VMware Adds Load Balancer, Analytics Engine to NSX
VMware rolled out updates to its NSX networking platform including a new analytics engine and load...
Rackspace Targets Hybrid-Cloud Adoption With New Services
Rackspace rolled out five new enhancements to its hybrid cloud portfolio aimed at helping customers...
Mellanox Reveals SmartNICs With 200 Gb/s Connectivity
Mellanox today introduced a pair of SmartNICs for data center servers and storage systems at...
IBM Drives Quantum-Safe Cryptography Into Its Public Cloud
IBM predicts that due to the rate of progress in quantum computing data protected by current...
VMware Buys Carbon Black for $2.1B and Pivotal for $2.7B
VMware said it will buy Pivotal in a deal valued at $2.7 billion and security company Carbon Black...
Supercharging Firewall Events for Self-Serve
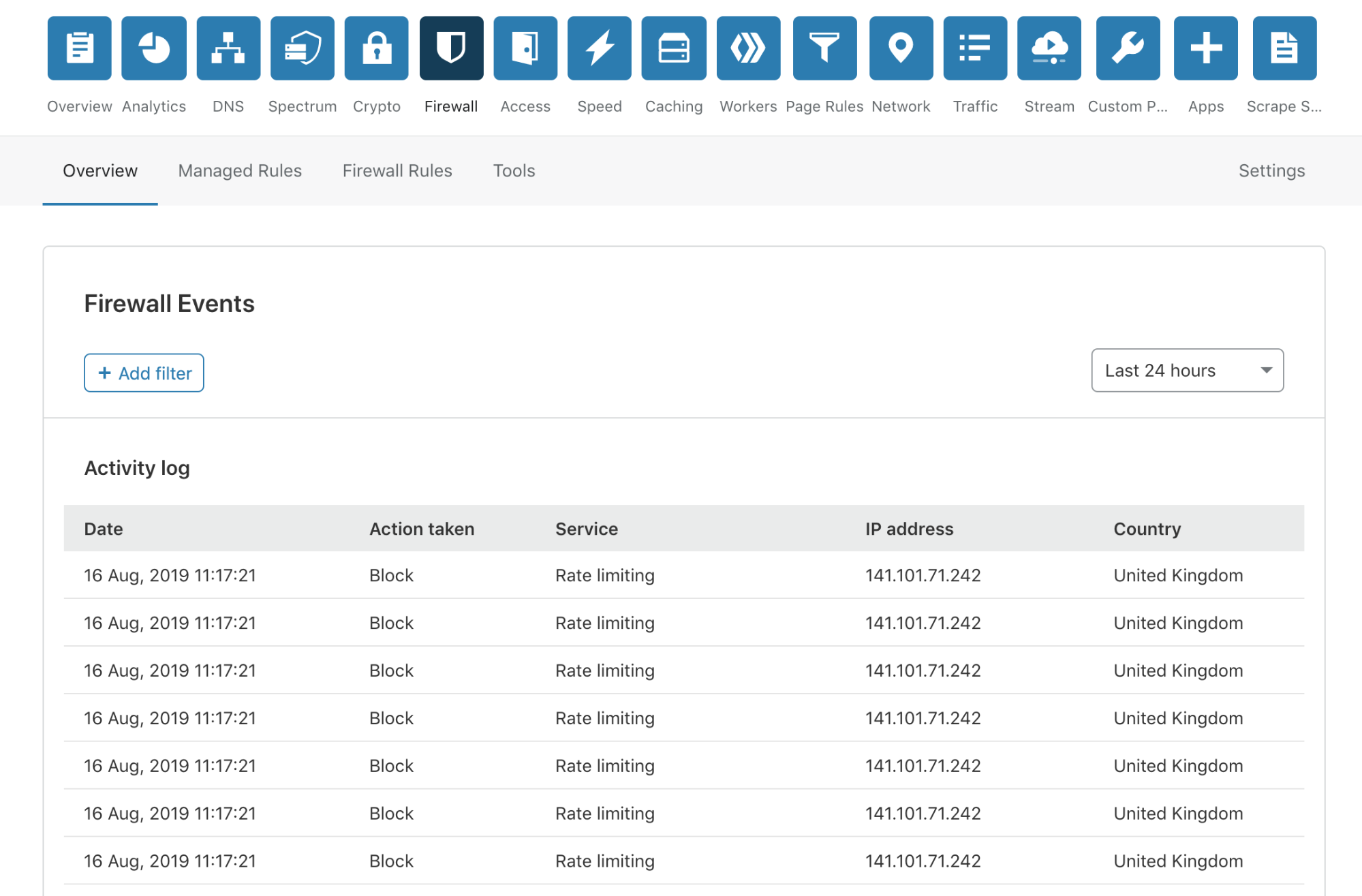
Today, I’m very pleased to announce the release of a completely overhauled version of our Firewall Event log to our Free, Pro and Business customers. This new Firewall Events log is now available in your Dashboard, and you are not required to do anything to receive this new capability.
