IPv6 Buzz 033: ARIN’s Role In IPv6 Address Allocation
ARIN is the official network numbers register for IPv4 and IPv6 addresses, as well as ASNs, for North America. The IPv6 Buzz crew talk with Mark Kosters, ARIN's CTO, about its role in providing IPv6 address resources, policy, and advocacy.
The post IPv6 Buzz 033: ARIN’s Role In IPv6 Address Allocation appeared first on Packet Pushers.
Day Two Cloud 016: Checking Up On Azure Kubernetes Service
On today's Day Two Cloud podcast, host Ned Bellavance checks in on Azure Kubernetes Service (AKS), which launched to the public in June of 2018. Ned and guest Justin Luk discuss why Microsoft rolled out AKS when it already had existing container services, business drivers for AKS, customer adoption, lessons learned, and more.Day Two Cloud 016: Checking Up On Azure Kubernetes Service
On today's Day Two Cloud podcast, host Ned Bellavance checks in on Azure Kubernetes Service (AKS), which launched to the public in June of 2018. Ned and guest Justin Luk discuss why Microsoft rolled out AKS when it already had existing container services, business drivers for AKS, customer adoption, lessons learned, and more.
The post Day Two Cloud 016: Checking Up On Azure Kubernetes Service appeared first on Packet Pushers.
Red Hat’s OpenShift Service Mesh Nears Prime Time
The OpenShift Service Mesh handles service-to-service communication of Kubernetes-orchestrated...
Supercharging Firewall Events for Self-Serve
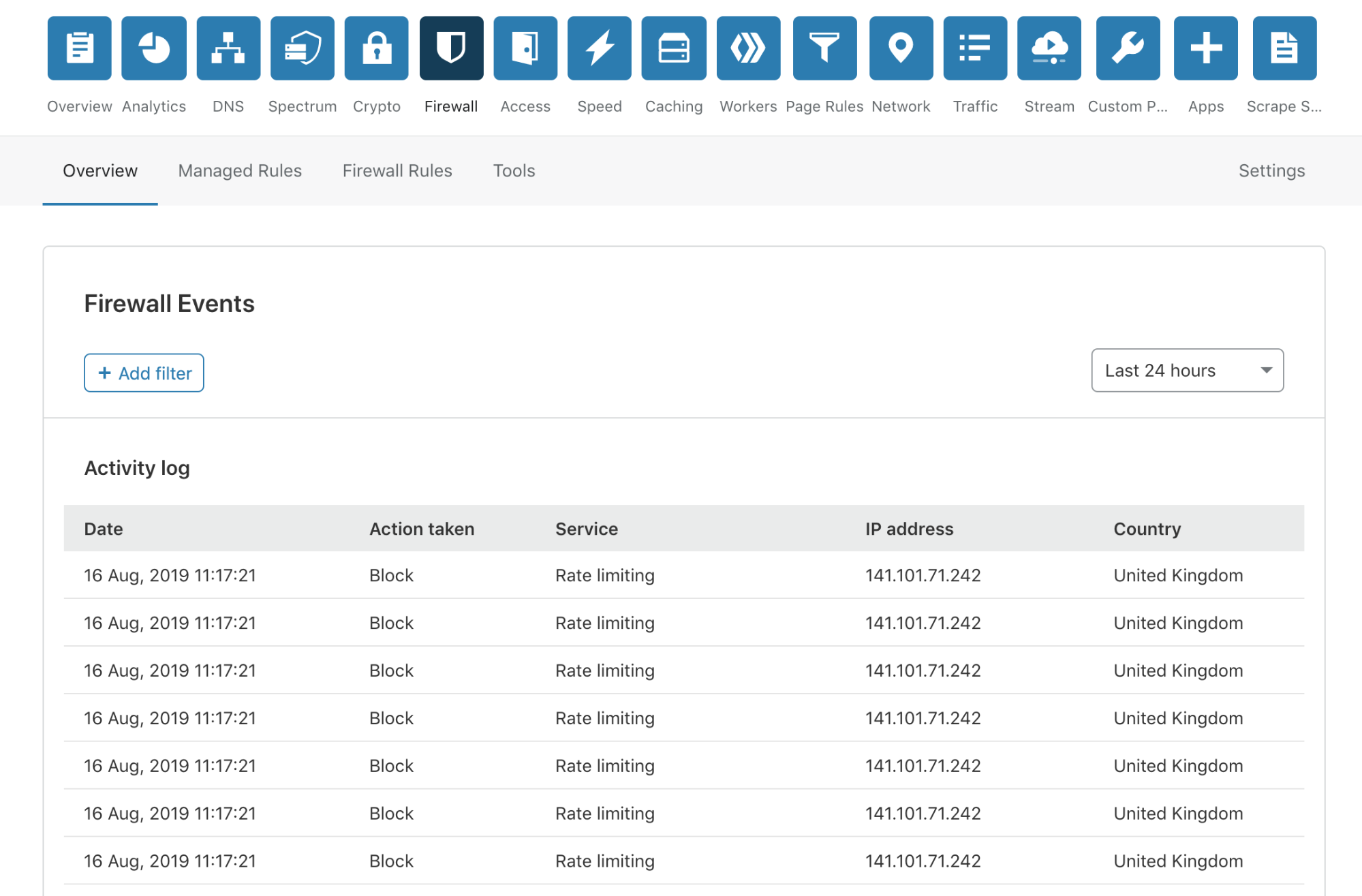
Today, I’m very pleased to announce the release of a completely overhauled version of our Firewall Event log to our Free, Pro and Business customers. This new Firewall Events log is now available in your Dashboard, and you are not required to do anything to receive this new capability.
