VMware Claims 100 Production Deployments for NSX
 The 'Fight of the Century' ran on NSX, it turns out.
The 'Fight of the Century' ran on NSX, it turns out.
HP Chalks Up the First OEM Deal for VMware NSX
 Beyond reselling VMware NSX, HP has plans for some SDN federation.
Beyond reselling VMware NSX, HP has plans for some SDN federation.
Get Smarter About WiFi
WiFi has grown in leaps and bounds, and demand is increasing. Make sure your environment is ready.Defending the White Elephant
Click here to download the full report that includes attack details, TTPs and indicators of compromise.
Myanmar is a country currently engaged in an important political process. A pro-democracy reform took place in 2011 which has helped the government create an atmopshere conducive to investor interest. The country is resource rich, with a variety of natural resources and a steady labor supply. Despite recent progress, the country is subject to ongoing conflict with ethnic rebels and an ongoing civil war. Analysts suggest that both China and the United States are vying for greater influence in Myanmar, with China in particular having geopolitical interest due to sea passages, port deals, and fuel pipelines that are important to its goals. Geopolitical analysts have suggested that the United States may have its own interests that involve thwarting Chinese ambitions in the region.
APT groups from multiple countries – including China – have been known to target organizations of strategic interest with aggressive malware-based espionage campaigns. One of the malware families used in such a scenario is the well-known Remote Access Trojan PlugX, also known as Korplug, that enables full access to the victim’s machine and network.
Multiple instances of PlugX and related downloader Continue reading
Defending the White Elephant
Click here to download the full report that includes attack details, TTPs and indicators of compromise. Myanmar is a country currently engaged in an important political process. A pro-democracy reform took place in 2011 which has helped the government create an atmopshere conducive to investor interest. The country is resource rich, with a variety of […]How to Bring SDN/NFV into Reality
Unless you've been living inside a cave, or on top of a mountain without any Internet connection, you must have heard or read the news about Software-Defined Networking (SDN). In fact, SDN news pops up too often these days it makes some skeptics start thinking whether it is really real or just another hype in networking industry.
The challenge is it seems like everybody comes with their own definition of SDN. Each networking vendor displays its solution based on each own interpretation of SDN implementation. IETF group called the Interface to the Routing System (I2RS) is still trying to standardize southbound programming protocols and network-wide, multilayer topologies that include both virtual and real elements, network overlays and underlays. Open Networking Foundation (ONF), as a user-driven organization dedicated to the promotion and adoption of SDN, until today is mainly focusing on standardization of OpenFlow protocol. And the rise of new SDN startups, no doubt have created lots of excitement with many innovations within SDN spaces, contributes to the confusion at the same time.
The questions from today's business leaders in companies that consume networking technologies: if we want to embrace SDN, are we on the right track? Which way to go? Continue reading
Looking at IS-IS Security
Engineers hardly ever think of the control plane as an attack surface — from the new/old wave of centralized controllers (Rule 11!) to the middle term wave of distributed routing protocols, the control plane just hums along in the background without many people thinking about it from a security perspective. That is, until a big […]
The post Looking at IS-IS Security appeared first on Packet Pushers.
This Is How You Handle Customer Support Issues
My first ride with Uber was a love at first sight – the amount of friction they managed to remove from using-a-taxi process is unbelievable.
However, every love story eventually faces real-life issues, and what really matters is how you handle them at that point.
Read more ...Docker Meetup Bangalore -Networking presentation
Following link captures the slides that I presented at Docker Meetup, Bangalore. You can find more details on the meetup here and here.Docker Meetup Bangalore -Networking presentation
Following link captures the slides that I presented at Docker Meetup, Bangalore. You can find more details on the meetup here and here.Can We Shrink (or Eliminate) VMs to Suit Containers?
![]() VMs can help the container cause, but there's room for improvement, say speakers at OpenStack Silicon Valley.
VMs can help the container cause, but there's room for improvement, say speakers at OpenStack Silicon Valley.
Why Cisco?
Why do i keep focusing so much on Cisco, when there are clearly alot of different vendors out there with similar products and technologies?
There are several reasons for this.
1) I began the professional part of my networking career with Cisco.
2) Cisco has a proven track record when it comes to education and learning.
3) Even though not always the best match for all use-cases, Cisco is a big player in almost all areas of networking.
4) The networking opportunities provided by Cisco is by far the best of what ive seen. Take for example the Cisco Learning Network.
5) Cisco Press is really awesome in my opinion. They have alot of really high quality books out there.
6) Great opportunities to interact with the company. By this i mean to participate in programs like Cisco Champions and different SME (Subject Matter Expert) related activities.
7) Cisco documentation is not perfect, but its hands down the best I’ve seen across multiple vendors.
8) And ofcourse Cisco Live! 
