Stopping Drupal’s SA-CORE-2019-003 Vulnerability
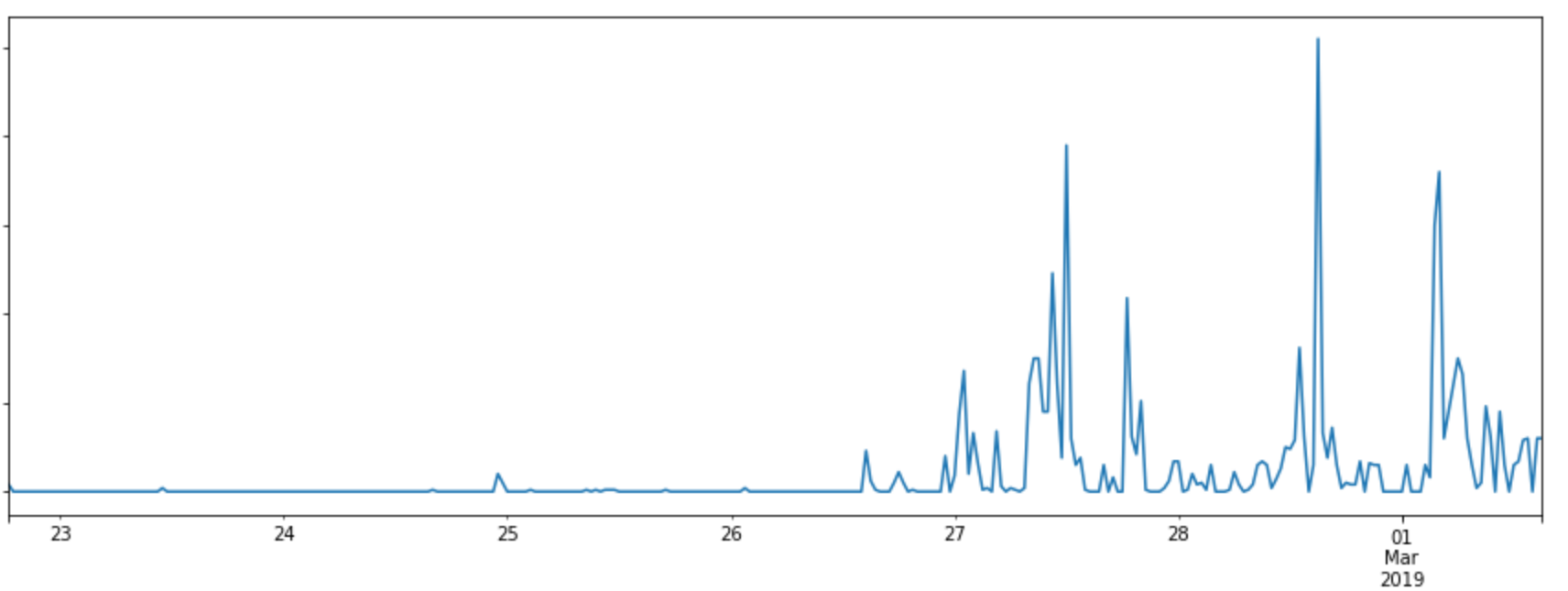
On the 20th February 2019, Drupal announced that they had discovered a severe vulnerability and that they would be releasing a patch for it the next day. Drupal is a Content Management System used by many of our customers, which made it important that our WAF protect against the vulnerability as quickly as possible.
As soon as Drupal released their patch, we analysed it to establish what kind of payloads could be used against it and created rules to mitigate these. By analysing the patch we were able to put together WAF rules to protect cloudflare customers running Drupal.
We identified the type of vulnerability we were dealing within 15 minutes. From here, we were able to deploy rules to block the exploit well before any real attacks were seen.
The exploit
As Drupal's release announcement explains, a site is affected if:
From looking at the patch we very quickly realised the exploit would be based on deserialization. The option ['allowed_classes' Continue reading
Lobbying and Lying to Make Insecure HTTPS Protocols at ETSI

ETSI shows its coin-operated nature by working on insecure protocols
The post Lobbying and Lying to Make Insecure HTTPS Protocols at ETSI appeared first on EtherealMind.
Introducing NSX-T 2.4 – A Landmark Release in the History of NSX
In February 2017, we introduced VMware NSX-T Data Center to the world. For years, VMware NSX for vSphere had been spearheading a network transformation journey with a software-defined, application-first approach. In the meantime, as the application landscape was changing with the arrival of public clouds and containers, NSX-T was being designed to address the evolving needs of organizations to support cloud-native applications, bare metal workloads, multi-hypervisor environments, public clouds, and now, even multiple clouds.
