Creating a single pane of glass for your multi-cloud Kubernetes workloads with Cloudflare
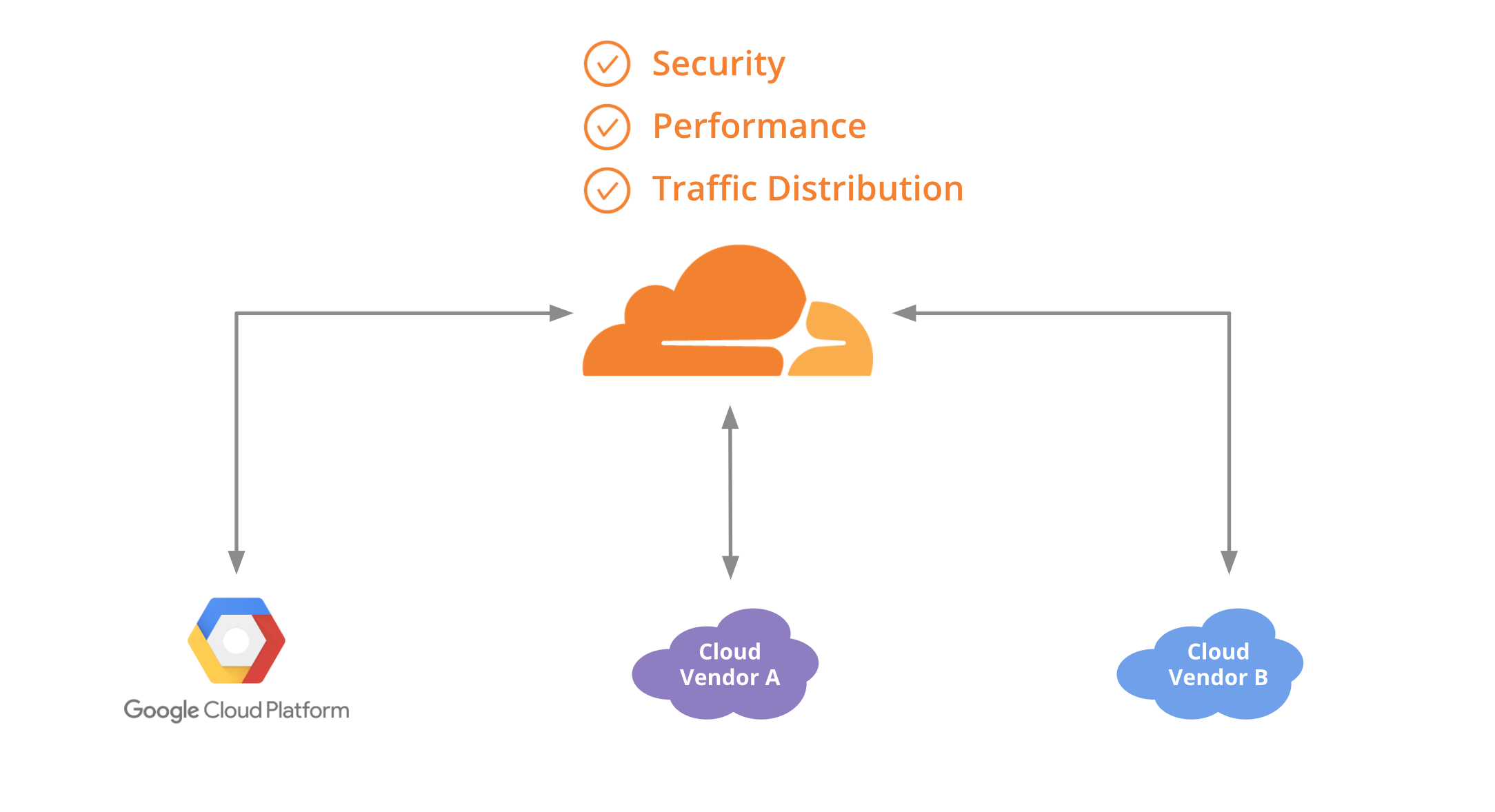
(This is a crosspost of a blog post originally published on Google Cloud blog)
One of the great things about container technology is that it delivers the same experience and functionality across different platforms. This frees you as a developer from having to rewrite or update your application to deploy it on a new cloud provider—or lets you run it across multiple cloud providers. With a containerized application running on multiple clouds, you can avoid lock-in, run your application on the cloud for which it’s best suited, and lower your overall costs.
