OMG, Not Again: New Mobile Internet Protocol Vulnerabilities
Every now and then a security researcher “discovers” a tunneling protocol designed to be used over a protected transport core and “declares it vulnerable” assuming the attacker can connect to that transport network… even though the protocol was purposefully designed that way, and everyone with a bit of clue knew the whole story years ago (and/or it’s even documented in the RFC).
It was MPLS decades ago, then VXLAN a few years ago, and now someone “found” a “high-impact vulnerability” in GPRS Tunnel Protocol. Recommended countermeasures: whitelist-based IP filtering. Yeah, it’s amazing what a wonderful new tool they found.
Unfortunately (for the rest of us), common sense never generated headlines on Hacker News (or anywhere else).
Announcing the Tigera – Nutanix Partnership
Today we are pleased to announce our partnership with Nutanix, creators of the industry’s most popular hyper-converged infrastructure (HCI) technology. HCI combines datacenter hardware using locally-attached storage resources with intelligent software to create flexible building blocks that replace legacy infrastructure consisting of separate servers, storage networks, and storage arrays.
Networking and securing microservices running Kubernetes and securely accessing external resources can be challenging, often requiring the use of overlay networks and NATs. At scale, this becomes extremely complex. Cloud-native enterprises seeking a consistent container networking experience across multiple cloud environments have adopted Calico, the de facto standard in open-source Kubernetes networking technologies.
Nutanix is now offering Calico as a component of Karbon, Nutanix’s enterprise Kubernetes management solution that enables turnkey provisioning, operations, and lifecycle management of Kubernetes. With this integration, Karbon users can now take advantage of simplified Kubernetes networking and production-grade network security based on Calico’s native tooling, providing scalable throughput that meets the performance demands of Karbon users.
“Karbon, now with Calico embedded, gives our customers significantly more powerful networking and network security capabilities while preserving the simplicity of provisioning and operating a Kubernetes cluster,” said Greg Muscarella, VP of Products at Nutanix. “Calico eliminates Continue reading
Phased Approach to Securing a Data Center
In the fight against relentless cyberattacks, organizations have long relied on traditional perimeter firewalls to protect sensitive workloads and information in the data center. But today, in the era of distributed applications and hybrid cloud environments, we know that perimeter defenses are not enough to stop cybercriminals.
To improve security postures inside corporate networks — which means protecting against both bad actors who penetrate perimeter defenses and malicious insiders — organizations must monitor, detect, and block hostile east-west (internal) traffic using internal firewalls.
To date, network and security professionals have generally viewed securing east-west traffic as too complex, expensive, and time-consuming for their brownfield, and even greenfield, data centers. At VMware, we agree with that perception: it’s certainly true for organizations trying to detect and prevent the lateral movement of attackers by employing traditional, appliance-based perimeter firewalls as internal firewalls.
There’s a Better Way to Secure the Data Center
Instead of awkwardly forcing appliance-based firewalls to serve as internal firewalls, organizations should employ a distributed, scale-out internal firewall specifically Continue reading
How CEOs think
CEO : "I read about that Twitter hack. Can that happen to us?"— Wim Remes (@wimremes) July 16, 2020
Security : "Yes, but ..."
CEO : "What products can we buy to prevent this?"
Security : "But ..."
CEO : "Let's call Gartner."
*sobbing sounds*
flowtrackd: DDoS Protection with Unidirectional TCP Flow Tracking


Magic Transit is Cloudflare’s L3 DDoS Scrubbing service for protecting network infrastructure. As part of our ongoing investment in Magic Transit and our DDoS protection capabilities, we’re excited to talk about a new piece of software helping to protect Magic Transit customers: flowtrackd. flowrackd is a software-defined DDoS protection system that significantly improves our ability to automatically detect and mitigate even the most complex TCP-based DDoS attacks. If you are a Magic Transit customer, this feature will be enabled by default at no additional cost on July 29, 2020.