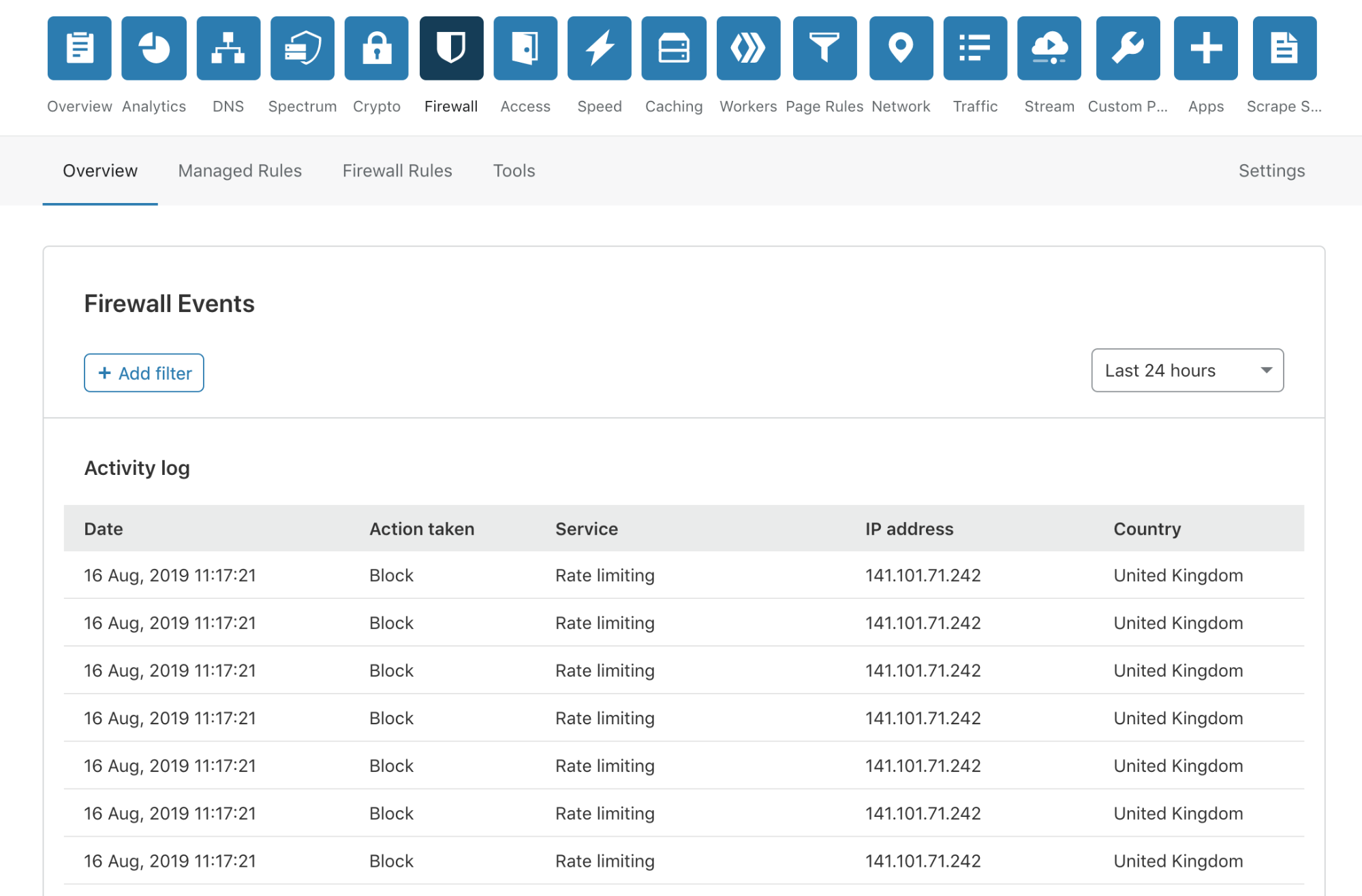
No more modals!
