VIRL – A slow greatness
I had a migration project from 6500 to ASRs. I have decided to check out VIRL.My migration setup requires 14 routers and a test server. Reading the system requirements for such a setup made me decide not to install on my laptop.
I went ahead and installed it on a not so small ESX server: A new UCS machine (24 cores, 380G memory, running 4 VMs, including VIRL), ESX 5.1.
I have allocated VIRL 4vCPU, 16GB memory.
The installation was not that short, but not that hard either. After the installation was over, I installed VM Maestro and started building my lab. Working with VM Maestro, which is VIRL's GUI, was really easy. The only annoying thing was my inability to set the interface numbers for the connections between routers.
Here is how my final setup looks like:
The setup is running 12 vIOS, 2 CSR1K, and one Ubuntu server, from where I ran my automated tests.
I pressed on "Start simulation" and then when trouble started. It took about 40 minutes for all the routers to load. Then the CLI felt like 2400 baud. It was crawling!
Notice that each time you start Continue reading
Docker Networking 101 – Mapped Container Mode
In this post I want to cover what I’m considering the final docker provided network mode. We haven’t covered the ‘none’ option but that will come up in future posts when we discuss more advanced deployment options. That being said, let’s get right into it.
Mapped container network mode is also referred to as ‘container in container’ mode. Essentially, all you’re doing is placing a new containers network interface inside an existing containers network stack. This leads to some interesting options in regards to how containers can consume network services.
In this blog I’ll be using two docker images…
web_container_80 – Runs CentOS image with Apache configured to listen on port 80
web_container_8080 – Runs CentOS image with Apache configured to listen on port 8080
These containers aren’t much different from what we had before, save the fact that I made the index pages a little more noticeable. So let’s download web_container_80 and run it with port 80 on the docker host mapped to port 80 on the container…
docker run -d --name web1 -p 80:80 jonlangemak/docker:web_container_80
Once it’s downloaded let’s take a look and make sure its running…
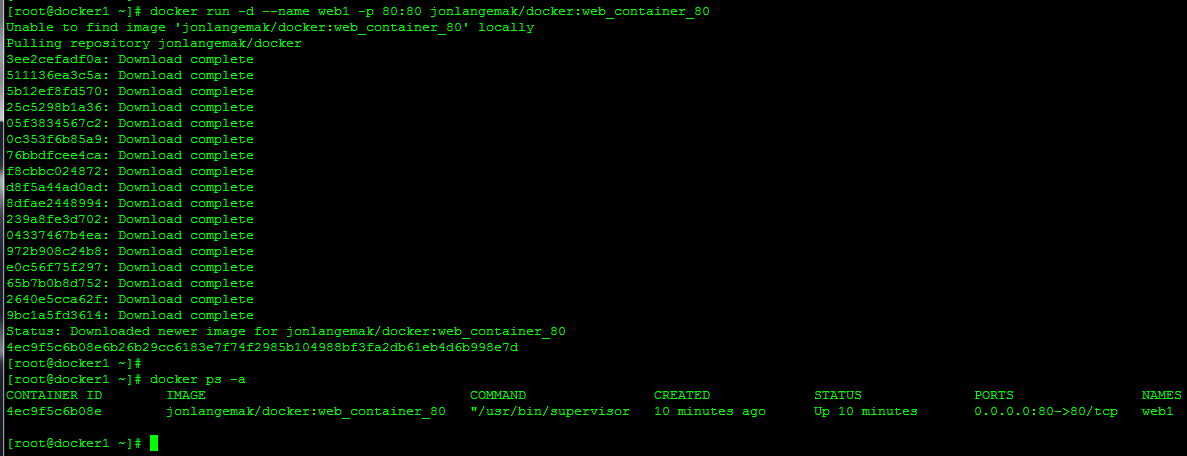
Here we can see that it’s Continue reading
What is Motivation?
Original content from Roger's CCIE Blog Tracking the journey towards getting the ultimate Cisco Certification. The Routing & Switching Lab Exam
What is Motivation? Why do some people pass one CCIE after the other and others never make it to one? The answer is motivation. They know what they want and more importantly they know what they need to do to achieve it. More motivational quotes here Have you ever wondered what makes you decide to... [Read More]
Post taken from CCIE Blog
Original post What is Motivation?
Qemu ASAv Appliance as Personal Firewall on Linux
The article discuss how to run Cisco Adaptive Security Virtual Appliance (ASAv) on KVM hypervisor as your personal firewall. Since ASAvQemu ASAv Appliance as Personal Firewall on Linux
The article discuss how to run Cisco Adaptive Security Virtual Appliance (ASAv) on KVM hypervisor as your personal firewall. Since ASAv version 9.3.2-200, Cisco supports deploying ASAv using Kernel-based Virtual Machine (KVM). Thanks for the support of KVM hypervisor, ASAv can be deployed in a very easy manner on Linux and any mysterious hacks is needed anymore.
