Verizon Buys Software-Defined Perimeter Assets From Vidder
 Vidder’s technology is already integrated into Verizon’s SDP service.
Vidder’s technology is already integrated into Verizon’s SDP service.
Weekly Wrap Podcast: Germany Jumps on Huawei 5G Ban Plans
 SDxCentral Weekly Wrap for Nov. 16, 2018: Germany Jumps on Huawei 5G Ban Plans.
SDxCentral Weekly Wrap for Nov. 16, 2018: Germany Jumps on Huawei 5G Ban Plans.
BlackBerry Bets $1.4B on IoT Security With Cylance Acquisition
 In a year when security startups are raising hundreds of millions in initial public offerings — including Cylance competitor Carbon Black that scored $152 million in its May IPO — it was widely assumed Cylance would follow suit.
In a year when security startups are raising hundreds of millions in initial public offerings — including Cylance competitor Carbon Black that scored $152 million in its May IPO — it was widely assumed Cylance would follow suit.
El Buen Fin: Tips to Shop Smart

Last week I had the opportunity to participate in the first edition of the International Internet and Entrepreneurship Forum (FIIE), in Monterrey, Mexico. The event was convened by NIC Mexico and other organizations of the Internet community of Latin America and the Caribbean as part of the activities of INCmty, an entrepreneurial festival with several years of tradition. The intersection between both topics is a fertile ground for reflection, especially in relation to the security of Internet of Things (IoT) devices.
IoT for Innovation and Entrepreneurship
The Internet has been known as a technology for facilitating innovation and entrepreneurship. The pace of technological development, together with the evolution of the Internet, has given rise to new solutions that seek to make life easier. Such is the case of the various devices connected to the Internet, which form the Internet of Things ecosystem.
Therefore, one of the issues addressed during the Forum was the role of IoT devices in the entrepreneurial ecosystem in the LAC region. There I took the opportunity to share the Internet Society’s vision of IoT security: we want people to benefit from the use of these devices in a trustworthy environment. The issue is particularly Continue reading
Announcing SSH Access through Cloudflare

We held our annual Cloudflare Retreat last week. Over 750 team members from nearly a dozen offices spent three days learning, bonding and some of them got to smash a VPN piñata on stage with a baseball bat. Yes, you read that right.
The latest feature added to Cloudflare Access let us celebrate the replacement of our clunky VPN with a faster, safer way to reach our internal applications. You can now place applications that require SSH connections, like your source control repository, behind Cloudflare Access. We’re excited to release that same feature so that your team can also destroy your own VPN (piñata not included).

How we smashed our VPN
We built Access to replace our corporate VPN. We started with browser-based applications, moved to CLI operations, and then began adding a growing list of single sign-on integrations. Our teammates added single sign-on support to the Cloudflare dashboard by combining Access and our serverless product, Workers. We improved the daily workflow of every team member each time we moved another application behind Access. However, SSH connections held us back. Whenever we needed to push code or review a pull request, we had to fall back to our Continue reading
Indian Companies Help Propel Cisco’s Strong Q1 2019 Earnings
 It was the company's second quarter of 50 percent-plus growth in India.
It was the company's second quarter of 50 percent-plus growth in India.
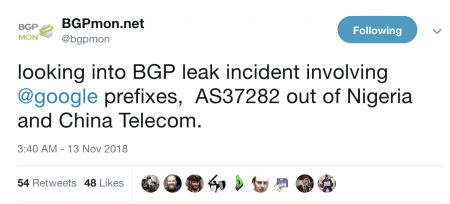
Route Leak Causes Major Google Outage