We have done away with those pesky modals, providing a much smoother user experience. To review more detailed information about an event, you simply click anywhere on the event list row.
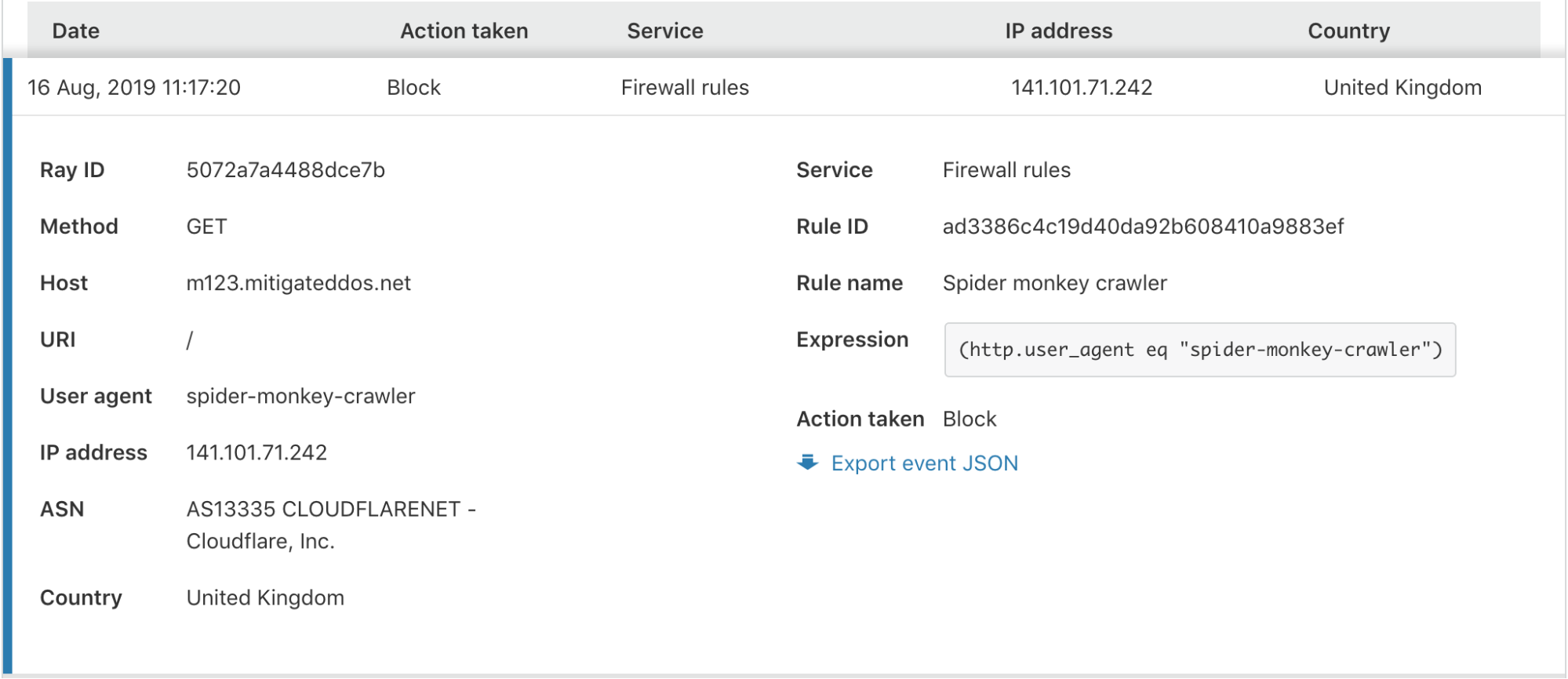
In the expanded view, you are provided with all the information you may need to identify or diagnose issues with your Firewall or find more details about a potential threat to your application.
