Nation-States Attack MSP Networks, DHS Security Alert Warns
 Managed service providers' customers — especially IT, energy, healthcare, communications, and manufacturing companies — are the end target for these attacks.
Managed service providers' customers — especially IT, energy, healthcare, communications, and manufacturing companies — are the end target for these attacks.
Are you ready? How to prepare for the DNSSEC Root KSK Rollover on October 11, 2018

Are you ready? Are your systems prepared so that DNS will keep functioning for your networks? One week from today, on Thursday, October 11, 2018, at 16:00 UTC ICANN will change the cryptographic key that is at the center of the DNS security system – what we call DNSSEC. The current key has been in place since July 15, 2010. This is a long-planned replacement.
If everything goes fine, you should not notice and your systems will all work as normal. However, if your DNS resolvers are not ready to use the new key, your users may not be able to reach many websites, send email, use social media or engage in other Internet activities!
This change of this central security key for DNS is known as the “Root Key Signing Key (KSK) Rollover”. It has been in discussion and planning since 2013. We’ve written many articles about it and spoken about it at many conferences, as have many others in the industry. ICANN has a page with many links and articles at:
But here we are, with only a few days left and you may be wondering – how can I know if my systems Continue reading
Notes on the Bloomberg Supermicro supply chain hack story
Bloomberg has a story how Chinese intelligence inserted secret chips into servers bound for America. There are a couple issues with the story I wanted to address.The story is based on anonymous sources, and not even good anonymous sources. An example is this attribution:
a person briefed on evidence gathered during the probe saysThat means somebody not even involved, but somebody who heard a rumor. It also doesn't the person even had sufficient expertise to understand what they were being briefed about.
The technical detail that's missing from the story is that the supply chain is already messed up with fake chips rather than malicious chips. Reputable vendors spend a lot of time ensuring quality, reliability, tolerances, ability to withstand harsh environments, and so on. Even the simplest of chips can command a price premium when they are well made.
What happens is that other companies make clones that are cheaper and lower quality. They are just good enough to pass testing, but fail in the real world. They may not even be completely fake chips. They may be bad chips the original manufacturer discarded, or chips the night shift at the factory secretly ran through on the Continue reading
National Cybersecurity Awareness Month = International IoT Security and Privacy Month

October is National Cybersecurity Awareness Month, and as part of our work with the Online Trust Alliance and our Internet of Things (IoT) campaign, we think October also deserves another label… International IoT Security and Privacy Month. There are a number of significant activities and developments related to security and privacy. Here are a few highlights of what’s happening, how we are participating, and how you can get involved.
- The “How to Make Trustworthy #IoT” Workshop – (Oct. 8) This year’s Internet Society Chapterthon is focused on IoT, and we are excited to see how all 43 participating Chapters raise awareness of the privacy and security issues surrounding IoT. On Monday, 8 October, Jeff Wilbur and Megan Kruse from the Online Trust Alliance be in New York City with the Internet Society New York Chapter (ISOC-NY) and IoTNation holding a workshop on ‘How to Make Trustworthy IoT’ – an IoT Privacy & Security Workshop. If you’ll be in New York City on Monday, please consider registering for the event, or watching the livestream starting at 2PM.
- Comments due for NIST Internal Report (NISTIR) 8228: Considerations for Managing IoT Cybersecurity and Privacy Risks – (Oct. 24) The report by Continue reading
China Hacked Supermicro Servers to Spy on Amazon, Microsoft, Report Says
 A former U.S. intelligent official said that data center server provider Supermicro was the "Microsoft of the hardware world" and that attacking Supermicro motherboards was "like attacking the whole world.”
A former U.S. intelligent official said that data center server provider Supermicro was the "Microsoft of the hardware world" and that attacking Supermicro motherboards was "like attacking the whole world.”
SD-WAN vs. Next-Gen Firewalls: Chicken or the Egg?
 At the SD-WAN Summit 2018 in Paris, one of the more contentious debates was which will come first: next-generation firewall or new SD-WAN capabilities?
At the SD-WAN Summit 2018 in Paris, one of the more contentious debates was which will come first: next-generation firewall or new SD-WAN capabilities?
Announcing Firewall Rules


Threat landscapes change every second. As attackers evolve, becoming more dynamic and devious, vulnerabilities materialize faster than engineers can patch their applications. Part of Cloudflare’s mission is to keep you and your applications safe. Today, Cloudflare is launching a new feature, giving customers what they have been requesting - fine-grained control over their incoming requests.
Cloudflare already offers a number of powerful firewall tools such as IP rules, CIDR rules, ASN rules, country rules, HTTP user-agent blocking, Zone Lockdown (for these URIs only allow traffic from those IPs), and our comprehensive managed rules within our WAF (Web Application Firewall). But sometimes, you need to combine the power of these to fully mitigate an attack, and to express a block rule that breaks the boundaries of the existing tools, to be able to “block traffic to this URI when the request comes from that IP and the user-agent matches one of these”.
