New RFC 8360 – RPKI Validation Reconsidered – Offers Alternative Validation Procedures to Improve Routing Security
RFC 8360, Resource Public Key Infrastructure (RPKI) Validation Reconsidered, is now published in the RFC libraries.
What is RPKI?
Resource Public Key Infrastructure (RPKI) aims to improve the security of the Internet routing system, specifically the Border Gateway Protocol (BGP), by establishing a hierarchy of trust for BGP routes. Today, most organizations simply trust that routing updates they get are sent by authorized senders. This is how bad actors and misconfigurations can cause massive routing issues. With RPKI, the receiving organization can verify that the sending organization is authorized to send the routing update.
RPKI works by issuing X.509-based resource certificates to holders of IP addresses and AS numbers to prove assignment of these resources. These certificates are issued to Local Internet Registries (LIRs) by one of the five Regional Internet Registries (RIRs) who allocate and assign these resources in their service regions.
What Does This RFC Do?
In the IETF, participants have been discussing issues that may arise when resources move across registries. The problem happens when a subordinate certificate “over-claims” resources compared to its parent. According to the standard validation procedure specified in RFC 6487, the whole branch beneath would be invalidated. The closer to Continue reading
Infoblox Updates Cloud-Based DNS Security Offering To Block Malicious Sites
Infoblox updates its cloud-based DNS security service to run without agent software and improves its ability to filter unwanted and malicious sites.RSA Adds Security Orchestration, Automation to SIEM Platform
 RSA today rolled out an orchestration and automation tool for its SIEM product. It also reached a deal to acquire Fortscale, a behavioral analytics startup.
RSA today rolled out an orchestration and automation tool for its SIEM product. It also reached a deal to acquire Fortscale, a behavioral analytics startup.
Argo Tunnel: A Private Link to the Public Internet


Photo from Wikimedia Commons
Today we’re introducing Argo Tunnel, a private connection between your web server and Cloudflare. Tunnel makes it so that only traffic that routes through Cloudflare can reach your server.
You can think of Argo Tunnel as a virtual P.O. box. It lets someone send you packets without knowing your real address. In other words, it’s a private link. Only Cloudflare can see the server and communicate with it, and for the rest of the internet, it’s unroutable, as if the server is not even there.
How this used to be done
This type of private deployment used to be accomplished with GRE tunnels. But GRE tunnels are expensive and slow, they don’t really make sense in a 2018 internet.
GRE is a tunneling protocol for sending data between two servers by simulating a physical link. Configuring a GRE tunnel requires coordination between network administrators from both sides of the connection. It is an expensive service that is usually only available for large corporations with dedicated budgets. The GRE protocol encapsulates packets inside other packets, which means that you will have to either lower the MTU of your origin servers, or have your router do Continue reading
Combating Ransomware in Multi-Cloud Environments
 The rapidly evolving threat environment, coupled with a more vulnerable enterprise network signals a paradigm shift in how organizations will protect data residing on multi-cloud systems.
The rapidly evolving threat environment, coupled with a more vulnerable enterprise network signals a paradigm shift in how organizations will protect data residing on multi-cloud systems.
Juniper Networks’ Security Strategy: Unify Everything, Keep it Open
 Juniper Networks security team wants to unify threat detection, automated enforcement, and mitigation in a unified platform and integrate with other technology vendors to support non-Juniper gear.
Juniper Networks security team wants to unify threat detection, automated enforcement, and mitigation in a unified platform and integrate with other technology vendors to support non-Juniper gear.
