Delivering a Serverless API in 10 minutes using Workers
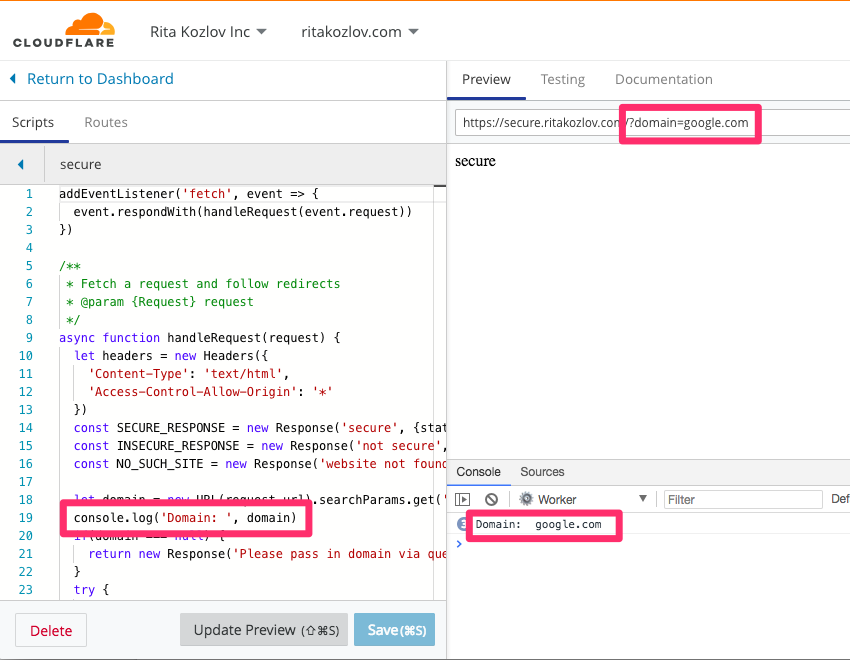
In preparation for Chrome’s Not Secure flag, which will update the indicator to show Not Secure when a site is not accessed over https, we wanted people to be able to test whether their site would pass. If you read our previous blog post about the existing misconceptions around using https, and preparing your site, you may have noticed a small fiddle, allowing you to test which sites will be deemed “Secure”. In preparation for the blog post itself, one of our PMs approached me asking for help making this fiddle come to life. It was a simple ask: we need an endpoint which runs logic to see if a given domain will automatically redirect to https.
The logic and requirements turned out to be very simple:
Make a serverless API endpoint
Input: domain (e.g. example.com)
Output: “secure” / “not secure”
Logic:
if http://example.com redirects to https://example.com
Return “secure”
Else
Return “not secure”
One additional requirement here was that we needed to follow redirects all the way; sites often redirect to http://www.example.com first, and only then redirect to https. That is an additional line of code I was prepared to handle.
I’ve done some Continue reading
Jask Raises $25M Series B Funding for Autonomous Security Platform
 This brings its total to $39 million. Kleiner Perkins led the funding round with participation from Battery Ventures, Dell Technologies Capital, TenEleven Ventures, and Vertical Venture Partners.
This brings its total to $39 million. Kleiner Perkins led the funding round with participation from Battery Ventures, Dell Technologies Capital, TenEleven Ventures, and Vertical Venture Partners.
NSX Cloud Blog Series Part 2: A Consistent Security Posture Across Your Hybrid Cloud
We now dig deeper into the cloud security use-case. As more and more companies embrace cloud, the cloud IT teams are tasked with the responsibility of ensuring that these cloud deployments are secure. Cloud inherently brings in new environments, and these cloud security teams are now faced with ensuring Enterprise security policy consistency across these multiple disparate cloud environments.
VMware NSX Cloud addresses these challenges, offering a common security and micro-segmentation platform across the on-premises and cloud environment. Together with NSX Data Center, it provides a single pane of glass to provision and manages consistent security controls not only for cross-cloud communication but also within each cloud.