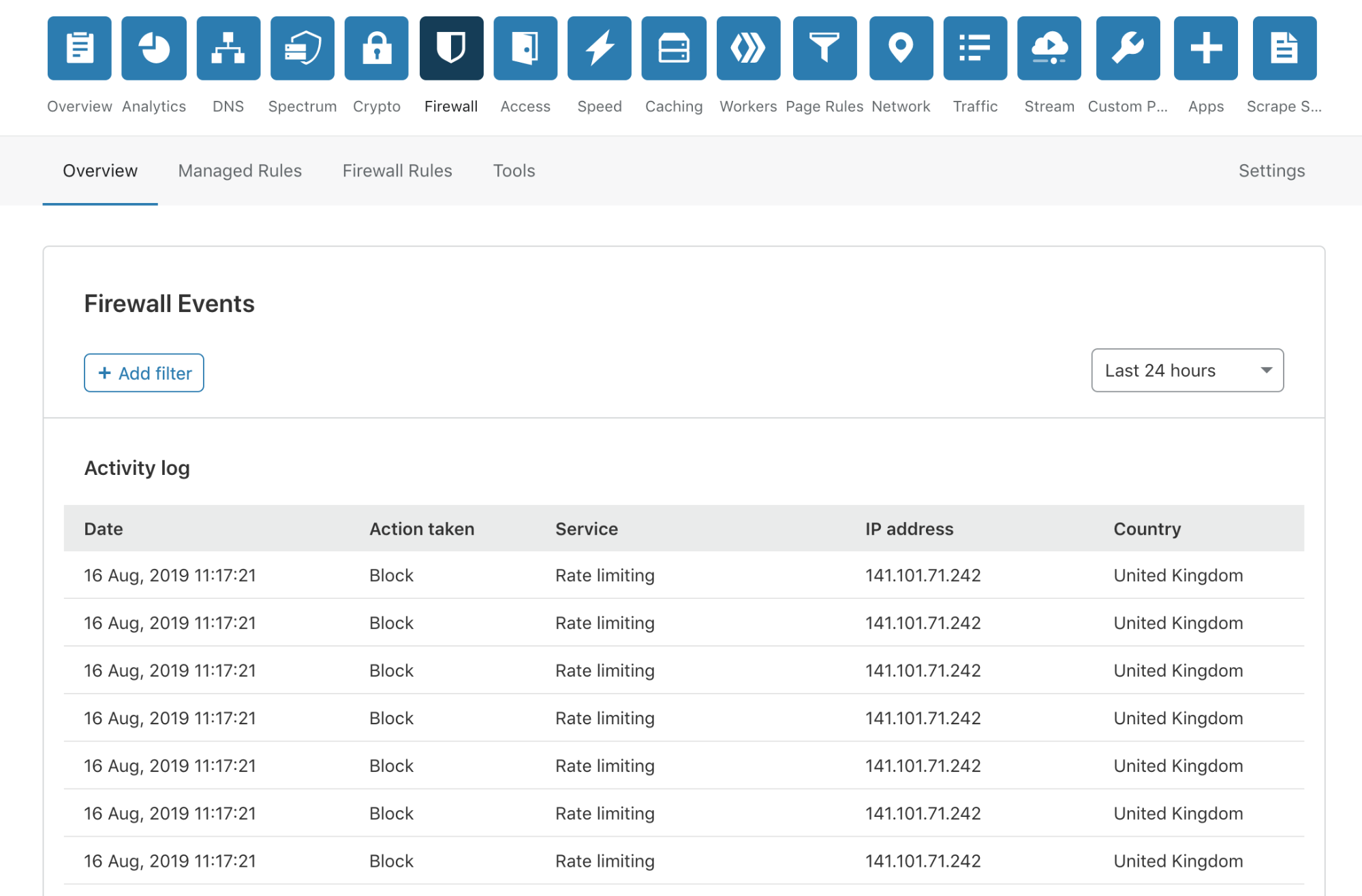
No more modals!
