Aryaka’s Global Network Provides Unique SD-WAN Security
 Aryaka's Passport service integrates security from Palo Alto Networks, Zscaler, and Radware.
Aryaka's Passport service integrates security from Palo Alto Networks, Zscaler, and Radware.
Summary of Cisco NX-OS security vulnerabilities I uncovered – Maximum Entropy

Cisco took FOUR YEARS to patch disclosed vulnerabilities in NX-OS.
Equinix Moves Into Cloud Security With Key Management, Encryption Service
 It uses Intel and Fortanix software.
It uses Intel and Fortanix software.
Short Take: Side Channel Attacks
In this short take, recently posted over at the Network Collective, I discuss what a side channel attack is, and why they are important.
Hub One Selects Versa to Offer SD-WAN, SD-Security to Enterprises
 The France-based provider enhanced its WAN capabilities with Versa's Cloud IP platform.
The France-based provider enhanced its WAN capabilities with Versa's Cloud IP platform.
Security Startup BioCatch Closes $30M Funding Round for ‘Behavioral Biometrics’
 The platform monitors more than 5 billion transactions per month, and generates real-time alerts when it detects behavioral anomalies.
The platform monitors more than 5 billion transactions per month, and generates real-time alerts when it detects behavioral anomalies.
Rough Guide to IETF 101: Internet of Things
The Internet of Things (IoT) is an increasingly hot buzzword around the Internet industry and the broader technology and innovation business arenas. We are often asked what the IETF is doing in relation to IoT and in this short Rough Guide to IETF 101 post I’d like to highlight some of the relevant sessions scheduled during the upcoming IETF 101 meeting in London. Also check out the IETF Journal IoT Category, the IETF IoT page, the IETF IoT Directorate, the Internet Society’s IoT page, or the Online Trust Alliance IoT page for more details about many of these topics. See also this recent article in the IETF Journal: Internet of Things: Standards and Guidance from the IETF.
The IETF Hackathon, held the weekend preceding the main IETF meeting (17-18 March), will include at least four projects directly related to IoT, with the possibility of more being added. More information is on the Hackathon wiki.
