My First Web Page
<h2>My First Web Page</h2>
<p>My first paragraph.</p>
<p>Never call dudud document.write after the document has finished loading.
<div id="om-utia0gbpx93d4wvo9abp-holder"></div>.
It will overwrite the whole document.</p>
<script>
document.write(5 + 6);
</script>The post My First Web Page appeared first on Tigera.
Calico monthly roundup: October 2023
Welcome to the Calico monthly roundup: October edition! From open source news to live events, we have exciting updates to share—let’s get into it!
Join us at KubeCon + CloudNativeCon North America 2023
We’re gearing up for KubeCon + CloudNativeCon 2023 in Chicago. Join us at booth #G13 for exciting Kubernetes security updates and pick up some cool new Calico swag! |
Customer case study: eHealth
Calico provides visibility and zero-trust security controls for eHealth on Amazon EKS. Read our new case study to find out how. |
|
Learn why a traditional firewall architecture doesn’t work for modern cloud-native applications and results in a huge resource drain in a production environment. |

The State of Calico Open Source: Usage & Adoption Report 2023 Get insights into Calico’s adoption across container and Kubernetes environments, in terms of platforms, data planes, and policies. |
Open source news
- Read stories of Calico Open Source in action from our Calico Big Cats
- Share your Calico Open Source journey and win Continue reading
Calico monthly roundup: September 2023
Welcome to the Calico monthly roundup: September edition! From open source news to live events, we have exciting updates to share—let’s get into it!
|
Discover how you can automate security, ensure consistency, and tightly align security with development practices in a microservices environment. |

The State of Calico Open Source: Usage & Adoption Report 2023 Get insights into Calico’s adoption across container and Kubernetes environments, in terms of platforms, data planes, and policies. |
Open source news
- Share your Calico Open Source journey and win a $25.00 gift card – Your journey with Calico Open Source matters to us! Share your experience and insight on how you solve problems and build your network security using Calico. Book a meeting to tell us about your journey and where you seek information. As a thank you, we’ll send you a $25.00 gift card!
- Calico Live – Join the Calico community every Wednesday at 2:00 pm ET for a live discussion about learning how to leverage Calico and Kubernetes for networking and security. We will explore Kubernetes security and policy design, network flow logs and more. Join Continue reading
Transforming Container Network Security with Calico Container Firewall
In today’s cloud-driven landscape, containerized workloads are at the heart of modern applications, driving agility, scalability, and innovation. However, as these workloads become increasingly distributed across multi-cluster, multi-cloud, and hybrid environments, the challenge of securing them grows exponentially. Traditional network security measures designed for static network boundaries are ill-suited for the dynamic nature of containerized applications.
The Challenge: Protecting Cloud-Native Workloads
The rapid migration to the cloud has resulted in an explosion of cloud workloads, ranging from traditional applications with minimal cloud adaptation to cloud-native applications exploiting the cloud’s elasticity and scalability.
Cloud-native applications, in particular, rely on microservices architectures, ephemeral and highly elastic containers, and CI/CD automation through platforms like Kubernetes. These applications embrace the cloud’s dynamic nature but introduce unique security challenges. Unlike traditional workloads, cloud-native applications lack fixed network boundaries and are highly distributed across hybrid and multi-cloud environments. They demand a new approach to network security.
The Need for a Container Firewall in DevOps Flows:
The essence of DevOps is speed and automation. Containers and orchestration platforms like Kubernetes enable rapid software development and deployment. However, this agility brings heightened security concerns.
Traditional firewalls, rooted in perimeter defenses, struggle to secure dynamic containerized environments effectively.
