NacXwan Taps Lanner for SD-WAN Hardware
The agreement pairs Lanner's universal CPE hardware with nacXwan’s SD-WAN software stack to...
How To Use 1.1.1.1 w/ WARP App And Cloudflare Gateway To Protect Your Phone From Security Threats
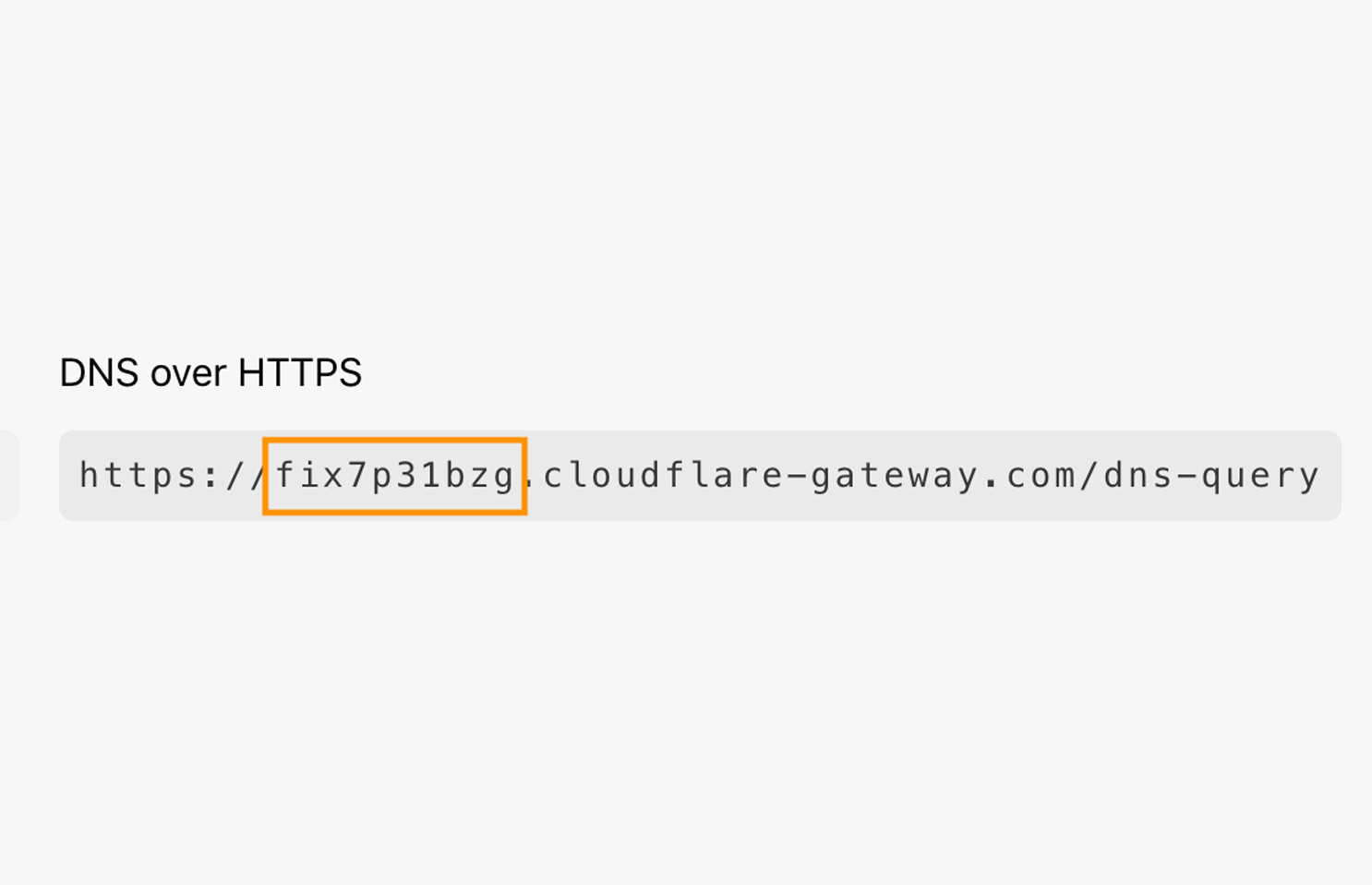
Cloudflare Gateway protects users and devices from security threats. You can now use Gateway inside the 1.1.1.1 w/ WARP app to secure your phone from malware, phishing and other security threats.
The 1.1.1.1 w/ WARP app has secured millions of mobile Internet connections. When installed, 1.1.1.1 w/ WARP encrypts the traffic leaving your device, giving you a more private browsing experience.
Starting today, you can get even more out of your 1.1.1.1 w/ WARP. By adding Cloudflare Gateway’s secure DNS filtering to the app, you can add a layer of security and block malicious domains flagged as phishing, command and control, or spam. This protection isn’t dependent on what network you’re connected to - it follows you everywhere you go.
You can read more about how Cloudflare Gateway builds on our 1.1.1.1 resolver to secure Internet connections in our announcement. Ready to get started bringing that security to your mobile device? Follow the steps below.
Download the 1.1.1.1 w/ WARP mobile app
If you don’t have the latest version of the 1.1.1.1 w/ WARP app go to the Apple Continue reading
Why use Typha in your Calico Kubernetes Deployments?
Calico is an open source networking and network security solution for containers, virtual machines, and native host-based workloads. Calico supports a broad range of platforms including Kubernetes, OpenShift, Docker EE, OpenStack, and bare metal. In this blog, we will focus on Kubernetes pod networking and network security using Calico.
Calico uses etcd as the back-end datastore. When you run Calico on Kubernetes, you can use the same etcd datastore through the Kubernetes API server. This is called a Kubernetes backed datastore (KDD) in Calico. The following diagram shows a block-level architecture of Calico.

