The false-false-balance problem
Until recently, journalism in America prided itself on objectivity -- to report the truth, without taking sides. That's because big debates are always complexed and nuanced, and that both sides are equally reasonable. Therefore, when writing an article, reporters attempt to achieve balance by quoting people/experts/proponents on both sides of an issue.Palo Alto Disappoints With Its Q2 Forecast
 Yet again, the stock dives after Palo Alto beats expectations.
Yet again, the stock dives after Palo Alto beats expectations.
Symantec Offers $2.3B for Consumer Security Firm LifeLock
 The deal includes LifeLock's colorful history, like it or not.
The deal includes LifeLock's colorful history, like it or not.
Oracle to Acquire DNS Provider Dyn
 Dyn made headlines in October when it was targeted in a DDoS attack that caused widespread outages.
Dyn made headlines in October when it was targeted in a DDoS attack that caused widespread outages.
Reverese Shell on Linux
Reverse shell is technique when a client connects to a server and the client provides its shell to the server. Clients is typically a host hidden behind the NAT or a firewall having an access to the server but not vice versa. Thanks to a reverse shell the server controls a client's shell having an access to the client's network even the client is hidden behind the NAT. They are several methods how to create a reverse shell used depending on software available on the client. I will show how to create a reverse shell using SSH, Ncat and Bash.
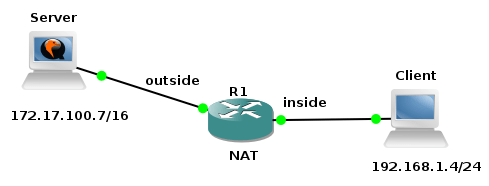
Picture 1 - Network Topology
Picture 1 shows our testing topology. The client (Ubuntu Server 16.04) is located behind the NAT with the IP address 192.168.1.4/24. The server (Kubuntu 16.04) has assigned the IP address 172.17.100.7/16.
1. Reverse Shell Using SSH Reverse Tunnel
This method is based on the fact that the client has knowledge of the server SSH login credentials and vice versa. SSH server must be running on both the server and client. Client must be allowed to access server through firewall.
Client:
$ ssh -R 10000:127.0.0.1:22 [email protected]. Continue reading
Technology Short Take #73
Welcome to Technology Short Take #73. Sorry for the long delay since the last Technology Short Take; personal matters have been taking quite the toll (if you follow me on Twitter, you’ll know to what personal matters I’m referring). In any case, enough of that—here’s some data center-related content that I hope you find useful!
Networking
- Ansible has made some good progress in supporting network automation in the latest release (2.2), according to this blog post. This is an area where I hope to spend more time in the coming weeks before years’ end.
- Tomas Fojta shows how to use a PowerShell script to monitor the health of NSX Edge gateways.
- Jeremy Stretch mulls over the (perceived) problem of getting traffic into and out of overlay networks. I recommend reading this article, as well as reading the comments. Many commenters suggest just using L3 and having the hosts participate in a routing protocol like BGP, but as Jeremy points out many switches don’t have the capacity to handle that many routes. (Or, if they do, they’re quite expensive.) Seems like there’s this company in Palo Alto making a product that handles this issue pretty decently…(hint).
- Cumulus Continue reading
Security Firm Prevalent Closes $60M in Funding
 The company helps small and mid-size companies reduce threats and risks from third-party vendors.
The company helps small and mid-size companies reduce threats and risks from third-party vendors.
Q&A with Kelly Ahuja, the New CEO at Versa Networks
 The former Cisco exec likes the security aspect of Versa's SD-WAN.
The former Cisco exec likes the security aspect of Versa's SD-WAN.
IBM Drops $200M on New Security Capabilities
 This includes its acquisition of Resilient Systems.
This includes its acquisition of Resilient Systems.
Siemplify Raises $10M for Its Security Platform
 The company has raised $14M since its launch in February.
The company has raised $14M since its launch in February.
Reactive Malicious Domain Detection (ENTRADA)
One interesting trend of the last year or two is the rising use of data analytics and ANI (Artificial Narrow Intelligence) in solving network engineering problems. Several ideas (and/or solutions) were presented this year at the IETF meeting in Seoul; this post takes a look at one of these. To lay the groundwork, botnets are often controlled through a set of domain names registered just for this purpose. In the same way, domain names are often registered just to provide a base for sending bulk mail (SPAM), phishing attacks, etc. It might be nice for registrars to make some attempt to remove such domains abused for malicious activities, but it’s difficult to know what “normal” activity might look like, or for the registrar to even track the usage of a particular domain to detect malicious activity. One of the papers presented in the Software Defined Network Research Group (SDNRG) addresses this problem directly.