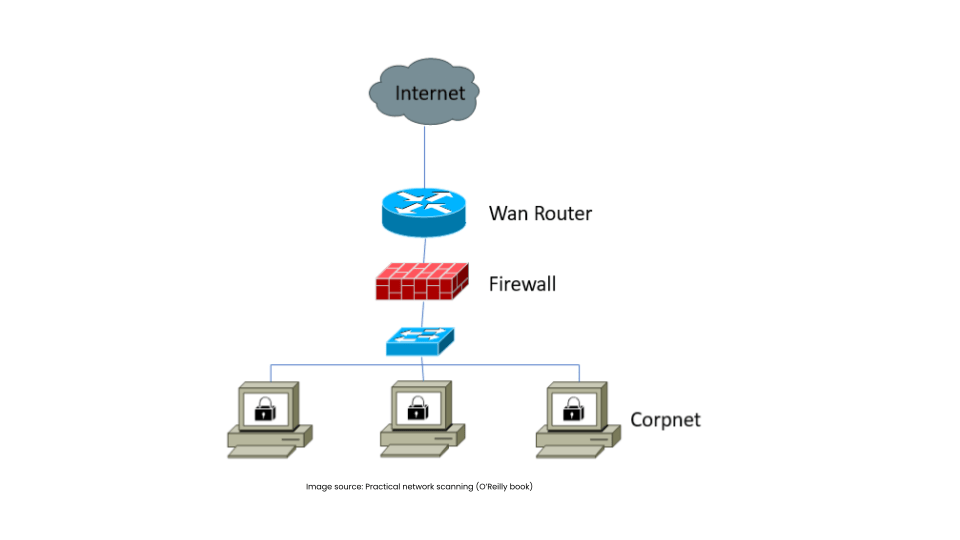
Fig Continue reading
What’s new in Calico Enterprise 3.18: Major workload-centric WAF updates and more
This release, we’re really excited about major improvements to Calico’s workload-centric WAF. We’ve made it much easier for users to configure and deploy the WAF in just a few clicks and we’ve also made it much easier to review and manage WAF alerts through our new Security Events feature.
Why do we need a new WAF for microservices?
Application security teams have deployed perimeter-based WAFs for decades to protect against common web attacks, with a focus on browser-based and client-side attacks. But with the rise of microservice architecture, there’s now a significant amount of HTTP traffic related to internal APIs. Moreover, with the growing use of open source and third-party software, all deployed within your Kubernetes cluster, you can no longer trust that the software running in your cluster is safe or secure. With this growing attack surface within your cloud environment, it’s critical to employ a workload-based WAF.
Calico’s workload-centric WAF
We know that security teams are struggling to keep up with the rapid pace of software development in their organizations, so we wanted to simplify the way that security teams secure application traffic. Further, we wanted to ensure that security teams can secure all workloads, not just their Continue reading
Calico monthly roundup: August 2023
Welcome to the Calico monthly roundup: August edition! From open source news to live events, we have exciting updates to share—let’s get into it!

*NEW* The State of Calico Open Source: Usage & Adoption Report 2023 Get insights into Calico’s adoption across container and Kubernetes environments, in terms of platforms, data planes, and policies. |

Customer case study: HanseMerkur Using Calico, HanseMerkur was able to reduce infrastructure overhead and achieve organizational compliance. Read our new case study to find out how. |
Open source news
- Calico Live – Join the Calico community every Wednesday at 2:00 pm ET for a live discussion about learning how to leverage Calico and Kubernetes for networking and security. We will explore Kubernetes security and policy design, network flow logs and more. Join us live on LinkedIn or YouTube.
- CNCF webinar – Watch the recording of our CNCF live webinar, where we talk about eBPF advantages and troubleshooting. Watch now.
- Calico for Microsoft Azure – Learn technical differences between different Azure networking options for Microsoft AKS environments and tradeoff analysis. Read blog post.
- Podcast – Listen to this joint podcast with Calico Big Cat, Parth Goswami, where they answer the Continue reading
New report: The state of Calico Open Source 2023
We are excited to announce the publication of our 2023 State of Calico Open Source, Usage & Adoption report! The report compiles survey results from more than 1,200 Calico Open Source users from around the world, who are actively using Calico in their container and Kubernetes environments. It sheds light on how they are using Calico across various environments, while also highlighting different aspects of Calico’s adoption in terms of platforms, data planes, and policies.
Report highlights
The report shows that Calico continues to be a pivotal part of the container and Kubernetes ecosystem, finding large-scale adoption across major Kubernetes platforms.
- Calico Open Source is mainly used for Kubernetes networking and security
- 63% are using Calico as a security policy engine on top of an existing CNI
- The top 3 Calico capabilities driving user adoption are its scalable networking, security policies and interoperability across different environments
- Calico users are using a combination of data planes including eBPF, standard Linux and Windows
- 16% of respondents use Calico’s newer eBPF data plane
- Calico policy creation and deployment is driven by the need for workload access control and secure egress access
- 85% of users need to achieve network segmentation and protect east-west traffic
Continue reading
Integrating Calico statistics with Prometheus
Metrics are important for a microservices application running on Kubernetes because they provide visibility into the health and performance of the application. This visibility can be used to troubleshoot problems, optimize the application, and ensure that it is meeting its SLAs.
Some of the challenges that metrics solve for microservices applications running on Kubernetes include:
- Visibility: Microservices applications are typically composed of many small, independent services. This can make it difficult to get a clear picture of the overall health and performance of the application. Metrics provide a way to aggregate data from all of the services, giving you a single view of the application.