If you’re using Kubernetes, you probably manage traffic to clusters and services across multiple nodes using internal load-balancing services, which is the most common and practical approach. But if you’re running an application on multiple clouds, it can be hard to distribute traffic intelligently among them. In this blog post, we show you how to use Cloudflare Load Balancer in conjunction with Kubernetes so you can start to achieve the benefits of a multi-cloud configuration.
To continue reading follow the Google Cloud blog here or if you are ready to get started we created a guide on how to deploy an application using Kubernetes on GCP and AWS Continue reading
The Cost of Cybercrime
Most people paying attention would expect that the cost of cybercrime has gone up in recent years. But a new report has put a number on it: Worldwide cybercrime costs an estimated $600 billion USD a year.
That’s up from $500 billion USD in 2014, the last time security vendor McAfee and think tank the Center for Strategic and International Studies released a similar study. The new estimate amounts to 0.8 percent of global GDP, up from 0.7 percent in 2014.
“Cybercrime is relentless, undiminished, and unlikely to stop,” writes report author James Lewis, senior vice president at CSIS. “It is just too easy and too rewarding, and the chances of being caught and punished are perceived as being too low.”
Lewis points to poorly-protected IoT devices as a particular problem. Insecure IoT devices “provide new, easy approaches to steal personal information or gain access to valuable data or networks,” he writes. They also power botnets that can create massive denial-of-service attacks.
Among the other reasons for the growth in the cost of cybercrime:
- Cybercriminals are embracing new attack technologies.
- Many new Internet users come from countries with weak cybersecurity.
- Online crime is becoming easier through cybercrime-as-a-service Continue reading
Cisco and Rackspace Team Up on Multi-Cloud Security
 The managed cloud provider deploys more than 22,000 Cisco firewalls.
The managed cloud provider deploys more than 22,000 Cisco firewalls.
Why Is Container Security So Difficult?
 IT departments want containers to make their lives easier, not harder.
IT departments want containers to make their lives easier, not harder.
AT&T Expands Network-Based SD-WAN to 150 Countries
 Companies can mix and match connectivity for different site types while maintaining a single network.
Companies can mix and match connectivity for different site types while maintaining a single network.
Future Thinking: Niel Harper on Cyber Threats
In 2017, the Internet Society unveiled the 2017 Global Internet Report: Paths to Our Digital Future. The interactive report identifies the drivers affecting tomorrow’s Internet and their impact on Media & Society, Digital Divides, and Personal Rights & Freedoms. In February 2018, we interviewed two stakeholders – Cyrating, a cybersecurity ratings agency, and Niel Harper, Senior Manager, Next Generation Leaders at the Internet Society – to hear their different perspectives on the forces shaping the Internet.
Niel Harper is a Young Global Leader at the World Economic Forum. He has more than 20 years of experience in the areas of telecoms management, cybersecurity, IT governance and strategy, ICT policy research and advisory services, and program management. (You can read Cyrating’s interview here).
The Internet Society: Experts predict an increase of frequency and impact of cyberattacks. What form are they likely to take in the future?
Niel Harper: In the foreseeable future, attackers are likely to fall under three categories: organized criminals seeking to profit from malicious online activities, online protesters (also known as hacktivists), and governments who target their own citizens or target other governments, whether for cyberespionage or cyberwarfare.
Criminals will continue to become more organized, selling Continue reading
Future Thinking: Cyrating on Cyber Threats
In 2017, the Internet Society unveiled the 2017 Global Internet Report: Paths to Our Digital Future. The interactive report identifies the drivers affecting tomorrow’s Internet and their impact on Media & Society, Digital Divides, and Personal Rights & Freedoms. In February 2018, we interviewed two stakeholders – Cyrating, a cybersecurity ratings agency, and Niel Harper, Senior Manager, Next Generation Leaders at the Internet Society – to hear their different perspectives on the forces shaping the Internet’s future.
Cyrating is the first cybersecurity ratings agency anchored in Europe, and helps forward-thinking organizations maximize their cybersecurity performance and investments. It identifies potential for improvement, benchmarks it against industry best practices, and provides standardized cybersecurity metrics. We spoke to François Gratiolet, one of Cyrating’s founders, about the future of a secure and trusted Internet.
(You can read Niel Harper’s interview here).
The Internet Society: Experts predict an increase of frequency and impact of cyberattacks. What form are they likely to take in the next three to five years?
