The Best and the Brightest Security and Privacy Experts Are Gathering Virtually at NDSS 2021

The 28th consecutive Network and Distributed System Security Symposium (NDSS 2021) kicks off today. NDSS is a premier academic research conference addressing a wide range of topics on network and system security. It’s an incubator for new, innovative ideas and research on the security and privacy of the Internet.
NDSS 2021, which takes place 21-25 February, will be one of the biggest NDSS symposia yet, featuring two keynotes, 90 peer-reviewed academic papers, six co-located workshops, and 19 posters focusing on vital and timely topics. All of this will happen virtually for the first time!
Here are some of the highlights.
Workshops
This year’s program officially started yesterday with three workshops on Sunday, 21 February. NDSS workshops are organized around a single topic and provide an opportunity for greater dialogue between researchers and practitioners in the area.
The Binary Analysis Research (BAR) Workshop returns for its fourth year at NDSS. Binary analysis refers to the process where humans and automated systems examine underlying code in software to discover, exploit, and defend against vulnerabilities. With the enormous and ever-increasing amount of software in the world today, formalized and automated methods of analysis are vital to improving security. This workshop will emphasize the Continue reading
Using HPKE to Encrypt Request Payloads
The Managed Rules team was recently given the task of allowing Enterprise users to debug Firewall Rules by viewing the part of a request that matched the rule. This makes it easier to determine what specific attacks a rule is stopping or why a request was a false positive, and what possible refinements of a rule could improve it.
The fundamental problem, though, was how to securely store this debugging data as it may contain sensitive data such as personally identifiable information from submissions, cookies, and other parts of the request. We needed to store this data in such a way that only the user who is allowed to access it can do so. Even Cloudflare shouldn't be able to see the data, following our philosophy that any personally identifiable information that passes through our network is a toxic asset.
This means we needed to encrypt the data in such a way that we can allow the user to decrypt it, but not Cloudflare. This means public key encryption.
Now we needed to decide on which encryption algorithm to use. We came up with some questions to help us evaluate which one to use:
- What requirements do we have for Continue reading
SEC 3. Building your own containerised PKI (root CA) with Linux and Docker to simplify and secure network automation
Hello my friend,
You know our passion to network automation. We truly believe, that this is the only sustainable way for the network development and operation. In the same time, one the key goals of the automation is to make your network secure and safe. Therefore, the security of the automation and communication channels used by automation is very important. So today we’ll take a look how to build
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Can automation make your network better?
Automation is the key component of the perpetual engine of your network development and operation. It allows you to run the network quick, stable, and safe. And we are willing you to benefit as much as you can from that.
We have created a new training, which is focused only on the Nornir and you can use it for the network (and not only) automation. It is an organic extension of our network automation training, which assumes you are already Continue reading
Industry-First Pay-as-you-go SaaS Platform for Kubernetes Security and Observability
We are excited to introduce Calico Cloud, a pay-as-you-go SaaS platform for Kubernetes security and observability. With Calico Cloud, users only pay for services consumed and are billed monthly, getting immediate value without upfront investment.
Introduction
Calico Cloud gives DevOps, DevSecOps, and Site Reliability Engineering (SRE) teams a single pane of glass across multi-cluster and multi-cloud Kubernetes environments to deploy a standard set of egress access controls, enforce security policies, ensure compliance, get end-to-end visibility, and troubleshoot applications. Calico Cloud is Kubernetes-native and provides native extensions to enable security and observability as code for easy and consistent enforcement across Kubernetes distributions, multi-cloud and hybrid environments. It scales automatically with the managed clusters according to the user requirements to ensure uninterrupted real-time visibility at any scale.
Security and Observability Challenges
- North-South Controls: Often microservices need to communicate with services or API endpoints running outside the Kubernetes cluster. Implementing access control from Kubernetes pods to external endpoints is hard. Most traditional or cloud provider’s firewalls do not understand the Kubernetes context which forces the ops team to allow traffic from the entire cluster or a set of worker nodes.
