Ansible Tower Advanced Smart Inventory Usage

Background
Smart Inventory is a feature that was added to Red Hat Ansible Tower 3.2. The feature allows you to generate a new Inventory that is made of up hosts existing in other Inventory in Ansible Tower. This inventory is always-up-to-date and is populated using what we call a host filter. The host filter is a domain specific query language that is a mix of Django Rest Framework GET query language with a JSON query syntax added in. Effectively, this allows you create an Inventory of Hosts and their relational fields as well as related JSON structures.
The ansible_facts field is a related field on a Host that is populated by Job Template runs (Jobs) that have fact caching enabled. Ansible Tower bolts on an Ansible fact cache plugin with Job Template that have fact caching enabled. Job Templates of this kind that run playbooks that invoke Ansible gather_facts will result in those facts being saved to the Ansible Tower database when the Job finishes.
A limitation of the Smart Inventory filter is that it only allows equality matching on ansible_fact JSON data. In this blog post I will show you how to overcome this limitation and add Continue reading
Business Solutions at AnsibleFest

I’ve always enjoyed listening to how customers are solving their business challenges using Red Hat Ansible Automation. From the simple to the uniquely creative solutions, they’re always fun to hear. So every time AnsibleFest comes around, I get especially excited knowing that I’ll have the chance to hear far more than one or two stories.
This year’s AnsibleFest in Austin is expected to be the biggest ever. To cater for the many different interests of attendees, we’ve created six specific tracks with curated content sure to interest. I’ve managed to “bag” the Business Solutions track, which will contain ten talks in total.
Sifting through the hundreds of submissions (the job gets harder every year!) I’ve picked out three talks which I’m really looking forward to listening to.
1. Upgrading the backend database of a £3 billion business website on a Friday afternoon
However that panned out, it’s sure to be a great story! I’m grabbing some popcorn for this one :)
2. Using Ansible to Satisfy Compliance Controls
Security automation is a big topic these days, and the security community has come to realise the power in Ansible to help them get things done. I’ve lost count of the Continue reading
Docker at Microsoft Ignite 2018
Docker will be at Microsoft Ignite in Orlando, FL the week of Sept 24th to showcase the latest release of Docker Enterprise. Specifically, we will be sharing insights for how to move your legacy Windows applications from Windows Server 2003/2008 to Windows Server 2016 and Azure.
Visit Docker in Booth #644 to learn more about how we’re helping IT org anizations learn about Docker Enterprise tools that help you to id and containerize Windows legacy applications. We’ll have technical experts there to answer your questions.
anizations learn about Docker Enterprise tools that help you to id and containerize Windows legacy applications. We’ll have technical experts there to answer your questions.
Make sure to check out these sessions featuring Docker:
- From Ops to DevOps with Windows Containers and Windows Server 2019. Specifically we are highlighting Lindsay, a joint Docker Microsoft customer that has migrated Windows legacy apps with Docker Enterprise to Azure. You can get more details about the session here.
- Thursday 9/27 @ 2pm: HPE Theatre in the HPE booth #2125. The session will focus on how Docker Enterprise is helping customers migrate their legacy apps and run them in a hybrid environment.
- Get a Hands on Tutorial at the Docker User Group
Docker is also partnering with Docker Captains in Orlando to deliver a hands-on lab focused on migrating a legacy Continue reading
Windows Server 2008 Cutoff: How Docker Enterprise Cures Migration Headaches
The coming end-of-support for Windows Server 2008 is the perfect opportunity for IT organizations to tap Docker Enterprise to modernize and secure legacy applications while saving millions in the process.
THE END IS NIGH (FOR WINDOWS SERVER 2008)
The coming end-of-support for Windows Server 2008 in January 2020 leaves IT organizations with a few viable options: migrate to a supported operating system (OS), rehost in Azure, or pay for an extended support contract (up to 75% of the license fee per year) to receive security updates beyond the cut-off date. The option of doing nothing (running applications on unsupported OS versions) is a non-starter for the vast majority of businesses, as this poses a significant security and compliance risk. We saw the impact of this last year when a massive ransomware attack that affected nearly 100 countries spread by targeting end-of-life and unpatched systems.
THE APPLICATION MIGRATION MIGRAINE
Upgrading will be no small feat as roughly 80% of all enterprise applications run on Windows Server. Of those applications, 70% still run on Windows Server 2008 or earlier versions*. Migrating all of these critical applications to a supported version of Windows Server is painful and costly, due to rigid legacy Continue reading
Windows XP OpenVPN TAP installation, “devcon.exe failed”
Although this article mainly targets OpenVPN TAP driver installation issue, The problem is likely not limited to that specific driver.
