Weekend Reads 121820
This is a rather oversized edition of the weekend reads… because I seem to have saved up a lot more links than usual.
The PC revolution started off life 35 years ago this week. Microsoft launched its first version of Windows on November 20th, 1985, to succeed MS-DOS. It was a huge milestone that paved the way for the modern versions of Windows we use today. While Windows 10 doesn’t look anything like Windows 1.0, it still has many of its original fundamentals like scroll bars, drop-down menus, icons, dialog boxes, and apps like Notepad Continue reading
Setting Boundaries Before You’re Swamped

We’re at the tail end of 2020 and things are hopeful for 2021. People are looking at the way IT has pulled together to enable working from anywhere and moving resources to the cloud and enabling users to get their jobs done. It’s a testament to the resilience of a group of sanitation workers behind the scenes whose job it is to clean up after management and sales and do the jobs no one else wants to do.
The cynic in me is worried about what the future is going to hold now that we’ve managed to transform the way we work. I couldn’t quite put my finger on it until I was checking out this Reddit thread from last week. The top rant had an interesting perspective on the way that 2021 is going to go for workers and I couldn’t agree more. My dread has a name, and it’s Overwork.
Harder, Not Smarter
If anything, 2020 proved that we can do amazing things with the right motivation. The superhero mentality of IT paid off handsomely as we stood up remote access servers and found ways to get access to resources for people that couldn’t come into the office Continue reading
How Strong Encryption Can Protect Survivors of Domestic Violence

For many of us in quarantine, our only privacy often comes in the form of digital communications. While we’re cooped up in our homes with other people, the online world can be a place to blow off steam, find distractions, and even seek refuge. This is especially true for survivors of domestic violence, sexual violence, stalking, and trafficking, who have historically relied on encrypted communications to find support and an escape.
This year has been particularly hard for survivors. Factor in spiking COVID-19 cases, the long slog of sheltering in place, economic uncertainty, and, in some regions, colder weather and shorter days – plus December and January holidays, which traditionally see an uptick in domestic violence incidents – and you have a perfect storm. Access to private online communication isn’t just a way to find support and escape, but a means of survival.
With the risk of domestic violence higher now, it is even more essential that we protect survivors’ privacy and safety online. In a pandemic, survivors may only be able to rely on digital communications for help, to limit in-person interactions.
This is why we worked with the National Network to End Domestic Violence to put together a Continue reading
John Capobianco | Automating the Canadian Parliament Network
John Capobianco, Senior IT Planner and Integrator at House of Commons, joins co-hosts Derick and Brandon to dive into his journey to network automation for the Canadian Parliament. If you're curious about network automation or have already begun to implement, this is the episode for you!
Heavy Networking 555: Top Network Design Trends Of 2020
Today's episode is the last Heavy Networking of 2020. In the spirit of an end-of-year reflection, we're going to talk about network design trends from this year, some of which were driven, or at least accelerated, by the pandemic hellscape that was 2020. Our guest is Zig Zsiga, a network designer, architect, CCDE, and instructor.Heavy Networking 555: Top Network Design Trends Of 2020
Today's episode is the last Heavy Networking of 2020. In the spirit of an end-of-year reflection, we're going to talk about network design trends from this year, some of which were driven, or at least accelerated, by the pandemic hellscape that was 2020. Our guest is Zig Zsiga, a network designer, architect, CCDE, and instructor.
The post Heavy Networking 555: Top Network Design Trends Of 2020 appeared first on Packet Pushers.
