Recapping the Incredible Presentations at future:net 2017
For those of you unable to attend future:net 2017 in Las Vegas, NV last month, fear not—what happens in Vegas doesn’t always stay in Vegas!
That’s right, thanks to the wonder that is YouTube, there are video recordings available of the amazing keynote speakers and presentations that took place at this year’s future:net conference, which brought together the technical and networking leaders shaping new network strategies, solutions and innovations for the future of digital transformation.
To cure you of any FOMO you may have, check out a recap of future:net presentations below, including links to their videos and a brief description of the speakers and topics discussed during each.

- Welcome Opening & CTO Perspective – Check out the presentation that kicked off future:net 2017! Pere Monclus, CTO of NSBU at VMware, offers his expert perspective and lays out his thoughts on the future of networking.
- Opening Keynote: Network Engineers Can Uncross Their Fingers by Emulating Hardware and Software Engineers – CEO & Co-Founder of Intentionet Ratul Mahajan argues that intent-based networking can be realized by borrowing and adapting approaches that have enabled hardware and software engineers to tame their own engineering complexity in his insightful opening keynote speech.
- What Is Continue reading
Demo: Multi-site Active-Active with NSX, F5 Networks GSLB, and Palo Alto Networks Security
I wrote this post prior on my personal blog at HumairAhmed.com. You can also see many of my prior blogs on multisite and Cross-vCenter NSX here on the VMware Network Virtualization blog site. This post expands on my prior post, Multi-site Active-Active Solutions with NSX-V and F5 BIG-IP DNS. Specifically, in this post, deploying applications in an Active-Active model across data centers is demonstrated where ingress/egress is always at the data center local to the client, or in other words localized ingress/egress. Continue reading
Micro-segmentation of the Epic Electronic Health Records System with VMware NSX
authors – Geoff Wilmington, Mike Lonze
Healthcare organizations are focusing more and more on securing patient data. With Healthcare breaches on the rise, penalties and fines for lost or stolen PHI and PII data is not only devastating to the patients, but to the Healthcare organization as well. The Ponemon Institute Annual Benchmark Study on Privacy & Security of Healthcare Data has shown that nearly 50 percent of Healthcare organizations, up 5 percent from a previous study, that criminal attacks are the leading cause of Healthcare breaches. [1] With breaches on the rise and Healthcare organizations feeling the pain, how can we help Healthcare start layering security approaches on their most critical business applications that contain this highly critical data?
The principle of least privilege is to provide only the necessary minimal privileges for a process, user, or program to perform a task. With NSX, we can provide a network least privilege for the applications that run on the vSphere hypervisor using a concept called Micro-segmentation. NSX places a stateful firewall at the virtual network card of every virtual machine allowing organizations to control very granularly how virtual machines communicate or don’t communicate with each Continue reading
5 Reasons Why Attending the Transform Security Track at vForum Online is a Must
If you’ve been working in IT for the past few years, you know how much the security landscape has changed recently. Application infrastructures — once hosted in on-premises data centers — now sit in highly dynamic public and private multicloud environments. With the rise of mobile devices, bring-your-own-device (BYOD) policies, and Internet of Things (IoT), end-user environments are no longer primarily about corporately managed desktops. And attackers are growing more sophisticated by the day.
In such an atmosphere, traditional network perimeter security ceases to provide adequate protection.
That’s where the VMware solutions come in. At the heart of the solutions is a ubiquitous software layer across application infrastructure and endpoints that’s independent of the underlying physical infrastructure or location. To really understand how it works, you need to experience it for yourself. And the Transform Security track at vForum Online Fall 2017 on October 18th is the perfect opportunity. As our largest virtual conference, vForum Online gives IT professionals like yourself the chance to take a deep dive into VMware products with breakout sessions, chats with experts, and hands-on labs — all from the comfort of your own desk.
With this free half-day event just weeks away, it’s time to Continue reading
Top 10 Networking and Security Sessions at VMworld Europe

