Cisco Says VPNFilter Attacks Bigger and Badder Than Originally Thought
 Newly discovered capabilities mean hackers can snoop on web traffic and execute man-in-the-middle attacks before killing the device.
Newly discovered capabilities mean hackers can snoop on web traffic and execute man-in-the-middle attacks before killing the device.
Pivotal Container Service (PKS) Integration With NSX-T Data Center: A lab study with Tips
Contributions from: Alka Gupta, Prasad Kalpurekkal
Pivotal Container Service (PKS) aims to simplify how enterprises deploy, run and manage Kubernetes clusters on any cloud. For detailed documentation of PKS installation and configuration, go here. For details on configuring PKS with NSX-T Data Center, go here.
Every enterprise wants to run containers in production. However, primary questions being asked are: “How do I get Kubernetes to work in my data center? How do I simplify deployment of Kubernets clusters? What about Networking and Security? ”
PKS answers these questions with a feature set tailored to the requirements of the enterprises. Read about PKS features in detail here.
One of the features PKS offers is tight integration with NSX-T Data Center, enabling advanced networking and security for container based emerging application architectures, just as it does for traditional 3-tier apps. In these environments, NSX-T Data Center provides Layer 3 container networking and advanced networking services such as built-in load balancing, micro-segmentation, multi-tenancy, central visibility with a central SDN controller, network topology choices and more. We demonstrated this at the Network Field Day 17 which you can see here.
In this blog, we call out the work done at VMware Global Solutions Partner lab on configuring Pivotal Continue reading
Fortinet Buys Bradford Networks, Adds Machine Learning to Its Web Application Firewall
 Machine learning allows Fortinet’s WAF to provide almost 100 percent application threat detection accuracy without requiring additional fine tuning, the company claims.
Machine learning allows Fortinet’s WAF to provide almost 100 percent application threat detection accuracy without requiring additional fine tuning, the company claims.
CA Technologies Rolls Out Cloud Partnership With IBM, Application Security Update
 VMware is a customer using the application security product, which allows companies to use open source libraries to speed software development without adding unmanaged risk.
VMware is a customer using the application security product, which allows companies to use open source libraries to speed software development without adding unmanaged risk.
Announcing General Availability of VMware NSX-T Data Center 2.2.0
VMware is pleased to announce that VMware NSX-T Data Center 2.2.0 has been released on June 5, 2018!
With this release we have introduced a number of excellent new features for on-premise deployments as well as the ability to manage Microsoft Azure based workloads as part of the NSX Cloud product. VMware NSX-T Data Center has also been updated to provide networking and security infrastructure for VMware Cloud on AWS.
Here is list of highlighted features that may be of most interested to customers. Note that this is not a complete list of new features. Please see the release notes for this release for all of the details.
Management of Workloads in Microsoft Azure
One of the most interesting new features of NSX-T Data Center 2.2 is the enablement of NSX Cloud, managing networking and security for applications running natively in public clouds, now including Microsoft Azure. This feature enables a true hybrid cloud with management of network security in a single view. This feature is detailed well in the following blog by Jonathan Morin so instead of repeating all the details here it is highly recommended you review this page: https://blogs.vmware.com/networkvirtualization/2018/06/nsx-cloud-a-new-and-improved-model-for-end-to-end-networking-and-security.html/
Enhanced Data Path Mode in N-VDS
G7 Leaders, the World is looking at you to make the right decisions
As Canadian Prime Minister Justin Trudeau gets ready to host the G7 Summit this week, renewed tensions around trade remind us how vulnerable the global economy is, and how working together is more important than ever to solve these complex issues.
And today, the world is looking to G7 leaders to make the right decisions.
The connected future is here. While the Internet has yet to reach its full potential (half of the world’s population remains offline), there’s little doubt that it’s already changing the landscape of trade, jobs, and the digital economy. According to data from McKinsey, the Internet accounts on average for 3.4 % GDP across the large economies that make up 70 % of global GDP. The global network offers a unique space where data, goods and services can flow and fuel the next wave of global growth, where anyone can take part and benefit from new economic opportunities.