François Gratiolet: We believe cyberattacks will intensify in the next three to five years; targeting both Internet users and the Internet’s underlying infrastructure. User attacks will move from phishing to social media, with Continue reading
Validating Leaked Passwords with k-Anonymity


Today, v2 of Pwned Passwords was released as part of the Have I Been Pwned service offered by Troy Hunt. Containing over half a billion real world leaked passwords, this database provides a vital tool for correcting the course of how the industry combats modern threats against password security.
I have written about how we need to rethink password security and Pwned Passwords v2 in the following post: How Developers Got Password Security So Wrong. Instead, in this post I want to discuss one of the technical contributions Cloudflare has made towards protecting user information when using this tool.
Cloudflare continues to support Pwned Passwords by providing CDN and security functionality such that the data can easily be made available for download in raw form to organisations to protect their customers. Further; as part of the second iteration of this project, I have also worked with Troy on designing and implementing API endpoints that support anonymised range queries to function as an additional layer of security for those consuming the API, that is visible to the client.
This contribution allows for Pwned Passwords clients to use range queries to search for breached passwords, without having to disclose a complete unsalted Continue reading
How Developers got Password Security so Wrong
Both in our real lives, and online, there are times where we need to authenticate ourselves - where we need to confirm we are who we say we are. This can be done using three things:
- Something you know
- Something you have
- Something you are
Passwords are an example of something you know; they were introduced in 1961 for computer authentication for a time-share computer in MIT. Shortly afterwards, a PhD researcher breached this system (by being able to simply download a list of unencrypted passwords) and used the time allocated to others on the computer.
As time has gone on; developers have continued to store passwords insecurely, and users have continued to set them weakly. Despite this, no viable alternative has been created for password security. To date, no system has been created that retains all the benefits that passwords offer as researchers have rarely considered real world constraints[1]. For example; when using fingerprints for authentication, engineers often forget that there is a sizable percentage of the population that do not have usable fingerprints or hardware upgrade costs.
Cracking Passwords
In the 1970s, people started thinking about how to better store passwords and cryptographic hashing started to Continue reading
Vectra Raises $123M for Global Push of its AI-Based Security Platform
 The startup’s revenue grew 181 percent in 2017 over the previous year.
The startup’s revenue grew 181 percent in 2017 over the previous year.
eBook: Making Networks Secure
 In this SDxCentral eBook, Making Networks Secure, we look at some of the key security strategies that are being used to protect networks in this new virtualized world.
In this SDxCentral eBook, Making Networks Secure, we look at some of the key security strategies that are being used to protect networks in this new virtualized world.
Episode 22 – Securing BGP
In part 3 of our deep dive into BGP operations, Nick Russo and Russ White join us again on Network Collective to talk about securing BGP. In this episode we cover topics like authentication, advertisement filtering, best practices, origin security, path security, and remotely triggered black holes.
 We would like to thank Cumulus Networks for sponsoring this episode of Network Collective. Cumulus is offering you, our listeners, a completely free O’Reilly ebook on the topic of BGP in the data center. You can get your copy of this excellent technical resource here: http://cumulusnetworks.com/networkcollectivebgp
We would like to thank Cumulus Networks for sponsoring this episode of Network Collective. Cumulus is offering you, our listeners, a completely free O’Reilly ebook on the topic of BGP in the data center. You can get your copy of this excellent technical resource here: http://cumulusnetworks.com/networkcollectivebgp
Show Notes:
- Authentication
- Classic MD5
- Enhanced Authentication extensions (EA). Supported by IOS XR and allows for SHA1 as well, along with key-chain rotations. Doesn’t appear commonly used
- GTSM, and how it can be better than the previous option in some cases
- Basic prefix filtering:
- From your customers: allow any number of their own AS prepended
- From the Internet: block bogons (RFC1918, class D/E, etc)
- To your peers: only your local space (ie, your customers)
- From your peers: only routes originating from their AS (any # of prepends)
- BCP38
- Techniques for spoofing prevention
- Describe with a simple snail mail analogy
- Usually uRPF strict Continue reading
Ready for Take-Off with Kubernetes, Cloud Foundry, and vSphere
A complex and diverse world
Singapore. Etihad. Wow. I always found it impressive when airlines were able to build a business and a brand without a significant domestic customer base to start off from. They instead focus on the global market, which is much more challenging. There is a competitive landscape of many players. There is the complexity of interconnecting a world of disparate lands and diverse customer cultures and preferences. An impressive feat.
The world of networking is becoming quite similar. From private, hybrid, and public cloud models, to increased use of SaaS, to the way SaaS and other apps are built using microservices architectures and containers, the landscape of islands to connect in an inherently secure and automated fashion is increasingly diverse and complex.
