“Understanding IPv6” – 7 Part IPv6 Network Computing Series
Newer to IPv6? Know it some but just want to go a little bit deeper? I realized I never put up here on my web site my 7 part … labor of love…. IPv6 blog series I did over on Network Computing. 
Understanding IPv6: The Journey Begins
Why is IPv6 so difficult to understand? Fish explains how she began unraveling this complex topic.
Understanding IPv6: Link-Local ‘Magic’
Fish performs a little IPv6 sleight of hand in the second post in her series on IPv6.
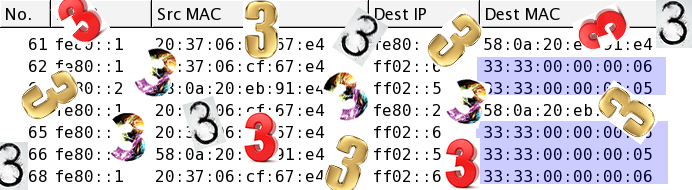
Understanding IPv6: A Sniffer Full Of 3s
Fish explores Wireshark sniffer traces in order to understand the difference between IPv4 and IPv6 addressing.
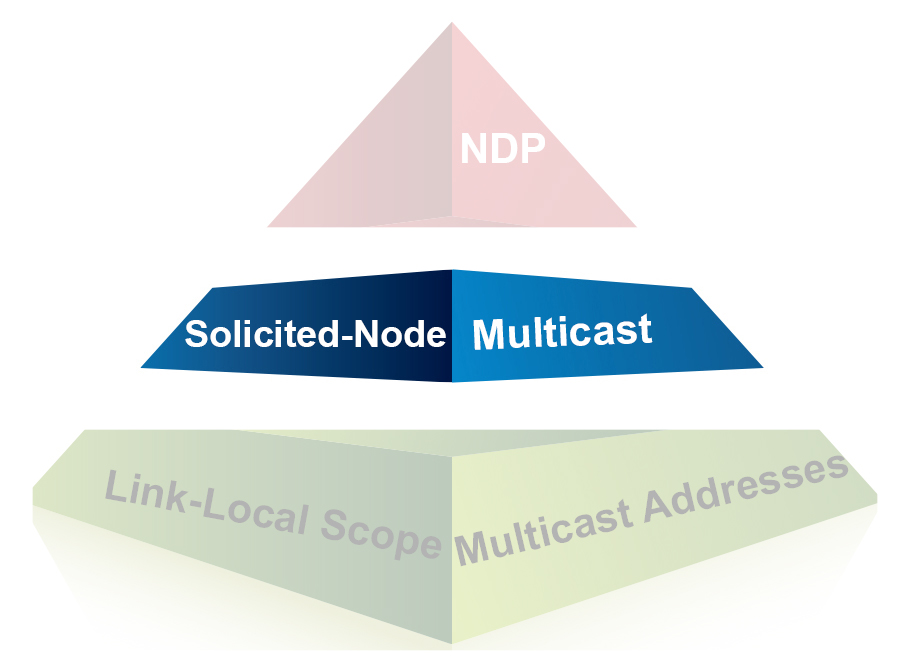
Understanding IPv6: What Is Solicited-Node Multicast?
Fish lays down the basics of solicited-node multicast, which provides the functionality for Neighbor Discovery in IPv6 addressing.
Understanding IPv6: Prepping For Solicited-Node Multicast
Before jumping into solicited-node multicast, a review of link-local scope multicast addresses is helpful.
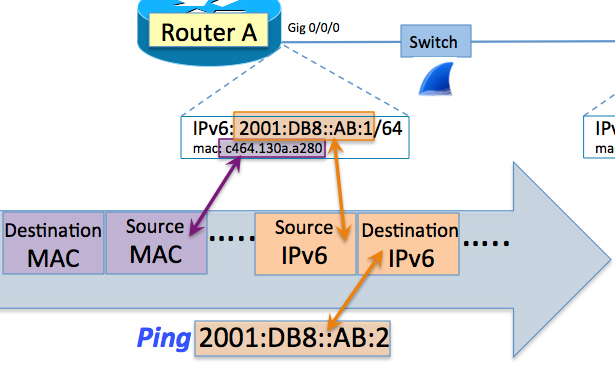
Understanding IPv6: The Ping Before Solicited-Node Multicast
Fish gets ready to walk through solicited-node multicast, analyzing an ICMP ping echo request in IPv4 and showing how it differs from IPv6.