At VMworld Europe 2016, we showed that network virtualization is mainstream and that NSX will illuminate the path to bring your data center into the future with robust security, speed, and agility.
One year later, NSX is out to show that it’s not just in the data center anymore… it’s everywhere. Beyond helping you master the data center, NSX is setting out to empower you to reign supreme over the cloud, remote and branch offices (ROBO), and even containers. To help you get there, VMworld Europe 2017 has 70+ networking and security sessions and 60+ NSX customers to share expertise and direct experience with NSX. And on top of all of that, VMware will be presenting an exciting new security product to help ensure your applications stay secure!
Check out the list of the top, not-to-be-missed networking and security sessions below. You should also explore the schedule builder on VMworld.com to reserve your spot in the top networking and security sessions as well as to discover the whole range of introductory and deep dive NSX sessions covering the entire use case spectrum.
See you in sunny Barcelona at VMworld Europe 2017!

| Date | Time | Session ID | Session Title |
| Tues Continue reading |
NSX-T: Routing where you need it (Part 1)
Network virtualization has come a long way. NSX has played a key role in redefining and modernizing networking in a Datacenter. Providing an optimal routing path for the traffic has been one of the topmost priorities of Network Architects. Thanks to NSX distributed routing, the routing between different subnets on a ESXi hypervisor can be done in kernel and traffic never has to leave the hypervisor. With NSX-T, we take a step further and extend this network functionality to a multi-hypervisor and multi-cloud environment. NSX-T is a platform that provides Network and Security virtualization for a plethora of compute nodes such as ESXi, KVM, Bare Metal, Public Clouds and Containers.
This blog series will introduce NSX-T Routing & focus primarily on Distributed Routing. I will explain Distributed Routing in detail with a packet walk between the VMs sitting in same/different hypervisors, connectivity to physical infrastructure and multi-tenant routing. Let’s start with a quick reference to NSX-T architecture.
NSX-T Architecture
NSX-T has a built-in separation for Management plane (NSX-T Manager), Control Plane (Controllers) and Data Plane (Hypervisors, Containers etc.). I highly recommend going through NSX-T Whitepaper for detailed information on architecture to understand the components and functionality of each of the planes.
Couple of interesting points that I want to highlight about the architecture:
- NSX-T Manager is decoupled from vCenter and is designed to run across all these heterogeneous platforms.
- NSX-T Controllers serve as central control point for all the logical switches within a network and maintains information about hosts, logical switches/routers.
- NSX-T Manager and NSX-T Controllers can be deployed in a VM form factor on either ESXi or KVM.
- In order to provide networking to different type of compute nodes, NSX-T relies on a virtual switch called “hostswitch”. The NSX management plane fully manages the lifecycle of this “hostswitch”. This hostswitch is a variant of the VMware virtual switch on ESXi-based endpoints and as Open Virtual Switch (OVS) on KVM-based endpoints.
- Data Plane stretches across a variety of compute nodes: ESXi, KVM, Containers, and NSX-T edge nodes (on/off ramp to physical infrastructure).
- Each of the compute nodes is a transport node & will be a TEP (Tunnel End Point) for the host. Depending upon the teaming policy, this host could have one or more TEPs.
- NSX-T uses GENEVE as underlying overlay protocol for these TEPs to carry Layer 2 information across Layer 3. GENEVE provides us the complete flexibility of inserting Metadata as TLV (Type, Length, Value) fields which could be used for new features. One of the examples of this Metadata is VNI (Virtual Network Identifier). We recommend a MTU of 1600 to account for encapsulation header. More details on GENEVE can be found on the following IETF Draft. https://datatracker.ietf.org/doc/draft-ietf-nvo3-geneve/
Before we dive deep into routing, let me define a few key terms.
Logical Switch is a broadcast domain which can span across multiple compute hypervisors. VMs in the same subnet would connect to the same logical switch.
Logical Router provides North-South, East-West routing between different subnets & has two components: Distributed component that runs as a kernel module in hypervisor and Centralized component to take care of centralized functions like NAT, DHCP, LB and provide connectivity to physical infrastructure.
Types of interfaces on a Logical Router
- Downlink- Interface connecting to a Logical switch.
- Uplink– Interface connecting to the physical infrastructure/physical router.
- RouterLink– Interface connecting two Logical routers.
Edge nodes are appliances with a pool of capacity to run the centralized services and would be an on/off ramp to the physical infrastructure. You can think of Edge node as an empty container which would host one or multiple Logical routers to provide centralized services and connectivity to physical routers. Edge node will be a transport node just like compute node and will also have a TEP IP to terminate overlay tunnels.
They are available in two form factor: Bare Metal or VM(leveraging Intel’s DPDK Technology).
Moving on, let’s also get familiarized with the topology that I will use throughout this blog series.

