Hedge 150: Micah Beck and Universal Broadband
What would the Internet look like—or what kinds of services would need to be developed and deployed—to make boradband class service available to every user? What could this kind of development do to drive entire societies forward? Micah Beck, from the University of Tennessee, joins Tom Ammon and Russ White to discuss universal broadband on this episode of the Hedge.
Day Two Cloud 167: Interviewing At A Huge Tech Company
On today's Day Two Cloud we talk about what it's like to interview for a job at a massive tech company. How do you get yourself in line? What can you expect from the interview? How do you prepare? How do you overcome your own imposter syndrome? Our guest is Nathaniel Avery, Outbound Product Manager at Google Cloud. He recently ran the gauntlet of the tech interview, and is here to share tips and insights on the process.
The post Day Two Cloud 167: Interviewing At A Huge Tech Company appeared first on Packet Pushers.
Day Two Cloud 167: Interviewing At A Huge Tech Company
On today's Day Two Cloud we talk about what it's like to interview for a job at a massive tech company. How do you get yourself in line? What can you expect from the interview? How do you prepare? How do you overcome your own imposter syndrome? Our guest is Nathaniel Avery, Outbound Product Manager at Google Cloud. He recently ran the gauntlet of the tech interview, and is here to share tips and insights on the process.Tier 1 Carriers Performance Report: September, 2022
The post Tier 1 Carriers Performance Report: September, 2022 appeared first on Noction.
Cloudflare DDoS threat report 2022 Q3

This post is also available in Français, Español, Português, 한국어, 简体中文, 繁體中文, and 日本語.

Welcome to our DDoS Threat Report for the third quarter of 2022. This report includes insights and trends about the DDoS threat landscape - as observed across Cloudflare’s global network.
Multi-terabit strong DDoS attacks have become increasingly frequent. In Q3, Cloudflare automatically detected and mitigated multiple attacks that exceeded 1 Tbps. The largest attack was a 2.5 Tbps DDoS attack launched by a Mirai botnet variant, aimed at the Minecraft server, Wynncraft. This is the largest attack we’ve ever seen from the bitrate perspective.
It was a multi-vector attack consisting of UDP and TCP floods. However, Wynncraft, a massively multiplayer online role-playing game Minecraft server where hundreds and thousands of users can play on the same server, didn’t even notice the attack, since Cloudflare filtered it out for them.
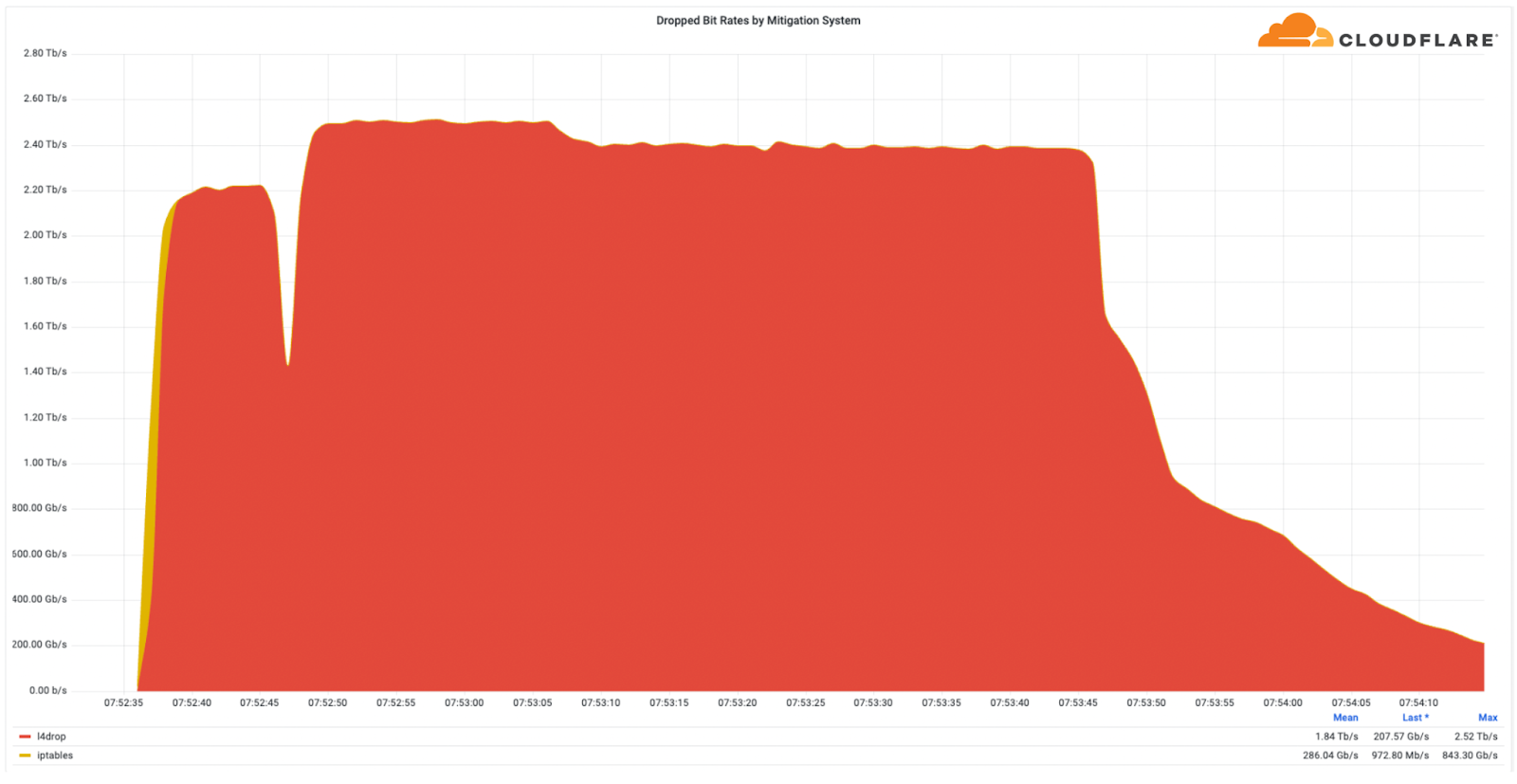
