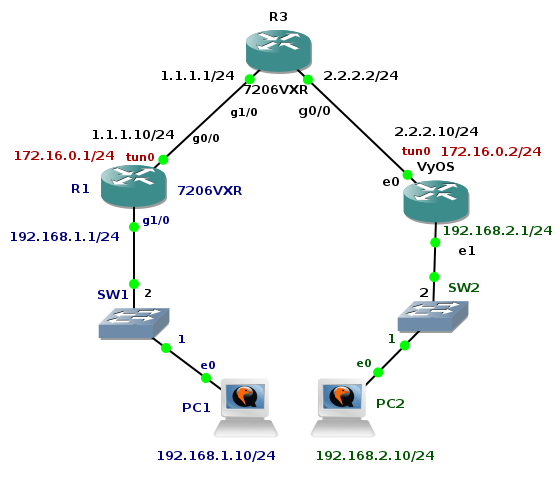
GRE over IPSec Tunnel Between Cisco and VyOS
The previous tutorial shown GRE tunnel configuration between Cisco router and Linux Core. The big advantage of GRE protocol is that it encapsulates L3 and higher protocols inside the GRE tunnel so routing updates and other multicast traffic can be successfully transferred over the tunnel. The main drawback of GRE protocol is the lack of built-in security. Data are transferred in plain-text over the tunnel and peers are not authenticated (no confidentiality). Tunneled traffic can be changed by attacker (no integrity checking of IP packets). For this reason GRE tunnel is very often used in conjunction with IPSec. Typically, GRE tunnel is encapsulated inside the IPSec tunnel and this model is called GRE over IPSec.
The tutorial shows configuration of OSPF routing protocol, GRE and IPSec tunnel on Cisco 7206 VXR router and appliance running VyOS network OS. Devices are running inside GNS3 lab an they are emulated by Dynamips (Cisco) and Qemu (VyOS).
Picture 1 - Topology
Note: VyOS installation is described here. You can easily build your own VyOS Qemu appliance using the Expect and Bash script shared in the article.
1. R3 Configuration
R3(config)# interface gigabitEthernet 1/0
R3(config-if)# ip address 1.1.1.1 255.255.255.0
R3(config-if)# no shutdown
R3(config-if)# interface gigabitEthernet 0/0
R3(config-if)# ip Continue reading
PCI Compliance in OpenStack Private Clouds With SDN
 Laying the foundation for better security moving forward.
Laying the foundation for better security moving forward.
Security Startup Illumio Joins the Docker Parade
 Illumio's ASP aims to cover all environments — which of course must include Docker containers.
Illumio's ASP aims to cover all environments — which of course must include Docker containers.
Jeb Bush is a cyber-weenie
Jeb Bush, one of them many 2016 presidential candidates, has numerous positions on "cyber" issues. They are all pretty silly, demonstrating that not only he but also his advisors profoundly misunderstand the issues.For example, his recent position opposing "NetNeutrality" regulations says this:
these rules prohibit one group of companies (ISPs) from charging another group of companies (content companies) the full cost for using their servicesUh, no, that's how Democrats frame the debate. ISPs charging content providers is actually a very bad thing. That we Republicans oppose NetNeutrality is not based on the belief that "charging content companies" is a good thing.
Instead, NetNeutrality is about technical issues like congestion and routing. Congestion is an inherent property of the Internet. NetNeutrality shifts the blame for congestion onto the ISPs. NetNeutrality means the 90% of Comcast subscribers who do not use Netflix must subsidize the 10% who are.
Or at least, that's one of the many ways Republicans would phrase the debate. More simply, all Republicans oppose NetNeutrality simply because it's over-regulation. My point is that Jeb Bush doesn't realized he's been sucked into the Democrat framing, and that what he says is garbage.
A better example is Jeb's position Continue reading
New Release of Cisco ACI Eases Layer 4-7 Integration
 The new release of Cisco Application Centric Infrastructure (ACI) includes innovations to ease Layer 4-7 network services integration.
The new release of Cisco Application Centric Infrastructure (ACI) includes innovations to ease Layer 4-7 network services integration.
Prez: Candidate synchronization
So last week I gave $10 to all the presidential campaigns, in order to watch their antics. One thing that's weird is that they often appear to act in unison, as if they are either copying each other, or are all playing from the same secret playbook.The candidates must report their donations every quarter, according to FEC (Federal Elections Commission) rules. The next deadline is September 30th. Three days before that deadline, half the candidates sent out email asking for donations to meet this "critical" deadline. They don't say why it's critical, but only that's is some sort of critical deadline that must be met, which we can only do so with your help. The real reason why, of course, is that this information will become public, implicitly ranking the amount of support each candidate has.
Four days before this deadline, I didn't get donation pleas mentioning it. Three days before, half the candidates mentioned it. It's as if one candidate sees such an email blast, realizes it's a great idea, and send's out a similar email blast of their own.
Two days before the deadline, three of the candidates sent out animated GIFs counting down to the deadline. Continue reading
Datadog Hunts Down Those Rogue Servers
 Using clustering algorithms, Datadog can spy cloud servers that aren't performing optimally.
Using clustering algorithms, Datadog can spy cloud servers that aren't performing optimally.
