So what if the tables wobble a little?
When I first met Cumulus, they were working out of a borderline-sketchy kind of warehouse space they had outgrown long before I showed up.
My job was to “make things better.” Initially, this had a lot to do with boxes and taking out garbage. I threw out a pile of flattened boxes about three feet high early on. The boxes had been stacked and tossed and shoved into a massive pile that consumed the small loft that hovered over the space. These people have no idea how dangerously close they came to becoming an episode of Hoarders.
Despite the mess, they are very good people. I’d been there only a short time when, one day, the bottom fell out of a box of stuff I was moving. Instantly I was surrounded by people who had everything picked up before I’d even registered what happened. One of them was on the phone the entire time and never missed a beat, I think he even made a sale. They were halfway back to their desks before I managed to say “thank you.”
I am not an engineer, but I am married to one, which is almost the same thing. (That Continue reading
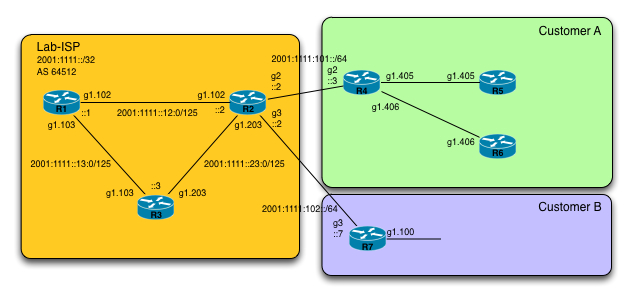
Trying out IPv6 Prefix Delegation
In this post i will show how and why to use a feature called IPv6 Prefix Delegation (PD).
IPv6 prefix delegation is a feature that provides the capability to delegate or hand out IPv6 prefixes to other routers without the need to hardcode these prefixes into the routers.
Why would you want to do this? – Well, for one is the administration overhead associated with manual configuration. If the end-customer only cares about the amount of prefixes he or she receives, then it might as well be handed out automatically from a preconfigure pool. Just like DHCP works today on end-user systems.
On top of that, by configuring a redistribution into BGP just once, you will automatically have reachability to the prefixes that has been handed out, from the rest of your SP network.
So how do you go about configuring this? – Well, lets take a look at the topology we’ll be using to demonstrate IPv6 Prefix Delegation.
First off, we have the SP core network which consists of R1, R2 and R3. They are running in AS 64512 with R1 being a BGP route-reflector for the IPv6 unicast address-family. As an IGP we are running OSPFv3 to provide Continue reading
Announcing Keyless SSL™: All the Benefits of CloudFlare Without Having to Turn Over Your Private SSL Keys

CloudFlare is an engineering-driven company. This is a story we're proud of because it embodies the essence of who we are: when faced with a problem, we found a novel solution. Technical details to follow but, until then, welcome to the no hardware world.
Fall in San Francisco
The story begins on a Saturday morning, in the Fall of 2012, almost exactly two years ago. I got a call on my cell phone that woke me. It was a man who introduced himself as the Chief Information Security Officer (CISO) at one of the world's largest banks.
"I got your number from a reporter," he said. "We have an incident. Could you and some of your team be in New York Monday morning? We'd value your advice." We were a small startup. Of course we were going to drop everything and fly across the country to see if we could help.
I called John Roberts and Sri Rao, two members of CloudFlare's team. John had an air of calm about him and owned more khaki pants than any of the rest of us. Sri was a senior member of our technical operations team and could, already at that point, Continue reading
Resiliency in Controller based Network Architectures
Last week Ivan Pepelnjak wrote an article about the failure domains of controller based network architectures. At the core of SDN solutions is the concept of a controller, which in most cases lives outside the network devices themselves. A controller as a central entity controlling the network (hence its name) provides very significant values and capabilities to the network. We have talked about these in this blog many times.