TCP-Based DDoS Attacks
In the first quarter of 2020, one out of every two L3/4 DDoS attacks Cloudflare mitigated was an ACK Flood, and over 66% of all L3/4 attacks were TCP based. Most types of DDoS attacks can be mitigated by finding unique characteristics that are present in all attack packets and using that to distinguish ‘good’ packets from the ‘bad’ ones. This is called "stateless" mitigation, because any packet that has these unique characteristics can simply be dropped without remembering any information (or "state") about the other packets that came before it. However, when attack packets have no unique characteristics, then "stateful" mitigation is required, because whether a Continue reading
In defense of open debate
The Letter said that the norms of liberalism tolerate disagreement, and that these norms are under attack by increasing illiberalism on both sides, both the left and the right.
My point is this: Masnick avoids the rebutting the letter. He's recycling his arguments against right-wingers who want their speech coddled, rather than the addressing the concerns of (mostly) left-wingers worried about the fanaticism on their own side.
Masnick mentions "free speech" 19 times in his rebuttal -- but the term does not appear in the Harper's letter, not even once. This demonstrates my thesis that his rebuttal misses the point.
The term "free speech" has lost its meaning. It's no longer useful for such conversations.
Left-wingers want media sites like Facebook, YouTube, the New York Times to remove "bad" speech, like right-wing "misinformation". But, as we've been taught, censoring speech is bad. Therefore, "censoring free speech" has to be redefined to as to not Continue reading
Zero Trust and the Cookie Metaphor
In old presentations on network security (watch this space; I’m working on a new security course for Ignition in the next six months or so), I would use a pair of chocolate chip cookies as an illustration for network security. In the old days, I’d opine, network security was like a cookie that was baked to be crunchy on the outside and gooey on the inside. Now-a-days, however, I’d say network security needs to be more like a store-bought cookie—crunchy all the way through. I always used this illustration to make a point about defense-in-depth. You cannot assume the thin crunchy security layer at the edge of your network—generally in the form of stateful packet filters and the like (okay, firewalls, but let’s leave the appliance world behind for a moment)—is what you really need.
There are such things as insider attacks, after all. Further, once someone breaks through the thin crunchy layer at the edge, you really don’t want them being able to move laterally through your network.
The United States National Institute of Standards and Technology (NIST) has released a draft paper describing Zero Trust Architecture, which addresses many of the same concerns as the cookie that’s crunchy Continue reading
From Micro-segmentation to Internal Firewalling
The Evolution of VMware NSX Service-defined Firewall
Today, many people take micro-segmentation for granted. It’s incredible to recall that just a few years ago, VMware introduced micro-segmentation to support the concept of Zero Trust — a security model that does not automatically trust entities within the security perimeter. Fast forward to the present, and many people have embraced that concept and made it their own. Meanwhile, VMware has extended its solution for micro-segmentation into a full-blown internal firewall. Let’s step back in time and see how VMware progressed from the initial micro-segmentation use case to today’s powerful Service-defined Firewall, deployed by thousands of organizations.
Pioneering the Market for Micro-segmentation
Back in 2013, VMware pioneered micro-segmentation with the release of VMware NSX, the VMware network virtualization and security platform, which propelled VMware into the world of software-defined network and security virtualization. This initial release enabled customers to run a complete Layer 2-Layer 4 stack in software. The guiding philosophy was to make world-class security easy to operationalize.
Some customers used NSX for network segmentation: they created virtual security zones in software where they had previously used hardware. Other customers adopted NSX for micro-segmentation: they were now able to provide Continue reading
No Humans Involved: Mitigating a 754 Million PPS DDoS Attack Automatically


On June 21, Cloudflare automatically mitigated a highly volumetric DDoS attack that peaked at 754 million packets per second. The attack was part of an organized four day campaign starting on June 18 and ending on June 21: attack traffic was sent from over 316,000 IP addresses towards a single Cloudflare IP address that was mostly used for websites on our Free plan. No downtime or service degradation was reported during the attack, and no charges accrued to customers due to our unmetered mitigation guarantee.