One of the values of this connected world is our ability to interconnect — the way we live our lives, the way we socialize, and we interact with the world. Everything from clothes to toys and toothbrushes are coming online as well. The International Data Continue reading
White Paper: Secure and Cost-Effective Digital Transformation
 A new white paper from Zscaler introduces a powerful solution for providing an efficient and secure experience between users and cloud/SaaS.
A new white paper from Zscaler introduces a powerful solution for providing an efficient and secure experience between users and cloud/SaaS.
Related Stories
Watch live – June 6 panel on “Innovation, security, and the Internet of Things (IoT)” in Ottawa
As a side event before the 2018 G7 Summit this week in Canada, tomorrow, 6 June 2018, the Internet Society will hold a panel to not only talk about the risks and opportunities the Internet of Things (IoT) brings, but also what policy makers can do to build a connected future for everyone.
The panel, Innovation, security, and the Internet of Things, will take place in Ottawa Ontario. If you’re in Ottawa, you can join us from 7:30 to 9:30 a.m. on Wednesday, 6 June, at the Alt Hotel Ottawa at 185 Slater St. If you’re somewhere else, the event will be
livestreamed.
Moderator David Akin (Global News) will facilitate a discussion between:
- Jeff Wilbur, Director, Online Trust Alliance
- Katie Watson, Policy Advisor, Internet Society
- Jacques Latour, Chief Technology Officer, Canadian Internet Registration Authority
- Mike Hoye, Engineering Community Manager, Mozilla
While the opportunities these connected devices can bring us are virtually unprecedented, the steps we must go through to protect ourselves online can feel overwhelming. At the Internet Society, we believe in a future where manufactures, software developers and service providers put people first and ensure user’s privacy and security is their top priority.
To understand Continue reading
Amazon, Google Vulnerable to Zip Slip, Says Snyk Security Research
 The security startup maintains a massive database of vulnerabilities in open source libraries.
The security startup maintains a massive database of vulnerabilities in open source libraries.
Integrating 3rd Party Firewalls with Amazon Web Services (AWS) VPC Networking
After figuring out how packet forwarding really works within AWS VPC (here’s an overview, the slide deck is already available to ipSpace.net subscribers) the next obvious question should be: “and how do I integrate a network services device like a next-generation firewall I have to use because $securityPolicy into that environment?”
Please don’t get me started on whether that makes sense, that’s a different discussion.
Christer Swartz, an old-time CCIE and occasional guest on Software Gone Wild podcast will show you how to do it with a Palo Alto firewall during my Amazon Web Services Networking Deep Dive workshop on June 13th in Zurich, Switzerland (register here).
Palo Alto Networks Replaces CEO With Former Google Exec Nikesh Arora
 The company wanted an accomplished business leader who has experience with large-scale platforms.
The company wanted an accomplished business leader who has experience with large-scale platforms.
Securing with NSX – Beyond the DevSecOps Paradigm
There are two digital explosions simultaneously happening in enterprises across all verticals. Enterprises are moving at a breakneck speed on every aspect of their business. From managing their supply-chain, making purchasing decisions, targeted marketing campaign to users, creating apps to connect with users and making it easier for users to consume their products.
The good news is technology is keeping pace and is a step ahead in helping the business achieve their goals. These business imperatives are forcing software iterations to be faster and be more efficient. This is leading to newer innovative models around people/processes/tools that we collectively call Continuous Integration(CI)/Continuous Development (CD). Teams leading the charge on CI/CD models are working in a “DevOps” model.
The second explosion is related to the first explosion. As complex software become easy-to-use and be ubiquitous, sophisticated tools can be used to attack enterprises. Managing Security is getting harder. Last decade – there was a belief – I am not going to be attacked. Fast forward today – enterprises expect to be attacked and breached. This is not just a baseless impression. Forrester’s 2018 survey shows that 66% of survey respondents have faced a major security incident.

”It’s kind Continue reading
VMware’s Future Is Networking, CEO Pat Gelsinger Says
 In addition to NSX, the company’s software-defined storage and hyperconverged products also saw strong growth during the first quarter of its fiscal 2019.