Centralized Control
When introducing a centralized entity into any inherently distributed system, the architecture of such a system needs to carefully consider failure domains and scenarios. Networks have been distributed entities, with each device more or less independent and a huge suite of protocols defined to manage the distributed state between all of them. When you think about it, it’s actually quite impressive to think about the extend of distribution we have created in networks. We have created an extremely large distributed system with local decision making and control. I am not sure there are too many other examples of complex distributed systems that truly run without some form of central authority.
It is exactly that last point that we networking folks tend to forget or ignore. Many control systems in Continue reading
Dynamic FCoE – Sparse-Mode FCoE Strikes Again
A while ago Cisco added dynamic FCoE support to Nexus 5000 switches. It sounded interesting and I wanted to talk about it in my Data Center Fabrics update session, but I couldn’t find any documentation at that time.
In the meantime, the Configuring Dynamic FCoE Using FabricPath configuration guide appeared on Cisco’s web site and J Metz wrote a lengthly blog post explaining how it all works, triggering a severe attack of déjà vu.
Read more ...BASICS- ICMP REDIRECTS
Redirect, ICMP type 5, is used by routers to notify hosts of another router on the data link that should be used for a particular destination.
TOPOLOGY
——————–
———- ROUTER R3——|
| Internet | / |——PC2 10.10.10.1
——— /
| /
ROUTER R1 ROUTER R2
172.16.10.40| | 172.16.10.5
| |
—————-LAN——————————–
|
|
PC1
172.16.10.1
Gateway 172.16.10.40
—————————————-
Consider above topology,where PC1 has default gatway config as 172.16.10.40 .PC1 send packet to router R1 to reach remote destination 10.10.10.1.Router R1 checks its routing table and find that next-hop to reach 10.10.10.1 is Router R2.SO now the ROuter R1 has to fwd packet througth the same interface on which it was received.Router R1 fwd packet to Router R2 and also send ICMP redirect message to PC1.This informs about the best path to reach destination 10.10.10.1 is through Continue reading
BASICS – PROXY ARP
Its very important for routing and is enabled default in IOS.
Its method by which router made himself available to the host.How ?
|——-ROuter——|
| |
PC1 PC2
IP 10.10.20.1/24 10.10.40.1/24
Consider that HostA(10.10.20.1/24) want to send traffic to HostB of diff subnet (10.10.40.1/24).
Host A neither have any default gateway configured nor it knows how to reach router.It will send arp request for 10.10.40.1,local router
when receives the request and also know how to reach subnet 10.10.40.0,will reply arp with its own hardware address.
Host A will see this reply, cache it, and send future IP packets for host B to the gateway. The gateway will forward such packets to
host B by the usual IP routing mechanisms. The gateway is acting as an agent for host B, which is why this technique is called “Proxy ARP”; we will refer to this as a transparent subnet gateway or ARP subnet gateway.
ARP cache entries generally shows multiple ip address are mapped to single hardware addresss ,It that case proxy arp is used and single hardware addresss is of router interface and multiple ip address is of hosts.
BASICS – ARP
How the ARP works ? Basic question but very imp to know it.
ARP is address resolution protocol,used to resolve logical IP address to physical hardware address.
ROUTER
|
|
———LAN——-
| |
| |
PC1 PC2
10.10.10.1 10.10.10.14
Consider that PC1 want to communicate with PC2.What is the actual process to communicate b/w them ?
PC want to sent traffic to PC2 ,it has got layer 3 address for source(10.10.10.1) and also destination (10.10.10.14).
It will move from upper layer down to lower layer 2 i.e data link layer.Layer 2 need to have source and destination MAC
address information to process further.PC1 has layer 3 information for source and destination but no layer 2 information for destination .
Here comes the saviour known as ARP .PC1 will send broadcast into the LAN asking that whoever owns IP 10.10.10.14 respond with its mac address.
The broadcast packet will have following info.
Source Ip : 10.10.10.1
Destination IP : 10.10.10.14
Source MAC : MAC Continue reading
On Policy in the Data Center: Comparing OpenStack policy efforts
(This post was written by Tim Hinrichs and Scott Lowe, with contributions from Pierre Ettori, Aaron Rosen, and Peter Balland.)
