Heavy Networking 679: Mountaintop Networking And Long-Haul Wireless
Today's Heavy Networking explores the challenges Wireless ISPs (WISPs) face when bringing services to locations without a lot of fiber in the ground. Those challenges include lining up radio antennas, maintaining mountaintop gear, wild horses, network and routing designs, and more. Our guest is Bradley Thompson, Senior Network Engineer at SkyFiber Internet.
The post Heavy Networking 679: Mountaintop Networking And Long-Haul Wireless appeared first on Packet Pushers.
Heavy Networking 679: Mountaintop Networking And Long-Haul Wireless
Today's Heavy Networking explores the challenges Wireless ISPs (WISPs) face when bringing services to locations without a lot of fiber in the ground. Those challenges include lining up radio antennas, maintaining mountaintop gear, wild horses, network and routing designs, and more. Our guest is Bradley Thompson, Senior Network Engineer at SkyFiber Internet.How to integrate Calico Image Scanner with Argo CI/CD
In today’s fast-paced software development environment, developers often use common public libraries and modules to quickly build applications. However, this presents a significant challenge for DevOps teams who must ensure that these applications are safe to use. As organizations move towards dynamic models of software development that rely on Continuous Integration and Continuous Deployment, the responsibility for deploying secure applications has shifted from traditional security teams to development teams.
To address this challenge, I will provide general guidelines on how to integrate the Calico Image Scanning feature into a CI/CD pipeline, using Argo. This will help ensure that images are built safely and free from Common Vulnerabilities and Exposures (CVEs). In this blog post, we will use a Kubernetes validating webhook configuration to attach a Calico Cloud admission controller that can accept or reject certain actions on resources, such as the creation of pods. This will prevent the deployment of images that contain known CVEs, thus strengthening the overall security of your software development process.
Overall Architecture
The building blocks to use Argo as an example of this integration are below:
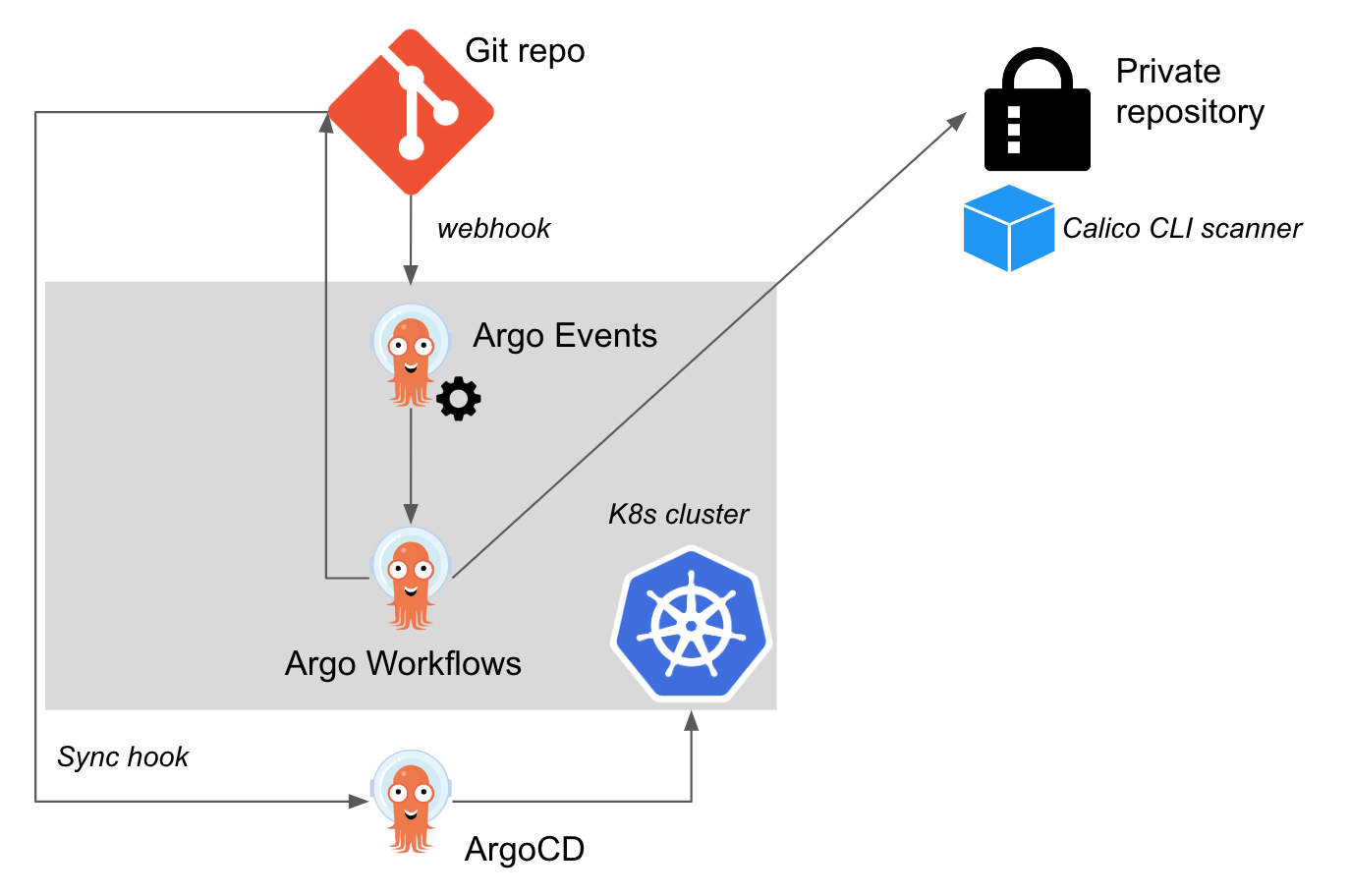
Relevant Calico configuration
Before even committing changes to our application, we must setup the Calico Admission Controller within our Continue reading
Aruba Isn’t A Wireless Company (Any More)