Let’s start with VISIBILITY. You can’t protect what you can’t see. As a cloud infrastructure/security team, you may have to manage 1 AWS cloud account (subscription in Azure) and 1 AWS VPC (VNET in Azure) … or you may be managing 500+ accounts/subscriptions, each having multiple VPCs / VNETs. As cloud deployments bring automation and higher levels of agility, the cloud footprint that you would be responsible for can quickly become large and constantly evolve. How do you ensure that this dynamic environment is secure?
Focused on this specific Continue reading
T-25 days until Chrome starts flagging HTTP sites as “Not Secure”
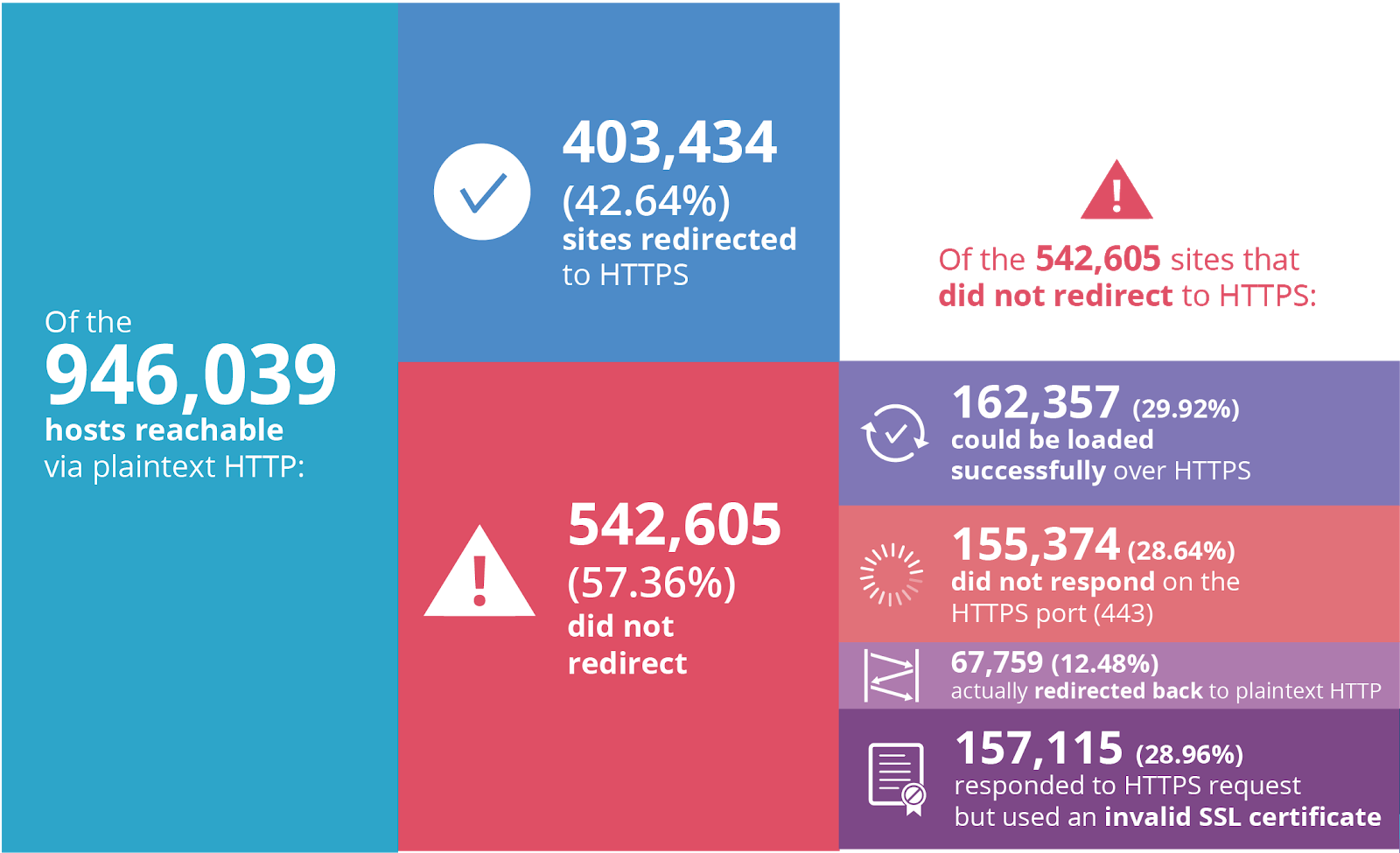
Less than one month from today, on July 23, Google will start prominently labeling any site loaded in Chrome without HTTPS as "Not Secure".