Google recently faced a major outage in many parts of the world thanks to a BGP leak. This incident that was caused by a Nigerian ISP – Mainone – occurred on 12 November 2018 between 21.10 and 22.35 UTC, and was identified in tweets from the BGP monitoring service BGPMon, as well as the network monitoring provider Thousand Eyes.
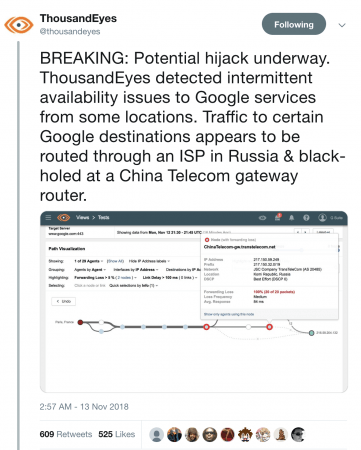
Google also announced the problem through their status page:
We’ve received a report of an issue with Google Cloud Networking as of Monday, 2018-11-12 14:16 US/Pacific. We have reports of Google Cloud IP addresses being erroneously advertised by internet service providers other than Google. We will provide more information by Monday, 2018-11-12 15:00 US/Pacific.
In order to understand this issue, MainOne Inc (AS37282) is peering at IXPN (Internet Exchange Point of Nigeria) in Lagos where Google (AS151169) and China Telecom (AS4809) are also members.
Google (AS15169) advertise their prefixes (more than 500) through the IXPN Route Server, where PCH (Packet Clearing House) collects a daily snapshot of BGP announcements of IXPN. Unfortunately, 212 prefixes (aggregates of those 500+ announcements) from Google were leaked, which was recorded by BGPMon and RIPEstat.
Looking at the RIPE stats it is evident Continue reading
How a Nigerian ISP Accidentally Knocked Google Offline
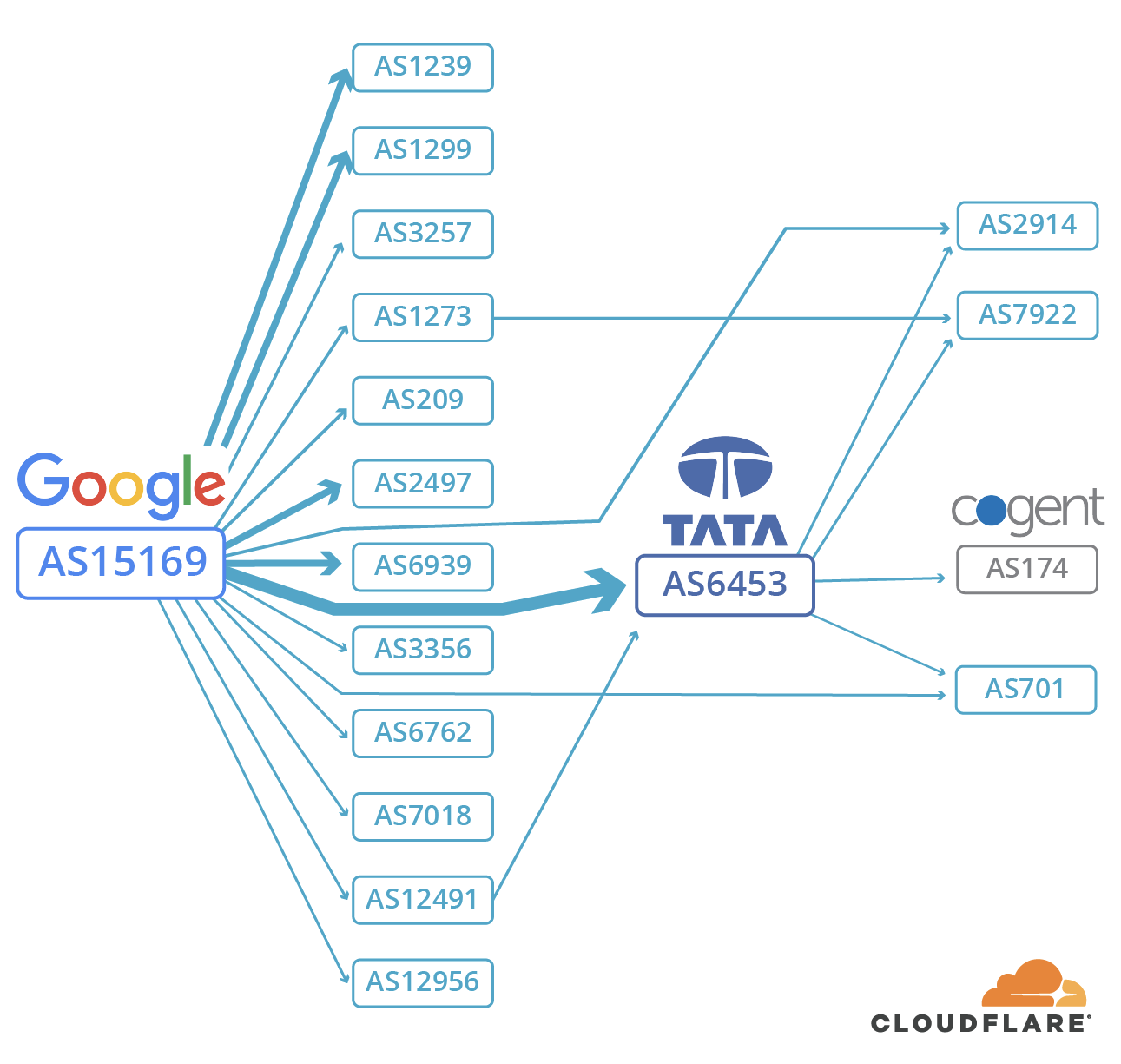
Last Monday evening — 12 November 2018 — Google and a number of other services experienced a 74 minute outage. It’s not the first time this has happened; and while there might be a temptation to assume that bad actors are at work, incidents like this only serve to demonstrate just how much frailty is involved in how packets get from one point on the Internet to another.
Our logs show that at 21:12 UTC on Monday, a Nigerian ISP, MainOne, accidentally misconfigured part of their network causing a "route leak". This resulted in Google and a number of other networks being routed over unusual network paths. Incidents like this actually happen quite frequently, but in this case, the traffic flows generated by Google users were so great that they overwhelmed the intermediary networks — resulting in numerous services (but predominantly Google) unreachable.
You might be surprised to learn that an error by an ISP somewhere in the world could result in Google and other services going offline. This blog post explains how that can happen and what the Internet community is doing to try to fix this fragility.
What Is A Route Leak, And How Does One Happen?
Gartner Report Highlights Different Vendor SD-WAN Strategies
 The analyst firm also predicts that by 2023 more than 90 percent of WAN edge infrastructure initiatives will be based on SD-WAN.
The analyst firm also predicts that by 2023 more than 90 percent of WAN edge infrastructure initiatives will be based on SD-WAN.
Seven New Spectre, Meltdown-Type Attacks Discovered
 Intel says not to worry and that the earlier patches it issued address these new security flaws as well as the older hardware bugs.
Intel says not to worry and that the earlier patches it issued address these new security flaws as well as the older hardware bugs.
Riverbed SD-WAN Gets Security, Enterprise-Routing Upgrade
 The vendor integrated SD-WAN, application acceleration, visibility, and security in a single device and says its SD-WAN now has more than 1,000 customers.
The vendor integrated SD-WAN, application acceleration, visibility, and security in a single device and says its SD-WAN now has more than 1,000 customers.
Germany Jumps on Huawei 5G Ban Plans, Says Report
 Government officials want to prevent German telecom operators from using equipment from Chinese firms to construct their 5G networks. This would be similar to moves made by the U.S. and Australia.
Government officials want to prevent German telecom operators from using equipment from Chinese firms to construct their 5G networks. This would be similar to moves made by the U.S. and Australia.
Inspecting Gadgets: Don’t Forget the Asterisk When Buying Smart Devices