Remember when Aruba was a wireless company? I know it sounds like something that happened 40 years ago but the idea that Aruba only really made wireless access points and some campus switches to support them isn’t as old as you think. The company, now known as HPE Aruba Networking (née Aruba, a Hewlett Packard Enterprise Company), makes more than just Wi-Fi gear. Yet the perception of the industry is that they’re still a wireless company looking to compete with the largest parts of the market.
Branching Out of Office
This year’s Aruba Atmopshere showed me that Aruba is trying to do more than just campus wireless. The industry has shifted away from just providing edge connectivity and is now focused on a holistic lineup of products that are user-focused. You don’t need to go much further than the technical keynote on the second day of the conference to see that. Or the Networking Field Day Experience videos linked above.
Do you know what Aruba wanted to showcase?
- Campus Switches
- Data Center Switches
- Private 5G/LTE
- SASE/SSE
- IoT
- Cloud-Enabled Management
You know what wasn’t on that list? Access points. For a “wireless” company that’s a pretty glaring omission, right? I think Continue reading
How to Put Your ‘Carbonivore’ Data Center on a Diet
By taking a strategic approach to their monitoring tools and tech stack, data centers can both help their bottom line and reduce their carbon footprint.Magic in minutes: how to build a ChatGPT plugin with Cloudflare Workers


Today, we're open-sourcing our ChatGPT Plugin Quickstart repository for Cloudflare Workers, designed to help you build awesome and versatile plugins for ChatGPT with ease. If you don’t already know, ChatGPT is a conversational AI model from OpenAI which has an uncanny ability to take chat input and generate human-like text responses.
With the recent addition of ChatGPT plugins, developers can create custom extensions and integrations to make ChatGPT even more powerful. Developers can now provide custom flows for ChatGPT to integrate into its conversational workflow – for instance, the ability to look up products when asking questions about shopping, or retrieving information from an API in order to have up-to-date data when working through a problem.
That's why we're super excited to contribute to the growth of ChatGPT plugins with our new Quickstart template. Our goal is to make it possible to build and deploy a new ChatGPT plugin to production in minutes, so developers can focus on creating incredible conversational experiences tailored to their specific needs.
How it works
Our Quickstart is designed to work seamlessly with Cloudflare Workers. Under the hood, it uses our command-line tool wrangler to create a new project and deploy it to Workers.
How Pingora keeps count