- Troubleshooting: When something goes wrong with a microservices application, it can be difficult to identify the root cause of the problem. Metrics can help you to track down the problem by providing information about the state of the application at the time of the failure.
- Optimization: Metrics can be used to optimize the performance of a microservices application. By tracking metrics such as CPU usage, memory usage, and network traffic, you can identify areas where the application can be improved.
- SLAs: Many microservices applications have SLAs that they must meet. Metrics can be used to Continue reading
Calico monthly roundup: July 2023
Welcome to the Calico monthly roundup: July edition! From open source news to live events, we have exciting updates to share—let’s get into it!

Customer case study: Upwork Using Calico, Upwork was able to enforce zero-trust security for its newly migrated containerized applications on Amazon EKS. Read our new case study to find out how. |

Container security – Self-paced workshop This self-paced tutorial is designed to help you prevent, detect, and stop breaches in containers and Kubernetes. Learn how to secure all aspects of your containerized applications—all at your own pace! |
Open source news
- Calico Live – Join the Calico community every Wednesday at 2:00 pm ET for a live discussion about learning how to leverage Calico and Kubernetes for networking and security. We will explore Kubernetes security and policy design, network flow logs and more. Join us live on Linkedin or YouTube.
- CNCF webinar – Watch our CNCF on-demand webinar, Container and Kubernetes security policy design: 10 critical best practices, here.
- Calico eBPF and XDP – Learn how to implement eBPF security policies and XDP to achieve better performance in your Kubernetes cluster. Hands-on lab environment available here.
- Calico Wall of Continue reading
Automated namespace isolation with Calico
Calico has recently introduced a powerful new policy recommendation engine that enables DevOps, SREs, and Kubernetes operators to automatically generate Calico policies to implement namespace isolation and improve the security posture of their clusters.
This new recommendation engine is unique for three reasons:
- Calico’s policy recommendations work continuously in the background over a user-configurable time period. This ensures that less frequent traffic flows are also accounted for in recommended policies.
- Policy recommendations leverage Calico’s policy tiers. Tiers enforce an order of precedence on how Calico policies are evaluated and enforced. The recommended policies are placed in their own tier and Calico ensures each generated rule does not conflict with other policies you have implemented.
- Recommended policies are
StagedNetworkPolicies, allowing admins and operators to audit the behavior of these security policies before actively enforcing them.
In this blog, we’ll dive into each of these areas in more detail and provide an in-depth overview of how policy recommendations work and how it can improve the security posture of your cluster.
Before we get started, let’s quickly talk about namespace isolation and why it’s so important.
Why is namespace isolation important?
Namespaces are a foundational concept within Kubernetes. They help divide your Continue reading
Using Web Application Firewall at container-level for network-based threats
The microservices architecture provides developers and DevOps engineers significant agility that helps them move at the pace of the business. Breaking monolithic applications into smaller components accelerates development, streamlines scaling, and improves fault isolation. However, it also introduces certain security complexities since microservices frequently engage in inter-service communications, primarily through HTTP-based APIs, thus broadening the application’s attack surface. This scenario is similar to breaking a chunk of ice into smaller pieces, increasing its surface area. It is crucial that enterprises address these security challenges before benefiting from adopting a microservice architecture.
Challenges implementing defense-in-depth for containers with perimeter-based Web Application Firewall
Kubernetes is the de-facto standard for microservices orchestration. However, as organizations increasingly adopt Kubernetes, they run the risk of inadvertently introducing security gaps. This is often the result of attempts to integrate traditional security tooling into a cloud-native ecosystem that is highly dynamic, ephemeral, and non-deterministic. Instead of implementing security around the platform, DevOps, security, and platform teams must look at enforcing defenses through the platform.
Let’s look at an example of a web application firewall (WAF) which is typically deployed at the ingress of a network or application. As shown in the diagram below, HTTP traffic is Continue reading
Exploring AKS networking options
At Kubecon 2023 in Amsterdam, Azure made several exciting announcements and introduced a range of updates and new options to Azure-CNI (Azure Container Networking Interface). These changes will help Azure Kubernetes Services (AKS) users to solve some of the pain points that they used to face in previous iterations of Azure-CNI such as IP exhaustion and big cluster deployments with custom IP address management (IPAM). On top of that, with this announcement Microsoft officially added an additional dataplane to the Azure platform.
The big picture
Worker nodes in an AKS (Azure Kubernetes Service) cluster are Azure VMs pre-configured with a version of Kubernetes that has been tested and certified by Azure. These clusters communicate with other Azure resources and external sources (including the internet) via the Azure virtual network (VNet).