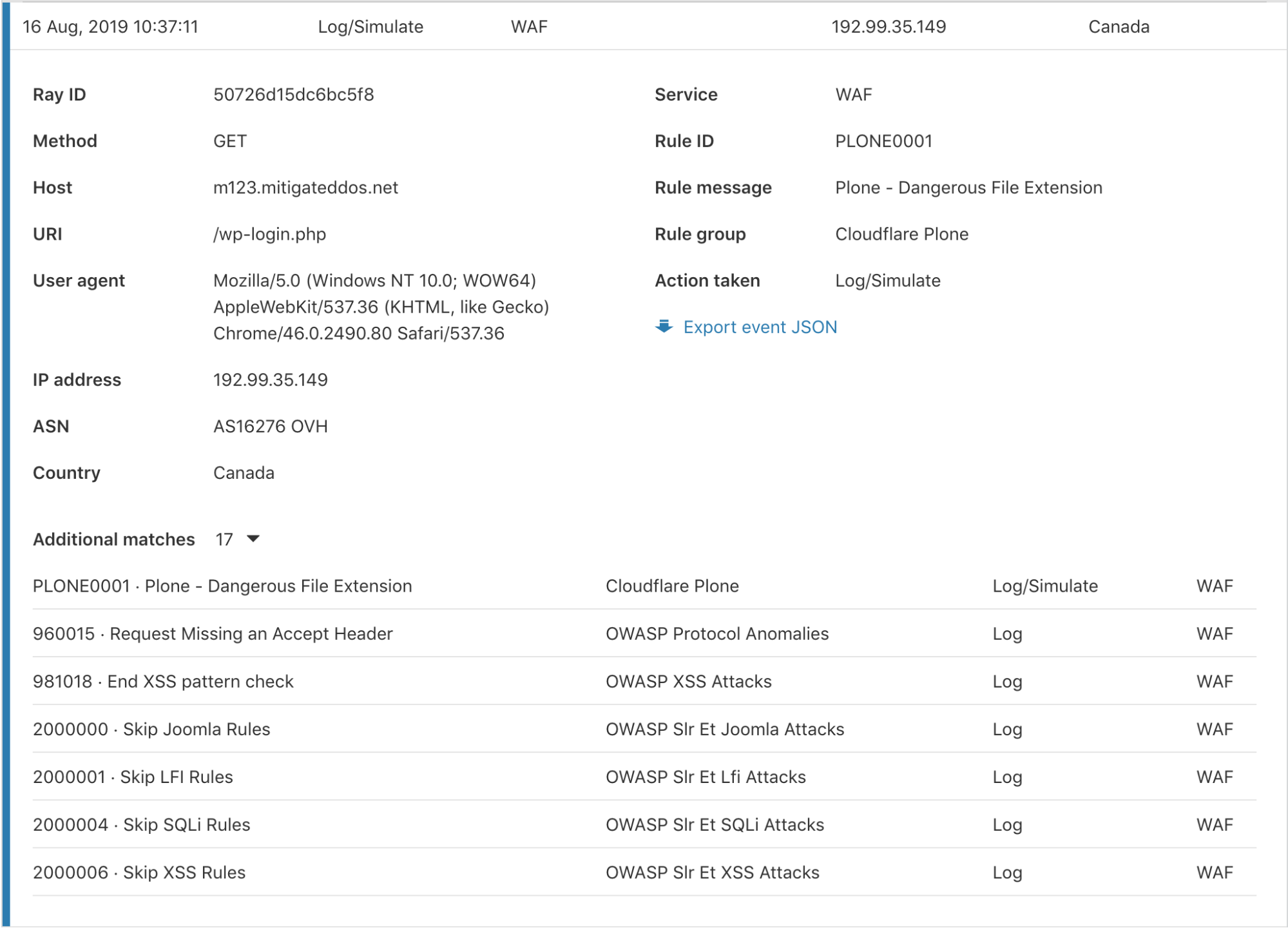
Additional matches per event
Cloudflare has several Firewall features to give customers granular control of their security. With this control comes some complexity when debugging why a request was stopped by the Firewall. To help clarify what happened, we have provided an “Additional matches” count at the bottom for events triggered by multiple services or rules for the same request. Clicking the number expands a list showing each rule and service along with the corresponding action.
Search for any field within a Firewall Event
Can a Composable Hypervisor Re-Imagine Virtualization?
“Virtualization is changing and what people need from virtualization is changing,” said Intel's...
VMware Buying Spree Continues With Intrinsic
VMware bought Intrinsic, an application security startup, in its fifth acquisition in three months,...
Microsoft, Intel, and Red Hat Back Confidential Computing
The Linux Foundation’s Confidential Computing Consortium is a who’s who of cloud providers,...
VMware Cloud on AWS: NSX and Avi Networks Load Balancing and Security
Authors and Contributors
I want to thank both Bhushan Pai, and Matt Karnowski, who joined VMware from the Avi Networks acquisition, for helping with the Avi Networks setup in my VMware Cloud on AWS lab and helping with some of the details in this blog.
Humair Ahmed, Sr. Technical Product Manager, VMware NSBU
Bhushan Pai, Sr. Technical Product Manager, VMware NSBU
Matt Karnowski , Product Line Manager, VMware NSBU
With the recent acquisition of Avi Networks, a complete VMware solution leveraging advanced load balancing and Application Delivery Controller (ADC) capabilities can be leveraged. In addition to load balancing, these capabilities include global server load balancing, web application firewall (WAF) and advanced analytics and monitoring.