Unfortunately until a valid license file is installed, ASAv throughput is limited to 100 Kbps. So far I have not found a way how to bypass this limitation as Cisco does not provide any evaluation licence as they offer for their CSR100v IOS-XE router. I also found out that ASAv keeps rebooting when Qemu is started without enabled KVM option. It limits deployment of ASAv Qemu images on Linux/FreeBSD as KVM is available for these operation systems only. Windows users should download and install ASAv edition for VMware hypervisor.
Software Requirements
• Linux x86_64 with installed Qemu and KVM
• Cisco ASAv Virtual Appliance - Qemu image asav932-200.qcow2 or later
HardwareRequirements
• CPU with VT-X or AMD-V hardware virtualization support
• 2GB RAM dedicated for ASAv virtual machine
1. ASAv Installation
Installation does not requires any special skills and takes only one reboot. Start the ASAv virtual machine Continue reading
Dynamically monitor interfaces with Nagios
 When you’re setting up your monitoring configuration for Nagios or compatible software it can be a hassle to decide which interfaces you actually want to monitor. Well rather how to monitor those interfaces. The nm_check_admin_up_oper_down plugin (part of Nelmon) checks the configuration of your network devices and reports a problem if you’ve indicated that the interface should be up.
When you’re setting up your monitoring configuration for Nagios or compatible software it can be a hassle to decide which interfaces you actually want to monitor. Well rather how to monitor those interfaces. The nm_check_admin_up_oper_down plugin (part of Nelmon) checks the configuration of your network devices and reports a problem if you’ve indicated that the interface should be up.
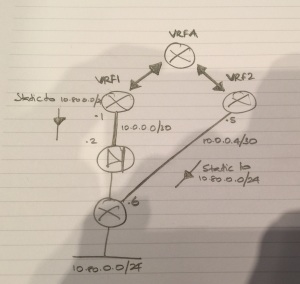
VRF Race Condition
A while ago I observed an interesting problem due to a routing misconfiguration. An asymmetric route was introduced across two discrete switches/routing instances. The route was then imported in a separate location.
When I began troubleshooting I was under the impression that the importer preferred one route over another because of admin distance or some other metric, or perhaps it was some sort of BGP esoterica you’d only encounter if you were using VRFs and MP-BGP to learn routes. However, the truth was probably something more prosaic.
Both routes were static routes. This meant their learning mechanism across importers was the same. The reason the importer preferred one route over another was probably due to one entering the routing table before the other.
Dynamically monitor interfaces with Nagios
 When you’re setting up your monitoring configuration for Nagios or compatible software it can be a hassle to decide which interfaces you actually want to monitor. Well rather how to monitor those interfaces. The nm_check_admin_up_oper_down plugin (part of Nelmon) checks the configuration of your network devices and reports a problem if you’ve indicated that the interface should be up.
When you’re setting up your monitoring configuration for Nagios or compatible software it can be a hassle to decide which interfaces you actually want to monitor. Well rather how to monitor those interfaces. The nm_check_admin_up_oper_down plugin (part of Nelmon) checks the configuration of your network devices and reports a problem if you’ve indicated that the interface should be up.
Continue reading
2015 is all about SDN WAN
The technology that gives me a “nerd hard-on” this month is SDN WAN. Here is why.
The post 2015 is all about SDN WAN appeared first on EtherealMind.
Configuring Syslog and SNMP on a Cisco Device
by Kevin Dooley, originally published on the Auvik blog There are two common ways to get management information about your network devicesCoding Basics: Python in Visual Studio
Python on Windows with Visual Studio
Whilst I’m an OSX and Linux fan, Windows is a key operating system in any enterprise and developing network applications in a Windows environment is also an important topic to cover off. Visual Studio (VS) is a Windows IDE (Integrated Development Environment) which will also soon be available for OSX (at the time of writing, it isn’t released). Whilst I’ve brushed over this previously, this post is a quick guide on how to setup a very easy to use environment to play with Python. This is not however an in depth tool chain guide. This is a 101 post but will be enough for most people to get to grips with Python who use Windows. Let’s face it, you don’t really want to be sitting on the command line doing this do you and Eclipse is not to everyone’s taste, especially if you have prior experience coding with .net for instance.
- Install the free version of Microsoft’s Visual Studio found here
- Install Python 3.x (or 2.x depending on your reasons) found here
- Install the Python tools for Visual Studion found here
I install both Python 2.x and 3.x as you Continue reading
Networking FAQ 4: Fundamentals
- At what OSI layer does protocol X operate?
- What's the difference between a router and a multilayer switch?
- What's the difference between forwarding and control planes?
- What's the difference between MTU and MSS?
- What's the difference between a VLAN interface and a BVI?
- How do tunnel interfaces work?
- What do NAT terms like "inside local" mean?
- Can I use the network and broadcast addresses in a NAT pool?
- Why do we need IP addresses? Can't we just use MAC addresses for everything?
- Does QoS provide more bandwidth?