In the first two parts of this blog series we discussed the problem of policy in the data center and the features that differentiate solutions to that problem. In this post, we give a high-level overview of several policy efforts within OpenStack.
Remember that a policy is a description of how (some part of) the data center ought to behave, a service is any component in the data center that has an API, and a policy system is designed to manage some combination of past, present, and future policy violations (auditing, monitoring, and enforcement, respectively).
The overview of OpenStack policy efforts talks about the features we identified in part 2 of this blog series. To recap, those features are:
- Policy language: how expressive is the language, is the language restricted to certain domains, what features (e.g. exceptions) does it support?
- Policy sources: what are the sources of policy, how do different sources of policy interact, how are conflicts dealt with?
- Services: which other data center services can be leveraged and how?
- Actions: what does the system do once Continue reading
Making better use of libvirt hooks
Libvirtd includes handy hooks for doing management work at various phases in the lifecycle of the libvirt daemon, attached networks, and virtual machines. I've been using these hooks for various things and have found them particularly useful for management of short-lived Linux containers. Some of my use cases for these hooks include:- changing network policy
- instantiating named routing tables
- creating ramdisks for use by containers
- pre-loading data before container startup
- archiving interesting data at container shutdown
- purging data at container destruction
Here's how the hooks work on a system with RedHat lineage:
The hook scripts live in /etc/libvirt/hooks. The scripts are named according to their purpose. I'm focusing right now on the LXC hook which is named /etc/libvirt/hooks/lxc. Note that neither the directory, nor the scripts exist by default.
The lxc script is called several times in each container's lifecycle, and is passed arguments that specify the libvirt domain id and the lifecycle phase. During startup and shutdown of one of my LXC systems, the script gets called five times, like this:
/etc/libvirt/hooks/lxc MyAwesomeContainer prepare begin -
/etc/libvirt/hooks/lxc MyAwesomeContainer start begin -
/etc/libvirt/hooks/lxc MyAwesomeContainer started begin -
/etc/libvirt/hooks/lxc MyAwesomeContainer stopped end -
/etc/libvirt/hooks/lxc MyAwesomeContainer release end -
In addition to having those Continue reading
Community Show – Killing the Spanning Tree with Anthony Sequeira and Orhan Ergun
No country for old men !!. This week in the Orhan Show, Anthony Sequeira and Orhan Ergun are talking about spanning tree , its drawbacks, spanning tree modes, technologies which can eliminate the spanning tree’s drawbacks or completely do not use it. Orhan recommends all audience to read this blog post about spanning tree which […]
Author information
The post Community Show – Killing the Spanning Tree with Anthony Sequeira and Orhan Ergun appeared first on Packet Pushers Podcast and was written by Orhan Ergun.
Community Show – Killing the Spanning Tree with SPB,TRILL,Fabricpath from Anthony Sequeira and Orhan Ergun
[player] No country for old men !!. This week in the Orhan Show, Anthony Sequeira and Orhan Ergun are talking about spanning tree , its drawbacks, spanning tree modes, technologies which can eliminate the spanning tree’s drawbacks or completely do not use it. Orhan recommends all audience to read this blog post about spanning tree […]
The post Community Show – Killing the Spanning Tree with SPB,TRILL,Fabricpath from Anthony Sequeira and Orhan Ergun appeared first on Packet Pushers.
Network Automation with Python, Ansible, and Twitter Integration
In the code I pushed last month, I created an Ansible playbook that pulls interface stats from a Nexus 9000 (or any other Nexus device supporting NX-API) and then creates a template report for those stats. It was pretty vanilla, nothing fancy about it.
There have been integrations with other social platforms, but to be honest, the one that has been stuck in my brain is Hubot that is used at GitHub. Several months back I remember hearing about Hubot for the second or third time while listening to the Cloudcast podcast with Mark Imbriaco (just before he went to Digital Ocean). It is amazing to see what can be done Continue reading
Running Docker on OSX and Other Fun Things
I have a friend who wants to test a tool I wrote in perl (yes yes, I know) but it seemed to me that it was going to be a big pain for him to have to install all the … Continue reading
If you liked this post, please do click through to the source at Running Docker on OSX and Other Fun Things and give me a share/like. Thank you!