Extend your security view from the data center to the edge
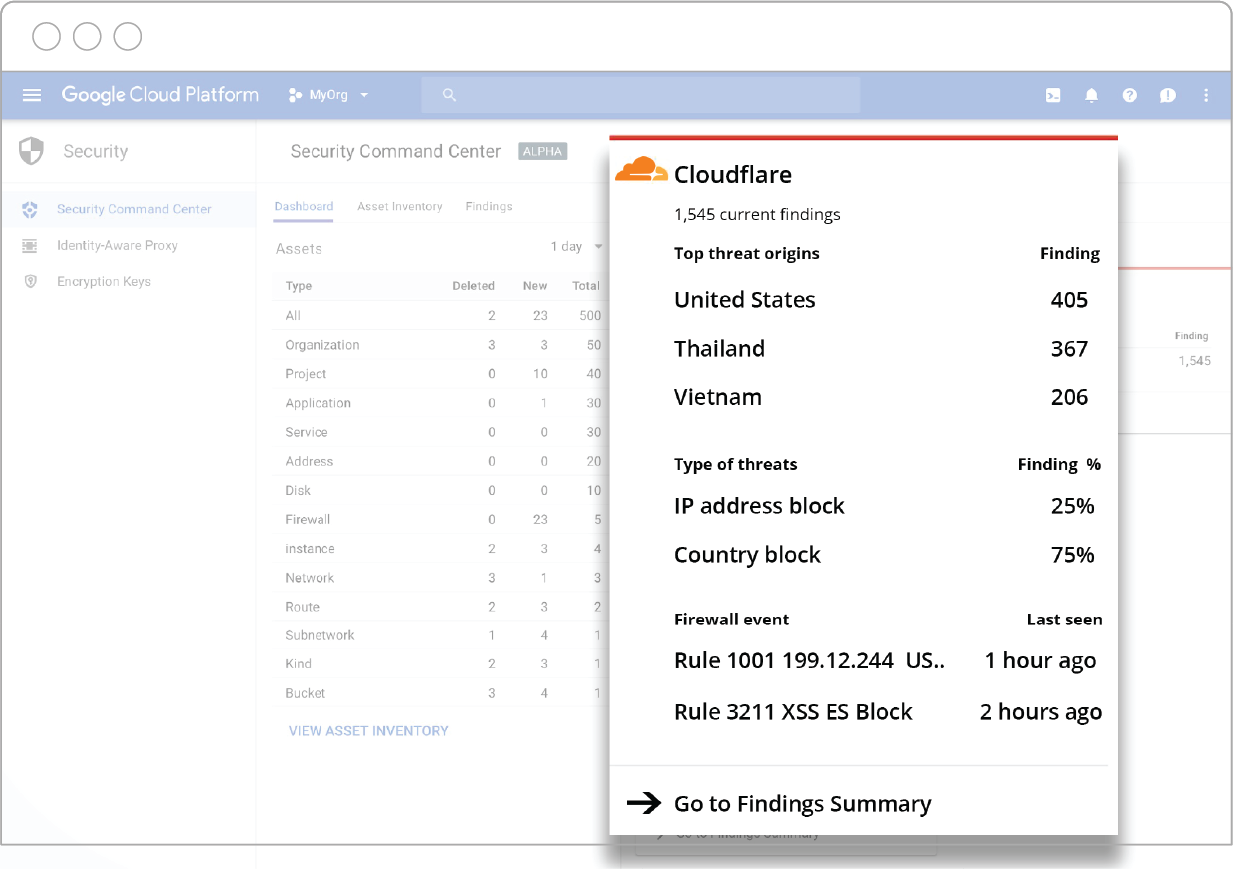
How great would it be to have a dashboard with a holistic view of threats, malicious server activity, vulnerabilities, sensitive data access levels and a daily scan of resources across all of your applications and services? Now you can.
Cloudflare is thrilled to announce its integration with Cloud Security Command Center (Cloud SCC) for Google Cloud Platform: A security and data risk platform helping enterprises gather data, identify threats, and act on them before they result in business damage or loss.
The advantage of the Cloud SCC solution is that it surfaces insights from both the Google Cloud Platform, as well as Cloudflare’s edge, in a unified dashboard.
What Cloudflare data is visible within the Cloud SCC dashboard?
Through Cloudflare’s API endpoints, data is pushed to Google’s Cloud SCC dashboard and domain name information mapped to the appropriate Google Cloud asset. Cloudflare’s branded card in the Cloud SCC dashboard is automatically populated with a summary of top theat origins, top types of threats, and latest Web Application Firewall (WAF) events.
