HS. Part 5. Automation at high-scale: Bringing network up (Docker SONIC-P4 and Linux bridges) based on the network graph.
Hello my friend,
Finally we approached the point where we start dealing with the network functions again, now at a high scale. After we have successfully generated the configuration files for our Microsoft Azure SONiC network functions, it is a time to boot them, span them and get the emulated data centre up and running.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Network automation training – now as a self-paced course as well
Following your asks we open a new format for the network automation training – self-paced format:
- It doesn’t matter what your timezone is.
- It doesn’t matter how much hours weekly do you have to study.
- It doesn’t matter how solid is your current background in automation, scripting and software development.
Because you decide on your own when, how often and how quickly you can learn.

At this training we teach you all the necessary concepts such as YANG data modelling, working with JSON/YAML/XML data formats, Linux administration basics, programming in Continue reading
Using Elastic Stack in Networking and Security
Andrea Dainese is continuing his journey through open-source NetDevOps land. This time he decided to focus on log management systems, chose Elastic Stack, and wrote an article describing what it is, why a networking engineer should look at it, and what’s the easiest way to start.
Building a Scalable Document Pre-Processing Pipeline
This article was originally posted on the Amazon Web Services Architecture blog.
In a recent customer engagement, Quantiphi, Inc., a member of the Amazon Web Services Partner Network, built a solution capable of pre-processing tens of millions of PDF documents before sending them for inference by a machine learning (ML) model. While the customer's use case--and hence the ML model--was very specific to their needs, the pipeline that does the pre-processing of documents is reusable for a wide array of document processing workloads. This post will walk you through the pre-processing pipeline architecture.
Daily Roundup: Cisco Debunks Security Myths
Cisco debunked security myths; Nvidia bought Cumulus; and T-Mobile claimed 5 standalone 5G firsts.
How Rakuten Mobile Corralled Vendors for Its Open RAN Vision
Complexities were abundant and corralling vendors for a virtualized, cloud-native, open radio...
UCMP: Augmenting L3 only designs
An aspiration of modern web scale networking is to leverage a pure L3 solution and integrate it with anycast addresses to allow for load balancing functionality. So why is this design aspirational? Well it requires discipline in the way that applications are architected— specifically around tenancy requirements and application redundancy. In this blog I’ll discuss a recent augmentation that was introduced into Cumulus Linux 4.1 that makes this style of design much more flexible in web scale networks.
Common challenges
Two common challenges when using anycast addressing in layer 3 only solutions are:
- Resilient hashing to support the change in ECMP paths
- Balancing traffic across unequal cost advertisements
Solutions
The first solution was implemented back in the early version of Cumulus Linux and is well documented. This solution is also known as “RASH” as the colloquial term.
The second solution addresses an interesting artifact of the way Layer 3 routes are advertised and learned, specifically with regards to next hop selection. Let us imagine the following simplified design:

The IP address of 192.168.1.101 is an anycast address that is being advertised by 3 different hosts in our environment. These three hosts are all serving the exact Continue reading
Nvidia Will Buy Cumulus Networks
Together with Mellanox, Nvidia says Cumulus’ open networking platform will help accelerate the...
T-Mobile Claims 5 Standalone 5G Firsts
Today’s 5G networks are effectively piggybacking on 4G LTE, but T-Mobile and others soon plan to...
Basic Linux Networking tips and tricks part-3: ss and netstat commands

Here is the third post of the series on basic network troubleshooting and tools under RHEL / CentOS. In this post, I will talk about the netstat and ss commands. Others posts of the series This post is part of a series about basic Linux Networking tips and tricks. The others posts of this series are: The ip and nmcli commands The mtr command The ss and netstat commands The curl command netstat The netstat command is a network utility used to display network connections, protocol or interfaces…
The post Basic Linux Networking tips and tricks part-3: ss and netstat commands appeared first on AboutNetworks.net.
Network Break 282: NVIDIA Completes Mellanox Acquisition; SpaceX Sets Date For Satellite Internet Beta Testing
The latest Network Break podcast examines NVIDIA's just-completed Mellanox acquisition, beta testing dates from SpaceX, the latest version of Cumulus Networks' NetQ management software, plus quarterly financial news for Juniper, Microsoft, and AmazonNetwork Break 282: NVIDIA Completes Mellanox Acquisition; SpaceX Sets Date For Satellite Internet Beta Testing
The latest Network Break podcast examines NVIDIA's just-completed Mellanox acquisition, beta testing dates from SpaceX, the latest version of Cumulus Networks' NetQ management software, plus quarterly financial news for Juniper, Microsoft, and Amazon
The post Network Break 282: NVIDIA Completes Mellanox Acquisition; SpaceX Sets Date For Satellite Internet Beta Testing appeared first on Packet Pushers.
State of the Internet – Job Snijders, IP Development Engineer @ NTT
In this episode Job Snijders shares some of his perspective on the current state of the Internet.
As you can expect when talking to Job, one of the topics is BGP Routing Security. We also touch on his work in IETF, OpenBSD, transit vs peering and IPv4 address exhaustion.
Listen below or subscribe in your favourite podcast player on the home screen!

