Fortinet Wins an SD-WAN Whopper
Also, CMC, Neutrona combine their SD-WAN resources; and Criterion Networks launches an SD-WAN...
ExtraHop CEO: We’ve Doubling Down on Cloud
Looking ahead to 2020, “our top priority is becoming the unquestioned leader" in cloud-based...
Weekly Wrap: Arista Networks Buys Big Switch
SDxCentral Weekly Wrap for Jan. 24, 2020: Big Switch will bolster Arista's enterprise play; IBM...
250M Microsoft Customer Records Exposed; Cisco Prescribes Patches
In the past three weeks, Microsoft, Cisco, Oracle, and Citrix have announced a slew of...
Daily Roundup: VMware Buys Nyansa
VMware bought AIOps vendor Nyansa; Red Hat was integral to IBM's Q4 success; and Vapor IO scored...
US Pledges $1B to Roast Huawei With Open RAN 5G
The proposed funding pales in comparison to the amount of money Huawei and other RAN stalwarts are...
Managing Financial Network Threats with SD-Branch
Financial networks are at a constant risk — especially since they rely on risky IoT devices....
Arista Networks Buys Big Switch
Several incumbent networking players, including Cisco, Dell Technologies, VMware, Juniper Networks,...
Verizon Exec Launches Privafy, Challenges Firewall, SD-WAN, VPN Vendors
The security startup has about a dozen paying customers and is “working with some of the largest...
5G and Me: And Security
In today’s uber-connected world, everyone has dealt with that little voice in the back of the...
Daily Roundup: Cisco Advances Intent-Based Networking
Cisco advanced intent-based networking; SK boasted standalone 5G first; and Citrix swatted ADC,...
Snyk Secures $150M, Snags $1B Valuation
The open source security startup reported over 400% revenue growth in 2019 and says its customers...
Telefónica Scores SD-WAN, Security Deal With Arlanxeo
The five-year contract will span more than 20 production sites in 11 countries across four...
Deep Dive: Scoring ISPs and Hosts on Privacy and Security

In April 2019 the Internet Society’s Online Trust Alliance (OTA) released its 10th Annual Online Trust Audit & Honor Roll. The Audit looks at the security and privacy practices of over 1,000 of the top sites on the Internet from retailers to governments. In this post we will take a deeper dive into the ISP/Hosts sector of the Audit. This sector is comprised of the top ISPs and other hosting organizations in the U.S. It includes everything from organizations that provide network access to organizations that host email services.
In the Audit, privacy statements are scored across 30 variables. ISP/Hosts were a decidedly mixed bag compared to other sectors, which tended to do either relatively well or poorly across the board in their statements. (Though to clear, the vast majority of organizations in the Audit had poor privacy statements, it was the most common reason for failure across privacy and security scoring.)
ISP/Hosts fell somewhat short in the presentation of their statements. OTA advocates several best practices that deal with how the privacy statement is displayed to make it as easy as possible for users to understand.
The simplest practice OTA advocates is a link to the privacy Continue reading
Citrix Swats ADC, Gateway Bugs, SD-WAN Fix in the Wings
“We urge customers to immediately install these fixes,” noted Citrix Chief Information Security...
IBM Secures $1.1B Contract With Banco Sabadell
The contract calls for IBM to simplify the bank's dispersed IT infrastructure and improve customer...
Oracle Fixes 334 Bugs in Record-Breaking Critical Patch Update
Almost 40 vulnerabilities with a 9.8 severity rating can be exploited over a network without...
Weekly Wrap: Nokia Cuts 180 Jobs With More to Come
SDxCentral Weekly Wrap for Jan. 17, 2020: 5G competition has been rough on Nokia; Citrix promises a...
McAfee Hires New CEO, Mulls Sale or IPO
“If they hired Peter Leav they are setting up to sell,” said analyst Zeus Kerravala.
