Replacing a Central Firewall
During one of my ExpertExpress engagements I got an interesting question: “could we replace a pair of central firewalls with iptables on the Linux server?”
Short answer: Maybe (depending on your security policy), but I’d still love to see some baseline scrubbing before the traffic hits the server – after all, if someone pwns your server, he’ll quickly turn off iptables.
Read more ...Using frameworks for effective sales presos
Anyone who has ever delivered a presentation or even listened to one knows that the key to an effective presentation is telling a story. If you peruse even a few pages of any of the books about how to deliver a solid presentation, you will find references to storytelling and its role in passing along information throughout history. Yes, we must tell stories. But not all stories work.
So how do you pick a story or a framework for a presentation that will be effective?
Stories vs frameworks
Let me start off by saying that you need both stories and frameworks. When you think about the structure of the points you want to convey, think about frameworks. When you want to make a point real, use a story. When you are delivering a technical presentation especially, you are very unlikely to find a single story that can weave in all the points you want to make. You are, after all, a presenter not a comedian. Don’t try to force all of your points into a long story.
So that leaves you searching for a framework. A framework is simply a way of organizing your points. It is ultimately the framework Continue reading
Network Automation & Controller Questionnaire
With all of the current trends coming in to the industry around policy based network configuration, network automation and controller value add, do you understand why and where the trends are coming from? With organisations, consultancy outfits and independents struggling to see where things are going in the industry, it’s imperative that as an industry we steer eduation and awareness. Sure, the big players are steering things, but you, the fraternity drive the demand. Have your say and the results will be published at the end of the year once there are enough submissions to represent a varying set of opinions.
Do you actually have a customer dying to move to a policy based operations model? Do you know what policy based configuration is and where the industry is going with it?
Does your organisation have a rigid change management stucture? How would your company handle automatic network configuration generation? Would you still need to manually execute the deployment and email with a “green tick” to the change board?
Do you automate your build configuration already? How do you do that? Are you comfortable with it?
Do you have ideas on what value a controller could bring to your organisation? Continue reading
Software Defined Networking – SDN
Software defined networking (SDN) is an approach to computer networking that allows network administrators to manage network services through abstraction of lower level functionality. This is done by decoupling the system that makes decisions about where traffic is sent (the control plane) from the underlying systems that forward traffic to the selected destination (the data […]
The post Software Defined Networking – SDN appeared first on Roger Perkin - Networking Articles.
CCIE RFC List for Routing & Switching Lab Exam
In computer network engineering, a Request for Comments (RFC) is a memorandum published by the Internet Engineering Task Force (IETF) describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems. The list below details all RFC’s relevant to the CCIE Routing and Switching track. CCIE RFC List OSPF RFC […]
The post CCIE RFC List for Routing & Switching Lab Exam appeared first on Roger Perkin - Networking Articles.
Universal SSL: Be just a bit more patient

It turns out it takes a while to deploy SSL certificates for 2 million websites. :-) Even longer when you get a flood of new sign ups. While we'd hoped to have the deployment complete within 24 hours of the announcement, it now looks like it's going to take a bit longer. We now expect that the full deployment will be complete about 48 hours from now (0700 UTC). Beyond that, nothing about the plan for Universal SSL has changed and hundreds of thousands of sites are already active.
Errors you may see
In order to get through the highest priority sites first, we've prioritized provisioning the sites with the most traffic.