- East-West Controls: Even after effective perimeter-based north-south controls, the organizations face challenges to Continue reading
Worth Reading: Internet of Trash
I love the recent Internet of Trash article by Geoff Huston, in particular this bit:
“Move fast and break things” is not a tenable paradigm for this industry today, if it ever was. In the light of our experience with the outcomes of an industry that became fixated on pumping out minimally viable product, it’s a paradigm that heads towards what we would conventionally label as criminal negligence.
Of course it’s not just the Internet-of-Trash. Whole IT is filled with examples of startups and “venerable” companies doing the same thing and boasting about their disruptiveness. Now go and read the whole article ;)
Worth Reading: Internet of Trash
I love the recent Internet of Trash article by Geoff Huston, in particular this bit:
“Move fast and break things” is not a tenable paradigm for this industry today, if it ever was. In the light of our experience with the outcomes of an industry that became fixated on pumping out minimally viable product, it’s a paradigm that heads towards what we would conventionally label as criminal negligence.
Of course it’s not just the Internet-of-Trash. Whole IT is filled with examples of startups and “venerable” companies doing the same thing and boasting about their disruptiveness. Now go and read the whole article ;)
Meraki-CLI – Command Line Utility for the Meraki Dashboard
Meraki changed the industry years ago as one of the first platforms to use a cloud portal for all configuration; forgoing the typical local CLI/GUI administration of network appliances. One of the first things a traditional network engineer (like myself) may notice about Meraki equipment is their complete lack of a command-line interface. For the […]
The post Meraki-CLI – Command Line Utility for the Meraki Dashboard appeared first on Packet Pushers.
Kubernetes Observability Challenges: The Need for an AI-Driven Solution
Kubernetes provides abstraction and simplicity with a declarative model to program complex deployments. However, this abstraction and simplicity create complexity when debugging microservices in this abstract layer. The following four vectors make it challenging to troubleshoot microservices.
- The first vector is the Kubernetes microservices architecture, where tens to hundreds of microservices communicate. Debugging such a componentized application is challenging and requires specialized tools.
- The second vector is the distributed infrastructure spread across heterogeneous on-premises and cloud environments.
- The third vector of complexity is the dynamic nature of Kubernetes infrastructure. The platform spins up required resources and provides an ephemeral infrastructure environment to scale the application based on demand.
- Lastly, in such a distributed environment, Kubernetes deployments need fine-grained security and an observability model with defense-in-depth to keep them secure. While modern security controls effectively protect your workloads, they can have unintended consequences by preventing applications from running smoothly and creating an additional layer of complexity when debugging applications.
Today, DevOps and SRE teams must stitch together an enormous amount of data from multiple, disparate systems that monitor infrastructure and services layers in order to troubleshoot Kubernetes microservices issues. Not only is it overwhelming to stitch this data, but troubleshooting using Continue reading
Fence Rail Transposition and Caesar Ciphers in Python
Recently I wrote simple encryption and decryption programs in Python to practice my coding skills. The first cipher_encrypt utility takes the clear_text.txt file as input. It first capitalizes all letters and then encrypts the text with the Rail fence cipher. The number of rows can be set using the variable k. The result of the […]Continue reading...
Worth Reading: AAA Deep Dive on Cisco Devices
Decades ago I understood the intricacies of AAA on Cisco IOS. These days I wing it and keep throwing spaghetti at the virtual wall until something sticks and I can log in (after all, it’s all in a lab, and I’m interested in routing protocols not interactions with TACACS+ server).
If you’re experiencing similar challenges you might appreciate AAA Deep Dive on Cisco Devices by the one and only Daniel Dib.
Worth Reading: AAA Deep Dive on Cisco Devices
Decades ago I understood the intricacies of AAA on Cisco IOS. These days I wing it and keep throwing spaghetti at the virtual wall until something sticks and I can log in (after all, it’s all in a lab, and I’m interested in routing protocols not interactions with TACACS+ server).
If you’re experiencing similar challenges you might appreciate AAA Deep Dive on Cisco Devices by the one and only Daniel Dib.