A single dashboard for Cloudflare for Teams
Starting today, Cloudflare Access can now be used in the Cloudflare for Teams dashboard. You can manage security policies for your people and devices in the same place that you build zero-trust rules to protect your applications and resources. Everything is now in one place in a single dashboard.
We are excited to launch a new UI that can be used across the entire Teams platform, but we didn’t build this dashboard just for the sake of a new look-and-feel. While migrating the Access dashboard, we focused on solving one of the largest sources of user confusion in the product.
This post breaks down why the original UI caused some headaches, how we think about objects in Cloudflare for Teams, and how we set out to fix the way we display that to our users.
Cloudflare Access
Cloudflare Access is one-half of Cloudflare for Teams, a security platform that runs on Cloudflare’s network. Teams protects users, devices and data without compromising experience or performance. We built Cloudflare Access to solve our own headaches with private networks as we grew from a team concentrated in a single office to a globally distributed organization.
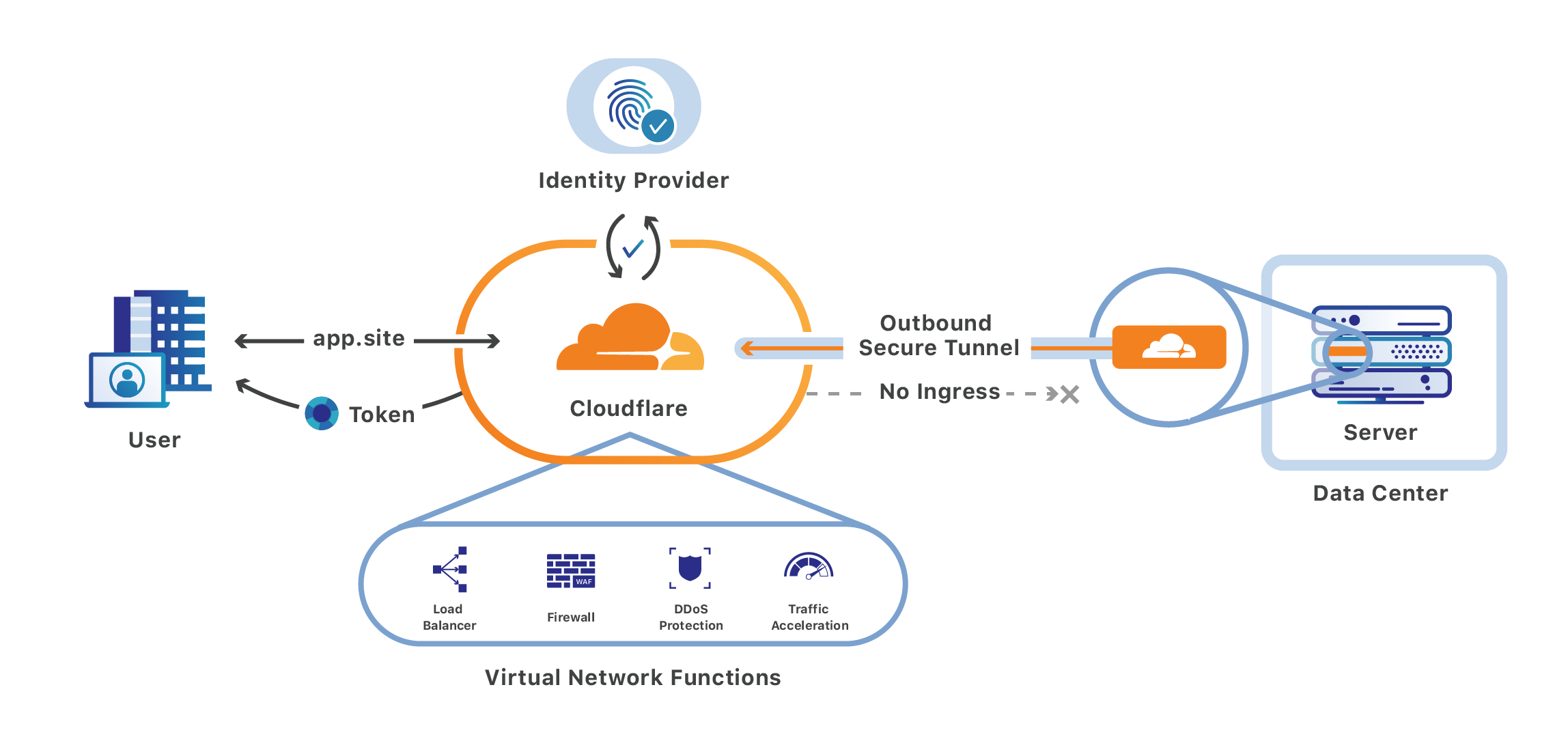
Cloudflare Access replaces corporate VPNs with Cloudflare’s Continue reading
Cisco Debunks Cybersecurity Myths
Cisco’s latest security report, based on a survey of almost 500 SMBs, aims to debunk myths about...
Key Factors in Attracting and Retaining Talent
Yesterday I posted a tweet on company culture that received a lot of positive feedback:
People thought this should be saved in a blog post, so this is it.
Company Culture
Do you want to attract and retain talent and high performers? Of course you do. Do you understand how to do that and are you willing to change your company culture?
Everything starts with culture. You may have heard the quote “Culture eats strategy for breakfast”, meaning that even the best stratety can’t compete with a company that has a great culture. Strategy without culture does not create success.
Gimmicks Are Not Culture
Most companies, such as the web scalers, often confuse gimmicks with culture. We have great company culture! We have ping pong tables, flipper games and even artists who play music for us! While these things can be entertaining, don’t mistake them for culture. Continue reading
The Week in Internet News: Classroom in a Car