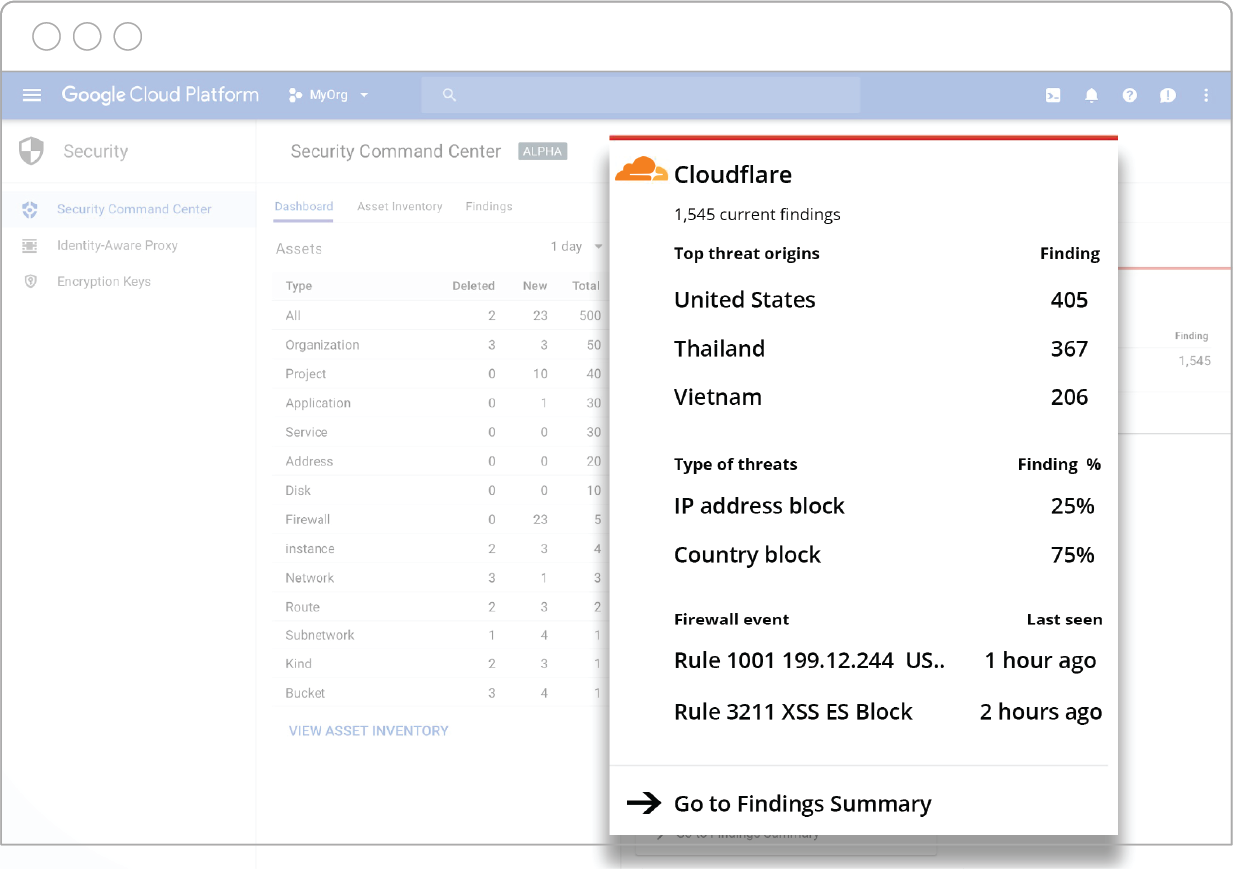
To view a full list of Cloudflare events, click on the Cloudflare card in Cloud SCC and it will take you to a “Cloudflare Findings” page. From there, you can Continue reading
Why the crypto-backdoor side is morally corrupt
Crypto-backdoors for law enforcement is a reasonable position, but the side that argues for it adds things that are either outright lies or morally corrupt. Every year, the amount of digital evidence law enforcement has to solve crimes increases, yet they outrageously lie, claiming they are "going dark", losing access to evidence. A weirder claim is that those who oppose crypto-backdoors are nonetheless ethically required to make them work. This is morally corrupt.What I am saying is that those arguing that we should reject third-party access out of hand haven’t carried their research burden. ... There are two reasons why I think there hasn’t been enough research to establish the no-third-party access position. First, research in this area is “taboo” among security researchers. ... the second reason why I believe more research needs to be done: the fact that prominent non-government experts are publicly willing to try to build secure third-party-access solutions should make the information-security community question the consensus view.
