Enabling the Software-Defined Branch with NSX
Reimagining the edge
While the importance of the cloud is obvious to anyone, the increasing importance of the edge is often overlooked. As digitization and the Internet of Things are leading to an exponential growth in the number of devices, the amount of data that is being generated by sensors in devices such as self-driving-cars, mobile endpoints and people tracking systems for retail is astronomical. Analyzing and turning that data into immediate actions is key to success in the era of digitization. The cloud enables massive data storage and processing, but it does not always lend itself to real time processing and immediate actions. Latency and the sheer amount of data to be transmitted are much less of a factor for the edge compared to the data center. In order to make instant decisions, some of the data processing needs to happen at the edge. At the same time, a large number of employees no longer work form the corporate HQ, but have ever increasing expectations with regards to application access regardless of their physical location. Distributed computing across the edge, along with high performance cloud access and distributed security enforcement give organizations “the edge”. Centralizing management and operations with distributed control and Continue reading
Rant: Microsoft attempts to shift blame onto NSA
Microsoft attempts to shift some blame, reduce brand damage by attacking the NSA (which can’t fight back)
The post Rant: Microsoft attempts to shift blame onto NSA appeared first on EtherealMind.
Reflexive Access List
How Does Internet Work - We know what is networking
Some of my readers commented on my old article about reflexive access-list with issues in the configuration. I tried it in the lab again to be sure I didn’t make any mistake in the configuration example and here I’m sharing the lab and the config used. About Reflexive Access Lists Extended ACLs are a special kind of extended access-lists that have limited stateful behaviour technique implemented for TCP sessions. It is better to say that reflexive access-list is simulating stateful behaviour because it, by use of ‘established’ command, is allowing TCP packets that have the ‘ACK’ bit set but not
Some notes on Trump’s cybersecurity Executive Order
President Trump has finally signed an executive order on "cybersecurity". The first draft during his first weeks in power were hilariously ignorant. The current draft, though, is pretty reasonable as such things go. I'm just reading the plain language of the draft as a cybersecurity expert, picking out the bits that interest me. In reality, there's probably all sorts of politics in the background that I'm missing, so I may be wildly off-base.John Oliver is wrong about Net Neutrality
Tune in now to catch @lastweetonight with @iamjohnoliver on why we need net neutrality and Title II. https://t.co/muSGrItCp9— EFF (@EFF) May 8, 2017
Open vSwitch Day at OpenStack Summit 2017
This is a “liveblog” (not quite live, but you get the idea) of the Open vSwitch Open Source Day happening at the OpenStack Summit in Boston. Summaries of each of the presentations are included below.
Kubernetes and OVN on Windows
The first session was led by Cloudbase Solutions, a company out of Italy that has been heavily involved in porting OVS to Windows with Hyper-V. The first part of the session focused on bringing attendees up to speed on the current state of OVS and OVN on Hyper-V. Feature parity and user interface parity between OVS/OVN on Hyper-V is really close to OVS/OVN on Linux, which should make it easier for Linux sysadmins to use OVS/OVN on Hyper-V as well.
The second part of the session showed using OVN under Kubernetes to provide networking between Windows containers on Windows hosts and Linux containers on Linux hosts, including networking across multiple cloud providers.
Lightning Talks
The lightning talks were all under 5 minutes, so a brief summary of these are provided below:
- Joe Stringer showed how to set up OVS with an OpenFlow controller (Faucet) to do networking between multiple hosts in 5 minutes or less.
- A gentleman (I didn’t catch Continue reading
Open vSwitch Day at OpenStack Summit 2017
This is a “liveblog” (not quite live, but you get the idea) of the Open vSwitch Open Source Day happening at the OpenStack Summit in Boston. Summaries of each of the presentations are included below.
Kubernetes and OVN on Windows
The first session was led by Cloudbase Solutions, a company out of Italy that has been heavily involved in porting OVS to Windows with Hyper-V. The first part of the session focused on bringing attendees up to speed on the current state of OVS and OVN on Hyper-V. Feature parity and user interface parity between OVS/OVN on Hyper-V is really close to OVS/OVN on Linux, which should make it easier for Linux sysadmins to use OVS/OVN on Hyper-V as well.
The second part of the session showed using OVN under Kubernetes to provide networking between Windows containers on Windows hosts and Linux containers on Linux hosts, including networking across multiple cloud providers.