When we wrote about Google’s plans back in February, the percent of sites loaded over HTTPS clocked in at 69.7%. Just one year prior to that only 52.5% of sites were loaded using SSL/TLS—the encryption protocol behind HTTPS—so tremendous progress has been made.
Unfortunately, quite a few Continue reading
Lessons from nPetya one year later
This is the one year anniversary of NotPetya. It was probably the most expensive single hacker attack in history (so far), with FedEx estimating it cost them $300 million. Shipping giant Maersk and drug giant Merck suffered losses on a similar scale. Many are discussing lessons we should learn from this, but they are the wrong lessons.An example is this quote in a recent article:
"One year on from NotPetya, it seems lessons still haven't been learned. A lack of regular patching of outdated systems because of the issues of downtime and disruption to organisations was the path through which both NotPetya and WannaCry spread, and this fundamental problem remains."This is an attractive claim. It describes the problem in terms of people being "weak" and that the solution is to be "strong". If only organizations where strong enough, willing to deal with downtime and disruption, then problems like this wouldn't happen.
But this is wrong, at least in the case of NotPetya.
NotPetya's spread was initiated through the Ukraining company MeDoc, which provided tax accounting software. It had an auto-update process for keeping its software up-to-date. This was subverted in order to deliver the initial NotPetya Continue reading
John Chambers’ VC Firm Backs Security Startup Balbix’s $20M Series B
 Cavium, Nutanix, and Equinix are all customers using the security company’s predictive breach-risk platform.
Cavium, Nutanix, and Equinix are all customers using the security company’s predictive breach-risk platform.
Secure coding practices in Java: challenges and vulnerabilities
Secure coding practices in Java: challenges and vulnerabilities Meng et al., ICSE’18
TL;DR : don’t trust everything you read on Stack Overflow.
Meng et al. conduct a study of Stack Overflow posts relating to secure coding practices in Java to find out the hot topics, what people struggle with, and whether or not the accepted answers are actually following security best practices.
We conducted an empirical study on Stack Overflow posts, aiming to understand developer’s concerns on Java secure coding, their programming obstacles, and insecure coding practices. We observed a wide adoption of the authentication and authorization features provided by Spring Security — a third-party framework designed to secure enterprise applications…
Well, how could I resist reading that! (Some readers may know that I was for many years the CTO of SpringSource). Spring Security does come in for some flak in this paper for the high volume of questions that are asked relating to it. There’s no calibration though for underlying popularity. One of the reasons there are a lot of questions, I posit, is that there are an awful lot of users of Spring Security. Spring Boot applications will use Spring Security, and Spring Boot has been growing Continue reading
Pulse Secure Elevates vADC Assets to Google Cloud
 The vADC uses central management tools to accelerate service deployment and increase security, scalability, and resiliency of applications as enterprises migrate to the cloud.
The vADC uses central management tools to accelerate service deployment and increase security, scalability, and resiliency of applications as enterprises migrate to the cloud.
Ping Identity Buys API Security Startup Elastic Beam
 Ping Identity also launched a new product that builds on Elastic Beam’s technology, as well as its own API security product, and uses AI to identify and block attacks targeting API infrastructures in public and hybrid clouds.
Ping Identity also launched a new product that builds on Elastic Beam’s technology, as well as its own API security product, and uses AI to identify and block attacks targeting API infrastructures in public and hybrid clouds.
NIC.BR and the Internet Society Work Together to Increase Routing Security in Brazil
This week on Tuesday, 26 June, the Internet Society and NIC.BR signed a Memorandum of Understanding (MoU) to work together to increase routing security in Brazil, including the MANRS initiative. Mutually Agreed Norms for Routing Security is a global initiative that provides crucial fixes to reduce the most common routing threats.
We are excited to strengthen our efforts to work together with NIC.br, and in fact this MoU only formalizes an existing long-term relationship between the two organizations. Our goal is to help increase the number of Brazilian Internet Service Providers and Internet Exchange Points joining efforts for a more secure and resilient Internet.