In this blog, we walk through an example of how the Avi Networks load balancer can be leveraged within a VMware Cloud on AWS software-defined data center (SDDC).
Cybersecurity Tech Accord Adopts Bug Disclosure Policies
The 111 Cybersecurity Tech Accord companies compete daily but all agree on the big picture:...
Deep Dive: How Healthcare Organizations Practice Privacy and Security

In April, the Online Trust Alliance published the 11th annual Online Trust Audit assessing the security and privacy of 1,200 top organizations across several industry sectors. For the first time, this year’s Audit covered 100 of the top healthcare organizations, including lab testing companies, pharmacies, hospital chains, and insurance providers.
How did they do?
Since this is the first year these organizations were included, we do not have historical comparisons, but we can compare how healthcare sites fared against the other audited sectors. Overall, 57% of healthcare sites made this year’s Honor Roll, the lowest of all the sectors we studied. By far the most common reason for failure in the healthcare sector was weak email security (35%, nearly triple the overall average). Failure due to privacy was better than average, while failure due to site security was slightly worse than average.
Email Security
SPF and DKIM help protect against forged email. Overall 87% of healthcare organizations had SPF on their top-level domain and 67% had DKIM (the lowest of any sector, and the main source of healthcare’s failing scores). DMARC builds on SPF and DKIM results, provides a means for feedback reports, and adds visibility for Continue reading
AWS ABCs: Granting A Third-Party Access to Your Account
There can be times when you’re working on the AWS Cloud where you need to grant limited access to your account to a third-party. For example:
- A contractor or a specialist needs to perform some work on your behalf
- You’re having AWS Professional Services or a partner from the Amazon Partner Network do some work in your account
- You’re conducting a pilot with AWS and you want your friendly neighborhood Solutions Architect to review something
In each of these cases you likely want to grant the permissions the third-party needs but no more. In other words, no granting of AdministratorAccess policies because it’s easy and just works. Instead, adherence to the principle of least privilege.
This post will describe two methods–IAM users and IAM roles–for proving limited access to third-parties.
Comparing the Two Approaches
The big difference with the IAM user approach vs the role-based approach is the way the credentials for each entity are handed out.
IAM users have long-term credentials that only change by a manual action (either the user or an administrator changes the credentials). Those credentials will continue to provide access to the account until they’re either changed or the user is disabled/deleted.
By contrast, roles Continue reading
VMworld 2019: Sneak Peak at Our Keynote Sessions. Plus a Chance to Win!
Networking & Security Keynotes at VMworld 2019
About a month ago, we published a VMworld security guide with shortlisted 100 to 300 level sessions that best illustrate real-world application of our products. This time, we’ll be focusing on two networking and security keynotes. The first keynote will highlight how VMware’s single-stack, complete networking and security platform can achieve a consistent operational network fabric for hybrid cloud environments, and the second keynote will focus on how users can leverage existing VMware infrastructure to implement a more effective, intrinsic security.
In addition, you will have a shot at winning Bose headphones simply by attending each event. Although chances are slim (1250 times harder to win both as opposed to just one), duplicate winners will be acknowledged so if you are looking for a present for yourself and a significant other, make sure to register and save on your yearly bonus! Winners will be announced at the end of each keynote, so make sure to stay until the end!
Showcase Keynote: Networking and Security for the Cloud Era [NETS3413KU]

There has never been a more exciting and challenging time in the networking space. As the cloud, application developers, IoT, Continue reading
U.S. Delays Huawei Ban Another 90 Days
Huawei earned itself another narrow and temporary reprieve from a blanket ban against doing...
Cisco and F5 Networks Discuss the Value of Tech Partnerships
SDxCentral spoke with Cisco and F5 Networks about their companies’ complementary approaches and...
Cloudflare Files IPO Paperwork to Battle AWS, Cisco, and Oracle
It also directly competes against CDN firms like Akamai, Limelight, and Fastly, which went public...
Cisco Software Subscriptions Hit 70%, China Trade War Spooks Investors
Cisco’s China revenue dropped 25% on an annualized basis in the fourth quarter.
Key Steps and Pitfalls to Avoid in Cloud Security, with Valtix’s CEO Vishal Jain
Hear from Valtix CEO Vishal Jain and is his take on cloud security today, where it’s going, and...