While you wait for your site to get provisioned, you may see a certificate mismatch error if you try and visit it over HTTPS. (Rest assured, there are no errors if you visit over HTTP.) The errors over HTTPS are expected and normal during the provisioning process. Examples of what these error looks like in various browsers )Chrome, Safari, Firefox, and Internet Explorer) are below:

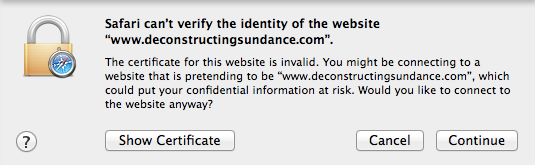
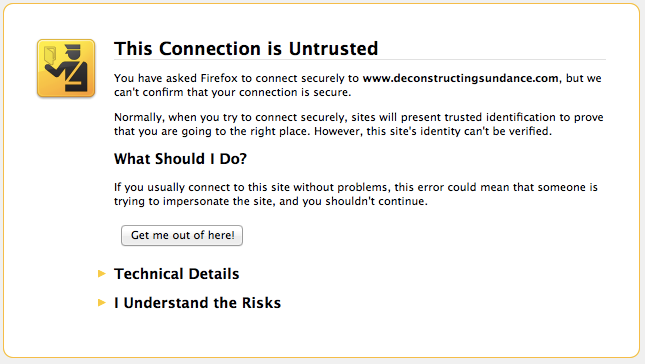
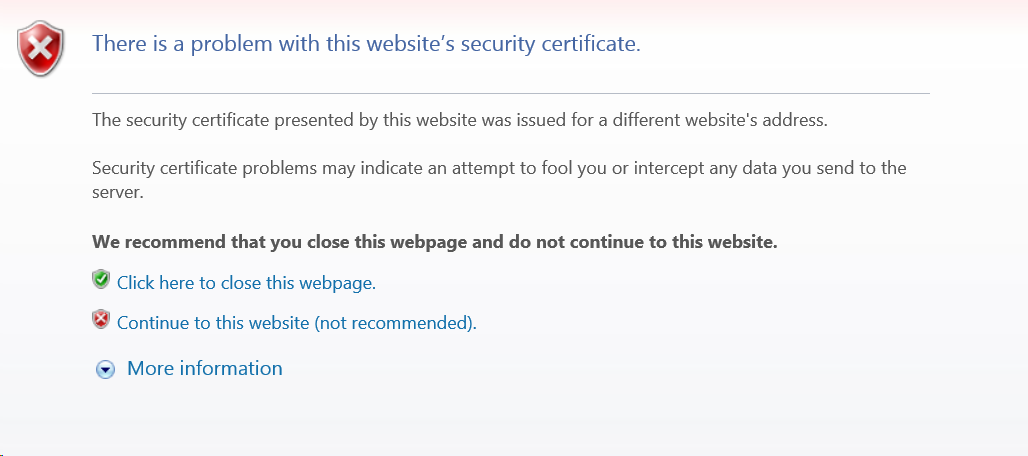
Tracking our progress
To give you a sense of our progress provisioning Universal SSL for your sites, we've updated the alert that Continue reading
Duty for Reporting: Is IT a Servant or a Steward
Duty for Reporting: Is IT a Servant or a Steward?
by Brian Boyko, Contributor - September 30, 2014
There’s an interesting “Ask Slashdot” thread from Slashdot user “MrWHO,” an IT guy who wonders why his clients preferred to receive PDF reports delivered via e-mail instead of signing into the dashboard. After all, dashboards are useful for up-to-the-minute, at-a-glance information (if they’re designed well), and they can also be used to sift through historical data. A report becomes obsolete soon after it is created (though it is far easier to show a PDF-based report to a person who does not have access to the dashboard), so it’s fair to ask why some business people prefer it.
The strange thing that I found was that many, many people were telling MrWHO, essentially, to shut up and stop complaining about the state of affairs. That IT is supposed to serve the clients and if they want reports, they get reports.
And I get that IT’s job is to support the business – or the client – but here’s my question: Does IT serve the business, or is it a steward of the business?
This is getting into some splitting of linguistic hairs, but Continue reading
Origin Server Connection Security with Universal SSL
Earlier today, CloudFlare enabled Universal SSL: HTTPS support for all sites by default. Universal SSL provides state-of-the-art encryption between browsers and CloudFlare’s edge servers keeping web traffic private and secure from tampering.
CloudFlare’s Flexible SSL mode is the default for CloudFlare sites on the Free plan. Flexible SSL mode means that traffic from browsers to CloudFlare will be encrypted, but traffic from CloudFlare to a site's origin server will not be. To take advantage of our Full and Strict SSL mode—which encrypts the connection between CloudFlare and the origin server—it’s necessary to install a certificate on the origin server.