Calico-node runs as a Daemonset, and has a fair amount of interaction with the Kubernetes API server. It’s easy for you to profile that by simply enabling audit logs for calico-node. For example, in my kubeadm cluster, I used the following audit configuration





If you ignore the license key API calls from calico-node, you will see that the API calls Continue reading
Versa Targets SMBs, Pens SD-WAN Deal With Nuvias
Versa Titan promises to simplify the deployment and management of branch offices and make it easier...
Will the Pandemic Propel DevSecOps? Snyk Says Yes
This is also a great time to start a bug bounty program, says Guy Podjarny, founder and president...
Daily Roundup: Cisco Buys Backhaul Vendor
Cisco secured a deal to buy Fluidmesh Networks; IBM CEO threw down a hybrid-cloud challenge; and DT...
How to Easily Secure Virtual Desktops for your Remote Employees
The COVID-19 pandemic has forced many organizations to shift their business online and their employees to work from home. As a result, business had to quickly adjust and scale up their infrastructure, sometimes with security as an afterthought.
Malicious actors are already taking advantage of this new reality by targeting the vulnerabilities commonly associated with employees connecting to corporate resources from their home environment. This includes social engineering and phishing campaigns, denial of service attacks, and exploiting vulnerabilities in home routers.
Secure VDI Environments with NSX
Providing employees working from home with secure and reliable access to their corporate resources and applications by the use of Virtual Desktop Infrastructure (VDI) helps our customers to reduce the impact on productivity and continuity as well as the risk associated with remote access to internal data.
In this blog post, I will cover a couple of use cases on how NSX can provide security for End User Compute and share some resources to help customers who are scaling up their VDI / remote desktop session host (RDSH) infrastructure to adapt to this new world in which vast numbers of employees are now working from home.
Protect Your Desktop Pools
The initial target of Continue reading
Versa CMO Stakes Claim in Competitive SD-WAN Market
Wood is no stranger to the SD-WAN market. He joined Versa’s executive team in February after a...
VMware: What to Do When Cybercriminals Hunt Your Company in Your Home
The worse-case scenario is “whether your entire brand will be used to attack your customers,”...
Weekly Wrap: Palo Alto Folds CloudGenix in $420M SASE Play
SDxCentral Weekly Wrap for April 3, 2020: CloudGenix had been targeting Cisco in the SD-WAN space;...
Do Coronavirus SOCs Look Like Zoom War Rooms?
When an incident occurs, enterprises typically rely on their on-site security operations centers to...
MUST READ: Using BGP RPKI for a Safer Internet
As I explained in How Networks Really Work and Upcoming Internet Challenges webinars, routing security, and BGP security in particular remain one of the unsolved challenges we’ve been facing for decades (see also: what makes BGP a hot mess).
Fortunately, due to enormous efforts of a few persistent individuals BGP RPKI is getting traction (NTT just went all-in), and Flavio Luciani and Tiziano Tofoni decided to do their part creating an excellent in-depth document describing BGP RPKI theory and configuration on Cisco- and Juniper routers.
There are only two things you have to do:
- Read the document;
- Implement RPKI in your network.
Thank you, the Internet will be grateful.
About them Zoom vulns…
Today a couple vulnerabilities were announced in Zoom, the popular work-from-home conferencing app. Hackers can possibly exploit these to do evil things to you, such as steal your password. Because of the COVID-19, these vulns have hit the mainstream media. This means my non-techy friends and relatives have been asking about it. I thought I'd write up a blogpost answering their questions.The short answer is that you don't need to worry about it. Unless you do bad things, like using the same password everywhere, it's unlikely to affect you. You should worry more about wearing pants on your Zoom video conferences in case you forget and stand up.
Now is a good time to remind people to stop using the same password everywhere and to visit https://haveibeenpwned.com to view all the accounts where they've had their password stolen. Using the same password everywhere is the #1 vulnerability the average person is exposed to, and is a possible problem here. For critical accounts (Windows login, bank, email), use a different password for each. (Sure, for accounts you don't care about, use the same password everywhere, I use 'Foobar1234'). Write these passwords down on paper and put that paper in Continue reading
SDxCentral’s Top 10 Articles — March 2020
Cisco Networking lessons learned during COVID-19; AT&T slashed more jobs; Microsoft topped...
Announcing the Beta for WARP for macOS and Windows