The attack was detected and handled automatically by Gatebot, our global DDoS detection and mitigation system without any manual intervention by our teams. Notably, because our automated systems were able to mitigate the attack without issue, no alerts or pages were sent to our on-call teams and no humans were involved at all.

During those four days, the attack utilized a combination of three attack vectors over the TCP protocol: SYN floods, ACK floods and SYN-ACK floods. The attack campaign sustained for multiple hours at rates exceeding 400-600 million packets per second Continue reading
The Hedge Pdocast Episode 43: Ivan Pepelnjak and Trusting Routing Protocols
Can you really trust what a routing protocol tells you about how to reach a given destination? Ivan Pepelnjak joins Nick Russo and Russ White to provide a longer version of the tempting one-word answer: no! Join us as we discuss a wide range of issues including third-party next-hops, BGP communities, and the RPKI.
Sandboxing in Linux with zero lines of code
Modern Linux operating systems provide many tools to run code more securely. There are namespaces (the basic building blocks for containers), Linux Security Modules, Integrity Measurement Architecture etc.
In this post we will review Linux seccomp and learn how to sandbox any (even a proprietary) application without writing a single line of code.
Tux by Iwan Gabovitch, GPL
Sandbox, Simplified Pixabay License
Linux system calls
System calls (syscalls) is a well-defined interface between userspace applications and the operating system (OS) kernel. On modern operating systems most applications provide only application-specific logic as code. Applications do not, and most of the time cannot, directly access low-level hardware or networking, when they need to store data or send something over the wire. Instead they use system calls to ask the OS kernel to do specific hardware and networking tasks on their behalf:
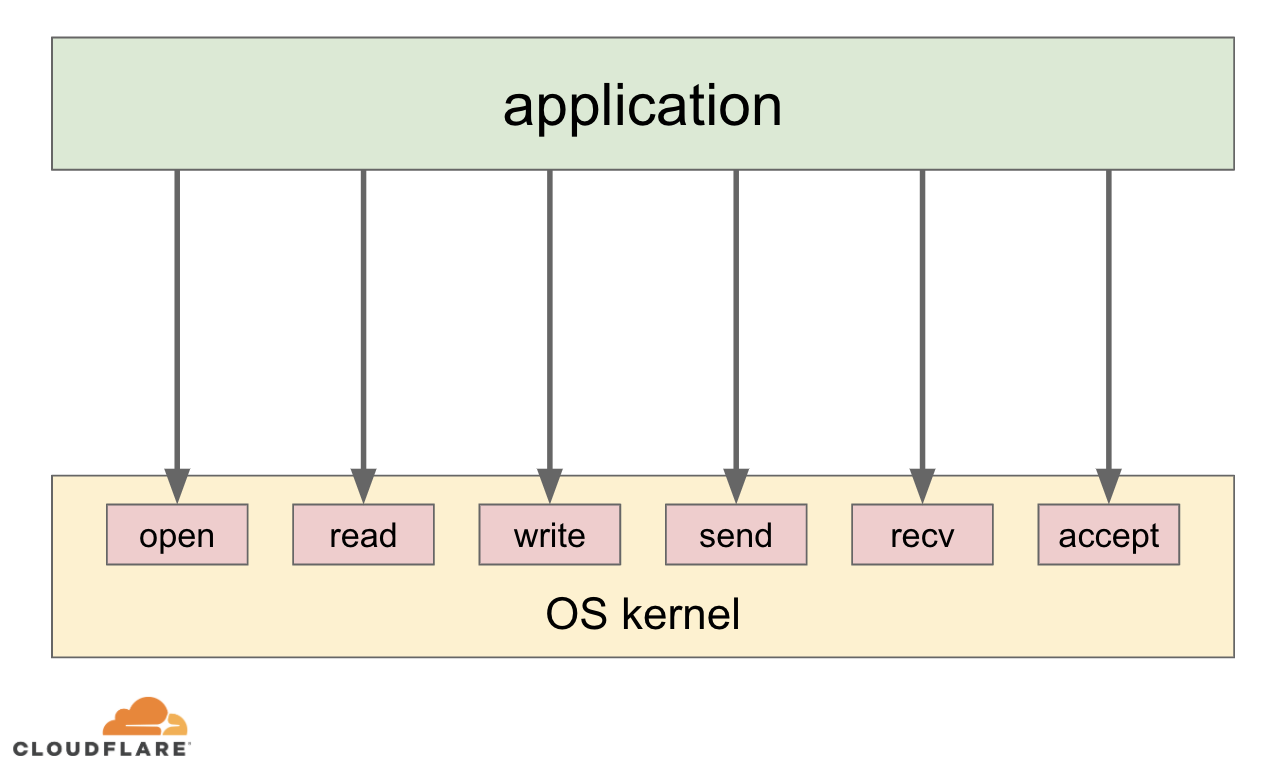
Apart from providing a generic high level way for applications to interact with the low level hardware, the system call architecture allows the OS kernel to manage available resources between applications as well as enforce policies, like application permissions, networking access control lists etc.