We made Universal SSL free so that everyone can use modern, strong encryption tools to protect their web traffic. More encrypted traffic helps build a safer, better Internet. In keeping with CloudFlare’s goal to help build a better Internet, we have some tips on how to upgrade your site from Flexible SSL to Full or Strict SSL.
Option 1: Full SSL: create a self-signed certificate
Dealing with Certificate Authorities (CAs) can be frustrating, and the process of obtaining a certificate can be time consuming. In the meantime, you can get started by installing a self-signed certificate on your origin server. This Continue reading
CWNP Conference Presentations
If it wasn’t Twitter I probably would not have known there was a CWNP conference going on, but luckily we have Twitter. Looks like it was a 3-day conference about all things wireless, I really will try and go next year. It also looks like they posted the presentations on their website found here, I’ve […]Fryguy.Net – IMPROVED!
My hosting provider, Digital Ocean, has added IPv6 to one of their NY Data centers. Over this weekend, and thanks to Shellshock BASH vulnerability, I finally got around to migrating the server to a new host that is IPv6 enabled. So as of this morning, there is a now a AAAA record for www.fryguy.net! IPv6 Ping […]SDN Skills Prerequisites Per Vendor Certifications
In the previous post, which kicked off a new series, I discussed the need to make some basic choices when building your SDN development plan. Today’s post begins to look more closely at the prerequisites, by examining what vendors tell us through the perquisites included for their SDN certifications. To that end, this post looks at HP, VMWare, and Cisco.
The Big Picture
To learn about SDN, and learn deeply, you will need to invest more than a little time. So you need a plan. That plan will include filling in the prerequisite skills that you may need before learning SDN well, some SDN skills common to most all SDN solutions, and some skills related to particular approaches to SDN that differ quite a bit.

Figure 1: Prerequisites, Foundation, and SDN Silos
Today’s post begins to look at prerequisites. This post focuses on three vendor’s SDN certifications. Cisco, VMWare, and HP all have thriving certification programs, and all three have been rolling out SDN-related certifications. All three programs have a clear vendor focus, which is not surprising. But what do they ask of us a prerequisite?
Follow-up posts will look at the specific topics, what I personally think people Continue reading
Managing the Network as a Fabric — About Time!
Earlier this September, I attended the Tech Field Day Networking Field Day 8 event. Over the course of three days, we saw presentations from many very interesting vendors including a mix of startups and established market leaders. One trend that really stuck out to me more this time around than at any previous NFD event was a nearly ubiquitous emphasis on data center network fabric management. In other words, truly managing an entire data center network (or at least a sub-block of it) as a single unit.
Just of the NFD8 presenters who were providing this option, we had Cisco with their ACI model (but it stands to reason that even the now-well-established FEX model has very similar capabilities), Big Switch Networks with their Big Cloud Fabric, Pluribus Networks’ Netvisor Software Defined Fabric, and Nuage Networks Virtual Services Platform. Each of these products has unique value propositions, so I’m not suggesting they’re all the same but rather pointing out that this concept of fabric-level management is clearly at the forefront of most, if not all, leading-edge data center solutions at this point. The concept has been building for a couple years, and other vendors are also pursuing this model Continue reading
Show 206 – Brocade’s OpenDaylight-Based Vyatta Controller – Sponsored
If you watch the software defined networking space, you might have noticed that Brocade has been quietly hiring a sharp group of actual (not self-proclaimed) thought leaders and developers. The question has been, “To what end? What’s Brocade going to do with all of these capable folks?” Today, we can answer that question. Brocade has built an […]
Author information
The post Show 206 – Brocade’s OpenDaylight-Based Vyatta Controller – Sponsored appeared first on Packet Pushers Podcast and was written by Ethan Banks.