An app built to demonstrate this diversity
If the airline to networking analogy is lost on you, or you think it’s too much of a stretch, let me pull up the second reason I used planes in my symbolism. My brilliant colleague Yves Fauser built an app to demonstrate how NSX is connecting and securing this variety of new app frameworks, and it happens to be a “plane spotter” app. You may have already Continue reading
FIRST/TF-CSIRT: The Changing Face of Cybersecurity
The Internet Society was recently approved as a Liaison Member of TF-CSIRT, the European Forum for Computer Security Incident Response Teams, and therefore took the opportunity to participate in the FIRST/TF-CSIRT Symposium that was held 5-7 February 2018 in Hamburg, Germany.
The Internet Society continues to support organisations and activities concerned with maintaining the safety, stability and security of the Internet, and our colleague Kevin Meynell is already known within the TF-CSIRT community having run the forum between 2008 and 2012 and overseen its transition from a grouping of primarily academic CSIRTs to a wider industry body encompassing more than 160 National, Government, Military and Commercial CSIRTs, as well as those in academia.
TF-CSIRT meets three times per year, but starting in 2008 the first meeting of the year has always been held jointly with FIRST, the global Forum of Incident Response and Security Teams. This provides an opportunity for the European CSIRTs to meet with their counterparts around the world to exchange information, and develop the networks of trust that are critical to effective cooperation in handling cyber incidents when they occur, but also in development of early warning and prevention techniques.
And a number of the presentations had particular Continue reading
Cisco Cybersecurity Report: Bad Guys Winning at Weaponizing Encryption
 More than half of all attacks resulted in financial damages of more than $500,000.
More than half of all attacks resulted in financial damages of more than $500,000.
How Useful Is Microsegmentation?
Got an interesting microsegmentation-focused email from one of my readers. He started with:
Since every SDDC vendor is bragging about need for microsegmentation in order to protect East West traffic and how their specific products are better compared to competition, I’d like to ask your opinion on a few quick questions.
First one: does it even make sense?
Read more ...NDSS 2018: Automating the Process of Vulnerability Discovery
NDSS 2018 is in full swing in San Diego this week and a couple of papers that really grabbed my attention were both in the same session on Network Security and Cellular Networks yesterday.
Samuel Jero, a PhD student at Purdue University and past IRTF Applied Networking Research Prize Winner, presented a fascinating paper on “Automated Attack Discovery in TCP Congestion Control Using a Model-guided Approach”. Of the many protocols and algorithms that are in daily use on the Internet, some are more fundamental and important than others and it doesn’t get much more fundamental and important than TCP congestion control.
TCP congestion control is what makes it possible for millions of autonomous devices and networks to seamlessly, and more-or-less fairly, share available bandwidth. Without it the network would literally collapse.
Attacks against congestion control to manipulate senders’ or receivers’ understanding of the state of the network have been known for some time. Jero and his co-authors Endadul Hoque, David Choffnes, Alan Mislove and Cristina Nita-Rotaru developed an approach using model-based testing to address the scalability challenges of previous work to automate the discovery of manipulation attacks against congestion control algorithms.
By building abstract models of several congestion Continue reading
Context-Aware Micro-segmentation – Remote Desktop Session Host Enhancements for Citrix
In a previous post by my colleague, Stijn, discussed the new changes to how NSX for vSphere 6.4 handles Remote Desktop Session Host, RDSH, systems with the Identity-based Firewall and context-aware micro-segmentation.
RDSH is an underlying technology from Microsoft that many vendors take advantage of to provide overlay management and application deployment technologies for. In this post, we’re going to discuss how NSX 6.4 and the new changes to support RDSH hosts works with Citrix XenApp systems.
Citrix XenApp can provide multiple users the ability to connect to a single system to access their applications using the RDSH technology. These users can be of the same type, for example all HR users, or of multiple types, HR and Engineering users. NSX has supported User Identity based firewalling for Virtual Desktops since the 6.0 release, but it did not address RDSH in which multiple user sessions are connecting to the same host This meant less flexibility in controlling what users could access data center application servers without isolating one set of users to one RDSH server. This model created a very rigid architecture for XenApp customers to follow, which brought about the use of Continue reading
Blockchain Makes an Appearance at Mobile World Congress 2018
 The new Trusted IoT Alliance looks at the intersection of IoT, security, and blockchain.
The new Trusted IoT Alliance looks at the intersection of IoT, security, and blockchain.