Automating the Cabbage Patch Network Today (2014)
“Sometimes my head is a bit of an idiot” is something my daughter might say and that happens to me too, if that time is today and this article, let me know. If you don’t get the Cabbage Patch reference and its juxtaposition to automation, see here. I’ve tried to avoid sarcasm (and arrogance) but have […]
Author information
The post Automating the Cabbage Patch Network Today (2014) appeared first on Packet Pushers Podcast and was written by Steven Iveson.
IOS: show tcp vty
On Cisco IOS, this is a very useful command "show tcp vty xx" to show TCP statistics of the VTY session. If you think your terminal is running slow because of packet loss or delay then this command will provide visibility. The other cause is the CPU/Memory running slow if you don't see any errors on the TCP (as you can see below).
The post IOS: show tcp vty appeared first on EtherealMind.
Cisco ACI Fabric Forwarding In A Nutshell
As I study software defined networking architectures, I’ve observed that none of them are exactly alike. There are common approaches, but once diving into the details of what’s being done and how, even the common approaches seem to have as many differences as similarities. One of the most interesting elements of SDN architectures […]Wrapping up the Debate
What do you want to be when you grow up? Can you picture it? Close your eyes. Now give your mental self a super-hero kind of outfit. What’s emblazoned on your shirt? What job roles do you think you’d like? What technology do you think you’d like to work with?
In the past, most networkers put some cert letters or logo on their mental super-hero selfie. However, I think that the changes in the networking industry mean that we need to pay a little more attention to building that future self-image through better professional development planning. Those plans help try and reach that ideal image of where we want to be in our careers – and how we go about planning our own development has to change along with the rapid changes in the networking industry.
Wrapping the Series
This really will be the last in this series, with posts related somehow to our Interop debate about traditional certs vs. SDN skills development. Here’s a list of the other posts in the series:
30 Blogs In 30 Days: Insanity?
So apparently, over at EtherealMind, that Greg Ferro chap is going slightly insane and has challenged himself and others to a “30 Blogs in 30 Days” challenge. Because I like Greg, I’m not going to make a big deal about … Continue reading
If you liked this post, please do click through to the source at 30 Blogs In 30 Days: Insanity? and give me a share/like. Thank you!
Drupal 7 SA-CORE-2014-005 SQL Injection Protection
Yesterday the Drupal Security Team released a critical security patch for Drupal 7 that fixes a very serious SQL injection vulnerability. At the same time we pushed an update to our Drupal WAF rules to mitigate this problem. Any customer using the WAF and with the Drupal ruleset enabled will have received automatic protection.
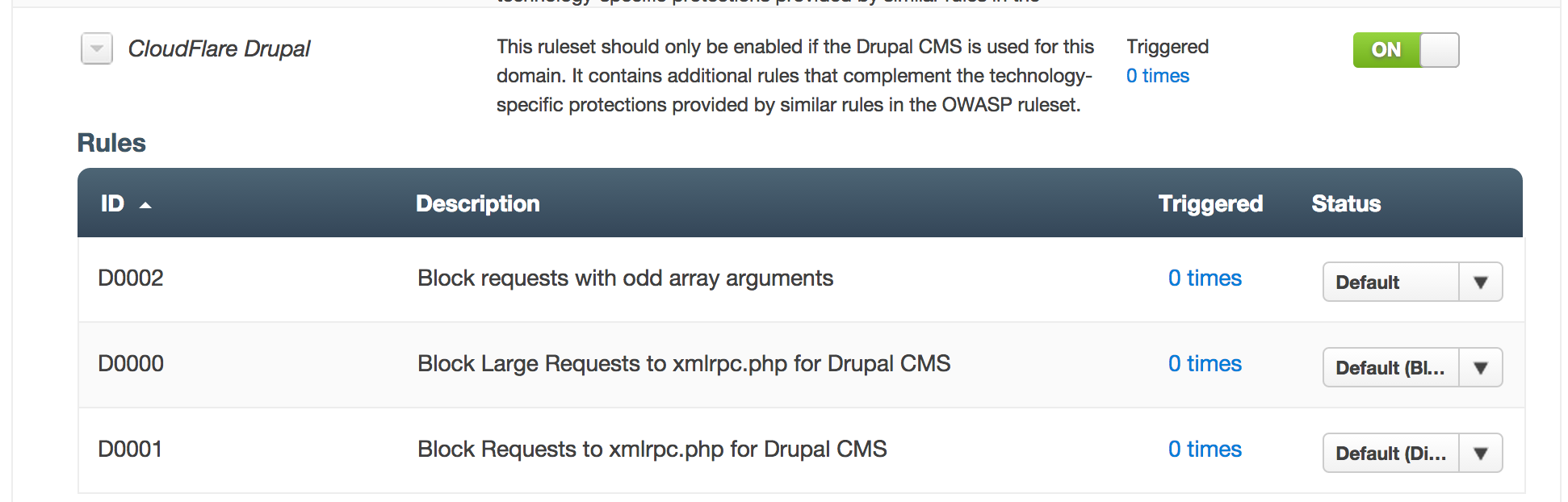
Rule D0002 provides protection against this vulnerability. If you do not have that ruleset enabled and are using Drupal clicking the ON button next to CloudFlare Drupal in the WAF Settings will enable protection immediately.