Modernize Network Security With Palo Alto Networks Prisma Access
Prisma Access, from Palo Alto Networks, combines security and access capabilities including CASB, FWaaS, and Zero Trust into a single, cloud-delivered service. Prisma Access can help enterprises provide a secure, high-performance experience for their remote workforces.
The post Modernize Network Security With Palo Alto Networks Prisma Access appeared first on Packet Pushers.
Hedge #66: Tyler McDaniel and BGP Peer Locking
Tyler McDaniel joins Eyvonne, Tom, and Russ to discuss a study on BGP peerlocking, which is designed to prevent route leaks in the global Internet. From the study abstract:
Holistic web protection: industry recognition for a prolific 2020
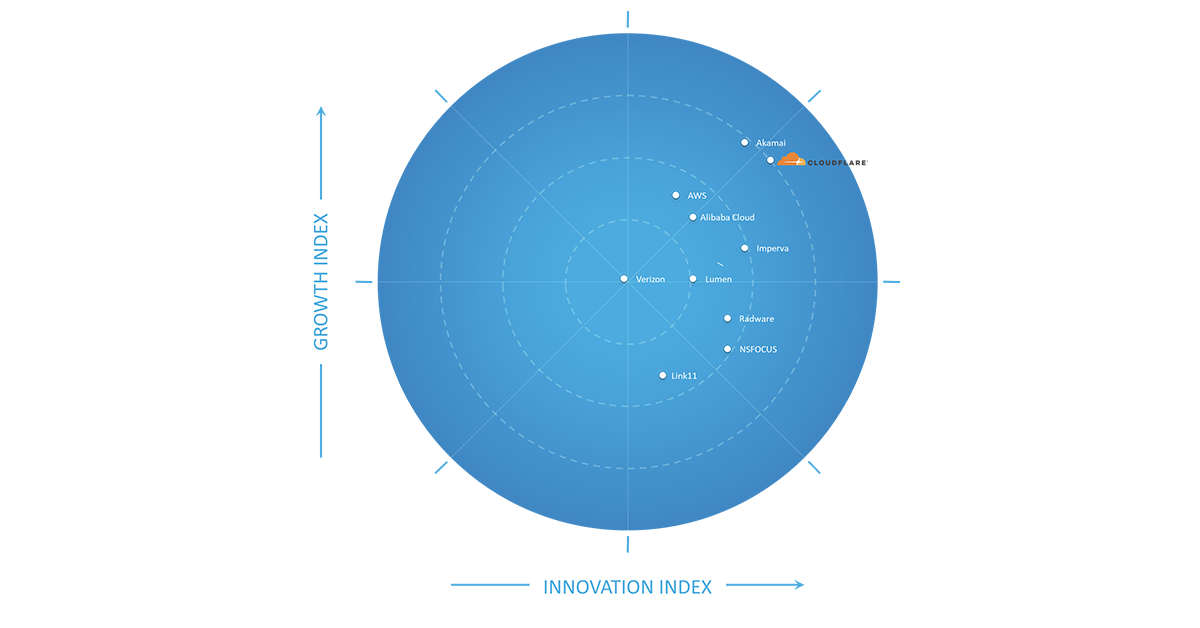
I love building products that solve real problems for our customers. These days I don’t get to do so as much directly with our Engineering teams. Instead, about half my time is spent with customers listening to and learning from their security challenges, while the other half of my time is spent with other Cloudflare Product Managers (PMs) helping them solve these customer challenges as simply and elegantly as possible. While I miss the deeply technical engineering discussions, I am proud to have the opportunity to look back every year on all that we’ve shipped across our application security teams.
Taking the time to reflect on what we’ve delivered also helps to reinforce my belief in the Cloudflare approach to shipping product: release early, stay close to customers for feedback, and iterate quickly to deliver incremental value. To borrow a term from the investment world, this approach brings the benefits of compounded returns to our customers: we put new products that solve real-world problems into their hands as quickly as possible, and then reinvest the proceeds of our shared learnings immediately back into the product.
It is these sustained investments that allow us to release a flurry of small improvements Continue reading