Base Go packages
The Go standard library is generally great, but some parts have replacements that are just plain better and remove frustrations that you may have not even realised were frustrations. Here are my recommendations for every Go program.
I wouldn’t recommend that anyone use the standard library version of these for any purpose, since better alternatives exist.
This list may expand in the future.
gorilla/mux
The standard router is fine, but very low level. Here’s some of the features that makes it vital.
Filter on HTTP method
With the standard router you have to manually check that the method is
what you expect it to be, and if the same endpoint has both GET and
POST then you have to route that yourself. With gorilla/mux it’s as simple as:
r := mux.NewRouter()
get := r.Method("GET").Subrouter()
post := r.Method("POST").Subrouter()
get.HandleFunc("/", handleRoot)
get.HandleFunc("/items", handleListItems)
post.HandleFunc("/items", handleUploadItem)
You can also assert that headers are in place, for example to check
X-Requested-With because some API endpoints should not be allowed in
cross-domain XHR requests. Adding it to the router instead of manual
checks simplifies code and reduces risk of forgetting to add the
check.
Pattern URLs
With Continue reading
Amateur Radio and FT8
My interest in SDR got me into Amateur Radio. One reason was that so that I could transmit on non-ISM bands and with more power. Turns out the 2.3GHz band available to Amateur Radio operators is much quieter than the 2.4GHz band where WiFi, bluetooth, microwave ovens, drones, cordless phones and everything else lives. Shocker, I know.
Amateur radio doesn’t just have voice and morse code, there’s also digital modes.
A popular mode is FT8. It’s only used to exchange signal reports, so there’s no chatting. It’s in fact often practically unattended.
It’s a good way to check the quality of your radio setup, and the radio propagation properties that depend on how grumpy the ionosphere is at the moment.
If you transmit, even if you nobody replies, you’ll be able to see on PSKReporter who heard you, which is useful.
Because propagation should be pretty much symmetric, receiving a strong signal should mean that two-way communication is possible with the station. Though FT8 is a slow mode that will get through where others won’t, so a weak FT8 signal means that any voice communication is very unlikely to get through.
Unfortunately unlike WSPR the standard FT8 Continue reading
Yubikey for SSH on Windows
Short post this time.
If you on Linux set up your Yubikey in smartcard mode then you can use that Yubikey without any setup at all on Windows.
Just open
PuttyWincrypt, put
in the host to log in to, and under Connection > SSH > Auth set
Private key file for authentication to cert://*, then click
Open.
It’ll ask for the PIN, you’ll have to touch the Yubikey when it’s blinking, and you’re in.
Microsoft: ReFS is ridiculous
I’ve blogged before about how the new integrity-checking filesystem in Windows, ReFS, doesn’t actually have integrity checking turned on by default. It’s pretty silly that for a modern filesystem meant to compete with ZFS and BtrFS, to have the main 21st century feature turned off by default. But it’s not quite ridiculous. Not yet.
Now it turns out that scrubbing is only supported on Windows Server
- Microsoft honestly shipped an integrity-checking filesystem in Windows 10 with no way to repair or scrub it.
I used to say that Windows 10 is the best Windows ever, and that Microsoft kinda won my trust back. But what the hell?
I contacted Microsoft support over chat, who first suggested I do a system restore (sigh). But after I insisted that they please confirm that it’s supposed to work confirmed that no that only ships with Windows Server.
It’s not even clear from their pricing if I need the $882 Standard Edition or the $6,155 Datacenter Edition. Either one is way too much for such a standard feature.
What the hell, Microsoft? All I want is a checksumming file system. Either provide it, or don’t. Don’t give me a checksumming filesystem that can’t be Continue reading
Why bitcoin is terrible
For every day that passes I like bitcoin less. It’s bad for the world.
I have ranted about this many times, and it’s time I consolidate these rants into a blog post.
We’ll see with time if this rant ages poorly or not.