You may want to continue reading and give the very easy solution at the end of the article a try.
Recently I had to install OpenVPN on a system running Windows XP (Don’t ask). The installation went smoothly up until TAP driver installation and then suddenly things went haywire:
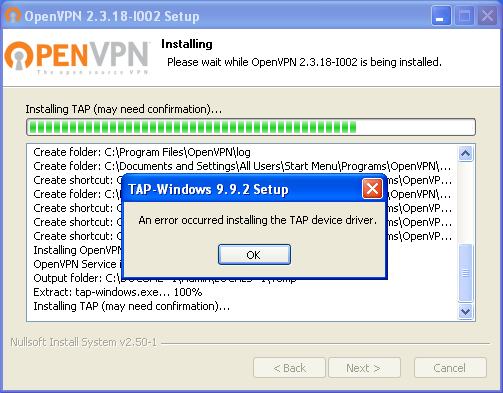
An error occurred installing the TAP device driver
The yellow marked status with the code of 28 in the device manager was not promising either:
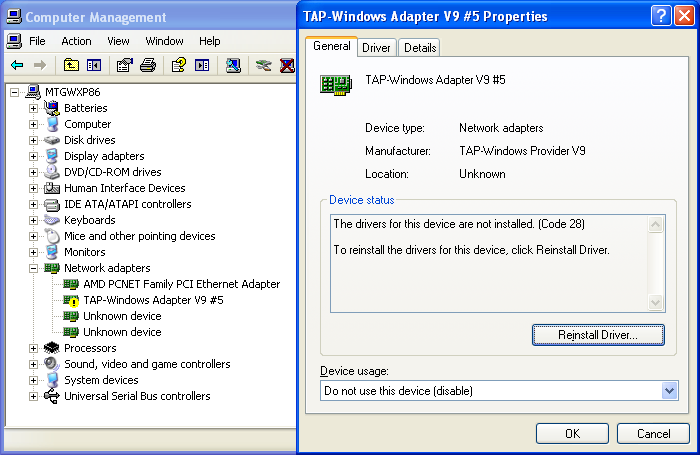
The drivers for this device are not installed. (Code 28)
In Windows XP, to install its inf file, TAP driver installation uses the built-in Windows Device Console (Devcon.exe). Pretty simple stuff, you just use devcon.exe with the install argument, supply the inf file and then provide the device’s Hardware ID.
This is the command being used to install each TAP NIC:
"C:\Program Files\TAP-Windows\bin\devcon.exe" install "C:\Program Files\TAP-Windows\driver\OemWin2k.inf" tap0901
Which gave a mundane error:
devcon.exe failed.
Devcon however, leaves a log file of its operation behind in %windir%\setupapi.log which included these lines:
#E122 Device install failed. Error 2: The system cannot find Continue reading
5 Reasons to Attend DockerCon

Are you ready to get started with Docker and containers or level up your current use?
Join the Docker team, the container ecosystem, contributors and maintainers, developers, IT professionals and executives at DockerCon Barcelona December 3-5. DockerCon is the must attend conference to learn, network and innovate with the container industry.
Besides Barcelona being a beautiful city with delicious food, here are our top 5 reasons to attend DockerCon:
- Think big. Docker containers and our container platform are being used everywhere for everything. Your possibilities are endless, from sending rockets to space to literally save the earth from asteroids, to running intensive genomics analysis to find cures for diseases or keeping e-commerce running smoothly for black Friday shoppers. Come to DockerCon and imagine your digital future.
- Start small. The promise of containerization is big, but the sheer volume of options can be intimidating. If you don’t know where to start, don’t worry. DockerCon has a path for you for each stage of the journey: from getting started, to launching your first project, to scaling out your environment, to building some new and innovating.
- The. Best. Content. DockerCon is known for its amazing speakers who deliver real takeaways and lessons learned. Continue reading
Get to Know Docker Desktop
Today on the Edge release channels, we released a new beta version of Docker Desktop, the product formerly known as Docker for Windows and Docker for Mac. You can download this new Edge release for both Windows and macOS. Docker Desktop enables you to start coding and containerizing in minutes and is the easiest way to run Docker Engine, Docker Swarm and Kubernetes on Mac and Windows. In addition to simple setup, Docker Desktop also includes other great features and capabilities such as:
- Fast edit-test cycles with volume mounting for code and data, including file change notifications.
- If you want to switch from Swarm to Kubernetes for orchestration, it’s a click of a button in the Docker Desktop UI.