Understanding IPv6: Solicited-Node Multicast In Action
In the Continue reading
Two Months Say More Than $45 Billion
Facebook CEO Mark Zuckerberg's decision to take 2 months of paternity leave may have a bigger impact than giving away $45 billion. Here's why.
The post Two Months Say More Than $45 Billion appeared first on Packet Pushers.
Two Months Say More Than $45 Billion
Facebook CEO Mark Zuckerberg's decision to take 2 months of paternity leave may have a bigger impact than giving away $45 billion. Here's why.
The post Two Months Say More Than $45 Billion appeared first on Packet Pushers.
VMware VCP5-DCV for a network engineer
Today I passed exam VCP550 and got VMware VCP5-DCV certification. Exam preparation For exam preparation I attended the official training that is mandatory to access the exam. The printed material provided with the training is good enough but I integrated with the great Mastering VMware vSphere 5.5 by Scott Lowe. The official documentation available online […]BT Praises ‘Cloud of Clouds’
 Riverbed gets an NFV win out of it, too.
Riverbed gets an NFV win out of it, too.
ONF Webinar Q&A + Video: Solving Interoperability & Operations Issues — The Guide to SDN for Optical Networks
 Why does transport SDN matter and how does one make it work? More with ONF's webinar Q&A.
Why does transport SDN matter and how does one make it work? More with ONF's webinar Q&A.
HPE Tops Enterprise Data Center Hardware Market
 Cisco and Microsoft are the leaders in the service provider and software data center sectors.
Cisco and Microsoft are the leaders in the service provider and software data center sectors.
HTTP/2 Demo: Under the Hood
At first glance, the potential performance improvements of HTTP/1.1 versus HTTP/2 on our demo page may seem a bit hard to believe. So, we put together a technical explanation of how this demo actually works. We’d also like to credit the Gophertiles demo, which served as a basis for our own HTTP/2 demo.
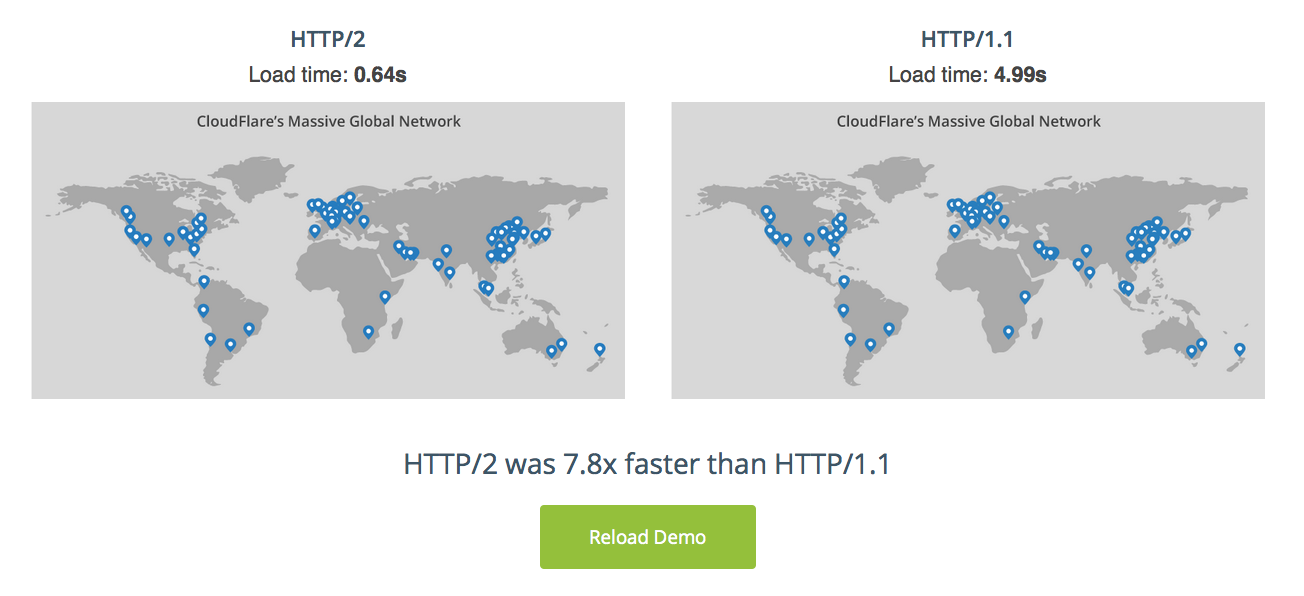
Overview
A web page can only be served over either HTTP/1.1 or HTTP/2—mixing protocols is not allowed. Our demo page is HTTP/2-enabled, so there’s no way to load HTTP/1.1 content directly on the same page. Inline frames (iframes) can be used to solve this issue. We embedded two iframes on our demo page, both containing the same source code. The key difference is that one iframe loads over an HTTP/1.1 CDN while the other loads over an HTTP/2 CDN.