We have done away with those pesky modals, providing a much smoother user experience. To review more detailed information about an event, you simply click anywhere on the event list row.
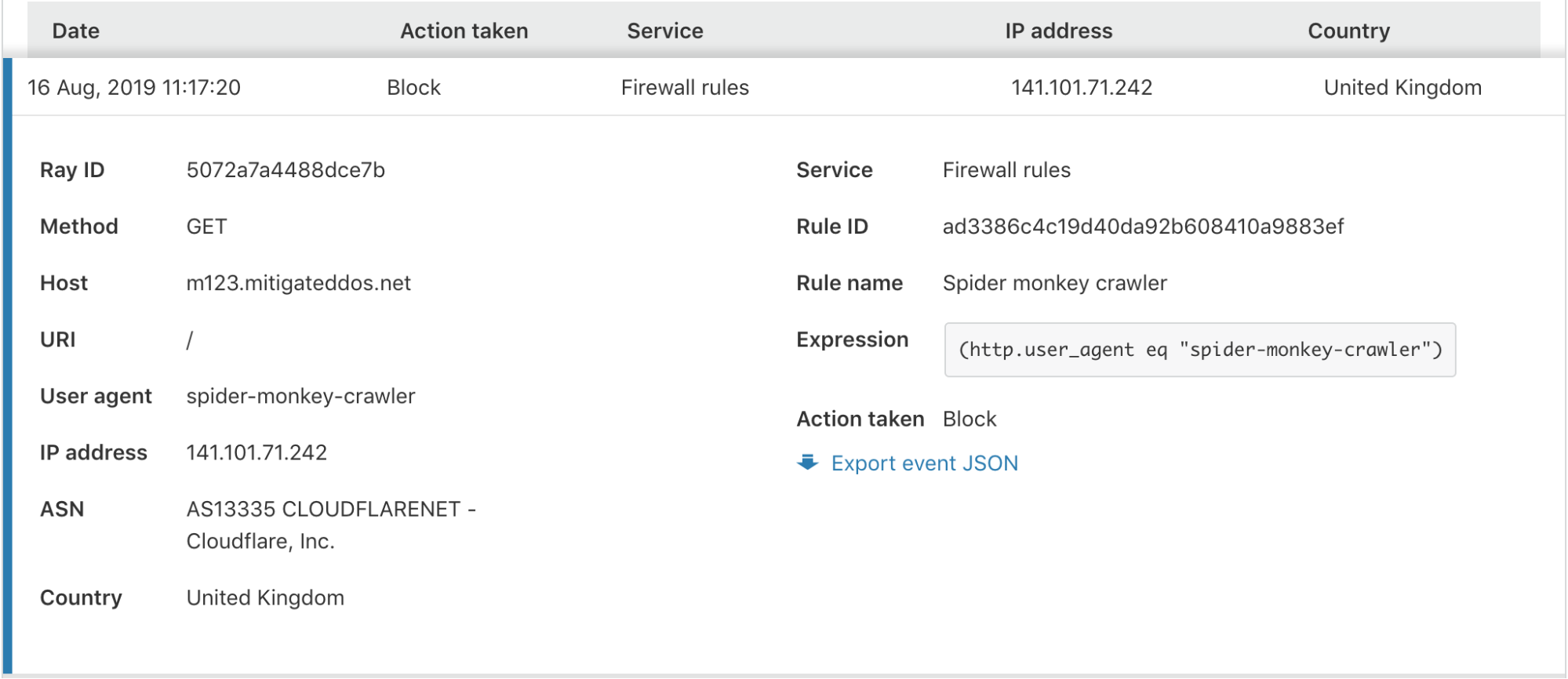
In the expanded view, you are provided with all the information you may need to identify or diagnose issues with your Firewall or find more details about a potential threat to your application.