- On Windows desktops, you can develop both Windows and Linux containers with Docker Desktop using a toggle selection in the UI.
- Docker Desktop handles the setup and teardown of lightweight VMs on both Windows and macOS, using Hyper-V on Windows desktops and Hyperkit on macOS.
- Built-in enterprise network support allows Docker Desktop to work with choice of VPNs and proxies.
You may have already noticed the new Docker Desktop name on www.docker.com, and over the next few months we Continue reading
How to install LUKS encrypted Ubuntu 18.04.x Server and enable remote unlocking
Much has been changed since my last post about LUKS remote unlock workaround (Particularly, The bug is finally fixed in cryptsetup 2:2.0.2-1ubuntu1.1 and no more workaround is needed). This, is the updated version on how to set things up properly.
UPDATE: Well, it turned out that while the previous bug is fixed, another one still exists. You can find the required workaround for it at the end of this article
In this post, I’m going to show you the required steps and downfalls on running a LUKS encrypted Ubuntu Server setup and how it can be extended to allow remote unlocking.
Prerequisites
- A server to install on
- Static public IP address
- The so called Alternative Ubuntu Server installer1
- Some patience ?
Installing and Setting up encrypted LVM
It is assumed that you already know your way around ISO files and how to boot them on your server.
We will also use the simplest possible setup: A server with a single disk
We are going to use LVM inside the LUKS container, it is Continue reading
Running the gcloud CLI in a Docker Container
A few times over the last week or two I’ve had a need to use the gcloud command-line tool to access or interact with Google Cloud Platform (GCP). Because working with GCP is something I don’t do very often, I prefer to not install the Google Cloud SDK; instead, I run it in a Docker container. However, there is a trick to doing this, and so to make it easier for others I’m documenting it here.
The gcloud tool stores some authentication data that it needs every time it runs. As a result, when you run it in a Docker container, you must take care to store this authentication data outside the container. Most of the tutorials I’ve seen, like this one, suggest the use of a named Docker container. For future invocations after the first, you would then use the --volumes-from parameter to access this named container.
There’s only one small problem with this approach: what if you’re using another tool that also needs access to these GCP credentials? In my case, I needed to be able to run Packer against GCP as well. If the authentication information is stored inside a named Docker container (and then accessed Continue reading
Ansible Tower 3.3 Available Now

We're happy to announce that Red Hat Ansible Tower 3.3 is now generally available. In this release, there are a number of enhancements that can help improve the automation in any organization. The team has been hard at work adding functionality with Red Hat OpenShift Container Platform, more granular permissions, scheduler improvements, support for multiple Ansible environments, and many other features.
Here are a few we are excited about!
Ansible Tower + OpenShift Container Platform
Push-button Ansible Tower deployment for Red Hat OpenShift Container Platform users is now here! Ansible Tower 3.3 is now a supported offering on Red Hat OpenShift Container Platform. The new Ansible Tower pod service in Red Hat OpenShift makes it easy to add capacity to Ansible Tower by adding additional pods. This enables users to scale at runtime as needed. Best of all, Ansible Tower is configurable directly from Red Hat OpenShift Container Platform.
- Scale Ansible Tower up and down at runtime as needed
- Add capacity to Ansible Tower by adding additional pods
All configurable directly from the Red Hat OpenShift Container Platform UI, CLI, and API.
More Granular Control
Ansible Tower now allows for even easier configuration of jobs for use Continue reading
Join the Beta for Docker Engine 18.09
A few weeks back, we announced changes to extend the maintenance lifecycle for Docker Engine – Community (CE). As part of these changes, we’re having a beta testing period to deliver a higher-quality engine to the market.
We’d like to invite our community members to now participate in this beta testing by installing the beta package, kicking the tires, and submitting issues.
Docker Engine – Community version 18.09 adds these new features:
- Built on containerd – Docker Engine’s new architecture is based on containerd 1.2 and fully supported through the Kubernetes containerd integration.
- BuildKit is now generally available – Access improved build performance (see slides 22-26) and scalability with the optional BuildKit integration. BuildKit remains opt-in with an environment variable, e.g.
$ DOCKER_BUILDKIT=1 docker build .
You can also set the feature option in /etc/docker/daemon.json to enable BuildKit by default:
{"features":{"buildkit": true}}
- Support for SSH connections to the docker host – The client can now connect to a remote docker daemon via SSH, e.g.
$ docker -H ssh://[email protected]
Install Instructions:
Only install the beta package on a new system without previous versions of docker-ce installed.