Today, we are excited to announce an important milestone in this journey – the NSX-T 2.4 release. This fourth release of NSX-T delivers advancements in networking, security, automation, and operational simplicity for everyone involved – from IT admins to DevOps-style teams to developers. Today, NSX-T has emerged as the clear choice for customers embracing cloud-native application development, expanding use of public cloud, and mandating automation to drive agility.
Let’s take a look at some of the new features in NSX-T 2.4:
Operational Simplicity: Easy to Install, Configure, Operate
What if delivering new networks and network services was as easy as spinning up a workload in AWS? In keeping with the ethos that networking can be made easier, over the past few releases, we Continue reading
Re-Introducing VMware AppDefense, Part I – Application Security in Virtualized and Cloud Environments
This blog will be part of a series where we start off with a basic re-introduction of VMware AppDefense and then progressively get into integrations, best practices, mitigating attacks and anomaly detection with vSphere Platinum, vRealize Log Insight, AppDefense and NSX Data Center. Before we get into the meat of things, let’s level-set on a few core principles of what VMware believes to be appropriate cyber hygiene. The full white paper can be viewed here.
- Follow a least privileged model
- The principle of least privilege is the idea that at any user, program, or process should have only the bare minimum privileges necessary to perform its function. For example, a user account created for pulling records from a database doesn’t need admin rights, while a programmer whose main function is updating lines of legacy code doesn’t need access to financial records. The principle of least privilege can also be referred to as the principle of minimal privilege (POMP) or the principle of least authority (POLA). Following the principle of least privilege is considered a best practice in information security.
- The least privilege model works by allowing only enough access to perform the required job. In an IT environment, adhering to Continue reading
A basic question about TCP
So on Twitter, somebody asked this question:I have a very basic computer networking question: when sending a TCP packet, is the packet ACK'ed at every node in the route between the sender and the recipient, or just by the final recipient?This isn't just a basic question, it is the basic question, the defining aspect of TCP/IP that makes the Internet different from the telephone network that predated it.
Remember that the telephone network was already a cyberspace before the Internet came around. It allowed anybody to create a connection to anybody else. Most circuits/connections were 56-kilobits-per-secondl using the "T" system, these could be aggregated into faster circuits/connections. The "T1" line consisting of 1.544-mbps was an important standard back in the day.
In the phone system, when a connection is established, resources must be allocated in every switch along the path between the source and destination. When the phone system is overloaded, such as when you call loved ones when there's been an earthquake/tornado in their area, you'll sometimes get a message "No circuits are available". Due to congestion, it can't reserve the necessary resources in one of the switches along the route, so the call can't be Continue reading
IHS Markit Talks Pioneering Private Cloud, Containers, and VMware Cloud on AWS
Global information, analytics, and solutions company IHS Markit provides data-driven insight for its government and corporate customers. Using VMware vRealize Automation, the company has already rolled out a private cloud that helped developers cut a 6-month infrastructure provisioning process down to one week. They’ve also been using VMware NSX-T Data Center to secure their workloads at a granular level with micro-segmentation, and to fundamentally re-think network design.
At VMworld 2018 in Las Vegas, Andrew Hrycaj, Principal Network Engineer for IHS Markit, spoke about the company’s plans for software-defined networking and hybrid cloud. IHS Markit has deployed VMware NSX Data Center, including NSX-T Data Center and VMware NSX Data Center for vSphere, into five data centers. “The NSX Data Center advantage for us is the fact that it can interact with so many different environments; from containers, to the public cloud environment with AWS and Azure, to on-prem,” said Hrycaj. “We’ll be able to utilize micro-segmentation across all of them with a common security footprint. If NSX-T goes to all those different environments, we can apply the same security policy across all those different platforms. It makes operations’ life easier because the transparency is there.”
Innovating with Continue reading
Nokia CEO Rajeev Suri Keeps 5G Pressure on Euro Operators
 Suri also stated that in terms of costs, Nokia was “confident” in its ability to compete, and...
Suri also stated that in terms of costs, Nokia was “confident” in its ability to compete, and...
Cloudflare’s RPKI Toolkit

A few months ago, we made a first then a second announcement about Cloudflare’s involvement in Resource Public Key Infrastructure (RPKI), and our desire to make BGP Internet routing more secure. Our mission is to build a safer Internet. We want to make it easier for network operators to deploy RPKI.