As we approach the holiday buying season, excitement is building for all the new IoT gadgets – “smart” everything for the home, fitness/health trackers and a plethora of connected children’s toys. But this excitement should come with a giant asterisk:
* Are these products safe?
We’ve all seen the horror stories – hacked baby monitors, vulnerable door locks, robot vacuums turned into roving surveillance devices and connected toys pulled from shelves.
Clearly these gadgets need further inspection. This week the Internet Society has joined with Consumers International and Mozilla to advocate for a set of five minimum security and privacy standards IoT manufacturers should follow to improve the safety of their products. Mozilla has incorporated these into their evaluation of 70 products in the latest version of Privacy Not Included, their holiday IoT buyer’s guide. More detailed explanations of the guide and evaluation criteria are also available.
These minimum guidelines are great start to improve IoT security and privacy. They are a subset of our IoT Trust Framework, which comprehensively addresses key security, privacy and lifecycle principles that should be incorporated into IoT offerings. Manufacturers can use this list of principles to practice “trust by design,” resellers can Continue reading
Research Brief: Achieving Success in Modern Network Automation
 This new Research Brief from AvidThink is aimed at providing enterprises and service providers with a view of the challenges in modern networking, and detailed strategies on how to overcome them by laying the right foundation for network automation.
This new Research Brief from AvidThink is aimed at providing enterprises and service providers with a view of the challenges in modern networking, and detailed strategies on how to overcome them by laying the right foundation for network automation.
Related Stories
U.S. R&E Community Embraces Routing Security

