Nutanix Muscles Into Enterprise Networking Territory
 Today: compute & storage. Tomorrow: the network!
Today: compute & storage. Tomorrow: the network!
Juniper To Go: vMX & vSRX Become Available in AWS
 Another step toward blending AWS and the enterprise network.
Another step toward blending AWS and the enterprise network.
Q3 2016 Earnings Highlights and Expectations
 Here's a quick recap of how the public companies that we cover performed in the third quarter of 2016.
Here's a quick recap of how the public companies that we cover performed in the third quarter of 2016.
Yes, the FBI can review 650,000 emails in 8 days
In today's news, Comey announces the FBI have reviewed all 650,000 emails found on Anthony Wiener's computer and determined there's nothing new. Some have questioned whether this could be done in 8 days. Of course it could be -- those were 650,000 emails to Wiener, not Hillary.IMPOSSIBLE:— General Flynn (@GenFlynn) November 6, 2016
There R 691,200 seconds in 8 days. DIR Comey has thoroughly reviewed 650,000 emails in 8 days? An email / second? IMPOSSIBLE RT
Reading Wiener's own emails, those unrelated to his wife Huma or Hillary, is unlikely to be productive. Therefore, the FBI is going to filter those 650,000 Wiener emails to get at those emails that were also sent to/from Hillary and Huma.
That's easy for automated tools to do. Just search the From: and To: fields for email addresses known to be used by Hillary and associates. For example, search for [email protected] (Hillary's current email address) and [email protected] (Huma Abedin's current email).
Below is an example email header from the Podesta dump:
From: Jennifer Palmieri <[email protected]>
Date: Sat, 2 May 2015 11:23:56 -0400
Message-ID: <-8018289478115811964@unknownmsgid>
Subject: WJC NBC interview
To: H <[email protected]>, John Podesta <[email protected]>,
Huma Continue reading
The 7 Largest Rounds of Funding of 2016 (So Far)
 There are clear trends among security and monitoring companies.
There are clear trends among security and monitoring companies.
FireEye Stock Climbs After Q3, Defying Security’s Slump
 Q3 revenues grew, and losses could have been worse.
Q3 revenues grew, and losses could have been worse.
Gigamon Introduces Overlapping Flow Samples to Its Platform
 There is also a security aspect to this new capability.
There is also a security aspect to this new capability.
In which I have to debunk a second time
So Slate is doubling-down on their discredited story of a secret Trump server. Tip for journalists: if you are going to argue against an expert debunking your story, try to contact that expert first, so they don't have to do what I'm going to do here, showing obvious flaws. Also, pay attention to the data.The experts didn't find anything
The story claims:
"I spoke with many DNS experts. They found the evidence strongly suggestive of a relationship between the Trump Organization and the bank".No, he didn't. He gave experts limited information and asked them whether it's consistent with a conspiracy theory. He didn't ask if it was "suggestive" of the conspiracy theory, or that this was the best theory that fit the data.
This is why "experts" quoted in the press need to go through "media training", to avoid getting your reputation harmed by bad journalists who try their best to put words in your mouth. You'll be trained to recognize bad journalists like this, and how not to get sucked into their fabrications.
Jean Camp isn't an expert
On the other hand, Jean Camp isn't an expert. I've never heard of her before. She gets details wrong. Continue reading
Intel Security Spinoff McAfee Unifies Its Security Platform
 Intel Security will soon adopt the name McAfee entirely.
Intel Security will soon adopt the name McAfee entirely.
Setting Sail on Secret Seas with Trireme

Container networking is a tough challenge to solve. The evolving needs of creating virtual networks to allow inter-container communications is difficult. But ensuring security at the same time is enough to make you pull your hair out. Lots of companies are taking a crack at it as has been demonstrated recently by microsegmentation offerings from Cisco, VMware NSX, and many others. But a new development on this front set sail today. And the captain is an old friend.
Sailing the Security Sea
Dimitri Stiladis did some great things in his time at Nuage Networks. He created a great overlay network solution that not only worked well for software defined systems but also extended into the container world as more and more people started investigating containers as the new way to provide application services. He saw many people rushing into this area with their existing solutions as well as building new solutions. However, those solutions were all based on existing technology and methods that didn’t work well in the container world. If you ever heard someone say, “Oh, containers are just lightweight VMs…” you know what kind of thinking I’m talking about.
Late last year, Dimitri got together with some of Continue reading
Cryptography
How Does Internet Work - We know what is networking
If you want to send or store data and be sure it is safe from being intercepted, you will use Cryptography. Cryptography uses chipper as mathematical virtual lock to make data scrambled so that is not understandable if intercepted by unauthorized third parties. There are different cryptography techniques, some of them are: encryption, hashing, and steganography. Cryptography can be differentiated by usage of different key types: Symmetric Key Encryption Asymmetric Key Encryption Symmetric Key Encryption is sometimes known as Secret Key Cryptography. Main characteristic of this type of cryptography is the same key usage in encryption and decryption of transferred
Aporeto Thinks Container Security Can Really Be This Simple
 Step One: Take the network out of it.
