Walled Gardens and Other Overlay Networks
Russ White wonders if the resurgence of Walled Gardens on the Internet is bad or a good thing. The long-term rise of Facebook, WeChat, Snapchat and other applications seems to be a sustaining trend. Overlay Network Previous walled gardens like AOL and CompuServe have been composting for many years. Their unique value was that they […]
The post Walled Gardens and Other Overlay Networks appeared first on EtherealMind.
5 Real Ways To Approach Security Automation
We've all heard about the benefits of automating system configurations to avoid human error, but introducing it to your infrastructure may be easier said than done. Here are five real-world ways to get started.How Did You Learn So Much About Networking?
One of my readers sent me a heartfelt email that teleported me 35 years down the memory lane. He wrote:
I only recently stumbled upon your blog and, well, it hurt. It's incredible the amount of topics you are able to talk about extensively and how you can dissect and find interesting stuff in even the most basic concepts.
May I humble ask how on earth can you know all of the things you know, with such attention to detail? Have you been gifted with an excellent memory, magical diet, or is it just magic?
Short answer: hard work and compound interest.
Read more ...Show 251 – Arista Networks CloudVision – Sponsored
Arista CloudVision is a turnkey approach to workload orchestration and workflow automation. Building on Arista’s success in building programmable and open software for the cloud with Arista EOS, CloudVision extends the EOS architecture to a network-wide perspective.
The post Show 251 – Arista Networks CloudVision – Sponsored appeared first on Packet Pushers.
Risky Business #379 — Ashley Madison dump, Troy Hunt and The Grugq
In this week's podcast we check in with Troy Hunt from HaveIBeenPwned.com. Troy has done the responsible thing in adding the Ashley Madison dataset to his service -- you can only search for email addresses in the dump after you've verified that you control them. We'll talk to him about why he did that.
SDN Market Size Projections Exceed GDP of Ecuador
Gartner recently issued its latest “Networking Hype Cycle,” which “tracks and analyzes the 35 most important networkingARM Counters Intel With an IoT Party of Its Own
 ARM wants to lend a hand to IoT.
ARM wants to lend a hand to IoT.
Introducing a Powerful Way to Purge Cache on CloudFlare: Purge by Cache-Tag
Today CloudFlare is introducing a new way to purge the cache using Cache-Tags. Cache-Tags are assigned to cached content via a Cache-Tag response header, and are stored as metadata with cached objects so that global purges take only seconds, targeting a granular, finite set of cached objects.
For example, an e-commerce website can use Cache-Tags to purge all of their catalog images at once, without affecting any of their other assets. A blog can use Cache-Tags to update their JavaScript files in cache, without forcing a cache miss on their CSS. A business can use Cache-Tags to purge cache of all four hundred pages of their blog without purging any of the pages from their core platform.
The CloudFlare Cache
With 42 data centers around the world, web pages served directly from CloudFlare’s cache are guaranteed to be just a few hops away from any visitor, anywhere. With a little bit of fine tuning, many websites succeed in delivering most of their content from cache, saving a majority of bandwidth on their origin servers. One website even managed to reduce their AWS bill by 96% when they started caching assets behind CloudFlare.
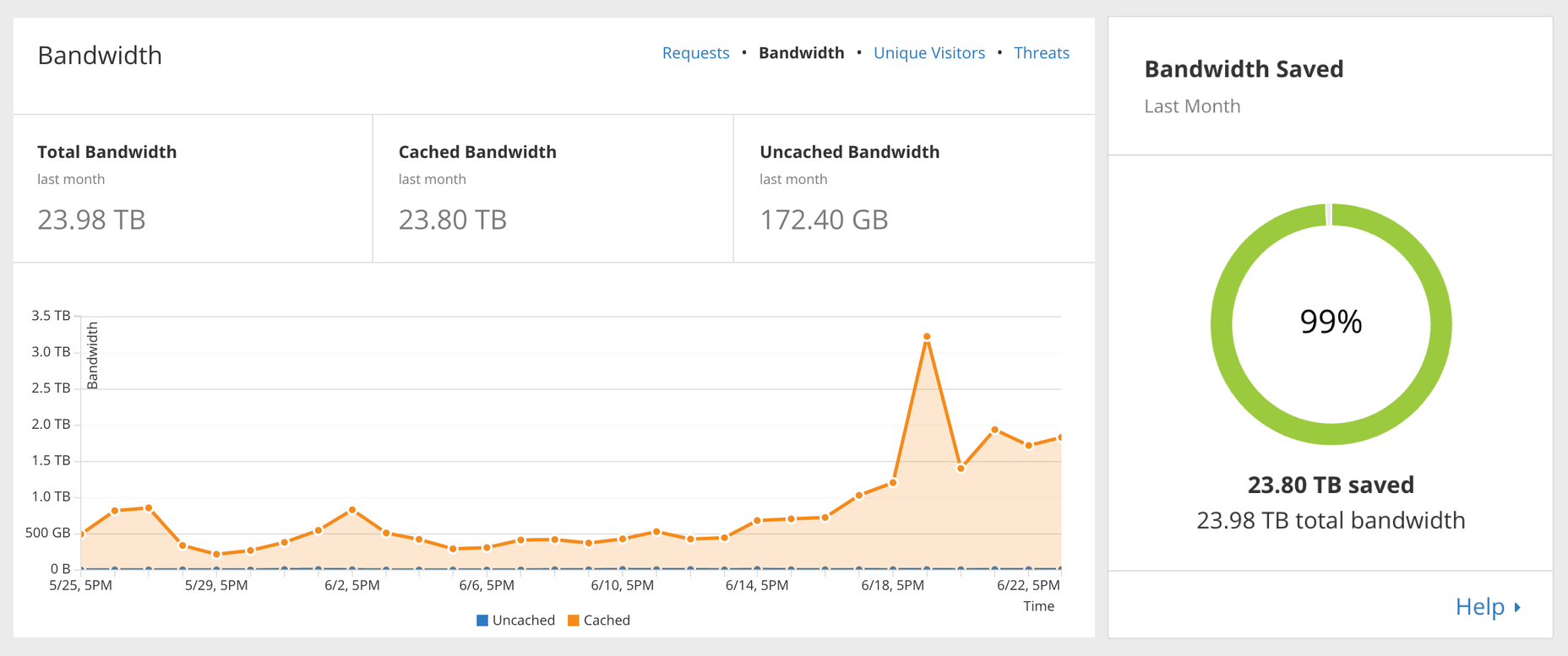
CloudFlare’s cache is powerful, but when a Continue reading
From Windows to Linux
I recently moved from Windows to Linux on my personal laptop and thought I might share my experience. This isn’t directly network related, but hopefully of interest to some portion of the large and diverse PP audience, especially considering recent events in the Microsoft realm. Ignoring that, using Linux ‘at home’ is a great way to learn about […]
The post From Windows to Linux appeared first on Packet Pushers.
Featured Guest Article: Deploying SDN in Service Provider Networks
 The role the SDN control layer plays.
The role the SDN control layer plays.
F5 iRules – What is a Program?
When I’m not working (boring right now), reading Everyday Feminism (fascinating*) or spending time with the family (awesome) I’m writing. I’ve three book projects on the go, two of which are taking far too long and rapidly become a chore. The third is the third edition of my F5 iRules book (I’m not shilling – […]
The post F5 iRules – What is a Program? appeared first on Packet Pushers.