Computing Euclidean distance on 144 dimensions
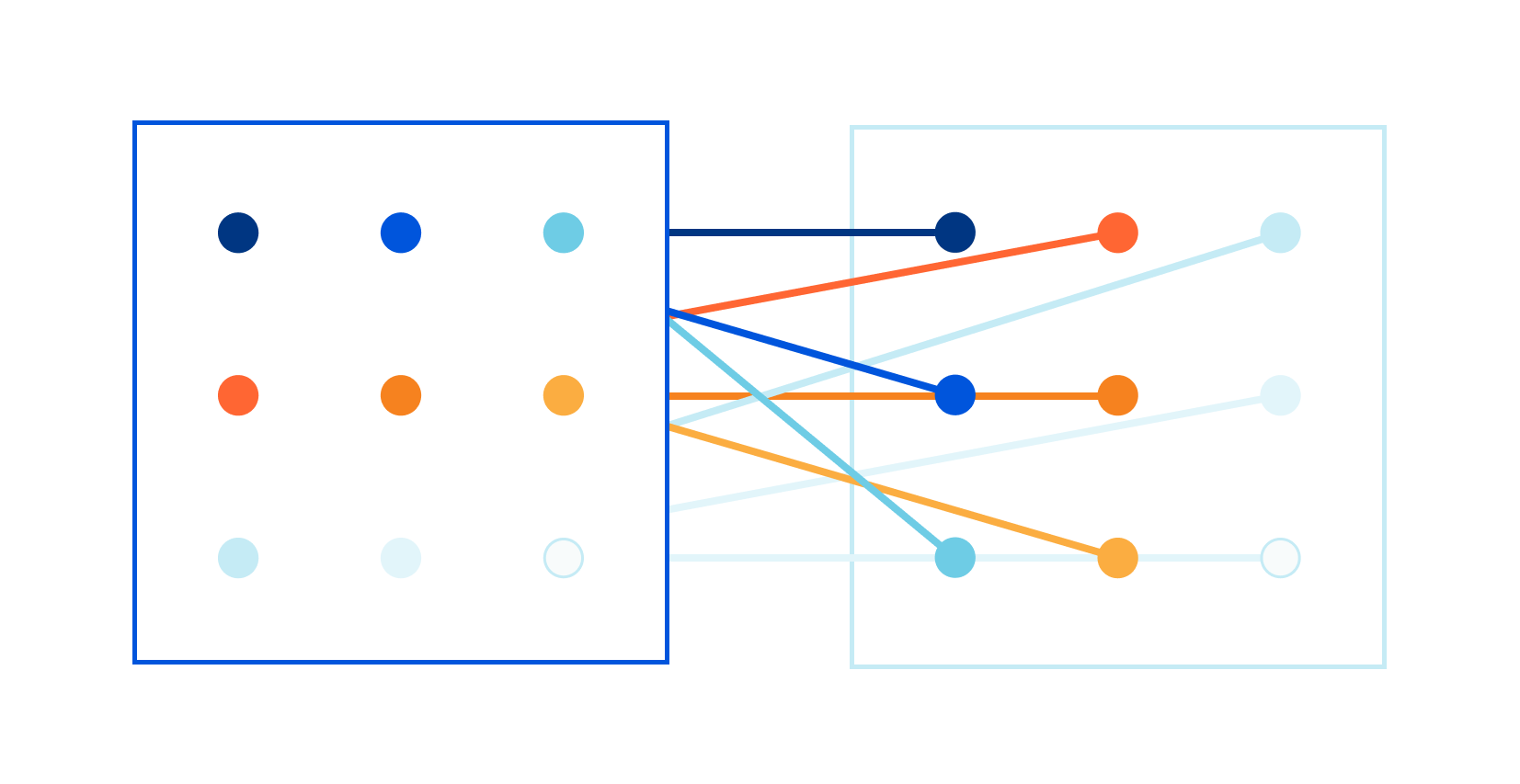
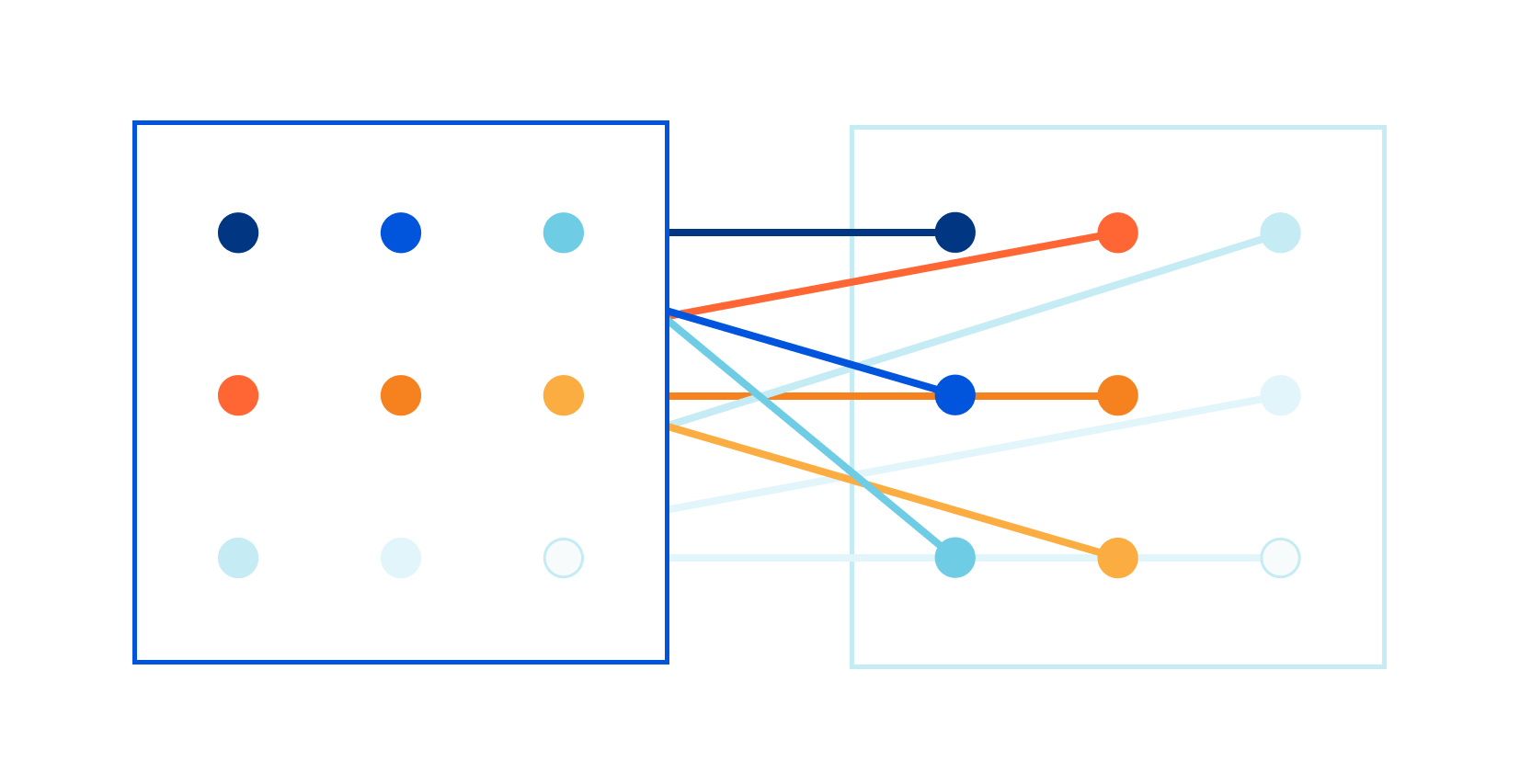
Late last year I read a blog post about our CSAM image scanning tool. I remember thinking: this is so cool! Image processing is always hard, and deploying a real image identification system at Cloudflare is no small achievement!
Some time later, I was chatting with Kornel: "We have all the pieces in the image processing pipeline, but we are struggling with the performance of one component." Scaling to Cloudflare needs ain't easy!