We chose Amazon CloudFront for the HTTP/1.1 CDN because it can only serve content over HTTP/1.1. For the HTTP/2 CDN, we’re using our own HTTP/2-enabled network. You can take a look at the individual HTTP/1.1 and HTTP/2 iframe content, which should have similar load times to the side-by-side example on our demo page.
Iframe Content
So, what is contained in Continue reading
PlexxiPulse—SDN Webinar with IHS 12/15
Next Tuesday, we are participating in a webinar hosted by IHS analyst Cliff Grossner titled “Which Architecture is Best for Software Defined Networking (SDN)?” Plexxi Director of Product Marketing Bob Noel will contribute to the conversation alongside Jim MacLeod of Fujitsu and Paul Barret of NetScout. Topics up for discussion include rollout timing for data centers, centralized vs. distributed control architecture and service assurance. The webinar will also include company use cases that illuminate the value of SDN adoption. Want to listen in? You can sign up VMUG USERCON conference in Boston this week. Plexxi Systems Engineer Chris Tassone walked blogger Paul Braren through the Plexxi platform at the show. Check it out!
Below are a few of our top picks for our favorite news articles of the week.
Xconomy: Enterprise Tech Strikes Back: Photos and Takeaways
By Gregory T. Huang
Steve Papa said it takes having a different viewpoint and the persistence to turn a bad idea into a good idea. Andy Ory said it takes choosing the right market and problem to solve in the first place. Ash Ashutosh said that fast is the new big. The translation from these successful serial entrepreneurs: building an enterprise-tech startup is hard work, but there has never been more opportunity than now…Plexxi’s Rich Napolitano, a longtime EMC executive, said “we need a better ecosystem here”—meaning more collaboration and mentorship in the enterprise-tech community.
CRN: The 10 Coolest Networking Startups Of 2015
By Mark Haranas
It seems everyone was trying to shake up the traditional networking world this year through faster, cheaper, software-driven solutions. Startups are saying 2015 is the year where software-defined networking (SDN) and the Internet of Things (IoT) began to hit the mainstream market. Innovators who hailed from networking leaders like Cisco and Juniper Networks are forming new companies focusing on things such as analytics, “X”-as-a-Service or converged infrastructure. Startups such as Versa Networks, founded by former Juniper top engineers, and Altocloud, started by a former Cisco top executive, are striving to make network solutions simpler, automated and more cost effective to drive business outcomes. Here are 10 networking startups that have shaken up the industry in 2015.Plexxi is seeking to change the networking world in the enterprise and service provider markets by creating underlays that enable the network to be as scalable and easy to use as a cloud environment.
The Stack: How SDN can help enterprises become a competitive force in the digital age
By Kalyan Kumar, Senior Vice President and Chief Technologist at HCL Technologies
With the digital age dawning, businesses are under mounting pressure to become more agile if they want to compete. This has led to a huge focus on cloud, big data and mobile, but what is often forgotten is that these digital services are delivered on an underlying network infrastructure. Failing to future-proof this platform could ultimately render investments in new technologies ineffective and reduce the benefits they deliver. Digital services require a platform that can scale with spikes in traffic while being able to adapt to changing traffic patterns in real time. Traditional network infrastructures are unable to provide the agility, elasticity and scalability needed to keep up with rapid digital transformation. In order to tackle this challenge effectively, businesses must transition from physical infrastructure to implement a software defined network (SDN) that is more aligned with modern business demands.