Additional matches per event
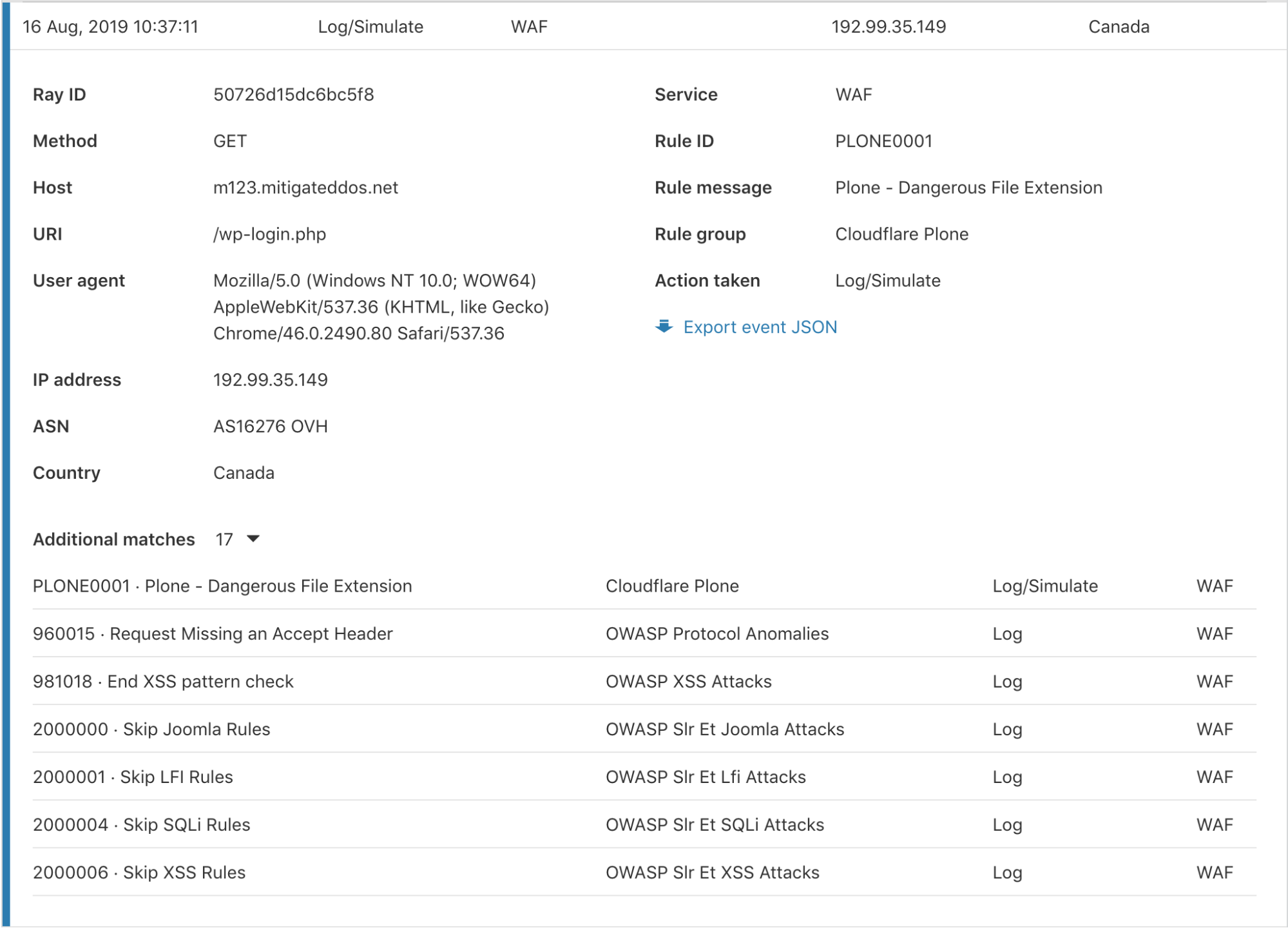
Cloudflare has several Firewall features to give customers granular control of their security. With this control comes some complexity when debugging why a request was stopped by the Firewall. To help clarify what happened, we have provided an “Additional matches” count at the bottom for events triggered by multiple services or rules for the same request. Clicking the number expands a list showing each rule and service along with the corresponding action.