Networking FAQ 4: Fundamentals
- At what OSI layer does protocol X operate?
- What's the difference between a router and a multilayer switch?
- What's the difference between forwarding and control planes?
- What's the difference between MTU and MSS?
- What's the difference between a VLAN interface and a BVI?
- How do tunnel interfaces work?
- What do NAT terms like "inside local" mean?
- Can I use the network and broadcast addresses in a NAT pool?
- Why do we need IP addresses? Can't we just use MAC addresses for everything?
- Does QoS provide more bandwidth?
Networking FAQ 4: Fundamentals
- At what OSI layer does protocol X operate?
- What's the difference between a router and a multilayer switch?
- What's the difference between forwarding and control planes?
- What's the difference between MTU and MSS?
- What's the difference between a VLAN interface and a BVI?
- How do tunnel interfaces work?
- What do NAT terms like "inside local" mean?
- Can I use the network and broadcast addresses in a NAT pool?
- Why do we need IP addresses? Can't we just use MAC addresses for everything?
- Does QoS provide more bandwidth?
Netscreen Packet Capture – Snoop

I’ve worked with Netscreens for a few years now, starting with ScreenOS version 5.x, and when troubleshooting I had always been pointed towards debug flow as the way to see what was going on. I suspect many of you have also been taught:
clear dbdebug flow basic- (wait for packets you wanted to capture)
undebug allget db stream(to view output)
This is definitely helpful for rule debugging but for simple packet capture is a bit over the top, which is where the snoop command comes in.
Snoop
To be clear, snoop won’t tell you anything about what decisions the firewall made about the packets, but it’s a simple way to see the actual traffic. Here’s an example of the output produced by snoop:
19944926.0: ethernet2/1(o) len=206:0010dbff2070->00005e000101/8100/0800, tag 1872
1.4.63.82 -> 1.15.18.27/17
vhl=45, tos=00, id=13096, frag=0000, ttl=64 tlen=188
udp:ports 500->500, len=168
00 00 5e 00 00 01 00 10 db a1 27 a1 81 00 07 50 ..^........p....
08 00 45 00 00 bc 33 28 00 00 40 11 b6 18 01 04 ..E...3([email protected]
3f 52 01 0e 12 1b 01 f4 01 f4 00 Continue readingIPv6 Renumbering – Mission Impossible?
In one of the discussions on v6ops mailing list Matthew Petach wrote:
The probability of us figuring out how to scale the routing table to handle 40 billion prefixes is orders of magnitude more likely than solving the headaches associated with dynamic host renumbering. That ship has done gone and sailed, hit the proverbial iceberg, and is gathering barnacles at the bottom of the ocean.
Is it really that bad? Is simple renumbering in IPv6 world just another myth? It depends.
Read more ...Using GNS3 for Basic Network Security Testing
(The original idea for this post came from a post my blog, “The Console Port,” which you can find atFabric visibility with Arista EOS
A leaf and spine fabric is challenging to monitor. The fabric spreads traffic across all the switches and links in order to maximize bandwidth. Unlike traditional hierarchical network designs, where a small number of links can be monitored to provide visibility, a leaf and spine network has no special links or switches where running CLI commands or attaching a probe would provide visibility. Even if it were possible to attach probes, the effective bandwidth of a leaf and spine network can be as high as a Petabit/second, well beyond the capabilities of current generation monitoring tools.The 2 minute video provides an overview of some of the performance challenges with leaf and spine fabrics and demonstrates Fabric View - a monitoring solution that leverages industry standard sFlow instrumentation in commodity data center switches to provide real-time visibility into fabric performance.
Fabric View is free to try, just register at http://www.myinmon.com/ and request an evaluation. The software requires an accurate network topology in order to characterize performance and this article will describe how to obtain the topology from a fabric of Arista Networks switches.
Arista EOS™ includes the eAPI JSON-RPC service for programmatic monitoring and control. The article Arista Continue reading
Untangle Scrutinized : Deep Dive into Untangle’s Features
This article is a followup to : Setting Up Untangle NGFW in a GNS3 Environment. In this one we take a deep dive into Untangle’sNFD9 Prep: SD-WAN
Software Defined WAN, or SD-WAN, looks to be a theme of Network Field Day 9, with presenters such as CloudGenix and VeloCloud showing us their offerings. At first glance, SD-WAN sounds pretty compelling. Who wouldn’t want to slash their WAN OpEx? How do these solutions work, and do they have legs? I’m hoping to find out.
What’s SD-WAN all about?
SD-WAN is about applying concepts of SDN to WAN networks. The goals are to increase flexibility and reduce WAN costs. This can be achieved through transport independence, dynamic path management, and better config management.
Historically we used private WAN circuits – leased lines, MPLS, etc. These had great SLAs, but the monthly costs were huge. The bandwidth was low, but guaranteed. Now that many places have access to high-speed Internet tails, it’s a lot harder to justify that cost. It’s very tempting to run IPSec VPNs across Internet links instead.
Those consumer Continue reading