CloudFlare WAF protection can help mitigate vulnerabilities like this, but it is vital that Drupal 7 users upgrade to the safe version of Drupal immediately.
The network won’t fit in your head anymore
Triggered by a discussion with a customer yesterday, it occurred to me (again?) that network engineers are creatures of habit and control. We have strong beliefs of how networks should be architected, designed and build. We have done so for long times and understand it well. We have tweaked our methods, our tools, our configuration templates. We understand our networks inside out. We have a very clear mental view of how they behave and how packets get forwarded, how they should be forwarded. It’s comfort, it’s habit, we feel (mostly) in control of the network because we have a clear model in our head.
I don’t believe this is a network engineering trait per se. Software engineers want to understand algorithms inside out, they want to understand the data modeling, types structures and relationships.
Uncomfortable
Many of us know the feeling. Something new comes around and it’s hard to put your head around it. It challenges the status quo, it changes how we do things, it changes what we (think we) know. When we are giving responsibility of something new, there is a desire to understand “it” inside out, as a mechanism to be able to control “it”.
Border6 Non-Stop Internet: a Commercial BGP-Based SDN
Several SDN solutions that coexist with the traditional control- and data planes instead of ripping them out and replacing them with the new awesomesauce use BGP to modify the network’s forwarding behavior.
Border6 decided to turn that concept into a commercial product that we dissected in Episode 12 of Software Gone Wild podcast.
Enjoy the show (this time in video format).
Automation – Is the cart before the horse?
 Over the last year I’ve had the opportunity to hear about lots of new and exciting products in the network and virtualization world. The one clear takeaway from all of these meetings has been that the vendors are putting a lot of their focus into ensuring their product can be automated. While I agree that any new product on the market needs to have a robust interface, I’m also sort of shocked at the way many vendors are approaching this. Before I go further, let me clarify two points. First, when I say ‘interface’ I’m purposefully being generic. An interface can be a user interface, it could be a REST interface, a Python interface, etc. Basically, its any means in which I, or something else, can interact with the product. Secondly, I’ll be the first person to tell you that any new product I look at should have a usable REST API interface. Why do I want REST? Simple, because I know that’s something that most automation tools or orchestrators can consume.
Over the last year I’ve had the opportunity to hear about lots of new and exciting products in the network and virtualization world. The one clear takeaway from all of these meetings has been that the vendors are putting a lot of their focus into ensuring their product can be automated. While I agree that any new product on the market needs to have a robust interface, I’m also sort of shocked at the way many vendors are approaching this. Before I go further, let me clarify two points. First, when I say ‘interface’ I’m purposefully being generic. An interface can be a user interface, it could be a REST interface, a Python interface, etc. Basically, its any means in which I, or something else, can interact with the product. Secondly, I’ll be the first person to tell you that any new product I look at should have a usable REST API interface. Why do I want REST? Simple, because I know that’s something that most automation tools or orchestrators can consume.
So what’s driving this? Why are we all of a sudden consumed with the need to automate Continue reading
IPv6 to IPv4 basic setup
Lab goal
The IPv6 VIP should be fc00:85::10.
Setup
Below is the IPv4 real servers configuration which we will use as a base config.
1 | /c/slb/real 1 |
Alteon configuration
1 | /c/slb/virt v6_85_10 |
Notice that we need the pip which is Proxy IP, a.k.a SNAT. Since we translating from IPv6 to IPv4 we need Alteon to act as a proxy and for that it needs IPv4 address to communicate with the real servers.
Test
Summary
Killer Apps in the Gigabit Age | Pew Research Center’s Internet & American Life Project
Very, very funny quote in the Pew Research Report: How could people benefit from a gigabit network? One expert in this study, David Weinberger, a senior researcher at Harvard’s Berkman Center for Internet & Society, predicted, “There will be full, always-on, 360-degree environmental awareness, a semantic overlay on the real world, and full-presence massive open […]
The post Killer Apps in the Gigabit Age | Pew Research Center’s Internet & American Life Project appeared first on EtherealMind.