Search for any field within a Firewall Event
Must Read: When Redundancy Actually Helps
Stumbled upon an excellent redundancy-focused blog post (HT: High Scalability). Here are just a few important points:
- Don’t make things too complex;
- Don’t add more risk than you take away;
- You’ve got to fail over in the right direction;
- You must be able to return to fully-redundant mode.
I’m guessing that people promoting stretched VLANs, vSphere and/or NSX clusters running across multiple sites, weird combination of EVPN and OTV, and a dozen similar shenanigans never considered any one of these points.
AfPIF Day Two: International Traffic, the Economics of Peering, and a Look Ahead to 2030

In the last five years, Africa’s international traffic patterns have changed, with international and intra regional traffic growing, according to the latest statistics from Telegeography, presented at this year’s AfPIF.
Johannesburg, Cape Town, Lagos, and Nairobi maintain their top hub status, but Cotonou, Kigali, Libreville, Abidjan, and Dakar have emerged as major hubs as international traffic grows. Cotonou recorded 88Gps between 2018 and 2019, showing a 77% growth, while Kigali recorded 75Gbps, a 92% growth, and Libreville had 113Gbps at 71% growth.
This was attributed to a drastic reduction in connectivity costs, which led to more data center space and eventual demand for more capacity to other international hubs. West African connection, especially between Dakar, Abidjan, Accra, and Lagos has also increased.
Telegeography monitors international transit traffic and the presentation was one of the highlights of the day. Domestic traffic is a bit harder to capture but Telegeography promised to work with more providers to get future snapshots of the growing traffic.
The presentation by Telegeography explored the shifting connectivity landscape in Africa and its effect on interconnection hubs, showing that new hubs may soon emerge, as more and more cities reduce the cost of connectivity and invest in more Continue reading
Install Golang Ubuntu1804
This will just be a quick post on how to install Golang on Ubuntu 1804. There will be no earth shattering knowledge bombs, it's more of a documentation post for myself. Others may or may not find it useful. Code versions used for this lab Ubuntu - 1804 Golang - 1.15.1 Download Download...Install Golang Ubuntu1804
Installing Golang on Ubuntu 1804.AnsibleFest Atlanta – Network Automation

Now that the agenda for AnsibleFest is live, we wanted to take a closer look at each of the tracks that we will offer. Soon you will be able to start building out your schedule for AnsibleFest, so we want to help you figure out what tracks and sessions will be best for you! We talked with Track Lead Andrius Benokraitis to learn more about the Network Automation track and the sessions within it.
Who is this track best for?
This track is best for Network Operators, Network Engineers, Cloud Operators, and DevOps Engineers. It is great for people who are looking to learn more about automating the configuration, management and operations of a computer network.
What topics will this track cover?
This track will cover topics that include operational application of Red Hat Ansible Automation for network use cases, including devices such as: switches, routers, load balancers, firewalls. We will also be discussing different point of views: Developer of modules vs. User and implementer of modules and roles. There will also be a discussion around how enterprises are using Ansible Automation as a platform for large scale network deployments.
What should attendees expect Continue reading
Veritas Moves Into VMware-Based Clouds
Veritas announced availability of its Enterprise Data Services Platform for VMware environments...
Splunk Plunks Down $1.05B, Acquires SignalFx
Splunk today announced an agreement to acquire SignalFx, which provides real-time monitoring and...
Creating Tagged Subnets Across AWS AZs Using Pulumi
As I mentioned back in May in this post on creating a sandbox for learning Pulumi, I’ve started using Pulumi more and more of my infrastructure-as-code needs. I did switch from JavaScript to TypeScript (which I know compiles to JavaScript on the back-end, but the strong typing helps a new programmer like me). Recently I had a need to create some resources in AWS using Pulumi, and—for reasons I’ll explain shortly—many of the “canned” Pulumi examples didn’t cut it for my use case. In this post, I’ll share how I created tagged subnets across AWS availability zones (AZs) using Pulumi.
In this particular case, I was using Pulumi to create all the infrastructure necessary to spin up an AWS-integrated Kubernetes cluster. That included a new VPC, subnets in the different AZs for that region, an Internet gateway, route tables and route table associations, security groups, an ELB for the control plane, and EC2 instances. As I’ve outlined in my latest post on setting up an AWS-integrated Kubernetes 1.15 cluster using kubeadm, these resources on AWS require specific AWS tags to be assigned in order for the AWS cloud provider to work.
As I started working on this, Continue reading
Can a Composable Hypervisor Re-Imagine Virtualization?
“Virtualization is changing and what people need from virtualization is changing,” said Intel's...