I have two hypervisors in above topology, ESXi and KVM. Both of these hypervisors have been prepared for NSX & have been assigned a TEP (Tunnel End Point) IP, ESXi Host: 192.168.140.151, KVM host: 192.168.150.152. These hosts have L3 connectivity between them via transport network. I have created 3 Logical switches via NSX Manager & have connected a VM to each one of the switches. I have also created a Logical Router named Tenant 1 Router, which is connected to all the logical switches and is acting as a Gateway for each subnet.
Before we look at the routing table, packet walk etc., let’s look at how configuration looks like in NSX Manager. Here is switching configuration, showing 3 Logical switches.

Following is the routing configuration showing the Tenant 1 Logical Router.

Once configured via NSX Manager, the logical switches and routers are pushed to both the hosts, ESXi and KVM. Let’s validate that on both hosts. Following is the output from ESXi showing the Logical switches and router.

Following is the output from KVM host showing the Logical switches and router.

NSX Controller MAC learning and advertisement
Before we look at the packet walk, it is important to understand how remote MAC addresses are learnt by the compute hosts. This is done via NSX Controllers. As soon as a VM comes up and connects to Logical switch, local TEP registers its MAC with the NSX Controller. Following output from NSX Controller shows that the MAC addresses of VMs on Web VM1, App VM1 and DB VM1 have been reported by their respective TEPs. NSX Controller publishes this MAC/TEP association to the compute hosts depending upon type of host.

Now, we will look at the communication between VMs on the same hypervisor.
Distributed Routing for VMs hosted on the same Hypervisor
We have WEB VM1 and App VM1 hosted on the same ESXi hypervisor. Since we are discussing the communication between VMs on same host, I am just showing the relevant topology below.

Following is how traffic would go from Web VM1 to App VM1.
- Web VM1 (172.16.10.11) sends traffic to the gateway 172.16.10.1, as the destination (172.16.20.11) is in different subnet. This traffic traverses Web-LS and goes to Downlink interface of Local distributed router running as a kernel module on ESXi Host.
- Routing lookup happens on the ESXi distributed router and 172.16.20.0 subnet is a Connected route. Packet gets routed and is put on the App-LS.
- Destination MAC lookup for MAC address of App VM1 is needed to forward the frame. In this case, App VM1 is also hosted on the same ESXi, we do a MAC address lookup and find a local MAC entry as highlighted in diagram above.
- L3 rewrite is done and packet is sent to App VM1.
Please note that the packet didn’t have to leave the hypervisor to get routed. This routing happened in kernel. Now that we understand the communication between two VMs (in different subnet) on same hypervisor, let’s take a look at the packet walk from Web VM1 (172.16.10.11) on ESXi to DB-VM1 (172.16.30.11) hosted on KVM.
Distributed Routing for VMs hosted on the different Hypervisors (ESXi & KVM)
- Web VM1 (172.16.10.11) sends traffic to the gateway 172.16.10.1, as the destination (172.16.30.11) is in different subnet. This traffic traverses Web-LS and goes to Downlink interface of Local distributed router on ESXi Host.
- Routing lookup happens on the ESXi distributed router. Packet gets routed and is put on the DB-LS. Following output show the distributed router on ESXi host and it’s routing table.

- Destination MAC lookup for MAC address of DB VM1 is needed to forward the frame. MAC lookup is done and MAC address of DB VM1 is learnt via remote TEP 192.168.150.152. Again, this MAC/TEP association table was published by NSX Controller to the hosts.

- ESXi TEP encapsulates the packet and sends it to the remote TEP with a Src IP=192.168.140.151, Dst IP=192.168.150.152.