The problem was in the speed of the matching algorithm itself. Let me elaborate. As John explained in his blog post, the image matching algorithm creates a fuzzy hash from a processed image. The hash is exactly 144 bytes long. For example, it might look like this:
00e308346a494a188e1043333147267a 653a16b94c33417c12b433095c318012
5612442030d14a4ce82c623f4e224733 1dd84436734e4a5d6e25332e507a8218
6e3b89174e30372d
The hash is designed to be used in a fuzzy matching algorithm that can find "nearby", related images. The specific algorithm is well defined, but making it fast is left to the programmer — and at Cloudflare we need the matching to be done super fast. We want to match thousands of hashes per second, of images passing through our network, against a database of millions of known images. To make this work, Continue reading
Streaming Telemetry with Avi Freedman on Software Gone Wild
Remember my rant how “fail fast, fail often sounds great in a VC pitch deck, and sucks when you have to deal with its results”? Streaming telemetry is no exception to this rule, and Avi Freedman (CEO of Kentik) has been on the receiving end of this gizmo long enough to have to deal with several generations of experiments… and formed a few strong opinions.
Unfortunately Avi is still a bit more diplomatic than Artur Bergman – another CEO I love for his blunt statements – but based on his NFD16 presentation I expected a lively debate, and I was definitely not disappointed.
Streaming Telemetry with Avi Freedman on Software Gone Wild
Remember my rant how “fail fast, fail often sounds great in a VC pitch deck, and sucks when you have to deal with its results”? Streaming telemetry is no exception to this rule, and Avi Freedman (CEO of Kentik) has been on the receiving end of this gizmo long enough to have to deal with several generations of experiments… and formed a few strong opinions.
Unfortunately Avi is still a bit more diplomatic than Artur Bergman – another CEO I love for his blunt statements – but based on his NFD16 presentation I expected a lively debate, and I was definitely not disappointed.
A quirk in the SUNBURST DGA algorithm
On Wednesday, December 16, the RedDrip Team from QiAnXin Technology released their discoveries (tweet, github) regarding the random subdomains associated with the SUNBURST malware which was present in the SolarWinds Orion compromise. In studying queries performed by the malware, Cloudflare has uncovered additional details about how the Domain Generation Algorithm (DGA) encodes data and exfiltrates the compromised hostname to the command and control servers.
Background
The RedDrip team discovered that the DNS queries are created by combining the previously reverse-engineered unique guid (based on hashing of hostname and MAC address) with a payload that is a custom base 32 encoding of the hostname. The article they published includes screenshots of decompiled or reimplemented C# functions that are included in the compromised DLL. This background primer summarizes their work so far (which is published in Chinese).
RedDrip discovered that the DGA subdomain portion of the query is split into three parts:
<encoded_guid> + <byte> + <encoded_hostname>
An example malicious domain is:
7cbtailjomqle1pjvr2d32i2voe60ce2.appsync-api.us-east-1.avsvmcloud.com
Where the domain is split into the three parts as
| Encoded guid Continue reading |
|---|
Enterprise File Workloads Shift to Cloud Data Management in 2021
Next year brings a new normal where cloud becomes core to enterprise IT strategies. As a result, multi-cloud data management becomes more important.Upcoming Webinar: How Routers Really Work
Just a gentle reminder that on Monday (just a few days from now) I’m teaching a three hour webinar over at Safari Books on How Routers Really Work. From the course description—
This training will peer into the internal components of a router, starting with an explanation of how a router switches packets. This walk through of a switching path, in turn, will be used as a foundation for explaining the components of a router, including the various tables used to build forwarding tables and the software components used to build these tables.
TTL255 finalist of Cisco 2020 IT Blog Awards
I'm excited to announce that TTL255.com is one of the finalists in the Most Educational category of the 2020 IT Blog Awards, hosted by Cisco.