Linux seccomp
Linux seccomp is yet another syscall on Linux, but it is a bit Continue reading
CVE-2020-5902: Helping to protect against the F5 TMUI RCE vulnerability
Cloudflare has deployed a new managed rule protecting customers against a remote code execution vulnerability that has been found in F5 BIG-IP’s web-based Traffic Management User Interface (TMUI). Any customer who has access to the Cloudflare Web Application Firewall (WAF) is automatically protected by the new rule (100315) that has a default action of BLOCK.
Initial testing on our network has shown that attackers started probing and trying to exploit this vulnerability starting on July 3.
F5 has published detailed instructions on how to patch affected devices, how to detect if attempts have been made to exploit the vulnerability on a device and instructions on how to add a custom mitigation. If you have an F5 device, read their detailed mitigations before reading the rest of this blog post.
The most popular probe URL appears to be /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp followed by /tmui/login.jsp/..;/tmui/util/getTabSet.jsp, /tmui/login.jsp/..;/tmui/system/user/authproperties.jsp and /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp. All contain the critical pattern ..; which is at the heart of the vulnerability.
On July 3 we saw O(1k) probes ramping to O(1m) yesterday. This is because simple test patterns have been added to scanning tools and small test programs made available by Continue reading
NSX Secures Physical Servers with Bare Metal Agents
Our last blog on how NSX secures physical servers provided background on why physical server security is crucial. We cover the percentage share of physical servers to all workloads in the data center and the specific roles physical servers still play. Today, physical servers by percentage are playing a decreasing role in the data center. However, it’s still a vital one, as we pointed out in our last blog on Securing Physical Servers with NSX Service-defined Firewall. In this blog, we will cover a primary way VMware NSX provides secure connectivity for physical servers using a bare metal agent. VMware NSX-T can now offer secure connectivity for Linux and Windows Server physical servers.
How NSX Distributed Firewall Protects Physical Servers
There are several ways in which NSX can provide security for physical servers. Our original article, Extending the Power of NSX to Bare Metal, outlines each of these methods.
- NSX Distributed Firewall (DFW) ingress rules for traffic from physical servers to virtual workloads
- NSX DFW egress rules for traffic from virtual workloads to physical servers
- The NSX Edge using centralized firewall rules to secure traffic between virtual and physical workloads
- Use NSX agents in Physical Servers

VMware NSX Continue reading
The Hedge Podcast Episode 42: Andrei Robachevsky and MANRS
The security of the global routing table is foundational to the security of the overall Internet as an ecosystem—if routing cannot be trusted, then everything that relies on routing is suspect, as well. Mutually Agreed Norms for Routing Security (MANRS) is a project of the Internet Society designed to draw network operators of all kinds into thinking about, and doing something about, the security of the global routing table by using common-sense filtering and observation. Andrei Robachevsky joins Russ White and Tom Ammon to talk about MANRS.