Now, let’s delve into the role of the dataplane within this context. The dataplane operations take place within each Kubernetes node. It is responsible for handling the communication between your workloads, and cluster resources. By default, an AKS cluster is configured to utilize the Azure dataplane, which Continue reading
Cybernews Expert Interview with Tigera President and CEO, Ratan Tipirneni
The challenges companies face regarding private and professional data protection are more important today than ever. In the modern enterprise, cloud computing and the use of cloud-native architectures enable unmatched performance, flexibility, velocity, and innovation. However, as digitalization pushes applications and services to the cloud, cyber criminals’ intrusion techniques have become increasingly sophisticated. To stay current with advancing technologies, doubling or tripling security measures is a must.
To understand the critical need for advanced cybersecurity measures, we turned to an expert in the industry, Ratan Tipirneni, President and CEO of Tigera – a company providing active, zero-trust-based security for cloud-native applications running on containers and Kubernetes.
Q: How did the idea of Tigera originate? What has your journey been like so far?
It was over six years ago that Tigera created Project Calico, an open-source container networking and security project.
As containers and Kubernetes adoption grew and organizations started using Kubernetes at scale, Tigera recognized the industry’s need for more advanced security and observability. Tigera has since grown from the Project Calico open-source project to a container security innovator that now supports many Fortune 100 companies across the globe.
Tigera’s continued success comes from listening to customers’ needs, understanding Continue reading
Preventing Vulnerable Container Deployments with Admission Control
In a previous blog post, Hands-on guide: How to scan and block container images to mitigate SBOM attacks, we looked at how Software Supply Chain threats can be identified and assessed. The severity of these vulnerabilities determine the posture or scan result for an image i.e. Pass, Warning or Fail. The next question is “What can we do with these results?”. To improve the security posture to reduce attacks on your workload we must ensure that workloads have the fewest possible vulnerabilities and layer on configuration security with KSPM, egress controls, and microsegmentation.
In this post we will cover how the scan results can be leveraged to add an additional layer of protection during Deploy Time in application deployment lifecycles.
It’s worth noting that Calico’s Image Scanner is an offline binary which can be run locally. This means the Image Scanner can be baked into any existing Continuous Integration/Continuous Delivery(CI/CD) pipeline. For example, after an image has been built the image can be scanned by the Image Scanner in an Execution Environment. Here checks can be configured to prevent the image from being pushed to a registry should vulnerabilities be detected. This is effectively how image scanning Continue reading
Optimizing Network Performance using Topology Aware Routing with Calico eBPF and Standard Linux dataplane
In this blog post, we will explore the concept of Kubernetes topology aware routing and how it can enhance network performance for workloads running in Amazon. We will delve into topology aware routing and discuss its benefits in terms of reducing latency and optimizing network traffic flow. In addition, we’ll show you how to minimize the performance impact of overlay networking, using encapsulation only when necessary for communication across availability zones. By doing so, we can enhance network performance by optimizing the utilization of resources based on network topology.
Understanding Topology Aware Routing
Kubernetes clusters are being deployed more often in multi-zone environments. The nodes that make up the cluster are spread across availability zones. If one availability zone is having problems, the nodes in the other availability zones will keep working, and your cluster will continue to provide service for your customers. While this helps to ensure high availability, it also results in increased latency for inter-zone workload communication and can result in inter-zone data transfer costs.
Under normal circumstances, when traffic is directed to a Kubernetes Service, it evenly distributes requests among the pods that support it. Those pods can be spread across nodes in different zones. Topology Continue reading
Implementing workload-centric Web Application Firewall (WAF) using Calico
Microservices security is a growing concern for businesses in the face of increasing cyber threats. With application layer attacks being a leading cause of breaches, it’s more important than ever to safeguard the HTTP-based communication between microservices within a Kubernetes cluster. Traditional web application firewalls (WAFs) are not designed to address this specific challenge, but Calico WAF offers a unique solution.
What is a workload-centric WAF?
Calico WAF, a workload-centric web application firewall, brings a fresh, cloud-native approach to securing microservices communication. Unlike traditional WAFs deployed at the edge of a Kubernetes cluster, Calico WAF focuses on protecting the intra-cluster traffic and applies zero-trust rules specifically designed for microservices within your cluster.
This innovative solution defends against common HTTP-layer attacks, such as server-side request forgery (SSRF), improper HTTP header type, occurring within the cluster. It seamlessly integrates with Calico Cloud network policies, enabling the enforcement of security controls at the host level for selected pods.