$ curl -fsSL test.docker.com Continue reading
Technology Short Take 104
Welcome to Technology Short Take 104! For many of my readers, VMworld 2018 in Las Vegas was “front and center” for them since the last Tech Short Take. Since I wasn’t attending the conference, I won’t try to aggregate information from the event; instead, I’ll focus on including some nuggets you may have missed amidst all the noise.
Networking
- Michael Kashin takes a look at AppSwitch and likens it to “serverless SDN.”
- Nick Buraglio exposes the different kinds of NAT—helpful if you’re new to networking and want to better understand NAT and the nuances involved.
Servers/Hardware
- Greg Schulz discusses new Power9-based systems announced by IBM; see his post. Normally I wouldn’t be too interested in non-x86 stuff, as it seems like x86 is ascendant. However, given the rise of all the various speculative execution attacks, and given the recent interest in ARM platforms (can’t recall if they are affected by the speculative execution attacks), is a revival of non-x86 platforms in the works?
Security
Nothing this time around, but I’ll stay alert for items to include next time!
Cloud Computing/Cloud Management
- This is just awesome.
- It’s fairly simplistic, but it could be useful nevertheless: the kube-resource-report project offers Continue reading
Kubernetes with Cilium and Containerd using Kubeadm
Now, if that isn’t a title jam-packed with buzzwords, I don’t know what is! In seriousness, though, I wanted to share how to use kubeadm to turn up a Kubernetes cluster using containerd (instead of Docker) and Cilium as the CNI plugin. I’m posting this because I wasn’t able to find a reasonable article that combined all the different threads—some posts talked about using containerd, others talked about using Cilium, and the official Kubernetes docs have examples for using kubeadm. The purpose of this post is to try to pull those threads together.
For structure and context, I’ll build upon the official Kubernetes document outlining creating highly available clusters with kubeadm. You may find it helpful to pull up that article next to this one, as I won’t be duplicating that content here. Instead, I’ll just reference additions/changes to the process in order to accommodate containerd and Cilium.
Before getting started, make sure that your systems will meet the minimum requirements for Cilium. For my testing, I used Ubuntu 16.04 with the latest HWE kernel (4.15.0-33-generic). I used a private fork of Wardroom to build the AWS AMIs with containerd and all the Kubernetes 1.11.2 Continue reading
Getting Started: Visit Us at AnsibleFest!

Hello, and welcome to another Getting Started blog post… though this one is a bit different. I’d like to tell you about AnsibleFest 2018 in Austin, TX, where for the first time there will be a dedicated Getting Started section at this annual event!
Participants who visit our area will be able to meet some members of the Getting Started team as well as attend presentations. The scheduled talks include Ansible Essentials (similar to the monthly webinars) and Writing Your First Playbook, based on our most popular blog post.
In addition to the two scheduled talks each day, there will also be a lounge area where attendees can ask questions and get answers from Ansible experts in person! Come stop by to learn about what makes Ansible different, how it works, and get a quick overview of Ansible Tower. No experience is required, which means this is going to be a great chance for you or perhaps a teammate who is new to Ansible to learn about it from the ground up.
Make sure to register soon so that we can see you in Austin this October!
Top Questions from VMworld 2018

Last week, the Docker team had a chance to interact with the attendees of VMworld to talk about containers and container platforms. We spoke to companies in all stages of their containerization journey – some were just getting started and figuring out where containers may be used, others had started early containerization projects, some had mature container environments. Here are some of the most common questions we were asked.
Q: We have developers that are using Docker containers now, but what is the relevancy of containers to me (as an IT or virtualization admin)?
A: While developers were the first to adopt containers, there are many benefits of containers for IT:
- Server consolidation: While virtualization did increase the number of virtual machines per server, studies show that servers are still greatly underutilized. On average, Docker Enterprise customers see 50% greater server consolidation with containerization. That means being able to pack more workloads onto existing infrastructure or even reducing the number of servers and therefore saving on licensing and hardware costs.
- Easier patching and maintenance: Containerized applications can be updated easily through changes to the source image file. This also means it’s possible to update and rollback patches on the Continue reading
Imagine Yourself on the DockerCon Stage
We want to hear from you
Share your story of how Docker and containers work for you at DockerCon EU in Barcelona Dec 3-5, 2018. DockerCon is the industry-leading container conference where thought leaders and the community of developers, IT professionals, architects and business leaders come together to learn, discover and engage with each other. Part of the learning experience is hearing about the possibilities of containerization from other teams using containers.
Don’t be shy about proposing your idea – no topic is too small or too big. For every presentation given, there are hundreds of people who learn and relate to the experience and insights that you share. Some of the best talks have come from people just like you — and for some, DockerCon is their very first time public speaking. Our team is standing by to help with any first timers’ jitters too!