Not a single day goes by without dozens of incidents affecting the Internet’s routing system. Route hijacking, route leaks, IP address spoofing, and other harmful activities can lead to Denial of Service (DoS) attacks, traffic inspection and surveillance, lost revenue, reputational damage, and more. As one of the biggest countries with high access rates, Brazil is also facing these incidents on a daily basis.
NIC.BR is responsible for the coordination and integration of all Internet service initiatives in Brazil, including long-standing activities related to Internet security. They are also responsible for many projects that Continue reading
At IETF 102: The Global Commission on the Stability of Cyberspace – Cyber diplomacy meets InfoSec and Technology
On Tuesday, 17 July, during IETF 102 in Montreal, the Global Commission on the Stability of Cyberspace (GCSC) will host a lunch panel on “Cyber Diplomacy Meets InfoSec and Technology.” During this session, the Commission wants to inform and engage with the IETF community on its work so far and the work that is in the pipeline.
The Global Commission on the Stability of Cyberspace is developing norms and policy initiatives that intend to counter the risk to the overall security and stability of cyberspace due to rise of offensive cyber-activities, and especially those by states.
Session Abstract
In this global environment we see conflict between states takes new forms, and cyber-activities are playing a leading role. There is an increasing risk of undermining the peaceful use of cyberspace and a growing for need norms and policies to enhance international security and stability.
The Global Commission on the Stability of Cyberspace, with commissioners from diverse backgrounds, sets out to develop proposals for norms and policies to enhance international security and stability and guide responsible state and non-state behavior in cyberspace.
During this lunch panel we want to engage with the IETF community to discuss the norms the commission Continue reading
Silver Peak Raises $90M From TCV to Accelerate SD-WAN Growth
 Silver Peak differentiates itself from other SD-WAN vendors with its Unity EdgeConnect SD-WAN physical or virtual appliance.
Silver Peak differentiates itself from other SD-WAN vendors with its Unity EdgeConnect SD-WAN physical or virtual appliance.
Is DevSecOps the Answer to Securing the Hybrid Cloud?
 DevSecOps automates core security tasks by embedding security controls and processes into DevOps, thus baking security into the code.
DevSecOps automates core security tasks by embedding security controls and processes into DevOps, thus baking security into the code.
Transform Your Branch Locations by Going Direct-to-Internet
 A new white paper from Zscaler discusses the importance of beginning your branch transformation journey with a solution designed and built to support a cloud-first enterprise
A new white paper from Zscaler discusses the importance of beginning your branch transformation journey with a solution designed and built to support a cloud-first enterprise
If We Care About the Internet, We Have to Be Willing to Do Our Part
Whether it’s playing dungeons and dragons over voice chat with my college friends hundreds of miles away, reading the latest movie reviews for summer blockbusters I’ll watch once they come out on video, or simply paying electrical bills, the Internet has become an important part of my life.
Yet, while I have come to rely on the Internet, I don’t always do what is best for it.
I don’t always patch my connected devices or applications, leaving them vulnerable to compromise and use in a botnet. I don’t look for security when buying an app or a device, let alone look at the privacy policies.
While I know I am hurting the overall security of the Internet, I find myself thinking, “I’m just one person, how much damage could I do?”
Unfortunately, according to one recent survey, there are a lot of people who act just like me.
The results from the 2018 CIGI-Ipsos Global Survey on Internet Security and Trust* suggest that many users fail to make security a priority as they shop for Internet of Things (IoT) devices. (IoT refers to “scenarios where network connectivity and computing capability extends to objects, sensors and everyday items not normally considered computers, allowing these devices to generate, exchange and consume data with minimal human Continue reading
SMB version detection in masscan
My Internet-scale port scanner, masscan, supports "banner checking", grabbing basic information from a service after it connects to a port. It's less comprehensive than nmap's version and scripting checks, but it's better than just recording which ports are open.Routing Security & IPv6 at NANOG 73 in Denver
We’ll be at NANOG 73 in Denver, CO, USA this week talking about routing security, MANRS, and IPv6.