Step One: Take the network out of it.
Apcera Platform Primes Containers for Enterprise Deployment
 Legacy apps and security are two of the big-ticket items.
Legacy apps and security are two of the big-ticket items.
Debunking Trump’s “secret server”
According to this Slate article, Trump has a secret server for communicating with Russia. Even Hillary has piled onto this story.It's time for Trump to answer serious questions about his ties to Russia. https://t.co/D8oSmyVAR4 pic.twitter.com/07dRyEmPjX— Hillary Clinton (@HillaryClinton) October 31, 2016
This is nonsense. The evidence available on the Internet is that Trump neither (directly) controls the domain "trump-email.com", nor has access to the server. Instead, the domain was setup and controlled by Cendyn, a company that does marketing/promotions for hotels, including many of Trump's hotels. Cendyn outsources the email portions of its campaigns to a company called Listrak, which actually owns/operates the physical server in a data center in Philidelphia.
In other words, Trump's response is (minus the political bits) likely true, supported by the evidence. It's the conclusion I came to even before seeing the response.
When you view this "secret" server in context, surrounded by the other email servers operated by Listrak on behalf of Cendyn, it becomes more obvious what's going on. In the same Internet address range of Trump's servers you see a bunch of similar servers, many named [client]-email.com. In other words, trump-email. Continue reading
GRE over IPSec Tunnel and NAT Between Cisco and VyOS
The goal of this tutorial is to provide a configuration for Cisco and VyOS network devices with configured PAT (Port Address Translation) that connect two remote sides A and B through point-to-point GRE tunnel encapsulated into a IPsec tunnel. In a previous tutorial we proved that GRE tunnels in conjunction with IPsec tunnels transmit multicast traffic while data integrity, authentication and confidentiality was in place. I also provided a simple configuration of GRE, IPsec tunnel and OSPF routing protocol on the Cisco and VyOS routers. In this tutorial I will go further and provide full configuration of the all network devices including PAT and access-lists. 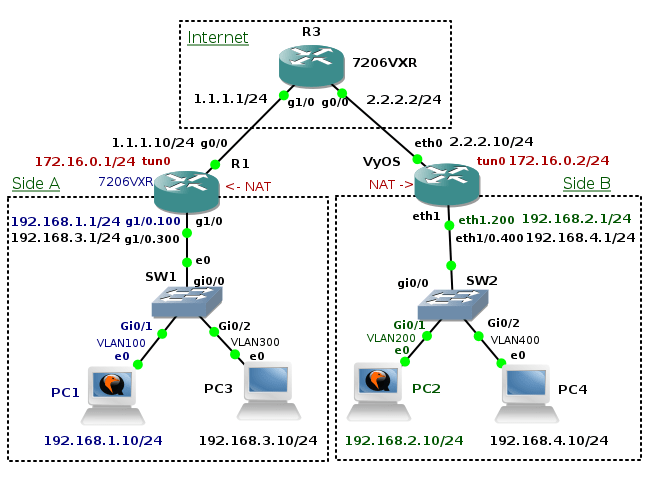
Picture 1 - Network Topology
Topology Description - Side A
Each side has a Layer 2 Cisco switch located in a LAN network. A switch connects hosts to its switchports. Each switchport is assigned to a particular VLAN. For instance, a host PC1 is connected to the switch SW1 and the switchport is assigned to a VLAN 100. Hosts in VLAN 100 (subnet 192.168.1.0/24) have guaranteed access to a remote subnet 192.168.2.0/24 via GRE/IPsec tunnel. A NAT access-list configured on a router R1 ensures that IP address of the host in VLAN 100 is not translated by PAT when a destination address is Continue reading
Nuage Thinks SD-WAN Should Reach Farther, Even Into Public Clouds
 Other SD-WANs don't think end-to-end, Nuage claims.
Other SD-WANs don't think end-to-end, Nuage claims.
Configuring Raspberry Pi as a router
Fortinet Q3 Earnings Disappoint
 Fortinet recently restructured its sales team.
Fortinet recently restructured its sales team.
F5 Beats Q4 Predictions With Strong Sales in North America
 Security seems to promise growth for the company.
Security seems to promise growth for the company.
New Attack Vector Can Amplify DDoS by 55x
 With LDAP and botnets, the amplification factor can reach unprecedented levels.
With LDAP and botnets, the amplification factor can reach unprecedented levels.