In addition to NSX, the company’s software-defined storage and hyperconverged products also saw strong growth during the first quarter of its fiscal 2019.
FBI Blames North Korea for Malware, Kaspersky Lawsuits Dismissed
 The two malware families target U.S. media, aerospace, financial, and critical infrastructure sectors’ networks.
The two malware families target U.S. media, aerospace, financial, and critical infrastructure sectors’ networks.
The First Lady’s bad cyber advice
First Lady Melania Trump announced a guide to help children go online safely. It has problems.Melania's guide is full of outdated, impractical, inappropriate, and redundant information. But that's allowed, because it relies upon moral authority: to be moral is to be secure, to be moral is to do what the government tells you. It matters less whether the advice is technically accurate, and more that you are supposed to do what authority tells you.
That's a problem, not just with her guide, but most cybersecurity advice in general. Our community gives out advice without putting much thought into it, because it doesn't need thought. You should do what we tell you, because being secure is your moral duty.
This post picks apart Melania's document. The purpose isn't to fine-tune her guide and make it better. Instead, the purpose is to demonstrate the idea of resting on moral authority instead of technical authority.
<-- --="" more="">
Strong Passwords
"Strong passwords" is the quintessential cybersecurity cliché that insecurity is due to some "weakness" (laziness, ignorance, greed, etc.) and the remedy is to be "strong".
The first flaw is that this advice is outdated. Ten years ago, important websites would frequently get hacked and Continue reading
APNIC Labs/CloudFlare DNS 1.1.1.1 Outage: Hijack or Mistake?
At 29-05-2018 08:09:45 UTC, BGPMon (A very well known BGP monitoring system to detect prefix hijacks, route leaks and instability) detected a possible BGP hijack of 1.1.1.0/24 prefix. Cloudflare Inc has been announcing this prefix from AS 13335 since 1st April 2018 after signing an initial 5-year research agreement with APNIC Research and Development (Labs) to offer DNS services.
Shanghai Anchang Network Security Technology Co., Ltd. (AS58879) started announcing 1.1.1.0/24 at 08:09:45 UTC, which is normally announced by Cloudflare (AS13335). The possible hijack lasted only for less than 2min. The last announcement of 1.1.1.0/24 was made at 08:10:27 UTC. The BGPlay screenshot of 1.1.1.0/24 is given below:

Anchang Network (AS58879) peers with China Telecom (AS4809), PCCW Global (AS3491), Cogent Communications (AS174), NTT America, Inc. (AS2914), LG DACOM Corporation (AS3786), KINX (AS9286) and Hurricane Electric LLC (AS6939). Unfortunately, Hurricane Electric (AS6939) allowed the announcement of 1.1.1.0/24 originating from Anchang Network (AS58879). Apparently, all other peers blocked this announcement. NTT (AS2914) and Cogent (AS174) are also MANRS Participants and actively filter prefixes.
Dan Goodin (Security Editor at Ars Technica, who extensively covers malware, computer espionage, botnets, and hardware hacking) reached Continue reading
French Hosting Provider Fends Off DDoS Attacks With NetScout vAPS
 As a hosting provider, Jaguar Networks has a higher risk of DDoS attacks because it aggregates its customers' risks in a shared infrastructure.
As a hosting provider, Jaguar Networks has a higher risk of DDoS attacks because it aggregates its customers' risks in a shared infrastructure.
New Features of Docker Enterprise Edition 2.0 – Top 12 Questions from the Docker Virtual Event
In the recent Docker Virtual Event, Unveiling Docker Enterprise Edition 2.0, we demonstrated some of the key new capabilities of the Docker Enterprise Edition – the enterprise-ready container platform that enables IT leaders to choose how to cost-effectively build and manage their entire application portfolio at their own pace, without fear of architecture and infrastructure lock-in. Designed to address enterprise customers’ needs, these net-new features extend across both Swarm and Kubernetes (Part 1 of this blog) and across Windows and Linux applications (Part 2 of this blog).