Automating a Multi-Action Security Workflow with VMware NSX
This post was written by VMware’s John Dias, (VCP-DCV), Sr. Systems Engineer, Cloud Management Solutions Engineering Team, and Hadar Freehling, Security & Compliance Systems Engineer Specialist
***
Through a joint effort with Hadar Freehling, one of my esteemed peers here at VMware, we co-developed a proof-of-concept workflow for a network security use case. Hadar created a short video showing and explaining the use case, but in summary this is a workflow that reacts to and remediates a security issue flagged by third-party integration with VMware NSX. In the video, TrendMicro is used but it could be any other partner integration with vShield Endpoint.
Here’s what happens:
- A virus is detected on a VM and is quarantined by the AV solution
- The AV solution tags the VM with an NSX security tag
- VMware NSX places the VM in a new Security Group, whose network policies steer all VM traffic through an intrusion prevention system (IPS)
- vCenter Orchestrator (vCO) monitors the security group for changes and when a VM is added
- a snapshot of the VM is taken for forensic purposes
- a vSpan session (RSPAN) is set up on the Distributed Virtual Switch to begin capturing inbound/outbound traffic on the VM
- once the Continue reading
Nontraditional network integrations
If you listen to the chatter around the network industry, you are starting to see a lot more discussion about integration. While particularly clueful individuals have been hip to the fact for awhile, it seems the industry at large is just awakening to the idea that the network does not exist in isolation. Put differently, the idea that the network can be oblivious to everything around it (and they to the network) is losing steam as orchestration frameworks like OpenStack take deeper root.
Having glue between the major infrastructure components is critical to having seamless operation across all the resources required to satisfy an application or tenant workload. But there is additional (potentially greater!) advantage to be had by performing some less traditional integrations.
Where do integrations matter?
There are two primary reasons to have integrated infrastructure: to cut down on time and to cut down on mistakes. Integration is almost always in support of automation. Depending on the exact integration, that automation is in support of making things faster and cheaper, or in making things less prone to Layer 8 issues.
The point here is that integration is rarely done just for the sake of integration. Companies need Continue reading
You’ve been doing the same thing for the last 20 years
When we were discussing my autumn travel plans, my lovely wife asked me “What are you going to talk about in Bern?” She has a technical background, but I didn’t feel like going into the intricacies of SDN, SDDC and NetOps, so I told her the essence of my keynote speech:
Read more ...The History of Open
Everybody is talking about “open” this or that – from Cisco making claims to new companies embracing open source code as a means of developing or accelerating their go-to-market strategies. But what does “open” really mean?
One challenge in using a broad and you might say amorphous term like open is that it can lead to confusion or a negative first impression that “this is just marketing.” To get some perspective, let’s look back a bit and see how we got to this point of open and what the original intent was.
Open systems are computer systems that provide some combination of interoperability, portability, and open software standards. (“Open” can also refer to specific installations that are configured to allow unrestricted access by people and/or other computers; this article does not discuss that meaning.)
The term “open” was popularized in the early 1980s, mainly to describe systems based on Unix, especially in contrast to the more entrenched mainframes, minicomputers, and engineering workstations in use at that time. Unlike older legacy systems, the newer generation of Unix systems featured standardized programming interfaces and peripheral interconnects. Third party development of hardware and software was Continue reading
OpenDaylight in the Enterprise: OpenFlow and NETCONF in the right places
When using Open Daylight (ODL), two open standards for configuration are OpenFlow & NETCONF. Which is the better choice ? Is there an option for both ? A use case on when to use OpenFlow and NETCONF protocols in the Enterprise by using the best features of each protocol.
The post OpenDaylight in the Enterprise: OpenFlow and NETCONF in the right places appeared first on EtherealMind.