External Links on Spine Switches
A networking engineer attending the Building Next-Generation Data Center online course asked this question:
What is the best practice to connect DC fabric to outside world assuming there are 2 spine switches in the fabric and EVPN VXLAN is used as overlay? Is it a good idea to introduce edge (border) switches, or it is better to connect outside world directly to the spine?
As always, the answer is “it depends,” this time based on:
The Networking RFCs: To read or not to read?
I see this question rather often asked on various social media. A post on Twitter a few days ago triggered this little blog post and I deeply appreciate the poster. The question was simple “Is it really necessary for an engineer to know or understand the key RFC numbers?”. Some of the engineers I work […]
The post The Networking RFCs: To read or not to read? appeared first on Packet Pushers.
Demo Bytes: Upgrading Network Devices With BackBox – Video
The BackBox network automation platform comes with many pre-built functions to make routine tasks performed by network administrators simple & foolproof. In this demo, BackBox’s Senior Product Manager Perry Greenwood shows Packet Pushers’ Ethan Banks how to automate network device upgrades using BackBox. We look at the entire lifecycle of the upgrade process, including scheduling, […]
The post Demo Bytes: Upgrading Network Devices With BackBox – Video appeared first on Packet Pushers.
Assume Disaster

One of the things that people have mentioned to me in the past regarding my event management skills is my reaction time. They say, “You are always on top of things when they go wrong. How do you do it?”
My response never fails to make them laugh. I offer, “I always assume something is going to go wrong. I may not know what it is but when it does happen I’m ready to fix it.”
That may sound like a cynical take on planning and operations but it’s served me well for many years. Why is it that things we spend so much time working on always seem to go off the rails?
Complexity Fails
Whether it’s an event or a network or even a carpentry project you have to assume that something is going to go wrong. Why? Because the more complex the project the more likely you are to hit a snag. Systems that build on themselves and require input to proceed are notorious for hitting blocks that cause the whole thing to snarl into a mess of missed timelines.
When I was in college studying project management I learned there’s even a term for Continue reading
Network Break 422: Microsoft Tasks Copilot To Do Your Drudge Work; Cisco Debuts A New Learning Platform
On this week's Network Break podcast we examine Palo Alto Networks adding AI Ops to its SASE offering, and Microsoft Copilot bringing AI into its suite of Office tools. The Ethernet Adapter market grew 22% in 2022, but not because more NICs were sold; we discuss the real reasons and cover more tech news.
The post Network Break 422: Microsoft Tasks Copilot To Do Your Drudge Work; Cisco Debuts A New Learning Platform appeared first on Packet Pushers.
Network Break 422: Microsoft Tasks Copilot To Do Your Drudge Work; Cisco Debuts A New Learning Platform
On this week's Network Break podcast we examine Palo Alto Networks adding AI Ops to its SASE offering, and Microsoft Copilot bringing AI into its suite of Office tools. The Ethernet Adapter market grew 22% in 2022, but not because more NICs were sold; we discuss the real reasons and cover more tech news.The quantum state of a TCP port
Have you noticed how simple questions sometimes lead to complex answers? Today we will tackle one such question. Category: our favorite - Linux networking.
When can two TCP sockets share a local address?
If I navigate to https://blog.cloudflare.com/, my browser will connect to a remote TCP address, might be 104.16.132.229:443 in this case, from the local IP address assigned to my Linux machine, and a randomly chosen local TCP port, say 192.0.2.42:54321. What happens if I then decide to head to a different site? Is it possible to establish another TCP connection from the same local IP address and port?
To find the answer let's do a bit of learning by discovering. We have prepared eight quiz questions. Each will let you discover one aspect of the rules that govern local address sharing between TCP sockets under Linux. Fair warning, it might get a bit mind-boggling.
Questions are split into two groups by test scenario:
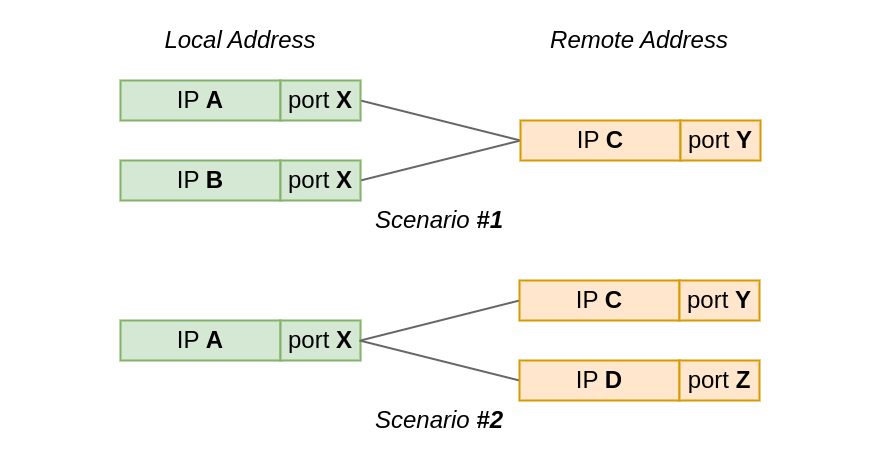
In the first test scenario, two sockets connect from the same local port to the same remote IP and port. However, the local IP is different for each socket.
While, in the second scenario, the local Continue reading
Everything you might have missed during Security Week 2023