In this blog post, we’ll go over some of the most common questions about these new features as well as some of the common questions that were asked about how Docker Enterprise Edition is packaged and deployed.
If you missed the live event, don’t worry! You can still catch the recording on-demand here.
Docker Enterprise Edition 2.0 Features
Q: Can I connect my corporate directory to permissions inside Docker Enterprise Edition?
A: Yes! You can integrate your corporate LDAP or Active Directory to Docker Enterprise Edition. Permissions can be mapped to one of the 5 built-in roles or administrators can create very granular and flexible Continue reading
Extending the Power of NSX to Bare-metal Workloads
Authors – Sridhar Subramanian and Geoff Wilmington
VMware NSX Data Center was built with the goal of consistent networking and security services independent of changing application frameworks or physical infrastructure. In the last couple of years, NSX Data Center has focused on delivering network and security abstractions for applications on any compute platform. In our journey, we have handled VM’s, containers, cloud, and now we are also looking to help our customers with scenarios where they need a unified experience for bare-metal workloads. The goal being to maintain a consistent security experience regardless of location or platform the workload is running on.
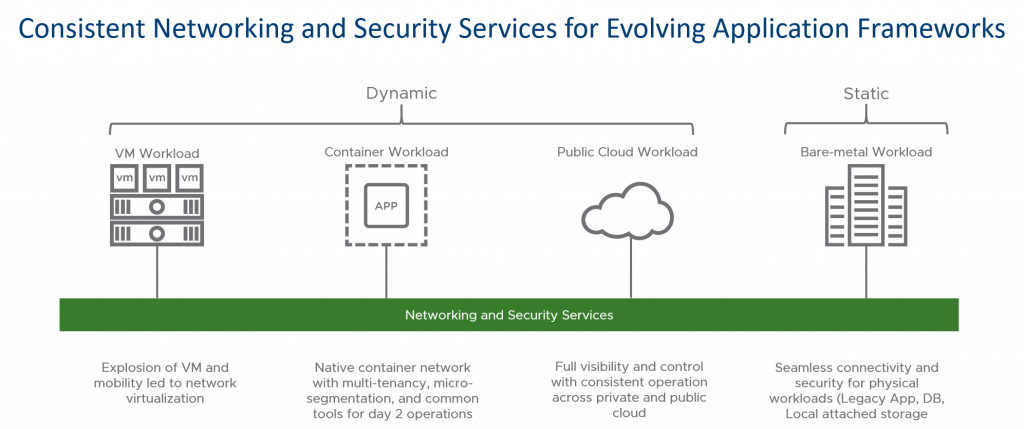
This experience means being able to take any workload, add it to an NSX Data Center Security Group and through the NSX Data Center Distributed Firewall have a consistent policy applied regardless of location and workload type. This consistent approach leverages the NSX DFW capabilities with stateful firewalling for the workloads. This is accomplished outside of using native OS capabilities like IP Tables or Windows Firewall so security admins only need to understand how to apply security through NSX DFW, and not have to understand the myriad of native OS approaches and complexity. By centralizing Continue reading
To Tackle the VPNFilter Botnet, It’s Going to Take Help from You and Me
If you’ve been reading the news lately, you might have seen headlines like “FBI to America: Reboot Your Routers, Right Now” or “F.B.I.’s Urgent Request: Reboot Your Router to Stop Russia-Linked Malware”. These headlines can be pretty alarming, and you may find yourself thinking, “things must be pretty bad if the FBI is putting out such an urgent warning.”
Cyber threats are not uncommon, but the good news is that the security community is working around the clock to tackle these threats as early and quickly as possible. Most of the time we do not see all this hard work, nor are we often asked to play a large part in taking down a botnet. But this time, by rebooting our routers, we can help the law enforcement and information security communities to identify infected routers so they can be cleaned up, moving us closer to a permanent fix for a particular kind of malware – VPNFilter.
Here is what happened …
From Discovery to Takedown
On 23 May, 2018, researchers at Cisco’s Talos publicly shared their findings about a large botnet of infected networking devices (home routers) they called “VPNFilter” because of concerns that the Continue reading