Data Center Knowledge: Why Hyperconverged Infrastructure is so Hot
By Yevgeniy Sverdlik
Hyperconverged infrastructure did not exist as a concept two or three years ago. Today, it is one of the fastest-growing methods for deploying IT in the data center, as IT departments look for ways to adjust to their new role in business and new demands that are placed on them. Gartner expects it to go from zero in 2012 to a $5 billion market by 2019, becoming the category leader by revenue in pre-integrated full-stack infrastructure products. The category also includes reference architectures, integrated infrastructure, and integrated stacks. “Hyperconvergence simply didn’t exist two years ago,” Gartner analyst Andrew Butler said. “Near the end of this year, it’s an industry in its own right.” But, he added, the industry has a lot of maturation ahead of it, which means far from all vendors who are in the space today will still be in it a few years from now. In a session at this week’s Gartner data center management summit here, Butler and his colleague George Weiss shared their view of what hyperconverged infrastructure is, why it’s so hot, and what might it all mean for data center managers.
eWeek: Enterprises Embracing Next-Generation Data Centers, Gartner Asserts
By Scot Peterson
Amid the growth of cloud computing and software as a service, the enterprise data center seems like it has lost its place to become a repository of outdated modes of operation and aging equipment ripe for replacement. The general impression is that the enterprise data center as we know it is dead. Long live the data center. Call it the enterprise-defined data center. The reality is that data centers will continue to exist. But they are quickly changing into hubs of innovation, smaller and more agile. This is something that we have seen coming, but now the trend is here. Data centers are changing under the feet of companies as they transform themselves around digital business models, which Garter analysts call “Mode 2” computing. “It’s an exciting time to be in infrastructure,” said Vijay Luthra, senior vice president, global head of infrastructure, engineering and operations at Northern Trust, a speaker here at the Gartner Data Center, Infrastructure and Operations Management Conference. “CIOs are looking at very disruptive models.”
Harvard Business Review: 8 Tech Trends to Watch in 2016
By Amy Webb
More than once you’ve probably looked at some new digital or technological development and asked yourself, “How did we miss that?” In order to chart the best way forward, you must understand emerging trends: what they are, what they aren’t, and how they operate. Such trends are more than shiny objects; they’re manifestations of sustained changes within an industry sector, society, or human behavior. Trends are a way of seeing and interpreting our current reality, providing a useful framework to organize our thinking, especially when we’re hunting for the unknown. Fads pass. Trends help us forecast the future. To identify emerging trends, I use a six-part methodology beginning with seeking out those on the fringes doing unusual experimentation or research. Next I look for patterns using my CIPHER model, where I identify previously unseen contradictions, inflections, practices, hacks, extremes, and rarities. Then I ask practical questions, mapping trajectories, building scenarios, and pressure-testing my conclusions.
What do you think? Share your opinions about these stories with us on Twitter.
The post PlexxiPulse—SDN Webinar with IHS 12/15 appeared first on Plexxi.
iPexpert’s Newest “CCIE Wall of Fame” Additions 12/11/2015
Please join us in congratulating the following iPexpert students who have passed their CCIE lab!
The Missing Tier: SDN MANO for Multiservice Networks
 Intelligent provisioning of SDN network services cries out for an analytics-based MANO layer.
Intelligent provisioning of SDN network services cries out for an analytics-based MANO layer.
Show 267: Juniper’s Sky Advanced Threat Prevention (Sponsored)
The Packet Pushers talk to Juniper Networks about Sky Advanced Threat Prevention (ATP), a cloud-based anti-malware service integrated with SRX Gateways. It employs multiple technologies to identify risks and provide a higher degree of accuracy in threat prevention.
The post Show 267: Juniper’s Sky Advanced Threat Prevention (Sponsored) appeared first on Packet Pushers.