Today’s article is going to cover our experience and the tools we are using. As a brief reminder, RPKI is a framework that allows networks to deploy route filtering using cryptography-validated information. Picture TLS certificates for IP addresses and Autonomous System Numbers (ASNs)
What it means for you:
We validate our IP routes. This means, as a 1.1.1.1 DNS resolver user, you are less likely to be victim of cache poisoning. We signed our IP routes. This means a user browsing the websites on Cloudflare’s network are unlikely to experience route hijacks.
All our Points of Presence which have a router compatible with The Resource Public Key Infrastructure (RPKI) to Router Protocol (RTR protocol) are connected to our custom software called GoRTR and are now filtering invalid routes. The deployment amounts to around 70% of our network.
We received many questions regarding the amount of invalid Continue reading
Cloudflare Registrar at three months


We announced Cloudflare Registrar in September. We launched the product by making it available in waves to our existing customers. During that time we gathered feedback and continued making improvements to the product while also adding more TLDs.
Staring today, we’re excited to make Cloudflare Registrar available to all of our customers. Cloudflare Registrar only charges you what we pay to the registry for your domain and any user can now rely on that at-cost pricing to manage their domain. As part of this announcement, we’d like to share some insights and data about domain registration that we learned during the early access period.
One-click DNS security makes a difference
When you launch your domain to the world, you rely on the Domain Name System (DNS) to direct your users to the address for your site. However, DNS cannot guarantee that your visitors reach your content because DNS, in its basic form, lacks authentication. If someone was able to poison the DNS responses for your site, they could hijack your visitors' DNS requests.
The Domain Name System Security Extensions (DNSSEC) can help prevent that type of attack by adding a chain of trust to DNS queries. When you enable DNSSEC Continue reading
SDxCentral’s Weekly Roundup — February 22, 2019
 Pivotal and Samsung join the O-RAN Alliance; Splunk withdraws from Russia; Microsoft expands its...
Pivotal and Samsung join the O-RAN Alliance; Splunk withdraws from Russia; Microsoft expands its...
Oracle, KPMG Cloud Threat Report Finds Confidence and Fear
 An Oracle and KPMG survey found 38 percent of professionals say the ability to detect and react to...
An Oracle and KPMG survey found 38 percent of professionals say the ability to detect and react to...
128 Technology Is Starting a Revolution for Secure SD-WAN, Networking
 Companies want simplicity and security, so “I don’t think building virtual networks on top of...
Companies want simplicity and security, so “I don’t think building virtual networks on top of...
Tenable, Forescout Both Merge Their IT and OT Security Platforms
 Preventing damaging intrusions to increasingly comingled IT and operational technology (OT) domains...
Preventing damaging intrusions to increasingly comingled IT and operational technology (OT) domains...
Cloudflare Access now supports RDP
Last fall, the United States FBI warned organizations of an increase in attacks that exploit vulnerabilities in the Remote Desktop Protocol (RDP). Attackers stole sensitive data and compromised networks by taking advantage of desktops left unprotected. Like legacy VPNs, RDP configurations made work outside of the office corporate network possible by opening a hole in it.
Starting today, you can use Cloudflare Access to connect over RDP without sacrificing security or performance. Access enables your team to lock down remote desktops like you do physical ones while using your SSO credentials to authenticate each connection request.
Stronger passwords with identity provider integration
The FBI cited weak passwords and unrestricted port access to RDP ports as serious risks that led to the rise in RDP-based attacks. Cloudflare Access addresses those vulnerabilities by removing them altogether.
When users connect over RDP, they enter a local password to login to the target machine. However, organizations rarely manage these credentials. Instead, users set and save these passwords on an ad-hoc basis outside of the single sign-on credentials used for other services. That oversight leads to outdated, reused, and ultimately weak passwords.
Cloudflare Access integrates with the identity credentials your team already uses. Whether your Continue reading
5G, IoT Security and … Oh, Look, a Dancing Robot!
 Security should be a hot topic at MWC 2019. But will it?
Security should be a hot topic at MWC 2019. But will it?
MWC Barcelona: 5G, Software, and Security With 100,000 Friends
 We here at SDxCentral are also interested in hearing more about the importance of software, network...
We here at SDxCentral are also interested in hearing more about the importance of software, network...
Pulse Secure Adds Software-Defined Perimeter, Protects Hybrid IT
 Pulse Secure added software-defined perimeter technology to its portfolio, which puts zero-trust...
Pulse Secure added software-defined perimeter technology to its portfolio, which puts zero-trust...
Ericsson and Juniper 5G Transport, Security Tie-Up Touts Progress
 The duo claims 20 contract wins since the partnership was announced last September. This includes a...
The duo claims 20 contract wins since the partnership was announced last September. This includes a...