- Firmware Updates for Internet of Things
- Semantic Interoperability (WISHI – Workshop on IoT Semantic/Hypermedia Interoperability) Test Event
- 6LoRITT: 6LoWPAN Interoperability Testing Sessions (plugtest) with the F-Interop Testing Platform
- Measuring leakage from IoT with a MITM (“man in the middle”) proxy
Deprecating TLS 1.0 and 1.1 on api.cloudflare.com
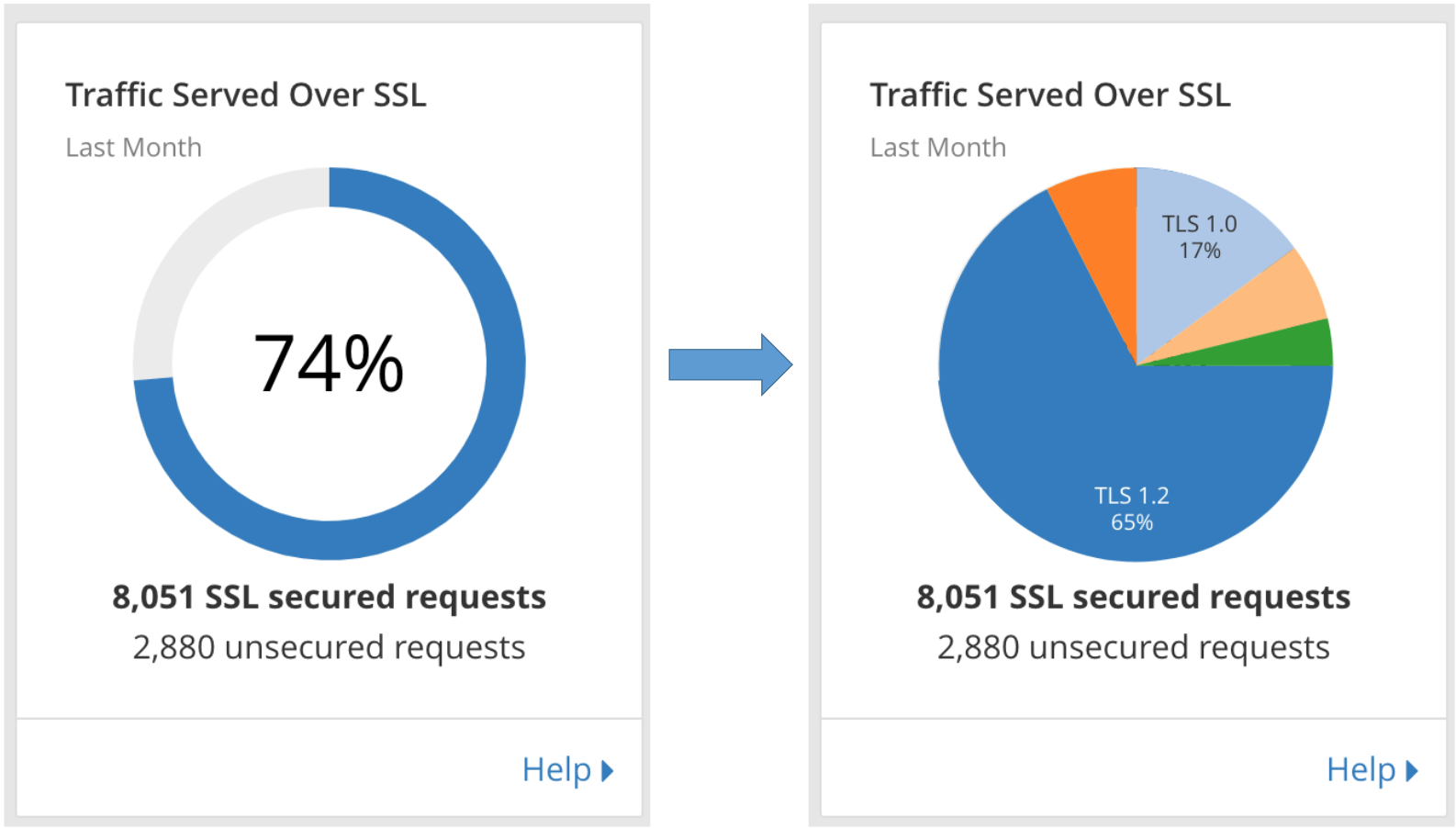
On June 4, Cloudflare will be dropping support for TLS 1.0 and 1.1 on api.cloudflare.com. Additionally, the dashboard will be moved from www.cloudflare.com/a to dash.cloudflare.com and will require a browser that supports TLS 1.2 or higher.
No changes will be made to customer traffic that is proxied through our network, though you may decide to enforce a minimum version for your own traffic. We will soon expose TLS analytics that indicate the percent of connections to your sites using TLS 1.0-1.3, and controls to set a specific minimum version. Currently, you may enforce version 1.2 or higher using the Require Modern TLS setting.
Prior to June 4, API calls made with TLS 1.0 or 1.1 will have warning messages inserted into responses and dashboard users will see a banner encouraging you to upgrade your browser. Additional details on these changes, and a complete schedule of planned events can be found in the timeline below.
Background
Transport Layer Security (TLS) is the protocol used on the web today to encrypt HTTPS connections. Version 1.0 was standardized almost 20 years ago as the successor to SSL Continue reading
Cyber Espionage Campaign ‘Slingshot’ Targets Victims Via Routers – Threatpost

Mikrotik routers as an attack vector
Applied Networking Research Workshop (ANRW) Call for Papers Due 20 April
We’re excited to share news of the third edition of the Applied Networking Research Workshop (ANRW2018), which will take place in Montreal, Quebec, on Monday, July 16 at the venue of the Internet Engineering Task Force (IETF) 102 meeting. The workshop program already includes some great invited talks and the Call for Papers is open now, with a deadline of 20 April.