- Packet is received at remote KVM TEP 192.168.150.152, where VNI (21386) is matched. MAC lookup is done and packet is delivered to DB VM1 after removing the encapsulation header.

A quick traceflow validates the above packet walk.

This concludes the routing components part of this blog. In the next blog of this series, I will discuss multi-tenant routing and connectivity to physical infrastructure.
Ensuring Good with VMware AppDefense
co-author Geoff Wilmington
Traditional data center endpoint security products focus on detecting and responding to known bad behavior. There are hundreds of millions of disparate malware attacks, with over a million getting added every day. In addition, there is the threat of zero-day attacks exploiting previously unknown vulnerabilities. It becomes a never-ending race to “chase bad” without ever staying ahead of the threat landscape. What if we took an opposite approach to security? What if, instead of “chasing bad” we started by “ensuring good”?
![]() VMware AppDefense is a new security product focused on helping customers build a compute least privilege security model for data center endpoints and provide automated threat detection, response, and remediation to security events. AppDefense is focused on “ensuring good” versus “chasing bad” on data center endpoints. When we focus our attention on what a workload is supposed to be doing, our lens for seeing malicious activity is much more focused and as a result, we narrow the exploitable attack surface of the workload down to what we know about.
VMware AppDefense is a new security product focused on helping customers build a compute least privilege security model for data center endpoints and provide automated threat detection, response, and remediation to security events. AppDefense is focused on “ensuring good” versus “chasing bad” on data center endpoints. When we focus our attention on what a workload is supposed to be doing, our lens for seeing malicious activity is much more focused and as a result, we narrow the exploitable attack surface of the workload down to what we know about.
Changing The Way We Secure Compute
AppDefense applies the concept of “ensuring good” by using three main techniques:
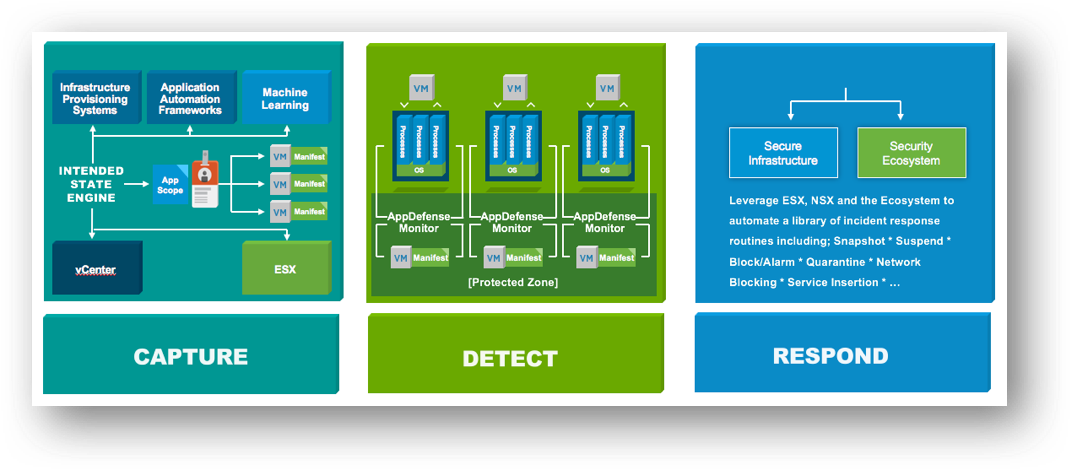
Capture
AppDefense starts by capturing Continue reading
Introducing VMware Skyline™
VMware Skyline™: an innovative support technology, developed entirely by VMware Engineering, that provides VMware technical support engineers with extreme visibility into your (customer’s) environment.
Customers with active support subscriptions install the VMware Skyline Collector, a standalone appliance that automatically and securely collects product usage data such as configuration, feature, and performance data.