The first problem is actually collecting enough information to analyze in a useful way. DNS servers, even top level domain (TLD) servers collect a huge amount of data—much more than most engineers might suspect. In fact, the DNS system is one of those vast sources of information Continue reading
Introducing Image Signing Policy in Docker Datacenter
My colleague colleague Ying Li and I recently blogged about Securing the Software Supply Chain and drew the analogy between traditional physical supply chains and the creation, building, and deployment involved in a software supply chain. We believe that a software pipeline that can be verified at every stage is an important step in raising the security bar for all software, and we didn’t stop at simply presenting the idea.
Integrated Content Trust and Image Signing Policy
In the recent release of Docker Datacenter, we announced a new feature that starts to brings these security capabilities together along the software supply chain. Built on Notary, a signing infrastructure based on The Update Framework (TUF), along with Docker Content Trust (DCT), an integration of the Notary toolchain into the Docker client, DDC now allows administrators to set up signing policies that prevent untrusted content from being deployed.
In this release of DDC, the Docker Trusted Registry (DTR) now also ships with integrated Notary services. This means you’re ready to start using DCT and the new Signing Policy features out of the box! No separate server and database to install, configure and connect to the registry.
Bringing it all together
Image Continue reading
Comments for my biracial niece
How to teach endian
On /r/programming is this post about byte-order/endianness. It gives the same information as most documents on the topic. It is wrong. It's been wrong for over 30 years. Here's how it should be taught.One of the major disciplines in computer science is parsing/formatting. This is the process of converting the external format of data (file formats, network protocols, hardware registers) into the internal format (the data structures that software operates on).
It should be a formal computer-science discipline, because it's actually a lot more difficult than you'd expect. That's because the majority of vulnerabilities in software that hackers exploit are due to parsing bugs. Since programmers don't learn about parsing formally, they figure it out for themselves, creating ad hoc solutions that are prone to bugs. For example, programmers assume external buffers cannot be larger than internal ones, leading to buffer overflows.
An external format must be well-defined. What the first byte means must be written down somewhere, then what the second byte means, and so on. For Internet protocols, these formats are written in RFCs, such as RFC 791 for the "Internet Protocol". For file formats, these are written in documents, such as those describing GIF files, JPEG Continue reading
Know What You’re Sinking Your Teeth Into—Eliminate Virtual Network Blind Spots
 Don’t blindly bite down on something until you know it’s just right.
Don’t blindly bite down on something until you know it’s just right.
Docker Datacenter adds enterprise orchestration, security policy and refreshed UI
Today we are excited to introduce new additions to Docker Datacenter, our Container as a Service (CaaS) platform for enterprise IT and application teams. Docker Datacenter provides an integrated platform for developers and IT operations teams to collaborate securely on the application lifecycle. Built on the foundation of Docker Engine, Docker Datacenter (DDC) also provides integrated orchestration, management and security around managing resources like access, images, applications, networks and more across the cluster.
This latest release of Docker Datacenter includes a number of new features and improvements focused in the following areas:
- Enterprise orchestration and operations to make running and operating multi container applications simple, secure and scalable
- Integrated end to end security to cover all of the components and people that interact with the application pipeline
- User experience and performance improvements ensure that even the most complex operations are handled efficiently
Let’s dig into some of the new features.
Enterprise orchestration with backward compatibility
This release of Docker Datacenter not only integrates the built in orchestration capabilities of Docker Engine 1.12 utilizing swarm mode and services, but also provides backwards compatibility for standalone containers using the docker run commands. To help enterprise application teams migrate, it is important Continue reading
Reliability of Clustered Solutions: Another Data Point
A while ago I wrote:
I haven’t seen any hard data, but intuition suggests that apart from hardware failures a standalone firewall might be more stable than a state-sharing firewall cluster.
Guillaume Sachot (working for a web hosting company) sent me his first-hand experience on this topic:
Read more ...RiskIQ Rakes in $30.5M in Series C Funding
 RiskIQ customers include Facebook and DocuSign.
RiskIQ customers include Facebook and DocuSign.
Accelerating the Journey to an Agile, Hybrid Cloud Infrastructure
 Rip and replace tactics almost always results in failure.
Rip and replace tactics almost always results in failure.
Introduction to Quantum Cryptography
How Does Internet Work - We know what is networking
Quantum cryptography is a new technique of securing computer network communication channel. Existing standard crypto systems are using advanced algorithms to create key pairs which are extremely hard to inverse engineer. Quantum cryptography avoids any mathematical algorithm and uses principles of quantum physics. Quantum crypto implements a new technique of generating and exchanging crypto keys which makes it impossible for third party entities to get those keys by snooping or to create man in the middle by snooping and sending copies of original key. Keys generated in this way will automatically destroy themselves if read by third-party interferer. When generated between two sides, using quantum key distribution, secret keys will