General DDoS attack trends
Overall this quarter, we've seen:
- An increase in DDoS attacks compared to last year.
- Longer-lasting volumetric attacks, a spike in attacks generated by the Mirai botnet and its variants.
- Surges in attacks targeting Continue reading
OSPF External Routes (Type-5 LSA) Mysteries
Daniel Dib posted a number of excellent questions on Twitter, including:
While forwarding a received Type-5 LSA to other areas, why does the ABR not change the Advertising Router ID to it’s own IP address? If ABR were able to change the Advertising Router ID in the Type-5 LSA, then there would be no need for Type-4 LSA which meant less OSPF overhead on the network.
TL&DR: The current implementation of external routes in OSPF minimizes topology database size (memory utilization)
Before going to the details, try to imagine the environment in which OSPF was designed, and the problems it was solving.
OSPF External Routes (Type-5 LSA) Mysteries
Daniel Dib posted a number of excellent questions on Twitter, including:
While forwarding a received Type-5 LSA to other areas, why does the ABR not change the Advertising Router ID to it’s own IP address? If ABR were able to change the Advertising Router ID in the Type-5 LSA, then there would be no need for Type-4 LSA which meant less OSPF overhead on the network.
TL&DR: The current implementation of external routes in OSPF minimizes topology database size (memory utilization)
Before going to the details, try to imagine the environment in which OSPF was designed, and the problems it was solving.
IPv6 Extension Headers Revisited
The topic of the robustness of IPv6 Extension Headers has experienced a resurgence of interest in recent months. I’d like to update our earlier report on this topic with some more recent measurement data.Palo Basic Setup
A run through using the CLI to set up a Palo firewall at home covering the initial configuration, upgrading, BGP routing and a basic firewall policy.
Tech Bytes: Get Early Attack Detection And Fast Response With Fortinet FortiDeceptor (Sponsored)
Today on the Tech Bytes podcast we’re talking deception. That is, deceiving attackers that try to exploit your network by creating fake assets and infrastructure. Sponsor Fortinet is here to talk about using deception techniques to spot intruders via its FortiDeceptor product. We’ll also talk about threat reconnaissance capabilities of a product called FortiRecon. Our guest is Moshe Ben Simon, VP of Product Management.
The post Tech Bytes: Get Early Attack Detection And Fast Response With Fortinet FortiDeceptor (Sponsored) appeared first on Packet Pushers.