It then listens for changes, events and patterns and analyzes the information using a robust rules and machine learning engine. The rules engine is where an ever-growing library of support intelligence, product knowledge, and logic is stored to analyze inbound streams of product information. Check out the video and the blog to learn more!
The post Introducing VMware Skyline™ appeared first on Network Virtualization.
Introducing VMware AppDefense – Expanding beyond micro-segmentation to threat detection and response
Hopefully, you have heard the news today! We couldn’t be more excited to announce the general availability of VMware AppDefense, our new security solution. AppDefense bolsters the micro-segmentations threat prevention capabilities delivered by NSX with data center endpoint threat detection and response. It’s no secret that organizations are spending more money than ever on security. It’s also no surprise that the only thing outpacing security spend are the losses due to security breaches. At VMware, we believe the struggle organizations face in gaining the upper-hand in this battle is due to a foundational architectural gap that creates misalignment between the infrastructure where security is applied and the applications that security is designed to protect.
NSX was the first step toward re-aligning network security policy with applications by leveraging the virtualization layer to enable micro-segmentation, as well as enhance the posture of other security solutions through integrations and features like service insertion and guest introspection. But applications are made up of both networks and data center endpoints like VMs. AppDefense is the other half of the puzzle. Whereas NSX prevents threats from moving freely throughout the network, AppDefense detects anything that does make it to an endpoint and can automatically Continue reading
NSX-T 2.0 is here !
VMware NSX is a network virtualization and security platform for the enterprise that is helping our customers make the transition to the digital era. As developers embrace new technologies like containers, and the percentage of workloads running in public clouds increases, network virtualization must expand to offer a full range of networking and security services, natively, in these environments.
Today, we are announcing the next version of NSX-T that can provide network virtualization for a multi-cloud and multi-hypervisor environment. The NSX technology that you are familiar with and use it for so many years is now be available for cloud and container environments. Circa VMworld 2016, we showed a prototype of NSX that can provide network virtualization and micro-segmentation for native AWS workloads. That journey is now complete and the initial availability of that service for some customers is already available for their AWS workloads.
NSX can now provide seamless network virtualization for workloads running on either VMs or Containers. VMs can be located either on-prem or on AWS. NSX will provide the entire feature set for either Vmware vSphere Hypervisors or KVM hypervisors. For native workloads on AWS, NSX will provide VMware NSX Secure Cloud to provide the Continue reading
NSX Going Wild at This Year’s VMworld
Get ready! NSX is hosting a major swag giveaway at VMworld as part of a celebration for everything our customers have accomplished in 2017! At various times throughout the conference, we’ll be on the prowl, looking for folks sporting NSX gear. If you’re spotted “in the wild” adorned with anything “NSX”, you could win some awesome swag and prizes.
Join the hunt: show off your NSX pride (and your photography skills), and post photos of anything #NSX with the hashtag #NSXintheWild. Winners will be chosen at random on the VMworld floor and online, so you never know when we might have you in our sights. But make no mistake – if you’re representing NSX in the wild, you’ll be a prime target for swag.