ANRW2018 will provide a forum for researchers, vendors, network operators and the Internet standards community to present and discuss emerging results in applied networking research. The workshop will also create a path for academics to transition research back into IETF standards and protocols, and for academics to find inspiration from topics and open problems addressed at the IETF. Accepted short papers will be published in the ACM Digital Library.
ANRW2018 particularly encourages the submission of results that could form the basis for future engineering work in the IETF, that could change operational Internet practices, that can help better specify Internet protocols, or that could influence further research and experimentation in the Internet Research Task Force (IRTF).
If you have some relevant work and would like to join us in Montreal for the workshop and maybe stick Continue reading
What John Oliver gets wrong about Bitcoin
John Oliver covered bitcoin/cryptocurrencies last night. I thought I'd describe a bunch of things he gets wrong.How Bitcoin works
Rough Guide to IETF 101: Internet Infrastructure Resilience
In this post of the Internet Society Rough Guide to IETF 101, I’ll focus on important work the IETF is doing that helps improve security and resilience of the Internet infrastructure.
BGP
What happens if an IXP operator begins maintenance work on the switches without ensuring that BGP sessions between the peers have been shut down? A network disruption and outage. A draft now in the RFC editor queue, “Mitigating Negative Impact of Maintenance through BGP Session Culling”, provides guidance to IXP operators on how to avoid such situations by forcefully tearing down the BGP sessions (session culling) affected by the maintenance before the maintenance activities commence. This approach allows BGP speakers to pre-emptively converge onto alternative paths while the lower layer network’s forwarding plane remains fully operational.
Another draft also in the RFC editor queue, “Graceful BGP session shutdown”, addresses issues related to planned maintenance. The procedures described in this document can be applied to reduce or avoid packet loss for outbound and inbound traffic flows initially forwarded along the peering link to be shut down. These procedures trigger, in both Autonomous Systems (AS), rerouting to alternate paths if they exist within the Continue reading
CGN, IPv6 and fighting online crime…
Security and Speed Remain Tradeoffs for Containers in HPC Environments
 The National Center for Atmospheric Research developed its own container platform.
The National Center for Atmospheric Research developed its own container platform.
Short Take – Side Channel Attack
Do you know what a side channel attack is? Do you know how it relates to you as a Network Engineer? In today’s Network Collective Short Take, Russ White helps explain what a side channel attack is, how it works, and some of the challenges that are inherent in defending against it.
The post Short Take – Side Channel Attack appeared first on Network Collective.
Tenable’s Lumin Helps CISOs Measure and Quantify Cyber Risk
 The company says the average customer detects upwards of 9,000 high- or critical-severity vulnerabilities every month.
The company says the average customer detects upwards of 9,000 high- or critical-severity vulnerabilities every month.
Netsparker Closes $40M Series A for its App Scanning Software
 San Francisco private equity fund Turn/River Capital led the round.
San Francisco private equity fund Turn/River Capital led the round.
Mesosphere Tightly Integrates Kubernetes in DC/OS Update
 The DC/OS platform slashes the steps required for production-ready Kubernetes.
The DC/OS platform slashes the steps required for production-ready Kubernetes.
Some notes on memcached DDoS
I thought I'd write up some notes on the memcached DDoS. Specifically, I describe how many I found scanning the Internet with masscan, and how to use masscan as a killswitch to neuter the worst of the attacks.Test your servers
Before Commenting on Someone Mentioning RFC1925 ;)
Some of my readers got annoyed when I mentioned Google’s BeyondCorp and RFC 1925 in the same sentence (to be perfectly clear, I had Rule#11 in mind). I totally understand that sentiment – reading the reactions from industry press it seems to be the best thing that happened to Enterprise IT in decades.
Let me explain in simple terms why I think it’s not such a big deal and definitely not something new, let alone revolutionary.
Read more ...