A while ago we shared how we replaced NGINX with our in-house proxy, Pingora. We promised to share more technical details as well as our open sourcing plan. This blog post will be the first of a series that shares both the code libraries that power Pingora and the ideas behind them.
Today, we take a look at one of Pingora’s libraries: pingora-limits.
pingora-limits provides the functionality to count inflight events and estimate the rate of events over time. These functions are commonly used to protect infrastructure and services from being overwhelmed by certain types of malicious or misbehaving requests.
For example, when an origin server becomes slow or unresponsive, requests will accumulate on our servers, which adds pressure on both our servers and our customers’ servers. With this library, we are able to identify which origins have issues, so that action can be taken without affecting other traffic.
The problem can be abstracted in a very simple way. The input is a (never ending) stream of different types of events. At any point, the system should be able to tell the number of appearances (or the rate) of a certain type of event.
In a simple example, colors are Continue reading
Hedge 178: Defined Trust Transport with Kathleen Nichols

The Internet of Things is still “out there”—operators and individuals are deploying millions of Internet connected devices every year. IoT, however, poses some serious security challenges. Devices can be taken over as botnets for DDoS attacks, attackers can take over appliances, etc. While previous security attempts have all focused on increasing password security and keeping things updated, Kathleen Nichols is working on a new solution—defined trust transport in limited domains.
Join us on for this episode of the Hedge with Kathleen to talk about the problems of trusted transport, the work she’s putting in to finding solutions, and potential use cases beyond IoT.
You can find Kathleen at Pollere, LLC, and her slides on DeftT here.
Video: Sample Kubernetes SDN Implementations
Read for more Kubernetes details? How about Container Networking Interface (CNI) described by Stuart Charlton as part of Kubernetes Networking Deep Dive webinar?
Notes:
- You REALLY SHOULD watch Kubernetes SDN architecture and Sample Kubernetes SDN Implementations videos first
- The video (and a large portion of Kubernetes Networking Deep Dive webinar) is available with Free ipSpace.net Subscription.
Video: Kubernetes Container Networking Interface (CNI)
Ready for more Kubernetes details? How about Container Networking Interface (CNI) described by Stuart Charlton as part of Kubernetes Networking Deep Dive webinar?
Notes:
- You REALLY SHOULD watch Kubernetes SDN architecture and Sample Kubernetes SDN Implementations videos first
- The video (and a large portion of Kubernetes Networking Deep Dive webinar) is available with Free ipSpace.net Subscription.
Tigera named as one of Forbes America’s Best Startup Employers in 2023
We are proud to announce that we have been named one of America’s Best Startup Employers 2023 by Forbes!
The Forbes list of America’s Best Startup Employers 2023 was compiled by evaluating 2,600 companies with at least 50 employees in the United States. All of the companies considered were founded between 2013 and 2020, from the ground up, and were not spin-offs of existing businesses. Just like other Forbes lists, businesses cannot pay to be considered. Evaluation was based on three criteria: employer reputation, employee satisfaction, and growth.
Great Place to Work 2022
2022

Inclusion in Forbes’ list comes after we were proudly certified as a Great Place to Work in 2022.
in 2022.
The Great Place to Work Certification recognizes employers that create an exceptional employee experience. The certification process involves surveying employees and the employer, and rankings are based on employee feedback and independent analysis. This means job searchers can rely on the certification to help them determine whether an organization is truly a great place to work.
Go Tigers!
Our core values are the foundation of everything we do. Tigera believes in a collaborative, flexible work environment built on mutual respect and commitment. We are delighted to hear that our Continue reading
Kubernetes Unpacked 025: The Kubernetes Developer Experience
Michael Levan and Calvin Hendryx-Parker talk about their experience using Kubernetes, the pros and cons of the orchestration platform, and its impact on infrastructure engineers and developers. Calvin offers great tips on how to make the developer experience better and what platform engineering teams can do to make everyone’s job flow properly.
The post Kubernetes Unpacked 025: The Kubernetes Developer Experience appeared first on Packet Pushers.