The Internet Society participated in a Routing Security Workshop that was held during the Internet2 Technology Exchange 2018 on 15 October 2018 in Orlando, United States. The research and education networking community has been one of the key targets of the MANRS initiative that is promoting adoption of best practices to reduce threats to the global routing system, and this community workshop followed on from a previous engagement we had with Internet2 and a number of other R&E networks in the US earlier in the year.
Internet2 interconnects R&E institutes across the United States in conjunction with regional and state networks, so we see them as a key partner in raising awareness of the routing security issues, as well as encouraging the adoption of the four MANRS principles. Indeed, one of the aims of MANRS is for network operator communities to take ownership of this process by generating awareness and disseminating best practices, along with making recommendations for improvement. So this workshop was a fantastic step in this direction.
Another positive step was Internet2 formally becoming a MANRS participant shortly before the workshop, follow in the footsteps of ESnet, CAAREN, KanREN, George Washington University, Indiana University, and DePaul University. WiscNet Continue reading
Real URLs for AMP Cached Content Using Cloudflare Workers


Today, we’re excited to announce our solution for arguably the biggest issue affecting Accelerated Mobile Pages (AMP): the inability to use real origin URLs when serving AMP-cached content. To allow AMP caches to serve content under its origin URL, we implemented HTTP signed exchanges, which extend authenticity and integrity to content cached and served on behalf of a publisher. This logic lives on Cloudflare Workers, meaning that adding HTTP signed exchanges to your content is just a simple Workers application away. Publishers on Cloudflare can now take advantage of AMP performance and have AMP caches serve content with their origin URLs. We're thrilled to use Workers as a core component of this solution.
HTTP signed exchanges are a crucial component of the emerging Web Packaging standard, a set of protocols used to package websites for distribution through optimized delivery systems like Google AMP. This announcement comes just in time for Chrome Dev Summit 2018, where our colleague Rustam Lalkaka spoke about our efforts to advance the Web Packaging standard.
What is Web Packaging and Why Does it Matter?
You may already see the need for Web Packaging on a daily basis. On your smartphone, perhaps you’ve searched for Christmas Continue reading
Latest Security Unicorn Netskope Scores $168.7M Series F
 An IPO is on the horizon but being acquired is not. “We are fiercely independent,” Netskope CEO Sanjay Beri said.
An IPO is on the horizon but being acquired is not. “We are fiercely independent,” Netskope CEO Sanjay Beri said.
Disastrous Cloud Transformation? Change Management Could Be the Answer
 To be successful in the cloud world, there needs to be an organizational shift within companies to encompass both change management and skills management.
To be successful in the cloud world, there needs to be an organizational shift within companies to encompass both change management and skills management.
Cisco Combines SD-WAN and Security, Extends Intent-Based Networking to Wireless
 The new Cisco SD-WAN Security product combines Viptela’s technology with Meraki, Cisco’s cloud-managed IT service and wireless LAN product, plus Cisco security software.
The new Cisco SD-WAN Security product combines Viptela’s technology with Meraki, Cisco’s cloud-managed IT service and wireless LAN product, plus Cisco security software.
We Won’t Save the Internet by Breaking It

On the anniversary of the armistice ending the First World War, more than 40 countries stood together for security online by signing the Paris Call for Trust and Security in Cyberspace. The call, which sets out a list of challenges the world needs to tackle, seems to be promising on paper. From hacking to harming the public core – all of this needs to be addressed. And it needs to be addressed urgently.
Others signed the call too. The Internet Society signed because we believe it is a continuation of calls we have made before. It maintains that solutions to Internet issues must be developed together with other Internet stakeholders – each performing its role, and all working collaboratively.
This approach is what allows the Internet to thrive and is key to the ultimate success of this call. Open, decentralized, and distributed. It’s not the traditional multilateral way of doing things, but it is the Internet way – the only one that can work.
There are real and pressing Internet security concerns. It’s critical that signatories to the call do not imagine they can address the concerns alone. The Internet depends, as a technical fact, on cooperative voluntary action, so Continue reading