Security Week 2023 is officially in the books. In our welcome post last Saturday, I talked about Cloudflare’s years-long evolution from protecting websites, to protecting applications, to protecting people. Our goal this week was to help our customers solve a broader range of problems, reduce external points of vulnerability, and make their jobs easier.
We announced 34 new tools and integrations that will do just that. Combined, these announcement will help you do five key things faster and easier:
- Making it easier to deploy and manage Zero Trust everywhere
- Reducing the number of third parties customers must use
- Leverage machine learning to let humans focus on critical thinking
- Opening up more proprietary Cloudflare threat intelligence to our customers
- Making it harder for humans to make mistakes
And to help you respond to the most current attacks in real time, we reported on how we’re seeing scammers use the Silicon Valley Bank news to phish new victims, and what you can do to protect yourself.
In case you missed any of the announcements, take a look at the summary and navigation guide below.
Monday
Stop Building Networks: It’s Time for Networking-as-a-Service
Networking-as-a-Service is the logical outcome of moving to the cloud and is a perfect match for today's anything-as-a-service economy.Test VRF-Aware DHCP Relaying with netlab
After figuring out how DHCP relaying works and testing it in a simple lab, I went a step further and tested VRF-aware DHCP relaying.
Lab Topology
I had to make just a few changes to the DHCP relaying lab topology:
- DHCP server is running on CSR 1000v. IOSv DHCP server does not support subnet selection DHCP option and thus doesn’t work with relays that do inter-VRF DHCP relaying.
- I put the link between the DHCP client and DHCP relay into a VRF.
Test VRF-Aware DHCP Relaying with netlab
After figuring out how DHCP relaying works and testing it in a simple lab, I went a step further and tested VRF-aware DHCP relaying.
Lab Topology
I had to make just a few changes to the DHCP relaying lab topology:
- DHCP server is running on CSR 1000v. IOSv DHCP server does not support subnet selection DHCP option and thus doesn’t work with relays that do inter-VRF DHCP relaying.
- I put the link between the DHCP client and DHCP relay into a VRF.
Worth Reading: History of 8-bit Bytes
Just in case you wondered why we have eight bits per byte: after Julia Evans investigated this mystery, Steven Bellovin published an excellent overview of the early years of bytes and words.
Worth Reading: History of 8-bit Bytes
Just in case you wondered why we have eight bits per byte: after Julia Evans investigated this mystery, Steven Bellovin published an excellent overview of the early years of bytes and words.
Understanding the Role of Digital Twins in Networking
Whether one is a telecom engineer or works in an enterprise, digital twins will eventually be the way managing a network is done.Wildcard and multi-hostname support in Cloudflare Access


We are thrilled to announce the full support of wildcard and multi-hostname application definitions in Cloudflare Access. Until now, Access had limitations that restricted it to a single hostname or a limited set of wildcards. Before diving into these new features let’s review Cloudflare Access and its previous limitations around application definition.
Access and hostnames
Cloudflare Access is the gateway to applications, enforcing security policies based on identity, location, network, and device health. Previously, Access applications were defined as a single hostname. A hostname is a unique identifier assigned to a device connected to the internet, commonly used to identify a website, application, or server. For instance, "www.example.com" is a hostname.
Upon successful completion of the security checks, a user is granted access to the protected hostname via a cookie in their browser, in the form of a JSON Web Token (JWT). This cookie's session lasts for a specific period of time defined by the administrators and any request made to the hostname must have this cookie present.
However, a single hostname application definition was not sufficient in certain situations, particularly for organizations with Single Page Applications and/or hundreds of identical hostnames.
Many Single Page Applications have two Continue reading
Account Security Analytics and Events: better visibility over all domains

Cloudflare offers many security features like WAF, Bot management, DDoS, Zero Trust, and more! This suite of products are offered in the form of rules to give basic protection against common vulnerability attacks. These rules are usually configured and monitored per domain, which is very simple when we talk about one, two, maybe three domains (or what we call in Cloudflare’s terms, “zones”).
The zone-level overview sometimes is not time efficient
If you’re a Cloudflare customer with tens, hundreds, or even thousands of domains under your control, you’d spend hours going through these domains one by one, monitoring and configuring all security features. We know that’s a pain, especially for our Enterprise customers. That’s why last September we announced the Account WAF, where you can create one security rule and have it applied to the configuration of all your zones at once!
Account WAF makes it easy to deploy security configurations. Following the same philosophy, we want to empower our customers by providing visibility over these configurations, or even better, visibility on all HTTP traffic.
Today, Cloudflare is offering holistic views on the security suite by launching Account Security Analytics and Account Security Events. Now, Continue reading
One-click ISO 27001 certified deployment of Regional Services in the EU
Today, we’re very happy to announce the general availability of a new region for Regional Services that allows you to limit your traffic to only ISO 27001 certified data centers inside the EU. This helps customers that have very strict requirements surrounding which data centers are allowed to decrypt and service traffic. Enabling this feature is a one-click operation right on the Cloudflare dashboard.
Regional Services - a recap
In 2020, we saw an increase in prospects asking about data localization. Specifically, increased regulatory pressure limited them from using vendors that operated at global scale. We launched Regional Services, a new way for customers to use the Cloudflare network. With Regional Services, we put customers back in control over which data centers are used to service traffic. Regional Services operates by limiting exactly which data centers are used to decrypt and service HTTPS traffic. For example, a customer may want to use only data centers inside the European Union to service traffic. Regional Services operates by leveraging our global network for DDoS protection but only decrypting traffic and applying Layer 7 products inside data centers that are located inside the European Union.
We later followed up with the Data Continue reading