Over the years I learned great deal from blogs and videos created by community members. At one point I realized that I also might have something to offer and started this blog to give back to community hoping to teach and inspire others.
Creating valuable technical content takes a lot of work and time commitment. After years of posting here I appreciate even more all content makers out there that often don't ask for anything in return.
This year I decided to submit TTL255.com to 2020 IT Blog Awards hoping to reach more people and see where that takes me.
If you find my content valuable and worth your time, please consider voting for TTL255.com by following the below link:
https://www.ciscofeedback.vovici.com/se/705E3ECD2A8D7180

You can find me in the Most Educational category:
While you there have a look at other amazing blog posts. Some of them might inspire you, some will teach you something new. All come from members of community that put themselves out there to share their knowledge with Continue reading
2020 IT Blog Awards finalist!

I have the honor of having my blog selected as a finalist in the Most Educational category of the 2020 IT Blog Awards, hosted by Cisco. It is an honor and a great joy for me to be selected, for the third consecutive year, alongside other high-level bloggers who all have very deep technical knowledge! I hope you enjoy my articles as much as I enjoy writing and sharing them. I know I could write more, but I try to put quality ahead of quantity. Please click here to vote…
The post 2020 IT Blog Awards finalist! appeared first on AboutNetworks.net.
International Community Joins Indian Policy and Cybersecurity Experts in Warning about the Dangers of Traceability

A growing group of international and local cybersecurity and policy experts are weighing in on proposed changes to Indian regulations that could jeopardize the safety of billions worldwide. By seeking to restrict WhatsApp and other popular messaging apps’ use of end-to-end encryption, the proposed policies pose a major threat to cybersecurity in India.
In Traceability and Cybersecurity, over 50 cybersecurity experts in Europe, North and Latin America, Africa, and the Asia-Pacific region agreed that amendments to the Information Technology (Intermediaries Guidelines) Rules under the Indian Information Technology Act proposed by the Indian Ministry of Electronics and Information Technology (MeiTY) will create many more problems than it seeks to solve.
Produced as a result of a global technical experts meeting series organized by the Internet Society in partnership with Medianama, the report notes that MeiTY’s proposal ignores sound advice: requiring intermediaries such as WhatsApp to enable the traceability of the content and data they handle is a major threat not only to the safety of users, but to India’s national security.
The report stresses that traceability would mean enabling third-party access to private communications, a move that undermines the end-to-end encryption that users everywhere, including government entities, rely on to Continue reading
Introducing Cloudflare Pages: the best way to build JAMstack websites


Across multiple cultures around the world, this time of year is a time of celebration and sharing of gifts with the people we care the most about. In that spirit, we thought we'd take this time to give back to the developer community that has been so supportive of Cloudflare for the last 10 years.
Today, we’re excited to announce Cloudflare Pages: a fast, secure and free way to build and host your JAMstack sites.
Today, the path from an idea to a website is paved with good intentions
Websites are the way we express ourselves on the web. It doesn’t matter if you’re a hobbyist with a blog, or the largest of corporations with millions of customers — if you want to reach people outside the confines of 140 280 characters, the web is the place to be.
As a frontend developer, it’s your responsibility to bring this expression to life. And make no mistake — with so many frontend frameworks, tooling, and static site generators at your disposal — it’s a great time to be in your line of work.
That is, of course, right up until the point when you’re ready to show your work off Continue reading
Build Your Virtual Lab Faster with My Network Simulation Tools
I love my new Vagrant+Libvirt virtual lab environment – it creates virtual machines in parallel and builds labs much faster than my previous VirtualBox-based setup. Eight CPU cores and 32 GB of RAM in my Intel NUC don’t hurt either.
However, it’s still ridiculously boring to set up a new lab. Vagrantfiles describing the private networks I need for routing protocol focused network simulations are a mess to write, and it takes way too long to log into all the devices, configure common parameters, enable interfaces…