That being said, recently i have begun to take a more neutral look at technologies. The reason being, that in this day and age, proprietary technologies become less prefered than open Continue reading
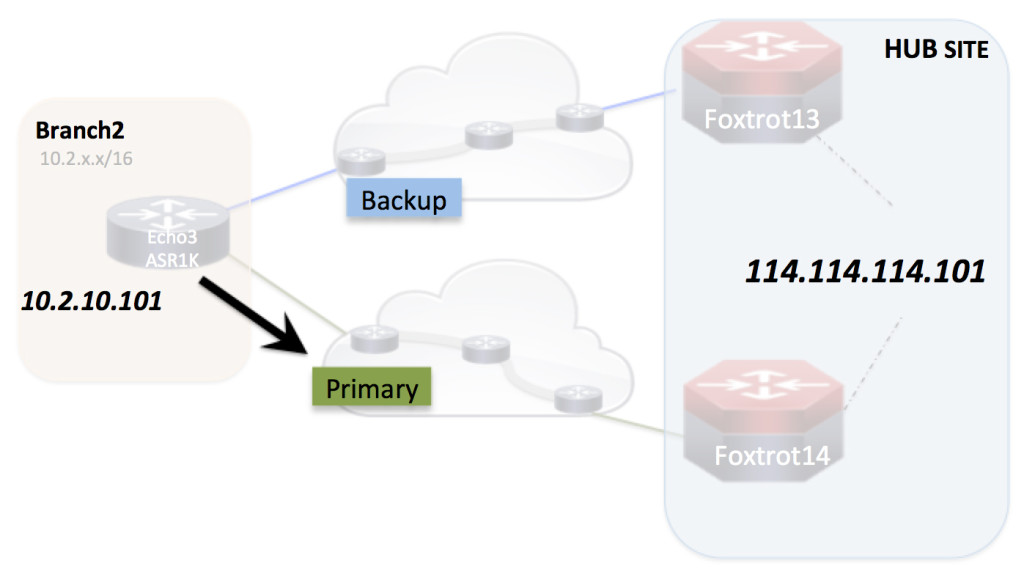
IWAN’s “Intelligent Path Control” & Using Your Backup Link
The blog I was going to post today was a blog about how PfRv3 (IWAN’s “Intelligent Path Control”) utilizes the GRE tunnel of the DMVPN underlay in order to make intelligent decisions about where to send business critical traffic based on knowledge of the health of the path that business critical traffic would take. …… But then I started realizing that while I have dug into a lot of DMVPN stuff recently on “Networking With Fish”…. I have not even really touched “Intelligent Path Control”. So……. let’s take a giant step backward.
“Intelligent Path Control” at the WAN – what can it do for you and why do you want it? In this blog I’m not going to try to be the definitive all encompassing guide of what all “Intelligent Path Control” is…. just enough to get us a little on the same page before we start “playing in the lab together” with it in future blogs.
The picture above is of a typical 1 router branch location with 2 WAN connections. One WAN connection is the primary and the other one sits there, unused, as just a backup … doing nothing Continue reading
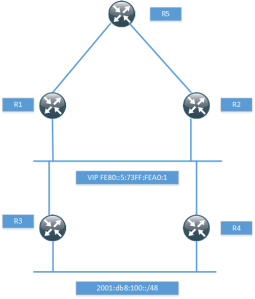
Busting Myths – IPv6 Link Local Next Hop into BGP
In some publications it is mentioned that a link local next-hop can’t be used when redistributing routes into BGP because routers receiving the route will not know what to do with the next-hop. That is one of the reason why HSRPv2 got support for global IPv6 addresses. One such scenario is described in this link.
The topology used for this post is the following.
I have just setup enough of the topology to prove that it works with the next-hop, so I won’t be running any pings and so on. The routers R1 and R2 have a static route for the network behind R3 and R4.
ipv6 route 2001:DB8:100::/48 GigabitEthernet0/1 FE80::5:73FF:FEA0:1
When routing towards a link local address, the exit interface must be specified. R1 then runs BGP towards R5, notice that I’m not using next-hop-self.
router bgp 100 bgp router-id 1.1.1.1 bgp log-neighbor-changes neighbor 2001:DB8:1::5 remote-as 100 ! address-family ipv6 redistribute static neighbor 2001:DB8:1::5 activate exit-address-family
If we look in the BGP RIB, we can see that the route is installed with a link local next-hop.
R1#sh bgp ipv6 uni BGP table version is 2, local router ID is 1.1.1.1 Status codes: s suppressed, Continue reading
Don’t Optimize the Last 5%
Robin Harris described an interesting problem in his latest blog post: while you can reduce the storage access time from milliseconds to microseconds, the whole software stack riding on top still takes over 100 milliseconds to respond. Sometimes we’re optimizing the wrong part of the stack.
Any resemblance to SDN in enterprises or the magical cost-reduction properties of multi-vendor data center fabrics is obviously purely coincidental.