Lightning Talks
The lightning talks were all under 5 minutes, so a brief summary of these are provided below:
- Joe Stringer showed how to set up OVS with an OpenFlow controller (Faucet) to do networking between multiple hosts in 5 minutes or less.
- A gentleman (I didn’t catch Continue reading
Security-as-a-Service on the Rise Among Mid-Tier Companies
 Network security spending is projected to reach $3.5 billion in 2021.
Network security spending is projected to reach $3.5 billion in 2021.
Docker Enterprise Edition Brings New Life Back to Legacy Apps at Northern Trust
Many organizations understand the value of building modern 12-factor applications with microservices. However, 90+% of applications running today are still traditional, monolithic apps. That is also the case for Northern Trust – a 128-year old financial services company headquartered in Chicago, Illinois. At DockerCon 2017, Rob Tanner, Division Manager for Enterprise Middleware at Northern Trust, shared how they are using Docker Enterprise Edition (EE) to modernize their traditional applications to make them faster, safer, and more performant.
Bringing Agility and Security to Traditional Apps
Founded in 1889, Northern Trust is a global leader in asset servicing, asset management, and banking for personal and institutional clients. Their clients expect best-of-breed services and experiences from Northern Trust and Rob’s team plays a large role in delivering that. While their development teams are focused on microservices apps for greenfield projects, Rob is responsible for over 400 existing WebLogic, Tomcat, and .NET applications. Docker EE became the obvious choice to modernize these traditional apps and manage their incredibly diverse environment with a single solution.
Containerizing traditional applications with Docker EE gives Northern Trust a better way to manage them and some immediate benefits:
- Improved security: As a financial institution, security is a top priority. Continue reading
Hacker dumps, magnet links, and you
In an excellent post pointing out Wikileaks deserves none of the credit given them in the #MacronLeaks, the author erroneously stated that after Archive.org took down the files, that Wikileaks provided links to a second archive. This is not true. Instead, Wikileaks simply pointed to what's known as "magnet links" of the first archive. Understanding magnet links is critical to understanding all these links and dumps, so I thought I'd describe them.The tl;dr version is this: anything published via BitTorrent has a matching "magnet link" address, and the contents can still be reached via magnet links when the original publisher goes away.
In this case, the leaker uploaded to "archive.org", a popular Internet archiving resource. This website allows you to either download files directly, which is slow, or via peer-to-peer using BitTorrent, which is fast. As you know, BitTorrent works by all the downloaders exchanging pieces with each other, rather getting them from the server. I give you a piece you don't have, in exchange for a piece I don't have.
BitTorrent, though still requires a "torrent" (a ~30k file that lists all the pieces) and a "tracker" (http://bt1.archive.org:6969/announce) that keeps a list Continue reading
Some notes on #MacronLeak
Tonight (Friday May 5 2017) hackers dumped emails (and docs) related to French presidential candidate Emmanuel Macron. He's the anti-Putin candidate running against the pro-Putin Marin Le Pen. I thought I'd write up some notes.Update: Several people [*] have pointed out Trend Micro reporting that Russian/APT28 hackers were targeting Macron back on April 24. Coincidentally, this is also the latest that emails appear in the dump.
Technology Short Take #82
Welcome to Technology Short Take #82! This issue is a bit behind schedule; I’ve been pretty heads-down on some projects. That work will come to fruition in a couple weeks, so I should be able to come up for some air soon. In the meantime, here’s a few links and articles for your reading pleasure.
Networking
- Kristian Larsson shows how to validate data using YANG. Practical examples like this have really helped me better understand YANG and its relationship to structured data you might exchange with a device or service.
- There’s lots of talk about applying test-driven development (TDD) principles in various automation contexts, but I like the fact that Ajay Chenampara provides some practical examples in his blog post on applying TDD in network automation using Ansible.
- Matt Oswalt talks about how the combination of NAPALM and StackStorm enables some interesting results, including the ability to verify configuration consistency. StackStorm isn’t something I’ve had the opportunity to learn/use at all, but it’s on my (ever-growing) list of things to check out.
