all started when I was going to do a post on IPv6 Multicasting. I grabbed 3 ASR1K and got them all prepped: cards, code, cables, configurations. Name the routers R1, R2, and R3. Add a couple Spirent TestCenter ports for traffic and sniffing , configure them, and we are good to go.
Time for “pre-flight check”, as it were.
- PIM neighbors up and running between the routers – CHECK
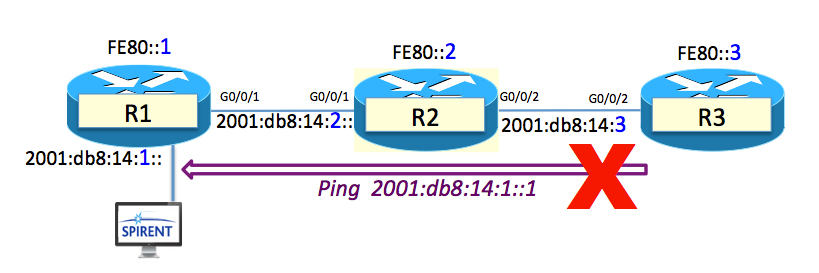
- Make sure that the R3 can ping 2001:db8:14:1::1 – Um……
Oh… crap… that didn’t work.
Let’s go to the active crime scene!
Make sure that the R3 can ping 2001:db8:14:1::
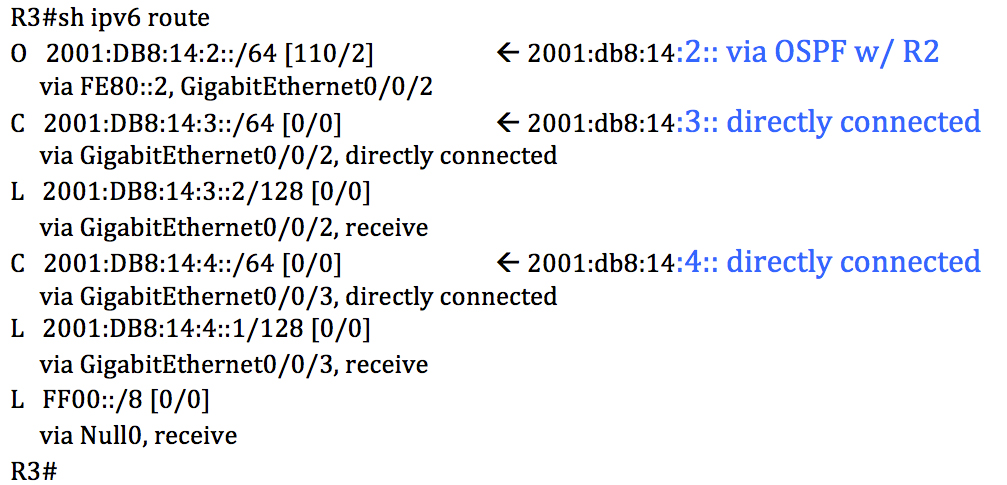
Well that didn’t work did it? Let’s check the routing table on R3.
From R3’s IPv6 routing table we see
Tutorial for small Hadoop cloud cluster LAB using virtual machines and compiling/running first “Hello World” Map-Reduce example project
I had Hadoop experience now for more than a year, thanks to a great series of Cloud Computing courses on Coursera.org, now after ~6 months of running via several cloud systems, I finally have time to put down some of my more practical notes in a form of an article here. I will not go much into theory, my target here would be to help someone construct his first small Hadoop cluster at home and show some of my amateur “HelloWorld” code that will count all words in all works of W. Shakespeare using the MapReduce. This should leave with with both a small cluster and a working compilation project using Maven to expand on your own later …
What I have used for my cluster is a home PC with 32G of RAM to run everything inside using vmWare Workstation. But this guide is applicable even if you run this usingVirtualBox, physical machines, or using virtual machines on some Internet cloud (e.g. AWS/Azure). The point will simply be 4 independent OS linux boxes that are together one a shared LAN to communicate between each other.
Lab Topology
For this one there is not much to say Continue reading
EVPN Inter-VLAN routing + mobility
So in the last blog I essentially looked at one of the most basic aspects of EVPN – a multi-site layer-2 network with nothing fancy going on, with traffic forwarding occurring between multiple sites in the same VLAN. The fact of the matter is that there was nothing going on there that you couldn’t do with a traditional VPLS configuration, however the general idea was to demonstrate the basics and take a look at the basic control-plane first.
In this update we’ll be looking at some of the more exclusive and highly useful aspects of EVPNs which make it a very attractive technology for things such as data-centre interconnect, there are a few things which are possible with EVPN which cannot be done with VPLS.
Consider the revised topology:

It’s the same topology from the first blog post, however I’ve simply added an additional VLAN (VLAN 101) to ge-0/0/22 of each EX4200 LAN switch, and an additional IXIA host.
For this post we’re going to look at a rather cool way of performing inter-VLAN forwarding between hosts in VLAN100 and VLAN101. Not that I want to spend time teaching people how to suck eggs, but generally in a simple network Continue reading
Cisco ASA and Office 365
Office 365 is widely used between many customers. Some of them happen to manage all the Internet connections through a Cisco ASA, not the fancy ASA-X with Firepower, just the plain old 5510. I was asked to allow Office 365 traffic, looks easy huh? Step 1: know your enemy After some Google-fu I found Microsoft […]Network Detective Series: Troubleshooting Method Ride-A-Long
“Hey Fish, how good are you at BFD? None of my BFD neighbors will come up.” Two simple sentences and I am “hooked.” I love troubleshooting! Troubleshooting is just a blast for me! It’s like being a Network Detective trying... Read More ›
The post Network Detective Series: Troubleshooting Method Ride-A-Long appeared first on Networking with FISH.
Looking inside Container Images
This blog is a continuation of my previous blog on Container standards. In this blog, we will look inside a Container image to understand the filesystem and manifest files that describes the Container. We will cover Container images in Docker, APPC and OCI formats. As mentioned in previous blog, these Container images will converge into … Continue reading Looking inside Container ImagesContainer Standards
In this blog, I will cover some of the standardization effort that is happening in the Containers area. I will cover some history, current status and also mention how the future looks like. In the next blog, we will look inside ACI and OCI Container images. Container Standards Lot of developments in Container area are done … Continue reading Container StandardsDocker 1.11 release presentation at Bangalore meetup
This link captures the slides on Docker release 1.11 release that I presented at Docker Meetup, Bangalore on June 4, 2016.Does Aerohive Scale?
Note: If you are a TL/DR type of person, let me give you the short answer to the title of the post: Yes! 
For everyone else, I will try my hardest to keep this as short as possible. I will include as many pictures and CLI screens as I think are needed to help answer the scalability question, and no more. While I entertained the idea of making two separate posts regarding scalability, I felt it best to keep it to a single post since AP(Access Point) to AP communication and layer 3 roaming are best explained together. My wife and friends will tell you that I can be long-winded. I apologize in advance.
Let me just start by saying that I work for Aerohive Networks. I have been an employee of Aerohive for about 3 months. In that time, I have learned a tremendous amount about the overall Aerohive solution and architecture. Prior to working for Aerohive, I worked for a reseller that sold for Cisco(to include Meraki), Aruba, and Aerohive. I wasn’t unaware of Aerohive, but let’s be honest for a minute. Aerohive doesn’t have a lot of information out there around how their various protocols work. This Continue reading
SDxCentral Weekly News Roundup — June 10, 2016
 DigitalOcean's CTO, Simplivity's latest, and more.
DigitalOcean's CTO, Simplivity's latest, and more.