Pay it forward: If you happen to spot some cool NSX gear in the wild, snap a photo and tweet it out using the hashtag #NSXintheWild. We hope you’ll join the fun and show off your NSX treasure. Your odds of winning some prizes will be much higher at VMworld if you do, as opposed to hitting the slots!
The post NSX Going Wild at This Year’s VMworld appeared first on Network Virtualization.
VMware NSX Day 1 Guide Library
Our VMware NSX Guides are authored and technically reviewed by VMware subject-matter experts and cover networking and security essentials.
Below you will find a description of the current books in our library along with a downloadable PDF link.
If you are interested in purchasing a hardcopy, you can do so at our online store.
Check out our Four New Releases!
New Release: VMware NSX Automation Fundamentals Guide
 VMware NSX Automation Fundamentals delivers the roadmap to understanding networking and security automation challenges in today’s data centers. It explains the fundamental nature of VMware NSX Data Center architecture while detailing integrated solutions for both VMware and third party offerings (such as VMware vRealize Automation, OpenStack, Puppet, Chef, PowerNSX) that assist in creating networking and security components on-demand.
VMware NSX Automation Fundamentals delivers the roadmap to understanding networking and security automation challenges in today’s data centers. It explains the fundamental nature of VMware NSX Data Center architecture while detailing integrated solutions for both VMware and third party offerings (such as VMware vRealize Automation, OpenStack, Puppet, Chef, PowerNSX) that assist in creating networking and security components on-demand.
Follow Caio on Twitter! And follow Thiago on Twitter too!
New Release: VMware NSX Network Virtualization Fundamentals
 During their digital transformation process, many IT organizations still struggle with traditional networking methods and security approaches. By successfully addressing these challenges in thousands of real-world implementations, VMware NSX Data Center has established itself as the leading network virtualization platform, revolutionizing the way data center networks are designed and operated. In Continue reading
During their digital transformation process, many IT organizations still struggle with traditional networking methods and security approaches. By successfully addressing these challenges in thousands of real-world implementations, VMware NSX Data Center has established itself as the leading network virtualization platform, revolutionizing the way data center networks are designed and operated. In Continue reading
VMware NSX-V: Security for VxRAIL Hyper-Converged Solutions
Check-out the new white paper on leveraging NSX-V for security within the VxRAIL hyper-converged platform. The paper outlines how VxRAIL hyper-converged solutions leveraging NSX-V for security solves many of the security challenges with traditional silo-based architectures. A brief outline is provided below. Make sure to checkout the white paper for additional details. Continue reading
Disaster Recovery with VMware NSX-V and Zerto
Note, this is a reposting of the blog that I initially posted here on humairahmed.com. In a prior blog, VMware NSX and SRM: Disaster Recovery Overview and Demo, I described and demoed how VMware NSX and SRM with vSphere Replication combined provide for an enhanced disaster recovery (DR) solution. SRM also provides additional integration with NSX when Storage Policy Protection Groups (SPPGs) are used by providing the ability to automate network mappings. One of the great things about the NSX-V platform, is it can be used with any DR orchestration tool that supports the VMware vSphere ESXi hypervisor. Some of the tools customers are using with NSX include VMware SRM, Dell EMC RP4VM, Zerto, and Veeam. As SRM was discussed and demonstrated in a prior blog, Zerto and NSX together is explained in more detail below. Continue reading
NSX Sessions for the Geeks at VMworld 2017
This year at VMworld 2017 we have a great agenda full of highly technical sessions around NSX. Over the past few years NSX has expanded to meet a variety of use cases as our Content Catalog clearly shows. Based on the project your working on today, check out our recommendations for the best technical sessions for these specific NSX use cases:
- General overview sessions
- Security
- NSX & Cloud Native Apps
- Application Continuity
- Automation
- Design & Architecture
General NSX Sessions:
TS7003KU: Transforming Networking and Security for the Digital Era
Speakers: Milin Desai, Tom Corn and 3 customers
At a time when changes to technology are coming at us at a fast pace, how do customers meet and exceed business expectations? This session will focus on how customers are on their SDDC journey in context of network and security. Through the lens of the customer we will share what drives adoption, technology updates, team dynamics and becoming part of the overall business success.
NET3282BU: The NSX Practical Path
Speakers: Nikhil Kelshikar, Ron Fuller
We will share how customers have found value with NSX by getting started with one of the use cases around Security, Automation or App continuity. We will show Continue reading
Top 10 Networking and Security Sessions
At VMworld 2016, we showed network virtualization has gone mainstream and that NSX is the sure-fire way for you to bring your data center into the future with unparalleled security, speed, and agility.
A year on, NSX is taking its show on the road, and its destination is… everywhere. Not satisfied to help you master only the data center, NSX is setting out to help you conquer the cloud, remote and branch offices (ROBO), and even containers. To help you get there, VMworld 2017 has 70+ networking and security sessions and 60+ NSX customers to show you the way forward firsthand. And as an added bonus, VMware will be launching an exciting new security product, to help ensure your applications stay secure!