Calico WAF ensures the secure communication between microservices within your Kubernetes cluster, reducing the risk of vulnerabilities and threats. By adopting Calico WAF, businesses can confidently fortify the HTTP-based communication channels within their microservices architecture. This comprehensive approach enhances the overall security posture of Continue reading
Build and secure multi-cluster CockroachDB using the Calico clustermesh: A step-by-step guide
This blog is written by Dhiraj Sehgal and Mike Bookham.
Dhiraj Sehgal is the Director of Technical Marketing at Tigera, where he helps customers learn more about Calico and provides best practices for securing cloud-native environments. He is passionate about everything cloud native, from Kubernetes to cloud security and observability.
Mike Bookham is a Channel Solutions Engineer at Cockroach Labs. As part of Mike’s role, he helps a range of different types of partner organizations get familiar with CockroachDB from a technical perspective. Mike has worked with cloud-native technologies for a number of years and specializes in Kubernetes and the surrounding ecosystem.
With the rapid adoption of Kubernetes in organizations and the push to standardize the orchestration of resources with this approach, databases are now also being deployed into Kubernetes. Historically, persistent workloads like databases were not recommended for their deployment into Kuberntes as it was complex to manage how data would be stored. This was a result of Kubertnes originally being designed for non persistent microservice architectures. However, in more recent times new database vendors are emerging with software built from the ground up to run in this environment.
Kubernetes mandates how the networking is deployed and configured in Continue reading
Audit and Compliance with Calico
In this blog post, I will be talking about audit and compliance and how to implement it with Calico. Most IT organizations are asked to meet some standard of compliance, whether internal or industry-specific. However organizations are not always provided with the guidance to implement it. Furthermore, when guidance has been provided, it is usually applicable to a more traditional and static environment and doesn’t address the dynamic nature of Kubernetes. Existing compliance tools that rely on periodic snapshots do not provide accurate assessments of Kubernetes workloads against your compliance standards.
Getting started with audit and compliance for Kubernetes clusters
A good starting point is understanding what type of compliance requirements needs to be enforced and confirming that the enforcement is successful. Following this is finding a way to easily report on the current state of your environment so you can proactively ensure you are complying with the standards defined. You should also be prepared to provide a report on-demand when an audit team is investigating.
This blog is not meant to be a how-to guide to meet HIPAA, PCI-DSS or SOC. However, it will provide you with the guidance regarding these regulations so you can apply it and understand Continue reading
Turbocharging host workloads with Calico eBPF and XDP
In Linux, network-based applications rely on the kernel’s networking stack to establish communication with other systems. While this process is generally efficient and has been optimized over the years, in some cases it can create unnecessary overhead that can impact the overall performance of the system for network-intensive workloads such as web servers and databases.
XDP (eXpress Data Path) is an eBPF-based high-performance datapath inside the Linux kernel that allows you to bypass the kernel’s networking stack and directly handle packets at the network driver level. XDP can achieve this by executing a custom program to handle packets as they are received by the kernel. This can greatly reduce overhead, improve overall system performance, and improve network-based applications by shortcutting the normal networking path of ordinary traffic. However, using raw XDP can be challenging due to its programming complexity and the high learning curve involved. Solutions like Calico Open Source offer an easier way to tame these technologies.
Calico Open Source is a networking and security solution that seamlessly integrates with Kubernetes and other cloud orchestration platforms. While infamous for its policy engine and security capabilities, there are many other features that can be used in an environment by installing Continue reading
Calico monthly roundup: June 2023
Welcome to the Calico monthly roundup: June edition! From open source news to live events, we have exciting updates to share—let’s get into it!

Customer case study: Box Using Calico, Box achieved zero-trust security and policy automation at scale in a multi-cluster environment. Read our new case study to find out how. |

Is your container environment compliant with NIST guidelines? This assessment helps you compare your current security posture against the NIST Cybersecurity Framework and assess your readiness to detect and protect against cyberattacks. |
Open source news
- Calico Live – Join the Calico community every Wednesday at 2:00 pm ET for a live discussion about learning how to leverage Calico and Kubernetes for networking and security. We will explore Kubernetes security and policy design, network flow logs and more. Join us live on Linkedin or YouTube.
- Calico Wall of Fame – As a valued member of our Calico users community, we would like to feature you on our NEW Project Calico Wall of Fame. To participate, fill out the form here.
Connect
- The next monthly Project Calico community meeting will happen on on July 9th at 9:00 am PT. Join the Zoom Continue reading
 Evaluating container firewalls for Kubernetes network security
Evaluating container firewalls for Kubernetes network security