Section 1: Practicalities
What bitcoin is trying to achieve in payments
These would be good things:
- Anonymity
- Peer to peer and remote payments
What bitcoin is actually good for
Bitcoin today is pretty much only good for two things:
- Committing crimes
- Speculating on currency
If you’re not doing one of those, then don’t use Bitcoin.
If you are an online store then sure, accept Bitcoin. There’s moral problems with supporting Bitcoin (see rest of post), but as long as you immediately convert to fiat currency when you receive payment it’s fine for you. There are even companies out there that’ll guarantee an exchange rate so that you never have to get into the business of currency.
You may say that Bitcoin can be used to get money out of China, or into Brazil, or to enable shopping of “things that should not be called ‘drugs’ anyway”, but you have to admit that no matter what you think Continue reading
WPA2 and Infineon
The recent bug in WPA2 has a worst case outcome that is the same as using a wifi without a password: People can sniff, maybe inject… it’s not great but you connect to open wifi at Starbucks anyway, and you’re fine with that because you visit sites with HTTPS and SSH. Eventually your client will get a fix too, so the whole thing is pretty “meh”.
But there’s a reason I call it “WPA2 bug” and I call the recent issue with Infineon key generation “the Infineon disaster”. It’s much bigger. It seems like the whole of Estonia needs to re-issue ID cards, and several years worth of PC-, smartcard-, Yubikey, and other production have been generating bad keys. And these keys will stick around.
From now until forever when you generate, use, or accept RSA keys you have to check for these weak keys. I assume OpenSSH will if it hasn’t already.
But then what? It’s not like servers can just reject these keys, or it’ll lock people out. And it’s not clear that an adversary even has your public key for SSH. And you can’t crack the key if you don’t have the public half. Maybe a Continue reading
Internet in China
In this post I’ll describe some experiences I had with the Internet in China, and what it means for people making websites in the west in order to reach expats, visitors, and anyone else in China. So this should be useful information even if you don’t care about China as a market at all.
This blog post may be updated, as I have more thoughts on Internet in China.
My subjective experience is that “Internet in China” is an oxymoron. How exactly is there “Internet” without Google, Facebook, and Twitter? When attaching an Android phone to a WiFi in China it even says “Wi-Fi has no Internet access”.
OK, that’s not entirely serious. Especially since I’m obviously not aware of what the Chinese language Internet looks like, not speaking or reading Chinese. Baidu looks like it largely provides the services Google does (search, maps, …), but they’re pretty much not translated. The Baidu Map app seems fine, but is almost useless if you don’t speak Chinese. The one thing it’s good for is that unlike Google Maps (if you can even get to it. see below) it actually shows you a correct location within China.
But more importantly it’s not Continue reading
Is my TPM affected by the Infineon disaster?
I made a tool to check if your TPM chip is bad. Well, it extracts the SRK public key and you can then use marcan’s tool to easily check if the key is good or bad.
Example use:
$ g++ -o check-srk -std=gnu++11 check-srk.cc -ltspi -lssl -lcrypto 2>&1 && ./check-srk
Size: 2048
Outputting modulus…
8490234823904890234823904823904890238490238490238490238490[…]893428490823904231
$ wget https://gist.githubusercontent.com/marcan/fc87aa78085c2b6f979aefc73fdc381f/raw/526bc2f2249a2e3f5d4450c7c412e0dbf57b2288/roca_test.py
[…]
$ python roca_test.py 8490234823904890234823904823904890238490238490238490238490[…]893428490823904231
Vuln!
(use -s if you have an SRK PIN)
If the SRK is weak then not only are very likely anything else you generated in the TPM weak, but also anything generated outside the TPM and imported is crackable, since your blobs are encrypted using this crackable SRK key.
Yubikey for SSH after the Infineon disaster
Because of the Infineon Disaster of 2017 lots of TPM and Yubikey keys have to be regenerated.
I have previously blogged about how to create these keys inside the yubikey, so here’s just the short version of how to redo it by generating the key in software and importing it into the yubikey.
