Creating BGP Multipath Lab with netsim-tools
I was editing the BGP Multipathing video in the Advanced Routing Protocols section of How Networks Really Work webinar, got to the diagram I used to explain the intricacies of IBGP multipathing and said to myself “that should be easy (and fun) to set up with netsim-tools”.
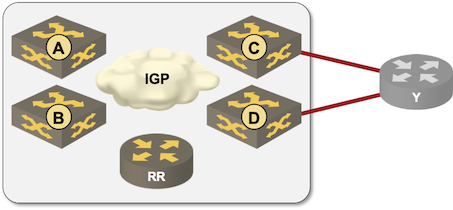
Fifteen minutes later1 I had the lab up and running and could verify that BGP works exactly the way I explained it in the webinar (at least on Cisco IOS).
Creating BGP Multipath Lab with netlab
I was editing the BGP Multipathing video in the Advanced Routing Protocols section of How Networks Really Work webinar, got to the diagram I used to explain the intricacies of IBGP multipathing and said to myself “that should be easy (and fun) to set up with netlab”.

Fifteen minutes later1 I had the lab up and running and could verify that BGP works exactly the way I explained it in the webinar.
Satyen Desai: Why I joined Cloudflare and why I am helping Cloudflare grow in Southeast Asia and Korea


I am excited to announce that I have joined Cloudflare as the Head of Southeast Asia and Korea (SEAK) region to help build a better Internet and to expand Cloudflare’s growing customer, partner and local teams across all the countries in SEAK. Cloudflare is at an emergence phase in this region, with immense growth potential, and this is just the beginning. Cloudflare has had a lot of success globally and our charter is to build on that success and momentum to grow our presence locally to address the demands in Singapore, Malaysia, Thailand, Indonesia, Philippines, Indochina and Korea. Customer engagements in each of the countries in SEAK presents a unique, rich and fulfilling engagement each with their own intricacies.
A little about me
I was born in India (Surat, Gujarat), and at the age of four our family moved to Bahrain where we lived for eight years. We then moved to New Zealand, which is where I completed my senior years of high school and also my Bachelor’s Degree in Information Engineering at Massey University. After graduation, we moved to Melbourne, Australia which is our family home and where my career started.
I love meeting and working with diverse and Continue reading
Utilizing BGP Communities for traffic steering – part 1: Firewalls
Overview:
I typically spend more time in the enterprise data center than most of our team members and this comes with its own unique set of problems. One discussion that seems to never fail to come up is “where do I put the Firewalls (FWs)?”. That is typically followed by I have a disaster recovery or backup site with FWs there as well. This inevitably leads to a state management problem. Let’s look at how we can utilize BGP to address this problem:
- what is a BGP standard community
- BGP best path selection process
- how to utilize them to steer traffic
This is something most service providers deal with on a daily basis but can be new to an enterprise.
BGP Standard communities
A BGP community is a route attribute that, essentially provides extra information for someone to take action or glean information from the route such as where it came from (location, type, organizational role).
By definition, a community is a 32 bit number that can be included with a route and when utilizing the new community format is displayed as (0-65535):(0-65535). It is recommend to utilize the new community format versus the old community format which is Continue reading
Live Webinar: How Routers Really Work