Flexibility and Control

© Stefano Kocka : Source Wikipedia
Common themes arose when we spoke to customers about their needs and also reviewed feature requests that our customer support team had seen, and we categorised the top pieces of feedback and feature requests into three core needs:
- More flexibility Continue reading
Palo Alto Networks Pays $173M for Cloud Security Startup RedLock
 Palo Alto Networks plans to combine technologies from RedLock and Evident, another recent acquisition, into one product that provides cloud security analytics, advanced threat detection, continuous security, and compliance monitoring.
Palo Alto Networks plans to combine technologies from RedLock and Evident, another recent acquisition, into one product that provides cloud security analytics, advanced threat detection, continuous security, and compliance monitoring.
Cisco’s David Ulevitch Leaves to Join a VC Firm
 David Ulevitch, who was once in charge of Cisco’s security business, is leaving to become a general partner at Andreesson Horowitz.
David Ulevitch, who was once in charge of Cisco’s security business, is leaving to become a general partner at Andreesson Horowitz.
Cloudflare Access: Sharing our single-sign on plugin for Atlassian
Here at Cloudflare, we rely on a set of productivity tools built by Atlassian, including Jira and Confluence. We secure them with Cloudflare Access. In the past, when our team members wanted to reach those applications, they first logged in with our identity provider credentials to pass Access. They then broke out a second set of credentials, specific to Atlassian tools, to reach Jira. The flow is inconvenient on a desktop and downright painful on a mobile device.
While Access can determine who should be able to reach an application, the product alone cannot decide what the user should be able to do once they arrive at the destination. The application sets those specific permissions, typically by requiring another set of user credentials. The extra step slows down and frustrates end users. Access saves time by replacing a cumbersome VPN login. However, we wanted to also solve the SSO problem for our team.
We created a plugin, specific to Atlassian, that could take identity data from the token generated by Access and map it to a user account. Our team members log in with our identity provider to pass Access, and then Access could set their user permissions in Jira Continue reading
Cohesity Targets Service Providers With Multi-Tenant Platform
 The software-defined platform runs on top of Cohesity, Cisco, HPE, or Dell EMC hyperconverged secondary storage appliances.
The software-defined platform runs on top of Cohesity, Cisco, HPE, or Dell EMC hyperconverged secondary storage appliances.
Putting the M in MANO
 In the rush to capitalize on NFV many operators have focused purely on the NFV orchestration, but as they move from trials to production, one key piece is missing — management.
In the rush to capitalize on NFV many operators have focused purely on the NFV orchestration, but as they move from trials to production, one key piece is missing — management.
AWS ABCs – Can I Firewall My Compute Instances?
In a previous post, I reviewed what a public subnet and Internet Gateway (IGW) are and that they allowed outbound and inbound connectivity to instances (ie, virtual machines) running in the AWS cloud.
If you’re the least bit security conscious, your reaction might be, “No way! I can’t have my instances sitting right on the Internet without any protection”.
Fear not, reader. This post will explain the mechanisms that the Amazon Virtual Private Cloud (VPC) affords you to protect your instances.
Security Groups
In a nutshell: security groups (SGs) define what traffic is allowed to reach an instance.
“Security group” is a bit of a weird name for what is essentially a firewall that sits in front of an instance, however if you think about it in terms of all servers at a particular tier in an N-tier application (eg, all the web servers) or all the servers that have a common function (eg, all PostgreSQL servers) and how each group would have its own security requirements when it comes to allowed ports, protocols, and IP addresses, then it makes a bit more sense: the security rules appropriate for a group of servers are all put together within Continue reading
The Facebook Breach: Some Lessons for the Internet
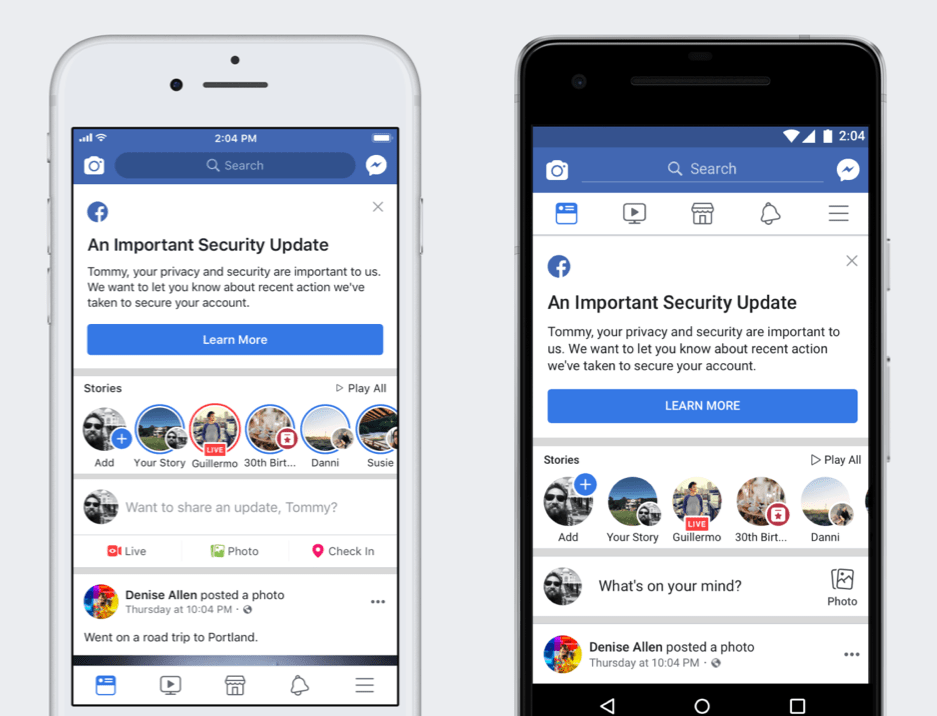
Last week Facebook found itself at the heart of a security breach that put at risk the personal information of millions of users of the social network.