Get Out of the Way
I have a lot of memories that have emerged from my years as a network engineer — from funny stories to profound moments to those times when I felt like a complete idiot (because we’re all idiots sometimes). One of those formative moments was when I was agonizing over the decision to leave the Global Escalation Team in customer support and move into an engineering focused role. I agonized over the change for a number of reasons.
I was moving out of something I knew well, directly supporting customers in a very real way. The Escalation Team was the last stop in customer support. If we couldn’t solve it, it couldn’t be solved. That meant a lot of high pressure customer interaction, doing troubleshooting work on really hard, really big problems. I learned a ton. The Escalation Team was also the top of the hill in my world. There wasn’t anyplace, really, I could imagine wanting to be more than working directly with customers, being able to say at the end of the day, “I helped someone solve a real problem,” or even better, “I helped someone learn how to solve a real problem.” Not only for external customers, Continue reading
Introducing Universal SSL

The team at CloudFlare is excited to announce the release of Universal SSL™. Beginning today, we will support SSL connections to every CloudFlare customer, including the 2 million sites that have signed up for the free version of our service.
This morning we began rolling out the Universal SSL across all our current customers. We expect this process to be complete for all current customers before the end of the day. Yesterday, there were about 2 million sites active on the Internet that supported encrypted connections. By the end of the day today, we'll have doubled that.
For new customers who sign up for CloudFlare's free plan, after we get through provisioning existing customers, it will take up to 24 hours to activate Universal SSL. As always, SSL for paid plans will be provisioned instantly upon signup.
How does it work?
For all customers, we will now automatically provision a SSL certificate on CloudFlare's network that will accept HTTPS connections for a customer's domain and subdomains. Those certificates include an entry for the root domain (e.g., example.com) as well as a wildcard entry for all first-level subdomains (e.g., www.example.com, blog.example.com, etc. Continue reading
Building a Small Cloud with UCS Mini
During the last round of polishing of my Designing Infrastructure for Private Clouds Interop New York session (also available in webinar format) I wondered whether one could use the recently-launched UCS Mini to build my sample private cloud.
Read more ...High availability in horizontally-scaled applications
The networking industry has a somewhat unique relationship with high availability. For compute, storage, and applications, failures are somewhat tolerable because they tend to be more isolated (a single server going down rarely impacts the rest of the servers). However, the network’s central role in connecting resources makes it harder to contain failures. Because of this, availability has been an exercise in driving uptime to near 100 percent.
It is absolutely good to minimize unnecessary downtime, but is the pursuit of perfect availability the right endeavor?
Device uptime vs application availability
We should be crystal clear on one thing: the purpose of the network is not about providing connectivity so much as it is about making sure applications and tenants have what they need. Insofar as connectivity is a requirement, it is important, but the job doesn’t end just because packets make it from one side to the other. Application availability and application experience are far more dominant in determining whether infrastructure is meeting expectations.
With that in mind, the focus on individual device uptime is an interesting but somewhat myopic approach to declaring IT infrastructure success. By focusing on building in availability at the device level, it is easy Continue reading
Shellshock protection enabled for all customers
On Thursday, we rolled out protection against the Shellshock bash vulnerability for all paying customers through the CloudFlare WAF. This protection was enabled automatically and immediately starting blocking malicious requests.
We had a number of requests for protection from Shellshock for all our customers, including those on the Free plan.
After observing the actual Shellshock traffic across our network and after seeing the true severity of the vulnerability become clear, we've built and tested a special Basic ShellShock Protection for all customers.
That protection is now operating and enabled for every CloudFlare customer (Free, Pro, Business and Enterprise). Paying customers have the additional protection of more complex Shellshock rules in the CloudFlare WAF.
Every CloudFlare customer is now being protected from the most common attack vectors based on the Shellshock problem and paying customers continue to have the more advanced protection that was rolled out yesterday.
The Seven Layer Model is Dead
Whether we have the funeral in New Orleans style (with a lot of brass and, well, other stuff), or in the more somber style we’re all so accustomed to– or even perhaps dance down the road singing, “ding dong, the model’s dead” — it’s time to pack the seven layer model into a virtual coffin […]