When it appears to stall, that’s when it’s waiting for a touch.
openssl genrsa -out key.pem 2048
openssl rsa -in key.pem -outform PEM -pubout -out public.pem
yubico-piv-tool -s 9a -a import-key --touch-policy=always -i key.pem
yubico-piv-tool -a verify-pin -a selfsign-certificate -s 9a -S '/CN=my SSH key/' -i public.pem -o cert.pem
yubico-piv-tool -a import-certificate -s 9a -i cert.pem
rm key.pem public.pem cert.pem
ssh-keygen -D /usr/lib/x86_64-linux-gnu/opensc-pkcs11.so -e
Delete all mentions of previous key. It’s good to have a disaster plan ahead of time if keys need to be replaced, but if you don’t have one:
- Inventory all bad keys. Make sure you have their fingerprints.
- Inventory all places this key could be installed.
- Generate new keys.
- Distribute new keys. (in this case, add to all relevant
~/.ssh/authorized_keys) - Remove all old keys.
- Grep for the keys found in Continue reading
Yubikey for SSH after the Infineon disaster
Because of the Infineon Disaster of 2017 lots of TPM and Yubikey keys have to be regenerated.
I have previously blogged about how to create these keys inside the yubikey, so here’s just the short version of how to redo it by generating the key in software and importing it into the yubikey.
When it appears to stall, that’s when it’s waiting for a touch.
openssl genrsa -out key.pem 2048
openssl rsa -in key.pem -outform PEM -pubout -out public.pem
yubico-piv-tool -s 9a -a import-key --touch-policy=always -i key.pem
yubico-piv-tool -a verify-pin -a selfsign-certificate -s 9a -S '/CN=my SSH key/' -i public.pem -o cert.pem
yubico-piv-tool -a import-certificate -s 9a -i cert.pem
rm key.pem public.pem cert.pem
ssh-keygen -D /usr/lib/x86_64-linux-gnu/opensc-pkcs11.so -e
Delete all mentions of previous key. It’s good to have a disaster plan ahead of time if keys need to be replaced, but if you don’t have one:
- Inventory all bad keys. Make sure you have their fingerprints.
- Inventory all places this key could be installed.
- Generate new keys.
- Distribute new keys. (in this case, add to all relevant
~/.ssh/authorized_keys) - Remove all old keys.
- Grep for the keys found in Continue reading
ReFS integrity is not on by default
I really don’t like the trend of filesystem authors to only care about filesystem integrity by default. How about having seat belt for your data integrity by default and let people turn it off if they want to compromise correctness for performance?
What I didn’t know is that ReFS integrity is not on by default. Only metadata integrity.
It’s also not visible or changeable in the UI (which is why I assumed they’d done the right thing), which is strange to me, this being Windows. No, you have to drop down into Microsoft’s crappy CLI.
How to check if it’s turned on.
Check files in one directory
PS E:\> Get-Item '*' | Get-FileIntegrity
FileName Enabled Enforced
-------- ------- --------
E:\SomeDirectory False True
E:\SomeOtherDirectory False True
E:\SomeFile.txt False True
[...]
Fuck you, Microsoft.
Check recursively
Of course Get-Item doesn’t do recursion. Why would it? That would
make sense.
PS E:\> Get-Children -Recurse 'E:\SomeDirectory' | Get-FileIntegrity
FileName Enabled Enforced
-------- ------- --------
E:\SomeDirectory\foo.txt False True
[...]
How to enable it
Both commands are needed. The first command sets the new default for the root directory, and the second adds checksums to all existing files and directories.
PS E:\> Continue readingMicrowave
Two interesting things I saw when listening to the output from my microwave:
- The frequency is not stable. I assume it’s not thermally controlled.
- Probably not a good idea to use WiFi channel 6, being 2.437GHz+-11MHz and all.