The deadline to submit a topic is just around the corner: Sept. 8, 2018
What do people want to hear about?
DockerCon provides a variety of breakouts to address the needs of both developers and IT teams whether they are new to containers or about to scale a global deployment.
Book Review: REST API Design Rulebook
REST API Design Rulebook (written by Mark Masse and published by O’Reilly Media; more details here) is an older book, published in late 2011. However, having never attempted to design a REST API before, I found lots of useful information inside that really helped shape my understanding of REST APIs and REST API design.
(In case you’re wondering why I was reading a book about REST API design, this ties into my 2018 project list and the software development project I recently launched.)
Overall, I found the book quite helpful and useful. If I had one complaint about the book, it would be the book’s repeated insistence on referring to WRML (Web Resource Modeling Language), which—as I understand it—is a proposed solution by the book’s author to some of the challenges around REST API design. I get that the author is sold on the value of WRML, but at times the book felt very much like a WRML commercial.
Aside from that one complaint, the book’s organization into a set of “rules” helped make the material reasonably consumable, and I appreciated the review of key terms at the end of each chapter.
I do still have some Continue reading
Better XMind-GNOME Integration
In December of 2017 I wrote about how to install XMind 8 on Fedora 27, and at the time of that writing I hadn’t quite figured out how to define a MIME type for XMind files that would allow users to double-click on an XMind file in Nautilus and open that file in XMind. After doing a bit of additional research and testing, I’ve found a solution and would like to share it here.
The solution I’ll describe here has been tested on Fedora 28, but it should work on just about any distribution with the GNOME desktop environment.
First, you’ll want to define the MIME type by creating an XML file in the ~/.local/share/mime/packages directory, as outlined here. I called my file application-vnd-xmind-workbook.xml, but I don’t know if the filename actually matters. (I derived the filename from this list of XMind file types.) The contents of the file should look something like this:
<mime-info xmlns="http://www.freedesktop.org/standards/shared-mime-info">
<mime-type type="application/vnd.xmind.workbook">
<comment>XMind Workbook</comment>
<glob pattern="*.xmind"/>
<glob pattern="*.XMIND"/>
<glob pattern="*.XMind"/>
</mime-type>
</mime-info>
You’ll note that multiple glob patterns are included to help deal with case sensitivity issues. The specific values used in Continue reading
Are Containers Replacing Virtual Machines?
With 20,000 partners and attendees converging at VMworld in Las Vegas this week, we often get asked if containers are replacing virtual machines (VMs). Many of our Docker Enterprise customers do run their containers on virtualized infrastructure while others run it on bare metal. Docker provides IT and operators choice on where to run their applications – in a virtual machine, on bare metal, or in the cloud. In this blog we’ll provide a few thoughts on the relationship between VMs and containers.
Point #1: Containers Are More Agile than VMs
At this stage of container maturity, there is very little doubt that containers give both developers and operators more agility. Containers deploy quickly, deliver immutable infrastructure and solve the age-old “works on my machine” problem. They also replace the traditional patching process, allowing organizations to respond to issues faster and making applications easier to maintain.
Point #2: Containers Enable Hybrid and Multi-Cloud Adoption
Once containerized, applications can be deployed on any infrastructure – on virtual machines, on bare metal, and on various public clouds running different hypervisors. Many organizations start with running containers on their virtualized infrastructure and find it easier to then migrate to Continue reading
Ansible Integrations at AnsibleFest

AnsibleFest is fast approaching! We couldn’t be more excited to be holding our 13th AnsibleFest in Austin, TX. This year's AnsibleFest is on track to be the biggest one ever. Ansible is the proverbial Swiss Army knife in the office desk drawer. The Ansible Integrations track will highlight the combined power of Ansible when used with other technologies. Combining Ansible with other technologies enables organizations to reach new heights with their automation.
As someone who has worked in the DevOps space for years, I'm looking forward to this track. It's filled with talks from speakers that have improved their existing tooling with Ansible. There are a few sessions you might find me standing in the back of (time permitting, of course) that I’d like to highlight here:
1. Ansible and HashiCorp: Better together from Sean Carolan, HashiCorp and Dylan Silva, Red Hat
Automation tools don’t have to be competitive. Great things can be achieved when you combine great tools together and collaborate. Come along and learn how Ansible users can leverage HashiCorp tools/products to achieve their goals of an automated enterprise through complimentary security, image management, post provisioning configuration and integrated end-to-end automation solutions. Read more here.
Having used Ansible Continue reading