So take a look at the list of the top, can’t-miss networking and security sessions below. You should also check out the schedule builder on VMworld.com to reserve your spot in the top networking and security sessions as well as to discover the whole range of introductory and deep dive NSX sessions covering the entire use case spectrum.
See you at VMworld US 2017!
| Date | Time | Session ID | Session Title |
| Mon August 28 | 11:00 AM – Continue reading |
NSX-Powered Credit Union Shifts Focus to Speed and Innovation
Personal banking sure isn’t what it used to be. Thankfully.
When is the last time you went to a bank? My trips are so infrequent that I actually enjoy the experience as a change of pace. That’s because normally, I get to transfer money or deposit a check not only online, but from my phone. And things in the banking sector aren’t slowing down, they’re speeding up, as new digital upstarts create competition and a pressure to innovate and make customers’ lives easier.
Still, not too long ago, the banking industry was still feeling the shockwaves of the financial crisis. Investments across the industry were tight, meaning more had to be done with less – a story many of us who have had roles in IT can relate to. So when Amy Hysell took on the role of CIO at the Arizona Federal Credit Union (AZFCU), she decided to take a fresh approach. To compete in this fast-moving industry, she stepped back and took a look at on how to enable speed and innovation, while keeping security as the top priority, and also without sacrificing cost efficiency.
Fast forward to today, and a peek at some of AZFCU’s services quickly Continue reading
Calling all networking leaders – future:net 2017 is coming
“I thought future:net was the smartest of the networking conferences I’ve attended this year. The speakers were excellent — especially the customer and end-user stories, which provided valuable insight…it reminded me a lot of the first years of the Open Network Summit — the brain trust of the industry would attend, and that made it a must-attend show.
Craig Matsumoto, Managing Editor, SDX Central
“A note to say what a privilege it was to participate in the future:net event. Seriously, absolutely top notch event that was free of the embuggerances that make large conferences such hard work. Congratulations on pulling it together and we hope for another invitation when it comes around again.”
Greg Ferro and Ethan Banks, Co-founders of Packet Pushers
We live in a hyper connected world – everything of value, from the apps, to the cloud, to the devices, to the users, is all closely tethered to one another. The network has become the critical platform that connects everything reliably and securely. IT must also evolve to support this new ecosystem of engagement. Ultimately, a lot has to happen for the network to deliver what customers need: a seamless and secure experience.
That’s why we’re looking Continue reading
Transforming IT Security in Three Key Steps
Several years ago, the CEO of a Fortune 100 company remarked: “If you went to bed last night as an industrial company, you’re going to wake up this morning as a software and analytics company.”
Today, these words are more true than ever—but so is the reality that the digital transformation in business has also given rise to significant changes across the IT landscape and, in turn, significant new challenges for IT security.
As people, devices, and objects become more connected, protecting all these connections and environments has become a top priority for many IT organizations. At the same time, it’s also become one of their biggest challenges. Securing each and every interaction between users, applications, and data is no easy feat—especially when you consider that securing these interactions needs to be done across environments that are constantly changing and increasingly dynamic.
So how do you mitigate risk in a world where IT complexity and “anytime, anywhere” digital interactions are growing exponentially? For organizations that are embracing cloud and virtualized environments, three common-sense steps—enabled by a ubiquitous software layer across the application infrastructure and endpoints that exists independently of the underlying physical infrastructure—are proving to be key for providing Continue reading
Networking Challenges in OpenStack Clouds
Did you decided that is time to implement OpenStack to build your Cloud? Have you tested in the lab? Evaluated many distributions available and hired specialized OpenStack resources? However, when the environment goes into production, Neutron is not integrating with the physical network?

If the above story closely resembles what you have faced, this post will unconceal the many challenges of Networking with any OpenStack distribution and how VMware NSX is the missing piece for your Cloud.
Networking and Security Challenges with OpenStack
Since its creation, the biggest challenges of OpenStack Clouds implementations are automation, integration and orchestration of the required networking and security components at the physical infrastructure layer. The main difficulty is that these environments are extremely heterogeneous and most of the devices do not have an open and programmable interface for configuration and, thus, the initial way of running OpenStack was to pre-provisioning the network manually and only use basics functionalities when implementing security services.
With the rise of Network Virtualization solutions and evolution of Open vSwitch, some of these challenges were solved, making it possible to create an abstraction layer from the physical elements of infrastructure and automate the virtual network through the programmable interface Continue reading