EnSilo Malware Protection Gives Red Bull Security Team Wings
 The endpoint security platform protected Red Bull from the WannaCry ransomware attack and helps the energy drink maker’s head of digital security sleep at night.
The endpoint security platform protected Red Bull from the WannaCry ransomware attack and helps the energy drink maker’s head of digital security sleep at night.
WannaCry after one year
In the news, Boeing (an aircraft maker) has been "targeted by a WannaCry virus attack". Phrased this way, it's implausible. There are no new attacks targeting people with WannaCry. There is either no WannaCry, or it's simply a continuation of the attack from a year ago.It's possible what happened is that an anti-virus product called a new virus "WannaCry". Virus families are often related, and sometimes a distant relative gets called the same thing. I know this watching the way various anti-virus products label my own software, which isn't a virus, but which virus writers often include with their own stuff. The Lazarus group, which is believed to be responsible for WannaCry, have whole virus families like this. Thus, just because an AV product claims you are infected with WannaCry doesn't mean it's the same thing that everyone else is calling WannaCry.
Famously, WannaCry was the first virus/ransomware/worm that used the NSA ETERNALBLUE exploit. Other viruses have since added the exploit, and of course, hackers use it when attacking systems. It may be that a network intrusion detection system detected ETERNALBLUE, which people then assumed was due to WannaCry. It may actually have been an nPetya infection instead (nPetya Continue reading
SPIFFE, SPIRE Join Cloud Native Computing Foundation Sandbox
 The open source workload identity framework projects are modeled after similar systems at Google, Netflix, and Twitter.
The open source workload identity framework projects are modeled after similar systems at Google, Netflix, and Twitter.
Hybrid Cloud Security 101: What IT Leaders Need to Know
 Hybrid cloud environments present a revolutionary change in how organizations store and manage their data. But what happens if access to the cloud is compromised or interrupted?
Hybrid cloud environments present a revolutionary change in how organizations store and manage their data. But what happens if access to the cloud is compromised or interrupted?
Cloudflare is adding Drupal WAF Rule to Mitigate Critical Drupal Exploit
Drupal has recently announced an update to fix a critical remote code execution exploit (SA-CORE-2018-002/CVE-2018-7600). In response we have just pushed out a rule to block requests matching these exploit conditions for our Web Application Firewall (WAF). You can find this rule in the Cloudflare ruleset in your dashboard under the Drupal category with the rule ID of D0003.
Drupal Advisory: https://www.drupal.org/sa-core-2018-002
Cloudflare is adding Drupal WAF Rule to Mitigate Critical Drupal Exploit
Drupal has recently announced an update to fix a critical remote code execution exploit (SA-CORE-2018-002/CVE-2018-7600). This patch is to disallow forms and form fields from starting with the “#” character which results in remote code execution.
We have also in accordance, just pushed out a rule to block requests matching these exploit conditions for our Web Application Firewall (WAF). You can find this rule in the Cloudflare ruleset in your dashboard under the Drupal category with the rule ID of D0003.
Drupal Advisory: https://www.drupal.org/sa-core-2018-002
VMware Buys Second Security Startup, E8 Security
 The virtualization giant will add E8 Security’s user and entity behavior analytics technology to its digital workspace platform.