Last April 1 we announced WARP — an option within the 1.1.1.1 iOS and Android app to secure and speed up Internet connections. Today, millions of users have secured their mobile Internet connections with WARP.
While WARP started as an option within the 1.1.1.1 app, it's really a technology that can benefit any device connected to the Internet. In fact, one of the most common requests we've gotten over the last year is support for WARP for macOS and Windows. Today we're announcing exactly that: the start of the WARP beta for macOS and Windows.
What's The Same: Fast, Secure, and Free
We always wanted to build a WARP client for macOS and Windows. We started with mobile because it was the hardest challenge. And it turned out to be a lot harder than we anticipated. While we announced the beta of 1.1.1.1 with WARP on April 1, 2019 it took us until late September before we were able to open it up to general availability. We don't expect the wait for macOS and Windows WARP to be nearly as long.
The WARP client for macOS and Windows relies on the Continue reading
Introducing 1.1.1.1 for Families

Two years ago today we announced 1.1.1.1, a secure, fast, privacy-first DNS resolver free for anyone to use. In those two years, 1.1.1.1 has grown beyond our wildest imagination. Today, we process more than 200 billion DNS requests per day making us the second largest public DNS resolver in the world behind only Google.

Yesterday, we announced the results of the 1.1.1.1 privacy examination. Cloudflare's business has never involved selling user data or targeted advertising, so it was easy for us to commit to strong privacy protections for 1.1.1.1. We've also led the way supporting encrypted DNS technologies including DNS over TLS and DNS over HTTPS. It is long past time to stop transmitting DNS in plaintext and we're excited that we see more and more encrypted DNS traffic every day.
1.1.1.1 for Families

Since launching 1.1.1.1, the number one request we have received is to provide a version of the product that automatically filters out bad sites. While 1.1.1.1 can safeguard user privacy and optimize efficiency, it is designed for direct, fast DNS resolution, not for blocking or Continue reading
Cloudflare now supports security keys with Web Authentication (WebAuthn)!