ECDSA and DNSSEC
Yes, that's a cryptic topic, even for an article that addresses matters of the use of cryptographic algorithms, so congratulations for getting even this far! This is a report of a an experiment conducted in September and October 2014 by the authors to measure the extent to which deployed DNSSEC-validating resolvers fully support the use of the Elliptic Curve Digital Signature Algorithm (ECDSA) with curve P-256.AS-Path Filtering
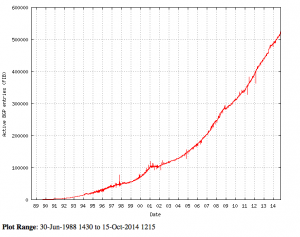
Before we get into the how, let’s talk about the why. According to the CIDR Report, the global IPv4 routing table sits at about 525,000 routes, it has doubled in size since mid 2008 and continues to press upwards at an accelerated rate. This momentum, which in my estimate started around 2006, will most likely never slow down. As network engineers, what are we to do? Sure, memory is as plentiful as we could ask for, but what of TCAM? On certain platforms, like the 7600/6500 on the Sup720 and even some of the ASR1ks we have already surpassed the limits of what they can handle (~512k routes in the FIB). While it is possible to increase the TCAM available for routing information, there are other solutions that don’t include replacing hardware just yet.
As far as I know, adjusting TCAM partitioning on the ASR1000 is not possible at this time.
Before I get too deep into this, I should clarify as many of you (yes, I’m looking at you Fry) are asking yourselves why is an ISP running BGP on a 6500… Many of my customers are small ISPs or data centers that have little to no Continue reading
Why Network Automation Won’t Kill Your Job
I’ve been focusing lately on shortening the gap between traditional automation teams and network engineering. This week I was fortunate enough to attend the DevOps 4 Networks event, and though I’d like to save most of my thoughts for a post dedicated to the event, I will say I was super pleased to spend the time with the legends of this industry. There are a lot of bright people looking at this space right now, and I am really enjoying the community that is emerging.
I’ve heard plenty of excuses for NOT automating network tasks. These range from “the network is too crucial, automation too risky” to “automating the network means I, as a network engineer, will be put out of a job”.
To address the former, check out Ivan Pepelnjak’s podcast with Jeremy Schulman of Schprokits, where they discuss blast radius (regarding network automation).
I’d like to talk about that second excuse for a little bit, because I think there’s an important point to consider.
A Recent Example
A few years back, I was working for a small reseller helping small companies consolidate their old physical servers into a cheap cluster of virtual hosts. For every sizing discussion that Continue reading
When they throw a Cisco guy to do something with HP networking gear
How does the internet work - We know what is networking
…There’s a nice little pdf to get you through HP is aware that most of networking engineers start their learning process in Cisco Networking Academy. Is is a normal course of events if you want to learn networking. Cisco has the very best study materials and best, carefully developed syllabus that is both high quality […]
When they throw a Cisco guy to do something with HP networking gear
Certified Application to Network Isomorphism Engineer, anyone?
Why would network engineers die?
Networking Is Not as Special as We Think It Is
I was listening to the Packet Pushers show #203 – an interesting high-level discussion of policies (if you happen to be interested in those things) – and unavoidably someone had to mention how the networking is all broken because different devices implement the same functionality in different ways and use different CLI/API syntax.
Read more ...Why Network Automation Won’t Kill Your Job
I’ve been focusing lately on shortening the gap between traditional automation teams and network engineering. This week I was fortunate enough to attend the DevOps 4 Networks event, and though I’d like to save most of my thoughts for a post dedicated to the event, I will say I was super pleased to spend the time with the legends of this industry. There are a lot of bright people looking at this space right now, and I am really enjoying the community that is emerging.Why Network Automation Won’t Kill Your Job
I’ve been focusing lately on shortening the gap between traditional automation teams and network engineering. This week I was fortunate enough to attend the DevOps 4 Networks event, and though I’d like to save most of my thoughts for a post dedicated to the event, I will say I was super pleased to spend the time with the legends of this industry. There are a lot of bright people looking at this space right now, and I am really enjoying the community that is emerging.SSLv3 Support Disabled By Default Due to POODLE Vulnerability

For the last week we've been tracking rumors about a new vulnerability in SSL. This specific vulnerability, which was just announced, targets SSLv3. The vulnerability allows an attacker to add padding to a request in order to then calculate the plaintext of encryption using the SSLv3 protocol. Effectively, this allows an attacker to compromise the encryption when using the SSLv3 protocol. Full details have been published by Google in a paper which dubs the bug POODLE (PDF).
Generally, modern browsers will default to a more modern encryption protocol (e.g., TLSv1.2). However, it's possible for an attacker to simulate conditions in many browsers that will cause them to fall back to SSLv3. The risk from this vulnerability is that if an attacker could force a downgrade to SSLv3 then any traffic exchanged over an encrypted connection using that protocol could be intercepted and read.
In response, CloudFlare has disabled SSLv3 across our network by default for all customers. This will have an impact on some older browsers, resulting in an SSL connection error. The biggest impact is Internet Explorer 6 running on Windows XP or older. To quantify this, we've been tracking SSLv3 usage.