- Aaron Conole provides an overview of using the
ovs-dpctlcommand to “program” the Open vSwitch (OVS) kernel module. It’s a bit geeky, but does provide some insight into Continue reading
FBI’s Comey dangerous definition of “valid” journalism
The First Amendment, the "freedom of speech" one, does not mention journalists. When it says "freedom of the press" it means the physical printing press. Yes, that does include newspapers, but it also includes anybody else publishing things, such as the famous agitprop pamphlets published by James Otis, John Dickinson, and Thomas Paine. There was no journalistic value to Thomas Paine's Common Sense. The pamphlet argued for abolishing the monarchy and for American independence.Today in testimony before congress, FBI directory James Comey came out in support of journalism, pointing out that they would not prosecute journalists doing their jobs. But he then modified his statement, describing "valid" journalists as those who in possession of leaks would first check with the government, to avoid publishing anything that would damage national security. It's a power the government has abused in the past to delay or censor leaks. It's specifically why Edward Snowden contacted Glenn Greenwald and Laura Poitras -- he wanted journalists who would not kowtow the government on publishing the leaks.
Comey's testimony today was in regards to prosecuting Assange and Wikileaks. Under the FBI's official "journalist" classification scheme, Wikileaks are not real journalists, but instead publish "intelligence porn" and Continue reading
Juniper Control Plane Protection
How Does Internet Work - We know what is networking
I already wrote about Control Plane Protection in one of my previous posts focused on Cisco device configuration. Here we will make the same thing on Juniper device, I was using Juniper SRX300 and Juniper SRX1500 devices in my lab. CoPP ?? Control Plane Protection (CoPP) is a method of protecting processor unit, running services on your network device, against excessive flooding. Excessive flooding of traffic aimed towards your router/firewall processor, being that valid or malicious, is always undesirable and can also be dangerous. A network device, which starts the receive more control traffic that his processor can process, will
Securing Network Automation Video Is Online
The awesome Troopers crew published conference videos, including my Securing Network Automation presentation (more, including slide deck).
Research: Verizon Data Breach Investigations Report 2017
Must read report to stay informed on security.
The post Research: Verizon Data Breach Investigations Report 2017 appeared first on EtherealMind.
The Myth of Pure Cloud
 Despite the movement to cloud, data centers will still be around for the foreseeable future.
Despite the movement to cloud, data centers will still be around for the foreseeable future.
Introducing TLS with Client Authentication
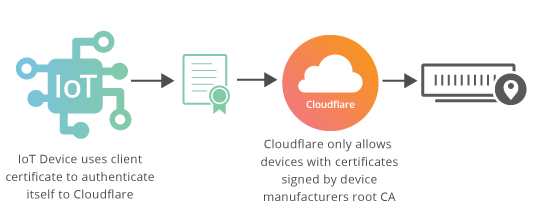
In a traditional TLS handshake, the client authenticates the server, and the server doesn’t know too much about the client. However, starting now, Cloudflare is offering enterprise customers TLS with client authentication, meaning that the server additionally authenticates that the client connecting to it is authorized to connect.
TLS Client Authentication is useful in cases where a server is keeping track of hundreds of thousands or millions of clients, as in IoT, or in a mobile app with millions of installs exchanging secure information. For example, an IoT company can issue a unique client certificate per device, and then limit connections to their IoT infrastructure to only their devices by blocking connections where the client doesn’t present a certificate signed by the company’s certificate authority.
Or in the case of a mobile banking app, where the bank wants to ensure customers’ secure financial data doesn’t get stolen by bots spoofing their mobile app, they can issue a unique certificate to every app install and in the TLS handshake validate requests are coming from their mobile app. Client authentication is also useful for VPNs, enterprise networks or staging sites, where corporations and developers need to lock down connections to only laptops Continue reading
Fortinet Reports Another Impressive Quarter
 Fortinet scored a $12M customer deal this quarter.
Fortinet scored a $12M customer deal this quarter.
vRealize Network Insight, NSX and Palo Alto Networks for micro-segmentation
Data Center cyber security is a fast-moving target where the IT teams need to constantly stay ahead of those that wish to do evil things. As security attacks can come from all directions, externally, and internally as well, the IT teams must fortify all the data, with a zero-trust security approach. Perimeter security augmented with intrusion detection and protection at the application level are the tools of choice for most data centers. This protects outsiders from getting in, as well as ensuring that the applications do not get impacted by a virus or other forms of malicious activities.
What has not been addressed is the intercommunications of applications amongst themselves, especially within the hypervisor layer, where virtual machines are communicating in an East-West traffic pattern. Traffic never hits the perimeter, and the conversations are happening several layers below the application layers where IDS sits. East-west traffic, from within the data center, has been an area overlooked as there is a gap organizationally. Simply put no one is paying attention to this area of vulnerability. The network infrastructure security teams are fortifying the perimeter, while the server teams are deploying IDS/IPS solutions. What has gone unnoticed is the East-West Continue reading