On September 28, news broke that an attacker exploited a technical vulnerability in Facebook’s code that would allow them to log into about 50 million people’s accounts.
While Facebook was quick to address the exploit and fix it, they say they don’t know if anyone’s accounts actually were breached.
This breach follows the Cambridge Analytica scandal earlier this year that resulted in the serious mishandling of the data of millions of people who use Facebook.
Both of these events illustrate that we cannot be complacent about data security. Companies that hold personal and sensitive data need to be extra vigilant about protecting their users’ data.
Yet even the most vigilant are also vulnerable. Even a single security bug can affect millions of users, as we can see.
There are a few things we can learn from this that applies to the other security conversations: Doing security well is notoriously hard, and persistent attackers will find bugs to exploit, in this case a combination of three apparently unrelated ones on the Facebook platform.
This Continue reading
Mini pwning with GL-iNet AR150
Seven years ago, before the $35 Raspberry Pi, hackers used commercial WiFi routers for their projects. They'd replace the stock firmware with Linux. The $22 TP-Link WR703N was extremely popular for these projects, being half the price and half the size of the Raspberry Pi.Unfortunately, these devices had extraordinarily limited memory (16-megabytes) and even more limited storage (4-megabyte). That's megabytes -- the typical size of an SD card in an RPi is a thousand times larger.
I'm interested in that device for the simple reason that it has a big-endian CPU.
All these IoT-style devices these days run ARM and MIPS processors, with a smattering of others like x86, PowerPC, ARC, and AVR32. ARM and MIPS CPUs can run in either mode, big-endian or little-endian. Linux can be compiled for either mode. Little-endian is by far the most popular mode, because of Intel's popularity. Code developed on little-endian computers sometimes has subtle bugs when recompiled for big-endian, so it's best just to maintain the same byte-order as Intel. On the other hand, popular file-formats and crypto-algorithms use big-endian, so there's some efficiency to be gained with going with that choice.
I'd like to have a big-endian computer around to Continue reading
Birthday Week Wrap-Up: Every day is launch day at Cloudflare
Our customers are accustomed to us launching new services, features, and functionality at a feverish pace, but recently, we’ve been especially active. This week we celebrated our 8th Birthday Week by announcing new offerings that benefit our customers and the global Internet community. Our mission is to help build a better Internet, and we’re convinced that launching new capabilities that benefit not only our customers, but also the broader Internet overall, is the best way to fulfill our mission.
Helping build a better Internet, one launch at a time
As an organization, we could choose to celebrate Cloudflare’s birthday in lots of different ways (a press release, a company party, or fun gifts for all our employees). But at Cloudflare, we have a unique birthday tradition: we roll up our sleeves and give our customers and the Internet community a new capability (i.e. a gift) every day of our birthday week.
Some of this past week’s launches have been entirely new offerings, like providing key-value storage across Cloudflare’s global cloud network with Cloudflare Workers KV. Other birthday week launches help improve the overall Internet ecosystem: the Bandwidth Alliance reduces data transfer charges from major cloud hosts and Cloudflare Registrar Continue reading
Barefoot Preps for 5G and IoT With Its Tofino Chip and the P4 Language
 Paired with the P4 programming language, Barefoot’s Tofino chip gives users the freedom to design what the chip can do.
Paired with the P4 programming language, Barefoot’s Tofino chip gives users the freedom to design what the chip can do.
Alphabet’s Chronicle Launches VirusTotal Enterprise With 100x Faster Malware Search
 VirusTotal also has new capabilities to help companies’ threat intelligence teams better analyze massive amounts of data.
VirusTotal also has new capabilities to help companies’ threat intelligence teams better analyze massive amounts of data.
Security Best Practices for Cloud-Native and Hybrid Cloud Organizations
 Both cloud-native and traditional organizations must implement a security practice that offers automation, abstraction, flexibility, visibility, and is application-aware.
Both cloud-native and traditional organizations must implement a security practice that offers automation, abstraction, flexibility, visibility, and is application-aware.
Buyer’s Guide: Modern Web-Scale Backup and Recovery
 The Buyer’s Guide to Modern Backup is the definitive resource to help you make the right choice for your next data protection solution. Download the buyer's guide today.
The Buyer’s Guide to Modern Backup is the definitive resource to help you make the right choice for your next data protection solution. Download the buyer's guide today.