The virtualization giant will add E8 Security’s user and entity behavior analytics technology to its digital workspace platform.
McAfee Drops New SOCs, Netskope Takes CASB Beyond Cloud Apps
 McAfee opened new security operations centers in Plano, Texas, and Cork, Ireland. Also today Netskope expanded its cloud security platform to include web access.
McAfee opened new security operations centers in Plano, Texas, and Cork, Ireland. Also today Netskope expanded its cloud security platform to include web access.
Kubernetes 1.10 Release Hits Storage, Security, and Networking
 The latest release continues the string of recent updates that while important are becoming more "boring" by design as the platform gains further maturity.
The latest release continues the string of recent updates that while important are becoming more "boring" by design as the platform gains further maturity.
A Solution to Compression Oracles on the Web

This is a guest post by Blake Loring, a PhD student at Royal Holloway, University of London. Blake worked at Cloudflare as an intern in the summer of 2017.
Compression is often considered an essential tool when reducing the bandwidth usage of internet services. The impact that the use of such compression schemes can have on security, however, has often been overlooked. The recently detailed CRIME, BREACH, TIME and HEIST attacks on TLS have shown that if an attacker can make requests on behalf of a user then secret information can be extracted from encrypted messages using only the length of the response. Deciding whether an element of a web-page should be secret often depends on the content of the page, however there are some common elements of web-pages which should always remain secret such as Cross-Site Request Forgery (CSRF) tokens. Such tokens are used to ensure that malicious webpages cannot forge requests from a user by enforcing that any request must contain a secret token included in a previous response.
I worked at Cloudflare last summer to investigate possible solutions to this problem. The result is a project called cf-nocompress. The Continue reading
London & Barcelona developers, we want to meet you this week


Are you based in London or Barcelona? Drop by the Cloudflare London office to meet Kenton Varda, lead architect of Cloudflare Workers, front end developers Marta Bondyra and David Sancho from Typeform, or drop by the Typeform office in Barcelona to hear from Jason Harmon, Typeform’s Chief Platform Officer. My Developer Relations teammates and I are visiting these cities over the next two weeks. We’d love to meet you and invite you to the three events we’re hosting.
Our first stop is the Cloudflare London office. Developers from our Cloudflare Apps partner, Typeform, are leading a talk on Tuesday, March 27th. The lead architect of Cloudflare Workers, Kenton Varda, is going to lead a follow-up talk about edge computing on Wednesday, March 28th.
Event #1: Building for a tech audience: Great dev lessons for adventurous makers
Tuesday, March 27th: 18:00-20:00
Location: Cloudflare London - 25 Lavington St, Second floor | SE1 0NZ London
Creating software from scratch, although fun, can be time consuming and expensive. Marta and David, both developers at Typeform, will tell you why their teams built tools to make the lives of developers a little easier and what they learned along the way.
How NSX Is Tapping into the Human Element Behind Network Virtualization

Virtualization can be a tricky concept for some people to wrap their heads around. Trying to explain the functionalities and benefits of technology like VMware NSX can quickly devolve into techno-babble. With that said, we’re trying to take another approach—a more human approach. Below are three customer stories that emphasize a human-interest element behind network virtualization and showcase the power of technologies like NSX to better human lives.
NSX Powers a ‘Classroom in the Cloud’ for Illinois Students
When the technology leaders of Bloomington’s public schools started looking for a way to make advanced, enterprise-level computing and Internet services affordable to students, they went the co-op route and turned to IlliniCloud. IlliniCloud has proven to be a game-changer for a public education system in crisis. The co-op is transforming the technology infrastructures of not just Bloomington’s public school district, but every school district in Illinois with an affordable and efficient model that results in major cost savings for schools, along with upgrades in technology and aging infrastructures.
VMware is the backbone of IlliniCloud and a natural fit, according to Jason Radford, CTO of IlliniCloud: “VMware believed in the IlliniCloud. They gave us the tools that were Continue reading