Near the microwave
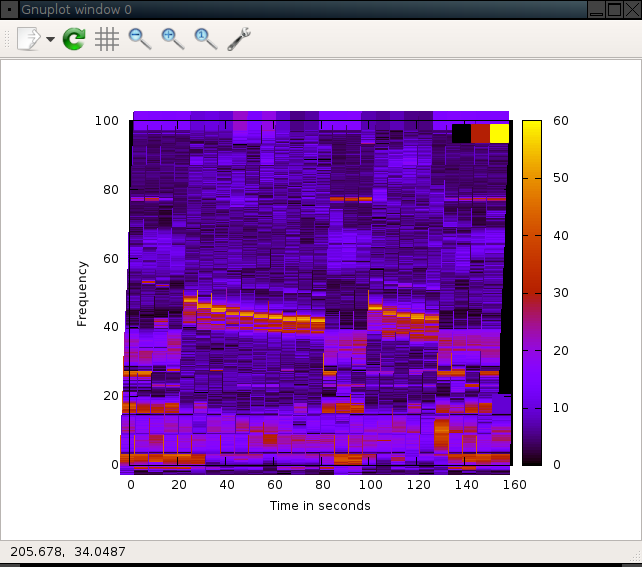
Some rooms away from the microwave
Separate measurement some rooms away.
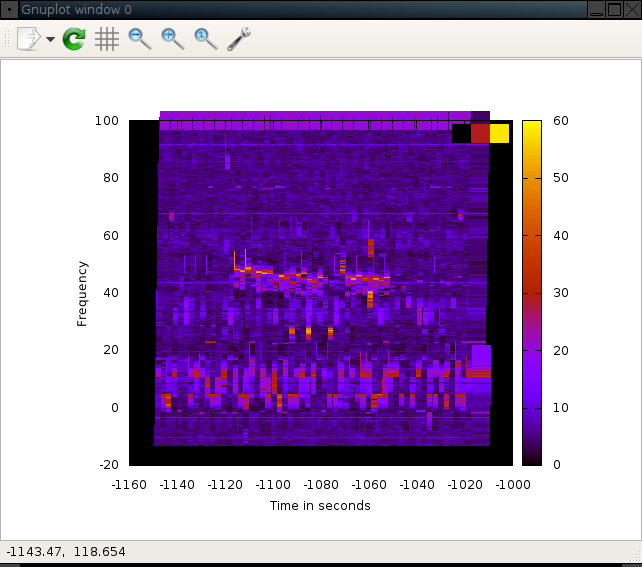
How to generate the graphs
# Edit usrp_spectrum_sense.py so that it prints time.time() instead of datetime.now()
./usrp_spectrum_sense.py --dwell-delay=0.1 -A RX2 -s 8000000 --real-time 2.4e9 2.5e9 > near-microwave.txt
# Edit near-microwave to remove the stupid verbose messages from the top.
cat > microwave.plot << EOF
set view map
set size ratio .9
set object 1 rect from graph 0, graph 0 to graph 1, graph 1 back
set object 1 rect fc rgb "black" fillstyle solid 1.0
set xlabel 'Time in seconds'
set ylabel 'Frequency'
set zlabel 'dB'
set terminal epslatex color
set output "near-microwave.eps"
splot 'near-microwave.txt' using ($1-1496693552.11):((($5/1000-2400000)/1000)):4 with points pointtype 5 pointsize 3 palette linewidth 30 title 'Signal'
EOF
gnuplot microwave.plot
convert near-microwave.{eps,png}
I can’t have GNUPlot output PNG directly because it hangs.
The magic value 1496693552.11 is the first timestamp in the file.
Decoding FSK
Something I’ve been playing with lately is software defined radio with GNURadio. I’m not good at it yet, but I’ve managed to decode the signals from a couple of things.
This is my step-by-step for how I decoded data from a boiler thermostat. I’m not saying it’s the best way, or even a good way. But it’s what got me there.
0. Find the frequency
Often this is written on the device itself. Other times it’s in the manual. If not, then more research is needed, such as by trying to find the manufacturer on fcc.gov or similar.