How to test HTTP/3 and QUIC with Firefox Nightly


HTTP/3 is the third major version of the Hypertext Transfer Protocol, which takes the bold step of moving away from TCP to the new transport protocol QUIC in order to provide performance and security improvements.
During Cloudflare's Birthday Week 2019, we were delighted to announce that we had enabled QUIC and HTTP/3 support on the Cloudflare edge network. This was joined by support from Google Chrome and Mozilla Firefox, two of the leading browser vendors and partners in our effort to make the web faster and more reliable for all. A big part of developing new standards is interoperability, which typically means different people analysing, implementing and testing a written specification in order to prove that it is precise, unambiguous, and actually implementable.
At the time of our announcement, Chrome Canary had experimental HTTP/3 support and we were eagerly awaiting a release of Firefox Nightly. Now that Firefox supports HTTP/3 we thought we'd share some instructions to help you enable and test it yourselves.
How do I enable HTTP/3 for my domain?
Simply go to the Cloudflare dashboard and flip the switch from the "Network" tab manually:
Using Firefox Nightly as an HTTP/3 client
Firefox Nightly has experimental support for Continue reading
Cryptojackers Target Docker Containers for Monero Mining
Palo Alto Networks and Aqua Security researchers say cryptojackers are inserting malicious images...
Huawei Cops To Lack of US Ambition
“We don’t necessarily have any ambition in the U.S. market just because this is such a...
VMware Tanzu Mission Control Gains Data Protection
The feature allows for central management of data protection of Kubernetes clusters running across...
VMware NSX-T Service Insertion and Gigamon GigaVUE Cloud Suite
We are delighted that our valued partner, Gigamon, and it’s GigaVUE Cloud Suite has met the certification requirements for VMware NSX-T service insertion.
Service Insertion for NSX-T
The concept of service insertion is key for the NSX platform, enabling users to seamlessly add third party applications at various points throughout the network. Having a robust ecosystem of partners provides maximum flexibility for NSX-T, allowing customers to add partner functionality, tailored to their unique requirements without degrading performance elsewhere in the software-defined data center (SDDC). Partner applications are put through a rigorous certification process ensuring the highest level of interoperability and reliability.
With the certification, GigaVUE Cloud Suite is now interoperable with VMware’s NSX-T and vCenter Server through APIs for improved agility and reduced manual management tasks. Gigamon customers now have comprehensive application visibility across complex hybrid environments, including east-west traffic, at scale.

Learn more
Please join the VMware and Gigamon teams at a joint webinar, Illuminate Applications in VMware-based Clouds to Secure and Optimize, on June 30, 10 am PDT. Learn about NSX service insertion, Gigamon GigaVue, and the advantages and a demo of Gigamon next-generation network visibility solutions.
The post VMware NSX-T Service Insertion and Gigamon GigaVUE Continue reading
Research: Off-Path TCP Attacks
I’s fnny, bt yu cn prbbly rd ths evn thgh evry wrd s mssng t lst ne lttr. This is because every effective language—or rather every communication system—carried enough information to reconstruct the original meaning even when bits are dropped. Over-the-wire protocols, like TCP, are no different—the protocol must carry enough information about the conversation (flow data) and the data being carried (metadata) to understand when something is wrong and error out or ask for a retransmission. These things, however, are a form of data exhaust; much like you can infer the tone, direction, and sometimes even the content of conversation just by watching the expressions, actions, and occasional word spoken by one of the participants, you can sometimes infer a lot about a conversation between two applications by looking at the amount and timing of data crossing the wire.
The paper under review today, Off-Path TCP Exploit, uses cleverly designed streams of packets and observations about the timing of packets in a TCP stream to construct an off-path TCP injection attack on wireless networks. Understanding the attack requires understanding the interaction between the collision avoidance used in wireless systems and TCP’s reaction to packets with a sequence number outside Continue reading