Phantom Cyber Raises $6.5M To Automate Security
 Someone needs to unify all those enterprise security tools, the startup reckons.
Someone needs to unify all those enterprise security tools, the startup reckons.
Juniper Unite Cloud-Enabled Enterprise Promises Agility & Security For Anytime, Anywhere Use
 As the reliance on the cloud continues to grow, Juniper finds a solution to bring agility, security, and faster services to enterprises: the Juniper Unite Cloud-Enabled Enterprise architecture.
As the reliance on the cloud continues to grow, Juniper finds a solution to bring agility, security, and faster services to enterprises: the Juniper Unite Cloud-Enabled Enterprise architecture.
How Encryption of Network Traffic Works?
How does Internet work - We know what is networking
I recently started studying again, this time as an attempt of deep-diving into some security concepts for one of my PhD courses. It’s interesting how, as much as you try to escape from it, mathematics will sooner or later catch you somewhere and you will need to learn a bit more of it. At least that happened to me… In this process I realised that if you go beyond simple security theory and network device configuration all other stuff is pure mathematics. The reason behind my unplanned course in mathematics is explained through the rest of this text. It will
Featured Interview: Paul Pindell on F5 & VMware NSX Integration
 F5 Networks Paul Pindell sat down with SDxCentral to discuss the F5 and VMware partnership and product integration with VMware NSX.
F5 Networks Paul Pindell sat down with SDxCentral to discuss the F5 and VMware partnership and product integration with VMware NSX.
CloudFlare Raises $110M with Promise to Eliminate Lots of Hardware
 A five-year-old upstart garners investments from Google, Microsoft, Baidu, and Qualcomm and sets its sights on competing with Amazon Web Services.
A five-year-old upstart garners investments from Google, Microsoft, Baidu, and Qualcomm and sets its sights on competing with Amazon Web Services.
Former Gigamon CEO Raises $7M for a Different Type of Security Monitoring
 Datiphy watches how data is being used — a managed service that's being turned into a software product for the U.S. market.
Datiphy watches how data is being used — a managed service that's being turned into a software product for the U.S. market.
I gave $10 to every presidential candidate
What happens when your candidate drops out of the 2016 presidential race? What do they do with the roughly million names of donors they've collected?SSL: A Winning Formula For A10 Networks?
 A10 and Blue Coat could find an edge by doing SSL well, one analyst believes.
A10 and Blue Coat could find an edge by doing SSL well, one analyst believes.
More Sites Turn Up With Cisco Router Malware
 SYNful Knock has been found at 199 IP addresses so far.
SYNful Knock has been found at 199 IP addresses so far.
Zerodium’s million dollar iOS9 bounty
Zerodium is offering a $1 million bounty for a browser-based jailbreak. I have a few comments about this. The two keywords to pick up on are "browser-based" and "untethered". The word "jailbreak" is a red-herring.It's not about jailbreaks. Sure, the jailbreak market is huge. It's really popular in China, and there are reports of $1 million being spent on jailbreaks. But still, actually getting a return on such an investment is hard. Once you have such a jailbreak, others will start reverse engineering it, so it's an extremely high risk. You may get your money back, but there's a good chance you'll be reverse-engineered before you can.
The bigger money is in the intelligence market or 0days. A "browser-based" jailbreak is the same as a "browser-based" 0day. Intelligence organizations around the world, from China, to Europe, and most especially the NSA, have honed their tactics, techniques, and procedures around iPhone 0days. Terrorist leaders are like everyone else, blinging themselves out with status displays like iPhones. Also, iPhone is a lot more secure than Android, so it's actually a good decision (intelligence organizations have hacked Android even more).
Every time Apple comes out with a new version (like iOS9), they Continue reading
Featured Video: Orchestrating FortiGate Security with Cisco ACI Integration
 Fortinet-Cisco ACI integration uses SDN to reduce costs and improve service delivery in the cloud and in multitenant data centers.
Fortinet-Cisco ACI integration uses SDN to reduce costs and improve service delivery in the cloud and in multitenant data centers.
Some notes on NSA’s 0day handling process
The EFF got (via FOIA) the government's official policy on handling/buying 0days. I thought I'd write up some notes on this, based on my experience. The tl;dr version of this post is (1) the bits they redacted are the expected offensive use of 0days, and (2) there's nothing surprising in the redacted bits.Before 2008, you could sell 0days to the government many times, to different departments ranging from the NSA to Army to everybody else. These government orgs would compete against each other to see who had the biggest/best cyber-arsenal.
In 2008, there came an executive order to put a stop to all this nonsense. Vuln sellers now only sold 0days once to the government, and then the NSA would coordinate them with everyone else.
That's what this "VEP" (Vuln Equities Process) document discusses -- how the NSA distributes vulnerability information to all the other "stakeholders".
I use "stakeholders" loosely, because there are a lot of government organizations who feel entitled to being part of the 0day gravy train, but who really shouldn't be. I have the impression the NSA has two processes, the real one that is tightly focused on buying vulns and deploying them in the field, Continue reading
Alcatel-Lucent Buys Device Security Firm Mformation
 Unlucky in a 2012 BlackBerry lawsuit, Mformation has now been picked up by Alcatel-Lucent.
Unlucky in a 2012 BlackBerry lawsuit, Mformation has now been picked up by Alcatel-Lucent.