Announcing the Cloudflare Access App Launch

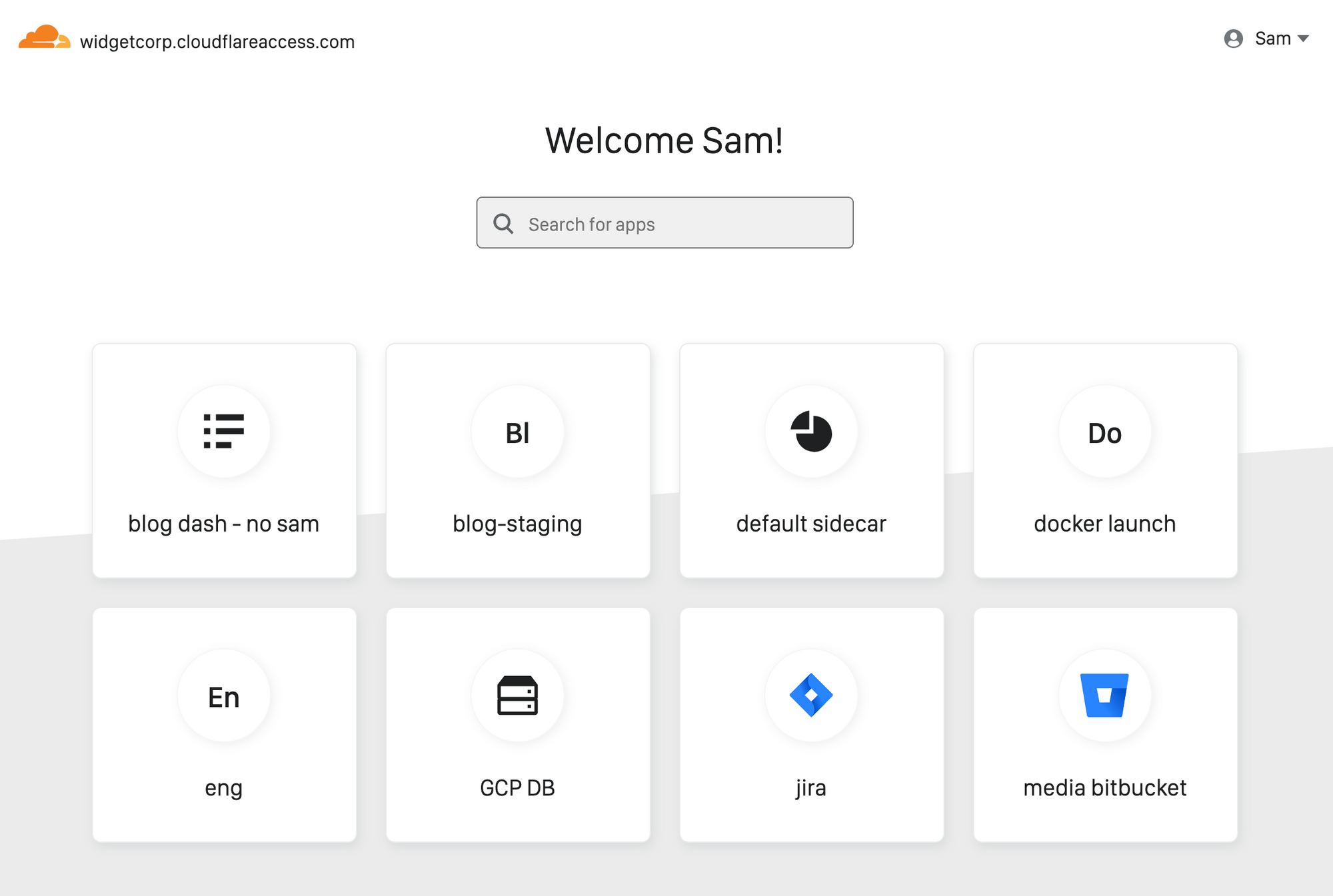
Every person joining your team has the same question on Day One: how do I find and connect to the applications I need to do my job?
Since launch, Cloudflare Access has helped improve how users connect to those applications. When you protect an application with Access, users never have to connect to a private network and never have to deal with a clunky VPN client. Instead, they reach on-premise apps as if they were SaaS tools. Behind the scenes, Access evaluates and logs every request to those apps for identity, giving administrators more visibility and security than a traditional VPN.
Administrators need about an hour to deploy Access. End user logins take about 20 ms, and that response time is consistent globally. Unlike VPN appliances, Access runs in every data center in Cloudflare’s network in 200 cities around the world. When Access works well, it should be easy for administrators and invisible to the end user.
However, users still need to locate the applications behind Access, and for internally managed applications, traditional dashboards require constant upkeep. As organizations grow, that roster of links keeps expanding. Department leads and IT administrators can create and publish manual lists, but those become Continue reading