This Friday (the 12th) I’m presenting a live webinar on How Routers Really Work over at Pearson. From the description:
This training will peer into the internal components of a router, starting with an explanation of how a router switches packets. This walk through of a switching path, in turn, will be used as a foundation for explaining the components of a router, including the various tables used to build forwarding tables and the software components used to build these tables.
Please join me by registering here.
I’ve changed just a few of the slides from the last time I gave this talk and reordered some things.
Tech Bytes: Balancing Remote Work And Back-To-Office Priorities With AppNeta (Sponsored)
As forecasts vary between a full return to office and distributed work, IT organizations have to figure out how to monitor and manage work-from-anywhere. This Tech Bytes episode, sponsored by AppNeta, explores how IT can balance on-prem and distributed-work priorities. AppNeta also recently introduced a new monitoring point that runs on Cisco Catalyst switches for improved visibility into app performance at branch and remote sites.
The post Tech Bytes: Balancing Remote Work And Back-To-Office Priorities With AppNeta (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Balancing Remote Work And Back-To-Office Priorities With AppNeta (Sponsored)
As forecasts vary between a full return to office and distributed work, IT organizations have to figure out how to monitor and manage work-from-anywhere. This Tech Bytes episode, sponsored by AppNeta, explores how IT can balance on-prem and distributed-work priorities. AppNeta also recently introduced a new monitoring point that runs on Cisco Catalyst switches for improved visibility into app performance at branch and remote sites.Why Modern Cybersecurity Requires AI
How to hamper the adversary using AI-Powered cybersecurity.Network Break 358: Unpacking Juniper’s Strategic Objectives; Intel Details New Infrastructure Chip
This weeks' Network Break discusses Juniper's Analyst & Influencer day plus a new Wi-Fi 6E announcement. Intel is teaming up with Google to develop a chip for offloading network, security, and storage jobs from the CPU (but Intel won't call it a DPU). And the FCC revokes authorization for China Telecom to operate in the United States.
The post Network Break 358: Unpacking Juniper’s Strategic Objectives; Intel Details New Infrastructure Chip appeared first on Packet Pushers.
Network Break 358: Unpacking Juniper’s Strategic Objectives; Intel Details New Infrastructure Chip
This weeks' Network Break discusses Juniper's Analyst & Influencer day plus a new Wi-Fi 6E announcement. Intel is teaming up with Google to develop a chip for offloading network, security, and storage jobs from the CPU (but Intel won't call it a DPU). And the FCC revokes authorization for China Telecom to operate in the United States.Sizing Up Post-Quantum Signatures
Quantum computers are a boon and a bane. Originally conceived by Manin and Feyman to simulate nature efficiently, large-scale quantum computers will speed-up innovation in material sciences by orders of magnitude. Consider the technical advances enabled by the discovery of new materials (with bronze, iron, steel and silicon each ascribed their own age!); quantum computers could help to unlock the next age of innovation. Unfortunately, they will also break the majority of the cryptography that’s currently used in TLS to protect our web browsing. They fall in two categories:
- Digital signatures, such as RSA, which ensure you’re talking to the right server.
- Key exchanges, such as Diffie–Hellman, which are used to agree on encryption keys.
A moderately-sized stable quantum computer will easily break the signatures and key exchanges currently used in TLS using Shor’s algorithm. Luckily this can be fixed: over the last two decades, there has been great progress in so-called post-quantum cryptography. “Post quantum”, abbreviated PQ, means secure against quantum computers. Five years ago, the standards institute NIST started a public process to standardise post-quantum signature schemes and key exchanges. The outcome is expected to be announced early 2022.
At Cloudflare, we’re not just following this Continue reading
How To Prevent Arthritis From Computer Usage?
Arthritis is one of the most common conditions faced by office workers. It can be mild or severe. Sometimes the pain can be unmanageable too. Besides that, it can affect you permanently.
If you work on computers every day, you are more likely to suffer from arthritis. But worry no more. Here are some measures that you can take to prevent arthritis from computer usage.
Maintain Movement
Does your job require you to sit in front of a computer all day? If so, then you need to consider taking breaks in between. That is because sitting in one position can stiffen your muscles. By moving around, you can release tension.
Besides that, you should also take small breaks when performing a repetitive task. For example, if you type consistently for long periods, stop in between. And for at least five minutes, ensure that your hands are at rest.
Keep Your Feet In Good Position
If you work on a high desk, then it’s most likely your feet won’t be touching the ground. That is something you need to avoid because it can stress your lower back. As a result, the risk of arthritis development will increase.
One way to ensure Continue reading
Feedback: Business Aspects of Networking
Every other blue moon someone asks me to do a not-so-technical presentation at an event, and being a firm believer in frugality I turn most of them into live webinar sessions collected under the Business Aspects of Networking umbrella.
At least some networking engineers find that perspective useful. Here’s what Adrian Giacometti had to say about that webinar:
Feedback: Business Aspects of Networking
Every other blue moon someone asks me to do a not-so-technical presentation at an event, and being a firm believer in frugality I turn most of them into live webinar sessions collected under the Business Aspects of Networking umbrella.
At least some networking engineers find that perspective useful. Here’s what Adrian Giacometti had to say about that webinar:
Proxmox Import QCOW2 Image
I recently migrated my homelab servers from running bare metal KVM/QEMU on Ubuntu, to running Proxmox as a hypervisor. As part of that process I migrated some of the VM's from KVM to Proxmox. In this post I will show you how I imported the qcow2 VM's from KVM/QEMU into...continue reading
Managing Hierarchical Device Configurations
Parsing and modifying IOS-like hierarchical device configurations is an interesting challenge, more so if you have no idea what the configuration commands mean or whether their order is relevant (I’m looking at you, Ansible ;).
Network to Code team decided to solve that problem for good, open-sourced Hierarchical Configuration Python library, and published a getting started article on their blog.