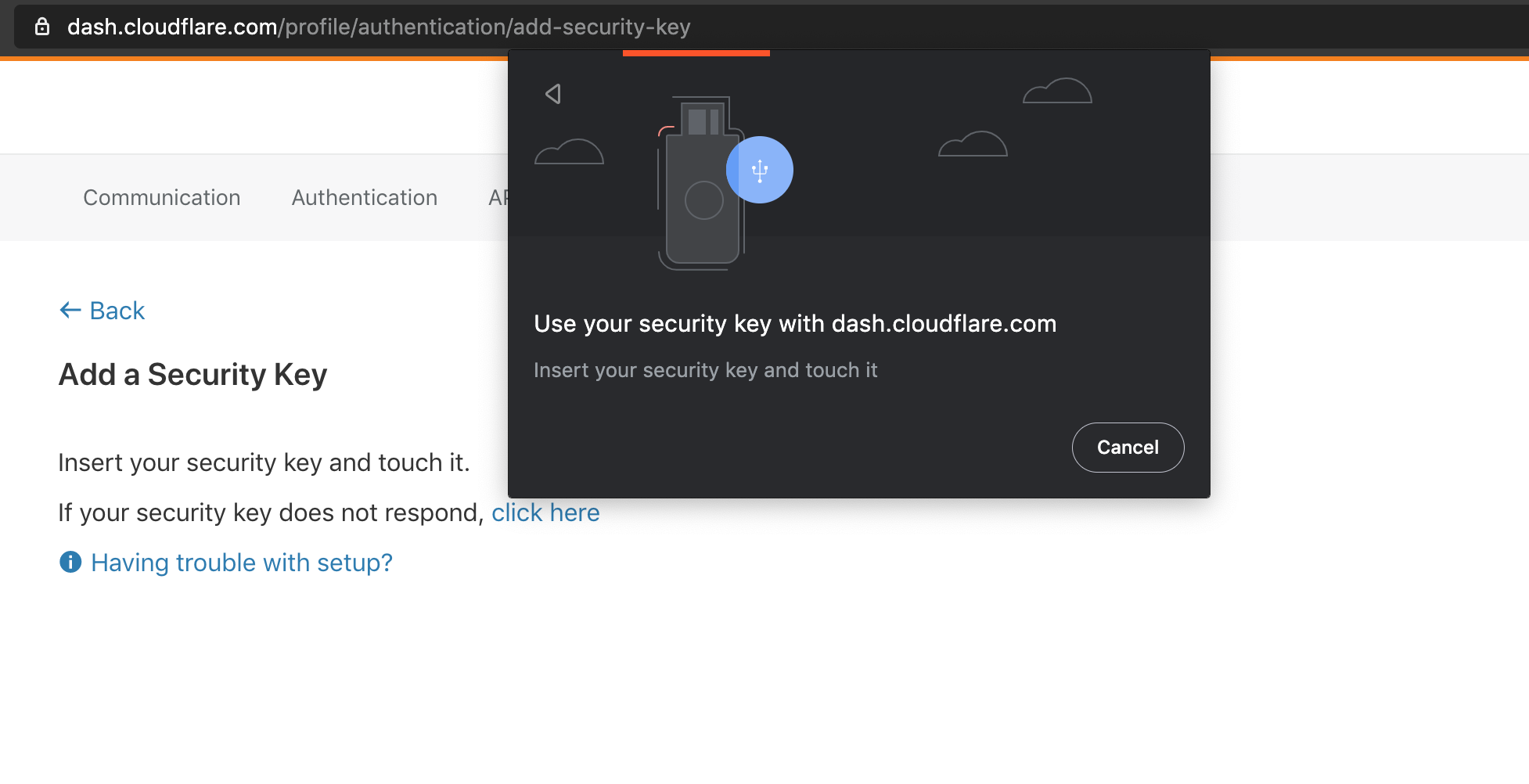
We’re excited to announce that Cloudflare now supports security keys as a two factor authentication (2FA) method for all users. Cloudflare customers now have the ability to use security keys on WebAuthn-supported browsers to log into their user accounts. We strongly suggest users configure multiple security keys and 2FA methods on their account in order to access their apps from various devices and browsers. If you want to get started with security keys, visit your account's 2FA settings.
What is WebAuthn?
WebAuthn is a standardized protocol for authentication online using public key cryptography. It is part of the FIDO2 Project and is backwards compatible with FIDO U2F. Depending on your device and browser, you can use hardware security keys (like YubiKeys) or built-in biometric support (like Apple Touch ID) to authenticate to your Cloudflare user account as a second factor. WebAuthn support is rapidly increasing among browsers and devices, and we’re proud to join the growing list of services that offer this feature.
To use WebAuthn, a user registers their security key, or “authenticator”, to a supporting application, or “relying party” (in this case Cloudflare). The authenticator then generates and securely stores a public/private keypair on the device. The keypair Continue reading
CybersecurityCares Lists Free Tools During Coronavirus
It all started with a blog post by Axonius’ Nathan Burke: Things will be weird in cybersecurity...
Palo Alto Folds CloudGenix in $420M SASE Play
CloudGenix will form the second pillar of Palo Alto's emerging secure access service edge offering,...