In this case it was easy. The manual said “868 MHz”, which is in the SRD860 band.
1. Capture some data
When I poked at the controls of the thermostat, saying “please make the room 25 degrees”, the thermostat must send this data to the boiler. I could hear the boiler start up and shut down, so there must be something sent between me pressing the buttons and I heard the results.
I started by centering around 868.5 Mhz with 1Msps. The minimum for the RTL-SDR is 900ksps, so even if you wanted to see less than 1MHz you need Continue reading
Killing idle TCP connections
Why
Let’s say you have some TCP connections to your local system that you
want to kill. You could kill the process that handles the connection,
but that may also kill other connections, so that’s not great. You
could also put in a firewall rule that will cause the connection to be
reset. But that won’t work on a connection that’s idle (also if one
side is initiator then using this method the other side would not tear
down its side of the connection). There’s
tcpkill, but it needs to
sniff the network to find the TCP sequence numbers, and again that
won’t work for an idle connection.
Ideally for these long-running connections TCP keepalive would be enabled. But sometimes it’s not. (e.g. it’s not on by default for gRPC TCP connections, and they certainly can be long-running and idle).
You could also do this by attaching a debugger and calling
shutdown(2) on the sockets, but having the daemon calling unexpected
syscalls thus getting into an unexpected state doesn’t really make for
a stable system. Also attaching a debugger hangs the daemon while
you’re attached to it.
This post documents how to do this on a Debian system.
Continue reading
Windows SSH client with TPM
I managed to get an SSH client working using an SSH pubkey protected by a TPM.
This is another post in my series in playing with TPM chips:
Optional: Take ownership of the TPM chip
This is not needed, since TPM operations only need well known SRK PIN, not owner PIN, to do useful stuff. I only document it here in case you want to do it. Microsoft recommends against it.
Set
OSManagedAuthLevelto 4HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\TPM\OSManagedAuthLevel2 -> 4Reboot.
Clear TPM
Run
tpm.mscand choose “Clear TPM”. The machine will reboot and ask you to press F12 or something for physical proof of presence to clear it.Set owner password from within
tpm.msc
Set up TPM for SSH
Create key
PIN must be at least 8 characters.C:\> tpmvscmgr.exe create /name “myhostnamehere VSC” /pin prompt /adminkey random /generate
Create CSR
Create a new text file
req.inf:[NewRequest] Subject = “CN=myhostnamehere” Keylength = 2048 Exportable = FALSE UserProtected = TRUE MachineKeySet = FALSE ProviderName = “Microsoft Base Smart Card Crypto Provider” ProviderType = 1 RequestType = PKCS10 KeyUsage = 0x80
C:\> certreq -new -f req.inf Continue reading
Windows SSH client with TPM
I managed to get an SSH client working using an SSH pubkey protected by a TPM.
Optional: Take ownership of the TPM chip
This is not needed, since TPM operations only need well known SRK PIN, not owner PIN, to do useful stuff. I only document it here in case you want to do it. Microsoft recommends against it.
-
Set
OSManagedAuthLevelto 4HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\TPM\OSManagedAuthLevel2 -> 4Reboot.
-
Clear TPM
Run
tpm.mscand choose “Clear TPM”. The machine will reboot and ask you to press F12 or something for physical proof of presence to clear it. -
Set owner password from within
tpm.msc
Set up TPM for SSH
-
Create key
tpmvscmgr.exe create /name "myhostnamehere VSC" /pin prompt /adminkey random /generatePIN must be at least 8 characters.
-
Create CSR
Create a new text file
req.inf:[NewRequest] Subject = "CN=myhostnamehere" Keylength = 2048 Exportable = FALSE UserProtected = TRUE MachineKeySet = FALSE ProviderName = "Microsoft Base Smart Card Crypto Provider" ProviderType = 1 RequestType = PKCS10 KeyUsage = 0x80certreq -new -f req.inf myhostname.csrIf you get any errors, just reboot and try again with the command that failed.