Searching for a signal: CNN has a story about a teacher in rural Virginia who drives 20 minutes to find a good WiFi signal in order to work. The middle school history teacher is one of about 18 million U.S. residents who lack access to high-speed broadband, according to the Federal Communications Commission. The teacher “lives in a valley between two mountains, where the only available home internet option is a satellite connection. Her emails can take 30 seconds to load, only to quit mid-message. She can’t even open files on Google Drive, let alone upload lesson modules or get on a Zoom call with colleagues.”
Demanding access: Meanwhile, in Oakland, California, hundreds of teachers and students are calling for free access to the Internet, demanding that the school district and mayor “take all necessary measures” to ensure that students have access, KTVU reports. “There is no equity in education for our most vulnerable students if all Oakland families do not have access to the internet,” said Keith Brown, president of the Oakland Education Association, said.
Legislating access: In the U.S. Congress, Senate Democrats are introducing a bill that would create a new $4 billion fund for schools Continue reading
PATCHBOX Setup.exe Review
Over the past few months, while browsing social media, I came across an ad for the PATCHBOX Setup.exe and it …Explore: BGP in Data Center Fabrics
Got mentioned in this tweet a while ago:
Watching @ApstraInc youtube stream regarding BGP in the DC with @doyleassoc and @jtantsura.Maybe BGP is getting bigger and bigger traction from big enterprise data centers but I still see an IGP being used frequently. I am eager to have @ioshints opinion on that hot subject.
Maybe I’ve missed some breaking news, but assuming I haven’t my opinion on that subject hasn’t changed.
Time in Suzieq
Time, time, time, see what’s become of me, while I looked around for my possibilities - Simon & Garfunkel One of the powerful features of Suzieq is the ability to observe the state of the network at a time in the past, or to play back changes in state in...Headcount: Firings, Hirings, and Retirings — April 2020
AT&T selected Stankey as its new CEO; Google to slow hiring; Cisco vowed no job cuts; plus the...