The North American Network Operators Group (NANOG) is the professional association for Internet engineering, architecture and operations. Its core focus is on continuous improvement of the data transmission technologies, practices, and facilities that make the Internet function. NANOG meetings are among the largest in the region, bringing together top technologists on a wide range of topics.
Routing Security
On Tuesday, 26 June, at 1:30PM, Andrei Robachevsky will give a talk called, “Routing Is At Risk. Let’s Secure It Together.”
From the session abstract:
“Stolen cryptocurrency, hijacked traffic blocking access to whole countries, derailing vital Web resources for thousands of people. Routing used to fly under the radar. As long as incidents weren’t too bad, no one asked too many questions, and routing security never made it to the top of the to-do list. But these days, routing incidents are regularly making the news, executives are getting nervous, and engineers are under pressure to make sure their network isn’t next. The problem is, you cannot secure your own network entirely by yourself. But you can help secure the global routing system Continue reading
Watch Live On Monday, 25 June – DNSSEC Workshop at ICANN 62 in Panama
With the DNSSEC Root Key Rollover coming up on October 11, how prepared are we as an industry? What kind of data can we collect in preparation? What is the cost benefit (or not) of implementing DANE? What can we learn from an existing rollover of a cryptographic algorithm?
All those questions and more will be discussed at the DNSSEC Workshop at the ICANN 62 meeting in Panama City, Panama, on Monday, June 25, 2018. The session will begin at 9:00 and conclude at 12:15 EST (UTC-5). [Note: this is one hour different than current US Eastern Daylight Time – Panama does not change to daylight savings time – and so this will begin at 10:00 EDT (UTC-4).]
The agenda includes:
- DNSSEC Workshop Introduction, Program, Deployment Around the World – Counts, Counts, Counts
- Panel: DNSSEC Activities and Post Key Signing Key Rollover Preparation
- DANE: Status, Cost Benefits, Impact from KSK Rollover
- An Algorithm Rollover (case study from CZ.NIC)
- Panel: KSK Rollover Data Collection and Analysis
- DNSSEC – How Can I Help?
- The Great DNSSEC/DNS Quiz
It should be an outstanding session! For those onsite, the workshop will be in Salon 4, the ccNSO room.
Announcing NDSS 2019 & the Call for Papers
It may seem far away, but it’s time to begin planning for the 26th Network and Distributed System Security Symposium. NDSS 2019 will once again be held in sunny San Diego at the lovely Catamaran Spa and Resort from 24-27 February 2019.
This annual security symposium is a premiere venue for fostering information exchange among researchers and practitioners of network and distributed system security. The target audience includes those interested in practical aspects of network and distributed system security, with a focus on actual system design and implementation. A major goal is to encourage and enable the Internet community to apply, deploy, and advance the state of available security technologies.
NDSS 2019 will have a new General Chair, Dr. Trent Jaeger of Pennsylvania State University. In addition, the Program Committee for NDSS 2019 is being chaired by Dr. Alina Opera of Northeastern University and Dr. Dongyan Xu of Purdue University. Additional positions will be announced in the coming weeks.
Most importantly for all you researchers out there, the NDSS 2019 Call for Papers has been released. As in years past, the focus of the symposium will be the many aspects of security and privacy including the security of emerging Continue reading
Automated localization for unreproducible builds
Automated localization for unreproducible builds Ren et al., ICSE’18
Reproducible builds are an important component of integrity in the software supply chain. Attacks against package repositories and build environments may compromise binaries and produce packages with backdoors (see this report for a recent prominent example of compromised packages on DockerHub). If the same source files always lead to the same binary packages, then an infected binary can be much more easily detected. Unfortunately, reproducible builds have not traditionally been the norm. Non-determinism creeping into build processes means that rebuilding an application from the exact same source, even within a secure build environment, can often lead to a different binary.
Due to the significant benefits, many open-source software repositories have initiated their validation processes. These repositories include GNU/Linux distributions such as Debian and Guix, as well as software systems like Bitcoin.
If you have a non-reproducible build, finding out why can be non-trivial. It takes time and a lot of effort to hunt down and eradicate the causes. For example, Debian unstable for AMD64 still had 2,342 packages with non-reproducible builds as of August 2017. (The number today as I’m writing this is 2,826). You can see a stubbornly persistent Continue reading