-
Get the CSR signed by any Continue reading
HSBC is not a real bank
From a customer’s perspective it’s hard to tell if HSBC UK is some sort of performance art as opposed to a real bank.
I will add more things to this blog post as they occur to me, since this is the first time I’m writing these down in one place some of the many many absurdities are bound to slip my mind.
How are they absurd? Let me count the ways.
You can only view about one month of transaction history in your account, and you see it in the logical reverse chronological order.
For anything older, you have to check your “statements”, which have overlapping data and are in chronological order. They have the data. They just refuse to show it to me in a useful form.
So if you want to inventory one month of expenses you now have to synchronize your recent transactions (reverse chronological) with one or two overlapping chronological ones. Oh, and multiply this by two to look at debit and credit card expenses.
If you thought the main banking website was bad (and it’s terrible. If you don’t think it’s absolutely awful then you’ve never seen e.g. SEB to compare), then you should Continue reading
HSBC is not a real bank
From a customer’s perspective it’s hard to tell if HSBC UK is some sort of performance art as opposed to a real bank.
I will add more things to this blog post as they occur to me, since this is the first time I’m writing these down in one place some of the many many absurdities are bound to slip my mind.
How are they absurd? Let me count the ways.
You can only view about one month of transaction history in your account, and you see it in the logical reverse chronological order.
For anything older, you have to check your “statements”, which have overlapping data and are in chronological order. They have the data. They just refuse to show it to me in a useful form.
So if you want to inventory one month of expenses you now have to synchronize your recent transactions (reverse chronological) with one or two overlapping chronological ones. Oh, and multiply this by two to look at debit and credit card expenses.
If you thought the main banking website was bad (and it’s terrible. If you don’t think it’s absolutely awful then you’ve never seen e.g. SEB to compare), then you should Continue reading
Ubiquity gear replacing BT HomeHub router
These are my notes from setting up Ubiquity wifi access point and router to replace the horrible BT HomeHub 5.
What’s wrong with BT HomeHub?
- It can’t hand out non-BT DNS servers
(and BT’s DNS servers MITM your queries and spoof NXDOMAIN
if the reply has rfc1918 addresses in them. This is known
and they “can’t” turn this off)
- This means that I had to turn off the DHCP server and run my own on a raspberry pi. So I’m actually replacing two devices. It was already not a all-in-one-box solution.
- The port forwarding database is not using unique key constraints, so you have to try and re-try adding port forwardings until you’re lucky and don’t hit a key collision.
- Only one wifi network. I want untrusted things (IoT) to be firewalled from the rest.
- I want to deny Internet access to some IoT things. I don’t need them to be able to connect anywhere. HomeHub doesn’t support that.
- Wifi range is not great. Not terrible, but bad enough that it doesn’t cover my home.
- I don’t know if it’s to blame, but I did not have a good experience trying to set up a second AP to automatically roam Continue reading
Ubiquity gear replacing BT HomeHub router
These are my notes from setting up Ubiquity wifi access point and router to replace the horrible BT HomeHub 5.
What’s wrong with BT HomeHub?
- It can’t hand out non-BT DNS servers
(and BT’s DNS servers MITM your queries and spoof NXDOMAIN
if the reply has rfc1918 addresses in them. This is known
and they “can’t” turn this off)
- This means that I had to turn off the DHCP server and run my own on a raspberry pi. So I’m actually replacing two devices. It was already not a all-in-one-box solution.
- The port forwarding database is not using unique key constraints, so you have to try and re-try adding port forwardings until you’re lucky and don’t hit a key collision.
- Only one wifi network. I want untrusted things (IoT) to be firewalled from the rest.
- I want to deny Internet access to some IoT things. I don’t need them to be able to connect anywhere. HomeHub doesn’t support that.
- Wifi range is not great. Not terrible, but bad enough that it doesn’t cover my home.
- I don’t know if it’s to blame, but I did not have a good experience trying to set up a second AP to automatically roam Continue reading